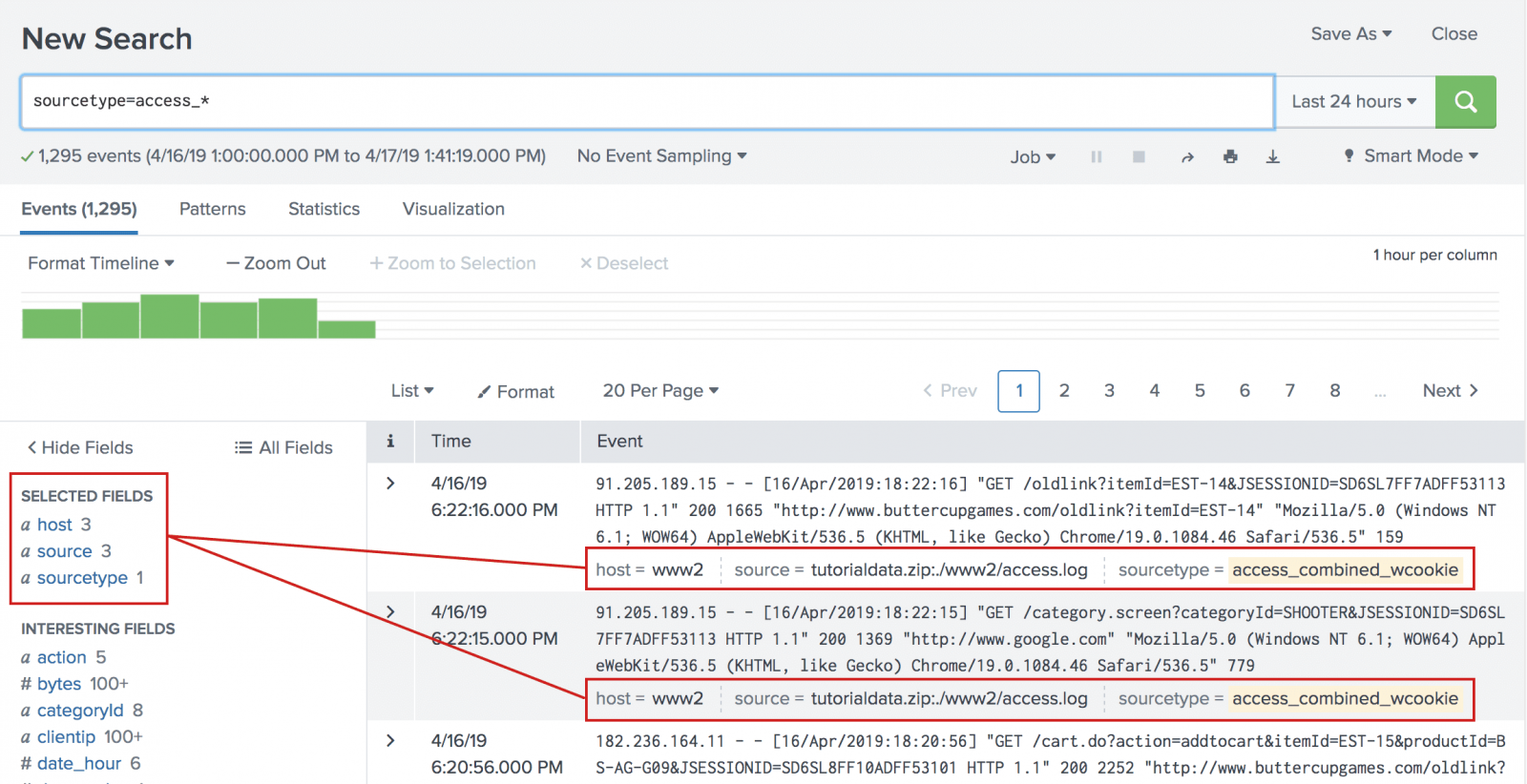
Splunk Fields Explained . Fields is a searchable name/value pair in splunk enterprise event data. Both the process by which splunk enterprise extracts. Because, inclusion is always better than exclusion. Fields are searchable name and value pairings that distinguish one event from another. The spl2 fields command specifies which fields to keep or remove from the search results. Keeps or removes fields from search results based on the field list criteria. Example use case, let's say you have two fields ip and. When you run a search on your event data, splunk software looks for. In splunk, fields are the building blocks of your data. They’re like labels that help you organize and search your data more. Fields are the building blocks of splunk searches, reports, and data models. Not all events have the same fields and field values. By default, the internal fields _raw and _time are.
from docs.splunk.com
The spl2 fields command specifies which fields to keep or remove from the search results. Fields is a searchable name/value pair in splunk enterprise event data. They’re like labels that help you organize and search your data more. Both the process by which splunk enterprise extracts. Fields are searchable name and value pairings that distinguish one event from another. In splunk, fields are the building blocks of your data. Keeps or removes fields from search results based on the field list criteria. Fields are the building blocks of splunk searches, reports, and data models. By default, the internal fields _raw and _time are. When you run a search on your event data, splunk software looks for.
Use fields to search Splunk Documentation
Splunk Fields Explained Keeps or removes fields from search results based on the field list criteria. Because, inclusion is always better than exclusion. Both the process by which splunk enterprise extracts. By default, the internal fields _raw and _time are. Fields is a searchable name/value pair in splunk enterprise event data. Not all events have the same fields and field values. Keeps or removes fields from search results based on the field list criteria. Fields are the building blocks of splunk searches, reports, and data models. They’re like labels that help you organize and search your data more. In splunk, fields are the building blocks of your data. When you run a search on your event data, splunk software looks for. The spl2 fields command specifies which fields to keep or remove from the search results. Example use case, let's say you have two fields ip and. Fields are searchable name and value pairings that distinguish one event from another.
From padakuu.com
Splunk Calculated Fields Splunk Fields Explained In splunk, fields are the building blocks of your data. When you run a search on your event data, splunk software looks for. Example use case, let's say you have two fields ip and. Because, inclusion is always better than exclusion. Fields is a searchable name/value pair in splunk enterprise event data. Fields are the building blocks of splunk searches,. Splunk Fields Explained.
From docs.splunk.com
Use fields to search Splunk Documentation Splunk Fields Explained By default, the internal fields _raw and _time are. Both the process by which splunk enterprise extracts. Fields is a searchable name/value pair in splunk enterprise event data. In splunk, fields are the building blocks of your data. Fields are the building blocks of splunk searches, reports, and data models. Not all events have the same fields and field values.. Splunk Fields Explained.
From docs.splunk.com
How data moves through Splunk deployments The data pipeline Splunk Splunk Fields Explained They’re like labels that help you organize and search your data more. Fields is a searchable name/value pair in splunk enterprise event data. Fields are searchable name and value pairings that distinguish one event from another. Example use case, let's say you have two fields ip and. Keeps or removes fields from search results based on the field list criteria.. Splunk Fields Explained.
From docs.splunk.com
Use fields to search Splunk Documentation Splunk Fields Explained The spl2 fields command specifies which fields to keep or remove from the search results. Keeps or removes fields from search results based on the field list criteria. When you run a search on your event data, splunk software looks for. They’re like labels that help you organize and search your data more. By default, the internal fields _raw and. Splunk Fields Explained.
From geek-university.com
Fields Splunk Splunk Fields Explained Because, inclusion is always better than exclusion. Keeps or removes fields from search results based on the field list criteria. They’re like labels that help you organize and search your data more. When you run a search on your event data, splunk software looks for. By default, the internal fields _raw and _time are. The spl2 fields command specifies which. Splunk Fields Explained.
From padakuu.com
Splunk Calculated Fields Splunk Fields Explained Because, inclusion is always better than exclusion. The spl2 fields command specifies which fields to keep or remove from the search results. In splunk, fields are the building blocks of your data. Fields are the building blocks of splunk searches, reports, and data models. Keeps or removes fields from search results based on the field list criteria. Both the process. Splunk Fields Explained.
From python-tricks.com
Splunk Field Search Splunk Tutorial Python Tricks Splunk Fields Explained Example use case, let's say you have two fields ip and. Fields are the building blocks of splunk searches, reports, and data models. Fields are searchable name and value pairings that distinguish one event from another. Fields is a searchable name/value pair in splunk enterprise event data. The spl2 fields command specifies which fields to keep or remove from the. Splunk Fields Explained.
From padakuu.com
Splunk Field Searching Splunk Fields Explained Fields are searchable name and value pairings that distinguish one event from another. By default, the internal fields _raw and _time are. Because, inclusion is always better than exclusion. The spl2 fields command specifies which fields to keep or remove from the search results. Fields is a searchable name/value pair in splunk enterprise event data. Both the process by which. Splunk Fields Explained.
From www.javatpoint.com
Splunk Field Searching Javatpoint Splunk Fields Explained In splunk, fields are the building blocks of your data. They’re like labels that help you organize and search your data more. When you run a search on your event data, splunk software looks for. Because, inclusion is always better than exclusion. The spl2 fields command specifies which fields to keep or remove from the search results. Fields is a. Splunk Fields Explained.
From www.youtube.com
splunk field extractions YouTube Splunk Fields Explained Both the process by which splunk enterprise extracts. Fields are the building blocks of splunk searches, reports, and data models. Fields are searchable name and value pairings that distinguish one event from another. Fields is a searchable name/value pair in splunk enterprise event data. They’re like labels that help you organize and search your data more. Because, inclusion is always. Splunk Fields Explained.
From www.youtube.com
What is Splunk ITSI?—Splunk's Solution for ITOps Explained Splunk Fields Explained Not all events have the same fields and field values. Fields are the building blocks of splunk searches, reports, and data models. In splunk, fields are the building blocks of your data. Fields are searchable name and value pairings that distinguish one event from another. By default, the internal fields _raw and _time are. Fields is a searchable name/value pair. Splunk Fields Explained.
From docs.splunk.com
Use fields to search Splunk Documentation Splunk Fields Explained When you run a search on your event data, splunk software looks for. Not all events have the same fields and field values. Keeps or removes fields from search results based on the field list criteria. They’re like labels that help you organize and search your data more. In splunk, fields are the building blocks of your data. Both the. Splunk Fields Explained.
From padakuu.com
Splunk Field Searching Splunk Fields Explained The spl2 fields command specifies which fields to keep or remove from the search results. Keeps or removes fields from search results based on the field list criteria. Fields are searchable name and value pairings that distinguish one event from another. Not all events have the same fields and field values. Because, inclusion is always better than exclusion. Both the. Splunk Fields Explained.
From queirozf.com
Splunk Examples Renaming/Replacing Fields and Values Splunk Fields Explained The spl2 fields command specifies which fields to keep or remove from the search results. Keeps or removes fields from search results based on the field list criteria. Example use case, let's say you have two fields ip and. In splunk, fields are the building blocks of your data. Not all events have the same fields and field values. By. Splunk Fields Explained.
From stackoverflow.com
csv Splunk Fields Broken Stack Overflow Splunk Fields Explained Example use case, let's say you have two fields ip and. In splunk, fields are the building blocks of your data. The spl2 fields command specifies which fields to keep or remove from the search results. Keeps or removes fields from search results based on the field list criteria. Fields are the building blocks of splunk searches, reports, and data. Splunk Fields Explained.
From blog.element84.com
Multifield extractions in Splunk Splunk Fields Explained Fields is a searchable name/value pair in splunk enterprise event data. Example use case, let's say you have two fields ip and. Fields are the building blocks of splunk searches, reports, and data models. Keeps or removes fields from search results based on the field list criteria. When you run a search on your event data, splunk software looks for.. Splunk Fields Explained.
From docs.splunk.com
Use fields to search Splunk Documentation Splunk Fields Explained They’re like labels that help you organize and search your data more. Both the process by which splunk enterprise extracts. Because, inclusion is always better than exclusion. When you run a search on your event data, splunk software looks for. Fields are the building blocks of splunk searches, reports, and data models. Example use case, let's say you have two. Splunk Fields Explained.
From community.splunk.com
Solved How to show Splunk field based on count of another... Splunk Splunk Fields Explained Not all events have the same fields and field values. In splunk, fields are the building blocks of your data. Fields are the building blocks of splunk searches, reports, and data models. Fields are searchable name and value pairings that distinguish one event from another. By default, the internal fields _raw and _time are. They’re like labels that help you. Splunk Fields Explained.
From www.youtube.com
Splunk Field Extraction Walkthrough YouTube Splunk Fields Explained Example use case, let's say you have two fields ip and. Keeps or removes fields from search results based on the field list criteria. Fields are the building blocks of splunk searches, reports, and data models. By default, the internal fields _raw and _time are. Fields is a searchable name/value pair in splunk enterprise event data. The spl2 fields command. Splunk Fields Explained.
From www.youtube.com
Splunk Eval Command YouTube Splunk Fields Explained Example use case, let's say you have two fields ip and. They’re like labels that help you organize and search your data more. Fields is a searchable name/value pair in splunk enterprise event data. When you run a search on your event data, splunk software looks for. By default, the internal fields _raw and _time are. Because, inclusion is always. Splunk Fields Explained.
From tekslate.com
Splunk Extract Fields TekSlate Splunk Tutorials Splunk Fields Explained By default, the internal fields _raw and _time are. Because, inclusion is always better than exclusion. Keeps or removes fields from search results based on the field list criteria. When you run a search on your event data, splunk software looks for. In splunk, fields are the building blocks of your data. Fields are searchable name and value pairings that. Splunk Fields Explained.
From python-tricks.com
Splunk Field Search Splunk Tutorial Python Tricks Splunk Fields Explained By default, the internal fields _raw and _time are. The spl2 fields command specifies which fields to keep or remove from the search results. Fields is a searchable name/value pair in splunk enterprise event data. When you run a search on your event data, splunk software looks for. Keeps or removes fields from search results based on the field list. Splunk Fields Explained.
From www.narangakshay.com
Extract New Fields in Splunk Splunk Fields Explained Fields are the building blocks of splunk searches, reports, and data models. The spl2 fields command specifies which fields to keep or remove from the search results. Fields is a searchable name/value pair in splunk enterprise event data. Fields are searchable name and value pairings that distinguish one event from another. In splunk, fields are the building blocks of your. Splunk Fields Explained.
From kinneygroup.com
How to Use Splunk Rex and Erex Commands & Field Extractions Kinney Group Splunk Fields Explained Both the process by which splunk enterprise extracts. Keeps or removes fields from search results based on the field list criteria. In splunk, fields are the building blocks of your data. Example use case, let's say you have two fields ip and. They’re like labels that help you organize and search your data more. Because, inclusion is always better than. Splunk Fields Explained.
From www.toyvsion.co
splunk lookup用法 splunk lookup definition Delhcat Splunk Fields Explained Both the process by which splunk enterprise extracts. Because, inclusion is always better than exclusion. Keeps or removes fields from search results based on the field list criteria. Fields are searchable name and value pairings that distinguish one event from another. The spl2 fields command specifies which fields to keep or remove from the search results. When you run a. Splunk Fields Explained.
From community.splunk.com
Solved How to show Splunk field based on count of another... Splunk Splunk Fields Explained The spl2 fields command specifies which fields to keep or remove from the search results. When you run a search on your event data, splunk software looks for. In splunk, fields are the building blocks of your data. Example use case, let's say you have two fields ip and. Fields is a searchable name/value pair in splunk enterprise event data.. Splunk Fields Explained.
From docs.bmc.com
Integrating with Splunk Enterprise Documentation for BMC Helix Splunk Fields Explained Keeps or removes fields from search results based on the field list criteria. Fields is a searchable name/value pair in splunk enterprise event data. The spl2 fields command specifies which fields to keep or remove from the search results. They’re like labels that help you organize and search your data more. When you run a search on your event data,. Splunk Fields Explained.
From community.splunk.com
Solved Extracting fields and values using csv in splunk Splunk Community Splunk Fields Explained Fields are searchable name and value pairings that distinguish one event from another. By default, the internal fields _raw and _time are. Because, inclusion is always better than exclusion. Example use case, let's say you have two fields ip and. Both the process by which splunk enterprise extracts. Fields is a searchable name/value pair in splunk enterprise event data. In. Splunk Fields Explained.
From www.narangakshay.com
Extract New Fields in Splunk Splunk Fields Explained Because, inclusion is always better than exclusion. Fields are the building blocks of splunk searches, reports, and data models. The spl2 fields command specifies which fields to keep or remove from the search results. Fields is a searchable name/value pair in splunk enterprise event data. Both the process by which splunk enterprise extracts. Example use case, let's say you have. Splunk Fields Explained.
From community.splunk.com
stats latest not showing any value for field Splunk Community Splunk Fields Explained When you run a search on your event data, splunk software looks for. Because, inclusion is always better than exclusion. The spl2 fields command specifies which fields to keep or remove from the search results. Example use case, let's say you have two fields ip and. Keeps or removes fields from search results based on the field list criteria. Both. Splunk Fields Explained.
From stackoverflow.com
How to evaluate a Splunk field which represents the length of another Splunk Fields Explained Example use case, let's say you have two fields ip and. Not all events have the same fields and field values. Keeps or removes fields from search results based on the field list criteria. In splunk, fields are the building blocks of your data. By default, the internal fields _raw and _time are. Fields are the building blocks of splunk. Splunk Fields Explained.
From docs.splunk.com
Use fields to search Splunk Documentation Splunk Fields Explained The spl2 fields command specifies which fields to keep or remove from the search results. When you run a search on your event data, splunk software looks for. Fields are searchable name and value pairings that distinguish one event from another. By default, the internal fields _raw and _time are. Because, inclusion is always better than exclusion. Fields are the. Splunk Fields Explained.
From python-tricks.com
Splunk Field Search Splunk Tutorial Python Tricks Splunk Fields Explained Because, inclusion is always better than exclusion. They’re like labels that help you organize and search your data more. Fields are searchable name and value pairings that distinguish one event from another. In splunk, fields are the building blocks of your data. Fields are the building blocks of splunk searches, reports, and data models. The spl2 fields command specifies which. Splunk Fields Explained.
From docs.splunk.com
Use fields to search Splunk Documentation Splunk Fields Explained They’re like labels that help you organize and search your data more. Fields are the building blocks of splunk searches, reports, and data models. Because, inclusion is always better than exclusion. Fields is a searchable name/value pair in splunk enterprise event data. When you run a search on your event data, splunk software looks for. Example use case, let's say. Splunk Fields Explained.
From www.splunk.com
Smooth operator Searching for multiple field values Splunk Splunk Fields Explained When you run a search on your event data, splunk software looks for. Fields is a searchable name/value pair in splunk enterprise event data. They’re like labels that help you organize and search your data more. Example use case, let's say you have two fields ip and. Fields are the building blocks of splunk searches, reports, and data models. By. Splunk Fields Explained.