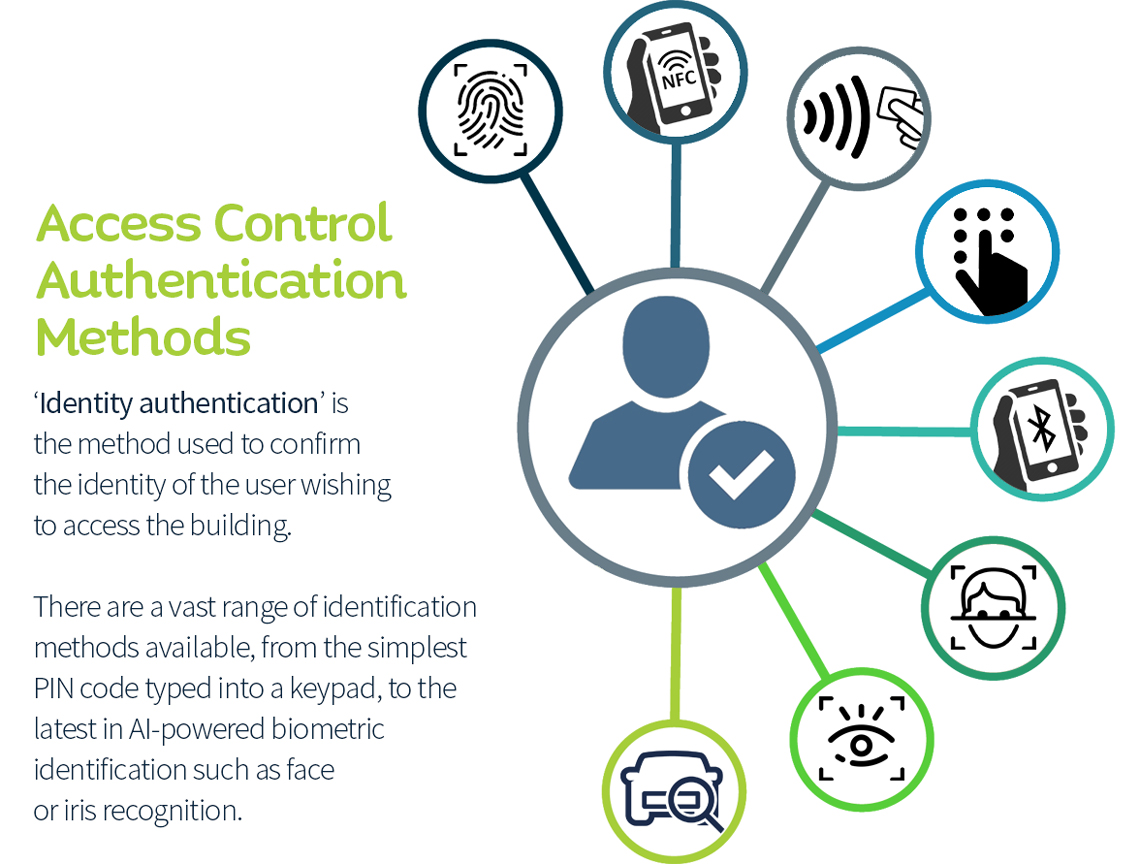
Implementing Access Control . Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Discretionary access control (dac) allows resource owners to control access. Here are some important best practices that can make access control more secure. Organizations planning to implement an access control system should consider three abstractions: This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. There are four main types of access control: Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what.
from cie-group.com
Here are some important best practices that can make access control more secure. This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. Discretionary access control (dac) allows resource owners to control access. Organizations planning to implement an access control system should consider three abstractions: There are four main types of access control: Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources.
How to design an Access Control system
Implementing Access Control Organizations planning to implement an access control system should consider three abstractions: Organizations planning to implement an access control system should consider three abstractions: This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. Discretionary access control (dac) allows resource owners to control access. Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. There are four main types of access control: Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. Here are some important best practices that can make access control more secure.
From seisecurity.com
Advantages of Implementing an Access Control System SEi Security Implementing Access Control Discretionary access control (dac) allows resource owners to control access. There are four main types of access control: Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. Here are some important. Implementing Access Control.
From digestley.com
Understanding Access Control And How To Implement It Implementing Access Control Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Discretionary access control (dac) allows resource owners to control access. This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. This article provides. Implementing Access Control.
From www.slideserve.com
PPT Implementing Access Control with Zend Framework PowerPoint Implementing Access Control This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. There are four main types of access control: Here are some important best practices that can make access control more secure. Organizations planning to implement an access control system should consider three abstractions: This article explores the importance of access control in. Implementing Access Control.
From xsopedia.wordpress.com
What is Access Control System and How Does it Work? Quest Implementing Access Control Discretionary access control (dac) allows resource owners to control access. There are four main types of access control: Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. This article explores the importance. Implementing Access Control.
From dokumen.tips
(PDF) implementing access control lists for threat mitigation DOKUMEN Implementing Access Control Organizations planning to implement an access control system should consider three abstractions: There are four main types of access control: Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Access control is an essential element of security that determines who is allowed to access certain data,. Implementing Access Control.
From peligro-e-portfolio.webflow.io
Module 5 Implementing Access Control, Authentication and Account Implementing Access Control Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. This article provides a brief insight into understanding access controls, and reviewing its definition, types,. Implementing Access Control.
From cyberhoot.com
Access Control Mechanism CyberHoot Implementing Access Control There are four main types of access control: Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Discretionary access control (dac) allows resource owners to control access. Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. This article provides a brief insight. Implementing Access Control.
From itchol.com
Why Access Control Is Important Access Control Examples and Solutions Implementing Access Control Here are some important best practices that can make access control more secure. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Discretionary access control (dac) allows resource owners to control access. This article explores the importance of access control in security strategies and provides an overview. Implementing Access Control.
From www.accelaz.com
Implementing Access Control The Essential Guide For Building Owners Implementing Access Control This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. There are four main types of access control: Discretionary access control (dac) allows resource. Implementing Access Control.
From biznis-plus.com
What Is RoleBased Access Control? Here’s A Quick Guide For Every Implementing Access Control Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. Access control is the. Implementing Access Control.
From www.varonis.com
What is RoleBased Access Control (RBAC)? Implementing Access Control Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. Organizations planning to implement an access control system should consider three abstractions: There are four main types of access control:. Implementing Access Control.
From www.slideserve.com
PPT Considerations for Implementing an Access Control System in UAE Implementing Access Control Here are some important best practices that can make access control more secure. Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. There are four main types of access control: Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Organizations planning. Implementing Access Control.
From blog.soliditech.com
Five Best Practices for Access Control Implementing Access Control Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Here are some important best practices that can make access control more secure. Organizations planning to implement an access control system should consider. Implementing Access Control.
From goodycyb.hashnode.dev
Implementing Role Based Access Control with GCP IAM Implementing Access Control Here are some important best practices that can make access control more secure. Discretionary access control (dac) allows resource owners to control access. Organizations planning to implement an access control system should consider three abstractions: Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. This article provides a brief insight into understanding access controls, and. Implementing Access Control.
From trivestgroup.com
What is Physical Access Control and Which Types Do You Need? Implementing Access Control This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. There are four main types of access control: Organizations planning to implement an access control system should consider three abstractions: Access control is the process that considers the. Implementing Access Control.
From www.secomllc.com
Implementing Access Controls 3 Ways they Reduce Costs Implementing Access Control This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. Here are some important best practices that can make access control more secure. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Organizations planning to implement an access control. Implementing Access Control.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Implementing Access Control Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. Organizations planning to implement an access control system should consider three abstractions: Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Access control is the process that considers the defined policy and determines. Implementing Access Control.
From cie-group.com
How to design an Access Control system Implementing Access Control Organizations planning to implement an access control system should consider three abstractions: There are four main types of access control: Here are some important best practices that can make access control more secure. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. This article provides a brief. Implementing Access Control.
From blog.smartbuildingsacademy.com
Implementing Access Control Integrations Implementing Access Control Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. Discretionary access control (dac) allows resource owners to control access. Access control is fundamental. Implementing Access Control.
From javascript.plainenglish.io
Implementing Access Control in React Apps A Complete Guide by Kyle Implementing Access Control Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Organizations planning to implement an access control system should consider three abstractions: This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. Discretionary access. Implementing Access Control.
From www.securiwiser.com
Understanding Data Access Control What it is and How it Works Implementing Access Control Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. This article provides a brief insight into understanding access controls, and reviewing its definition,. Implementing Access Control.
From www.youtube.com
Implementing Access Control YouTube Implementing Access Control There are four main types of access control: This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. This article explores the importance of access control in security strategies and. Implementing Access Control.
From alcatraz.ai
The Three Benefits of Multimodal Authentication for Physical Access Control Implementing Access Control There are four main types of access control: Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Discretionary access control (dac) allows resource owners to control access. Here are some important best practices that can make access control more secure. This article explores the importance of. Implementing Access Control.
From valasys.com
Top 5 Benefits of Implementing a Network Access Control Solution Today Implementing Access Control Discretionary access control (dac) allows resource owners to control access. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. This article explores the importance of access control in security. Implementing Access Control.
From csijax.com
Protecting Your Office How to Implement Access Controls Solutions Implementing Access Control Organizations planning to implement an access control system should consider three abstractions: Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. This article explores the importance of access control in security strategies and. Implementing Access Control.
From www.xorlogics.com
6 Tips for Implementing Access Control Authentication System With Implementing Access Control Organizations planning to implement an access control system should consider three abstractions: Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Discretionary access control (dac) allows resource owners to control access. Access control is the process that considers the defined policy and determines if a given subject. Implementing Access Control.
From www.atatus.com
RoleBased Access Control Definition, Implementation & More Implementing Access Control Here are some important best practices that can make access control more secure. There are four main types of access control: Organizations planning to implement an access control system should consider three abstractions: Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. This article provides a. Implementing Access Control.
From www.varonis.com
What is RoleBased Access Control (RBAC)? Implementing Access Control Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. There are four main types of access control: Discretionary access control (dac) allows resource owners to control access. Here are some important best practices that can make access control more secure. Organizations planning to implement an access control system should consider three abstractions: Access control is. Implementing Access Control.
From study.com
Access Control Types & Implementation Lesson Implementing Access Control Here are some important best practices that can make access control more secure. This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Discretionary access control (dac) allows resource. Implementing Access Control.
From medium.com
Implementing Strong Access Control in Cloud Environments Safeguarding Implementing Access Control Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. Discretionary access control (dac) allows resource owners to control access. This article provides a brief insight into understanding access controls, and reviewing its definition,. Implementing Access Control.
From www.fingerprint-access-control.com
Office Building Access Control using Biometrics Fingerprint Access Implementing Access Control There are four main types of access control: Here are some important best practices that can make access control more secure. Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. Discretionary access control (dac) allows resource owners to control access. Access control is an essential element of security that determines who is allowed to access. Implementing Access Control.
From blog.skyelearning.com
Access Control Best Practices Implementing Access Control Organizations planning to implement an access control system should consider three abstractions: This article explores the importance of access control in security strategies and provides an overview of key principles and best practices for its implementation. Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Here. Implementing Access Control.
From www.akmelock.com
9 Key Benefits of Implementing Access Control Systems BeTech Lock Implementing Access Control Here are some important best practices that can make access control more secure. Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Organizations planning to implement an access control system should consider three abstractions: This article provides a brief insight into understanding access controls, and reviewing. Implementing Access Control.
From www.threatkey.com
5 Key Benefits of Implementing Box Access Control Implementing Access Control Access control is the process that considers the defined policy and determines if a given subject is allowed to access a given object. Discretionary access control (dac) allows resource owners to control access. Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. Access control is an essential element of security that determines who is allowed. Implementing Access Control.
From www.businesstechweekly.com
Implementing Access Control Best Practices Implementing Access Control Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Access control is fundamental to maintaining the confidentiality, integrity, and availability of organizational resources. This article provides a brief insight into understanding access controls, and reviewing its definition, types, significance, and functions. Here are some important best practices. Implementing Access Control.