Ice Apple Indicators Of Compromise . During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint.
from www.thesslstore.com
During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the.
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed
Ice Apple Indicators Of Compromise Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints.
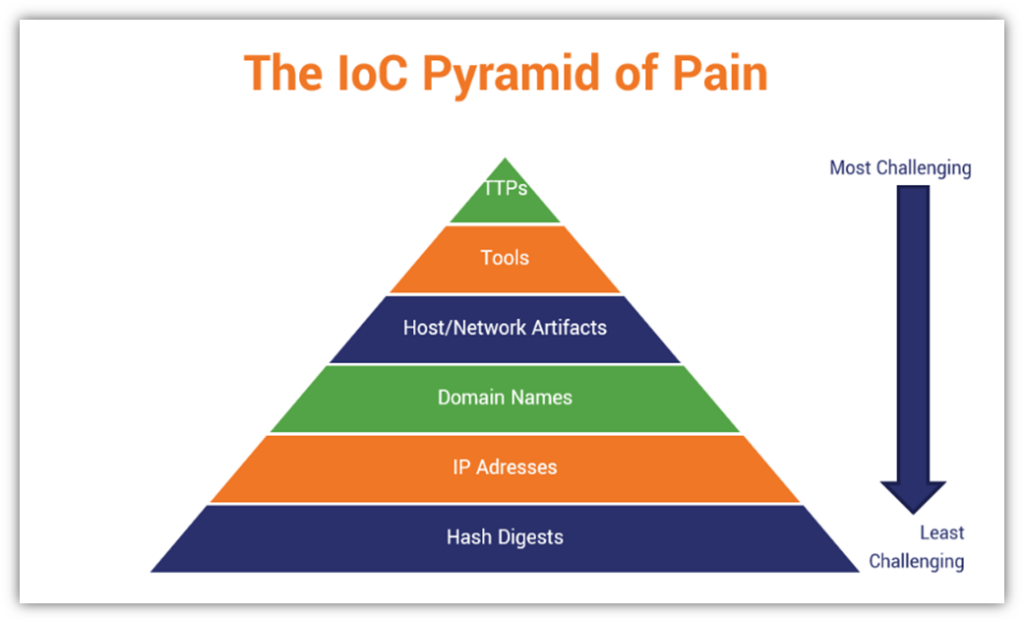
From www.domaintools.com
Tools To Quickly Extract Indicators of Compromise DomainTools Start Ice Apple Indicators Of Compromise During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. To halt other compromise. Ice Apple Indicators Of Compromise.
From www.linkedin.com
The Importance and Difference Between Indicators of Attack and Ice Apple Indicators Of Compromise Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities.. Ice Apple Indicators Of Compromise.
From techgenix.com
How Can an Indicator of Compromise (IOC) Help You in Cybersecurity? Ice Apple Indicators Of Compromise In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité.. Ice Apple Indicators Of Compromise.
From www.lepide.com
What are Indicators of Compromise? Ice Apple Indicators Of Compromise To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. Cyber defenders frequently rely. Ice Apple Indicators Of Compromise.
From hackforlab.com
Indicator of Attack vs Indicator of Compromises Indicator of Pivot Ice Apple Indicators Of Compromise To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. During routine detection. Ice Apple Indicators Of Compromise.
From www.sentinelone.com
What are Indicators of Compromise (IoCs)? An Easy Guide Ice Apple Indicators Of Compromise Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. To halt other compromise. Ice Apple Indicators Of Compromise.
From www.wallarm.com
What are Indicators of Compromise (IOC)? Ice Apple Indicators Of Compromise To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the.. Ice Apple Indicators Of Compromise.
From www.semanticscholar.org
Indicator of compromise Semantic Scholar Ice Apple Indicators Of Compromise Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data. Ice Apple Indicators Of Compromise.
From exobbptro.blob.core.windows.net
Indicator Of Compromise Sample at Arthur Carnes blog Ice Apple Indicators Of Compromise To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. An indicator of. Ice Apple Indicators Of Compromise.
From www.sekoia.io
What is an Indicator of Compromise (IoC)? SEKOIA.IO Ice Apple Indicators Of Compromise In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. Les. Ice Apple Indicators Of Compromise.
From github.com
GitHub Indicators of Ice Apple Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. Les indicateurs de compromission sont. Ice Apple Indicators Of Compromise.
From www.youtube.com
Understanding Indicators of Compromise for Incident Response YouTube Ice Apple Indicators Of Compromise To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities.. Ice Apple Indicators Of Compromise.
From www.elastic.co
Indicators of compromise Elastic Security Solution [8.15] Elastic Ice Apple Indicators Of Compromise In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. Cyber defenders frequently rely. Ice Apple Indicators Of Compromise.
From www.packetlabs.net
What are Indicators of Compromise (IoCs)? Ice Apple Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. In order to help your. Ice Apple Indicators Of Compromise.
From www.xcitium.com
What are Indicators of Compromise Security? IOC Meaning Ice Apple Indicators Of Compromise During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. In order to help your isac in the. Ice Apple Indicators Of Compromise.
From www.youtube.com
What are the Indicators of compromise YouTube Ice Apple Indicators Of Compromise During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that.. Ice Apple Indicators Of Compromise.
From www.lepide.com
What are Indicators of Compromise? Ice Apple Indicators Of Compromise Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to. Ice Apple Indicators Of Compromise.
From arcticwolf.com
Understanding Indicators of Compromise I Arctic Wolf Ice Apple Indicators Of Compromise Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on. Ice Apple Indicators Of Compromise.
From cyberartspro.com
IoC (Indicator Of Compromise) Nedir? CyberArts Ice Apple Indicators Of Compromise Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that.. Ice Apple Indicators Of Compromise.
From www.redpacketsecurity.com
Indicators of compromise (IOCs) how we collect and use them Ice Apple Indicators Of Compromise In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that.. Ice Apple Indicators Of Compromise.
From medium.com
A Guide to Indicators of Compromise (IoC) Analysis by Paritosh Medium Ice Apple Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints.. Ice Apple Indicators Of Compromise.
From www.upguard.com
What are Indicators of Compromise (IOCs)? UpGuard Ice Apple Indicators Of Compromise To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the.. Ice Apple Indicators Of Compromise.
From www.cyberwiki.in
Indicators of Compromise (IoCs) CyberWiki Encyclopedia of Cybersecurity Ice Apple Indicators Of Compromise In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect. Ice Apple Indicators Of Compromise.
From www.mdpi.com
Electronics Free FullText Key Requirements for the Detection and Ice Apple Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that.. Ice Apple Indicators Of Compromise.
From www.makeuseof.com
What Do the Indicators of Compromise Mean? The Best Tools to Help Ice Apple Indicators Of Compromise In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. Les. Ice Apple Indicators Of Compromise.
From widyasecurity.com
Apa itu Indicator of Compromise? • Widya Security Ice Apple Indicators Of Compromise To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint.. Ice Apple Indicators Of Compromise.
From www.thesslstore.com
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed Ice Apple Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. During. Ice Apple Indicators Of Compromise.
From fineproxy.org
Indicator of Compromise (IOC) FineProxy Glossary Ice Apple Indicators Of Compromise Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. To halt other compromise. Ice Apple Indicators Of Compromise.
From www.thesslstore.com
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed Ice Apple Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. In order to help your. Ice Apple Indicators Of Compromise.
From www.semanticscholar.org
Table 1 from Understanding Indicators of Compromise against Cyber Ice Apple Indicators Of Compromise Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the.. Ice Apple Indicators Of Compromise.
From www.youtube.com
What is IOC and IOA Indicator of Attack and Indicator of Compromise Ice Apple Indicators Of Compromise During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. Cyber defenders frequently rely. Ice Apple Indicators Of Compromise.
From securityboulevard.com
What are Indicators of Compromise in Threat Intelligence? Security Ice Apple Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in networks or on endpoints. To halt other compromise or. Ice Apple Indicators Of Compromise.
From blog.threat.zone
Glossary Indicator of Compromise VS Indicator of Attack Ice Apple Indicators Of Compromise To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. Cyber defenders frequently rely on indicators of compromise (iocs) to identify, trace, and block malicious activity in. Ice Apple Indicators Of Compromise.
From exobbptro.blob.core.windows.net
Indicator Of Compromise Sample at Arthur Carnes blog Ice Apple Indicators Of Compromise Les indicateurs de compromission sont les miettes de pain laissées par un agresseur après un incident de cybersécurité. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. In order to help your isac in the evaluation process, especially when assessing performance against objectives, some statistical input to the. Cyber defenders frequently rely. Ice Apple Indicators Of Compromise.
From www.scribd.com
Top 15 Indicators of Compromise PDF Denial Of Service Attack Ice Apple Indicators Of Compromise An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. To halt other compromise or prevent breaches of known iocs, successful ioc tools should be able to detect all malicious data that. During routine detection maintenance, our mac researchers stumbled upon a small set of files with backdoor capabilities. Cyber defenders frequently rely. Ice Apple Indicators Of Compromise.