Sign Message Gpg . This allows for the secure transmission of information between. View the fingerprint of a key, after confirming the key is authentic, sign the key. Given a signed document, you can either check the signature or check the signature and recover the original document. It takes 1 step to encrypt and sign. You’ll see that it only takes 1 step to decrypt and verify, as well. Gpg, or gnu privacy guard, is a public key cryptography implementation.
from confluence.atlassian.com
It takes 1 step to encrypt and sign. View the fingerprint of a key, after confirming the key is authentic, sign the key. This allows for the secure transmission of information between. Gpg, or gnu privacy guard, is a public key cryptography implementation. You’ll see that it only takes 1 step to decrypt and verify, as well. Given a signed document, you can either check the signature or check the signature and recover the original document.
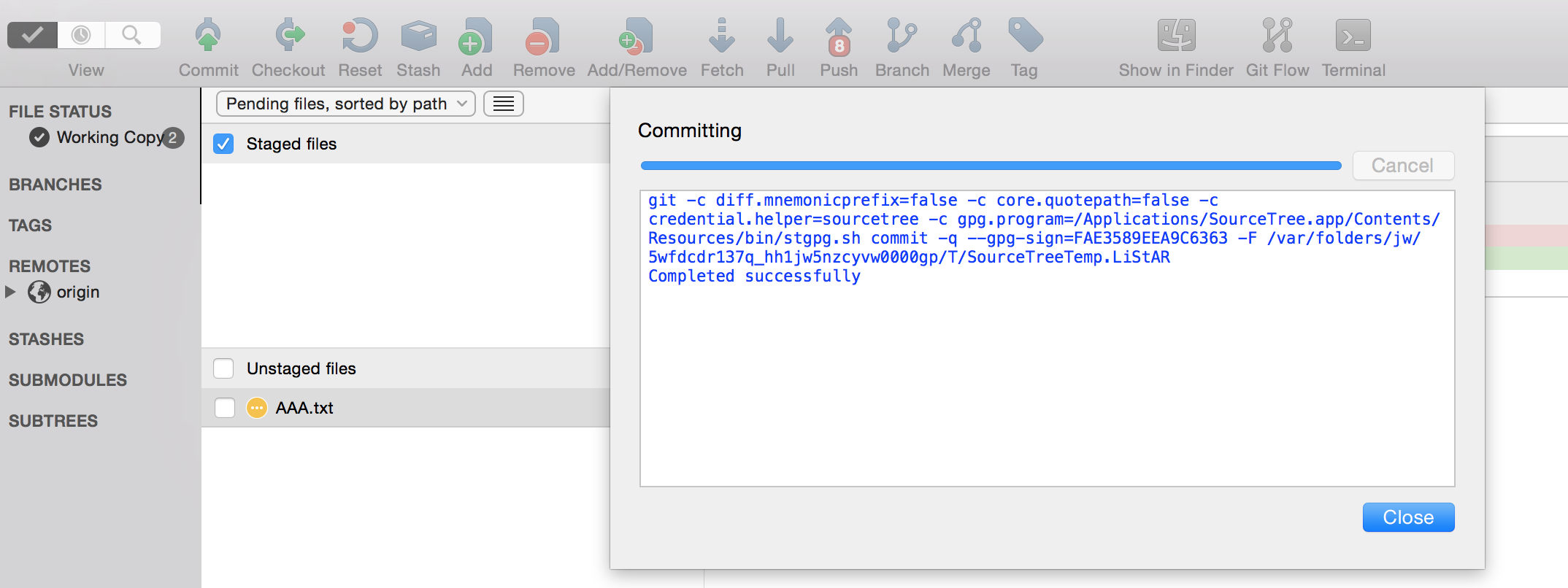
Setup GPG to sign commits within SourceTree Sourcetree Atlassian Documentation
Sign Message Gpg Gpg, or gnu privacy guard, is a public key cryptography implementation. You’ll see that it only takes 1 step to decrypt and verify, as well. Given a signed document, you can either check the signature or check the signature and recover the original document. View the fingerprint of a key, after confirming the key is authentic, sign the key. Gpg, or gnu privacy guard, is a public key cryptography implementation. It takes 1 step to encrypt and sign. This allows for the secure transmission of information between.
From www.gpgsigns.co.uk
Road & Safety Signs GPG Sign Message Gpg This allows for the secure transmission of information between. It takes 1 step to encrypt and sign. View the fingerprint of a key, after confirming the key is authentic, sign the key. Given a signed document, you can either check the signature or check the signature and recover the original document. You’ll see that it only takes 1 step to. Sign Message Gpg.
From www.wikihow.com
How to Verify a GPG Signature 5 Steps (with Pictures) wikiHow Sign Message Gpg Given a signed document, you can either check the signature or check the signature and recover the original document. This allows for the secure transmission of information between. Gpg, or gnu privacy guard, is a public key cryptography implementation. You’ll see that it only takes 1 step to decrypt and verify, as well. View the fingerprint of a key, after. Sign Message Gpg.
From fedoramagazine.org
GPG Using Your Key Fedora Magazine Sign Message Gpg Gpg, or gnu privacy guard, is a public key cryptography implementation. This allows for the secure transmission of information between. You’ll see that it only takes 1 step to decrypt and verify, as well. View the fingerprint of a key, after confirming the key is authentic, sign the key. It takes 1 step to encrypt and sign. Given a signed. Sign Message Gpg.
From www.youtube.com
How to sign a file or verify a signature of a file using GPG keychain YouTube Sign Message Gpg Gpg, or gnu privacy guard, is a public key cryptography implementation. View the fingerprint of a key, after confirming the key is authentic, sign the key. You’ll see that it only takes 1 step to decrypt and verify, as well. It takes 1 step to encrypt and sign. Given a signed document, you can either check the signature or check. Sign Message Gpg.
From slideplayer.com
CSE Computer Networks Prof. Aaron Striegel Department of Computer Science & Engineering Sign Message Gpg You’ll see that it only takes 1 step to decrypt and verify, as well. Given a signed document, you can either check the signature or check the signature and recover the original document. View the fingerprint of a key, after confirming the key is authentic, sign the key. It takes 1 step to encrypt and sign. Gpg, or gnu privacy. Sign Message Gpg.
From shahin.blog
Fixing the Git GPG sign issue Sign Message Gpg It takes 1 step to encrypt and sign. Given a signed document, you can either check the signature or check the signature and recover the original document. View the fingerprint of a key, after confirming the key is authentic, sign the key. This allows for the secure transmission of information between. You’ll see that it only takes 1 step to. Sign Message Gpg.
From www.tutonics.com
GPG Encryption Guide Part 1 Tutonics Sign Message Gpg View the fingerprint of a key, after confirming the key is authentic, sign the key. Given a signed document, you can either check the signature or check the signature and recover the original document. Gpg, or gnu privacy guard, is a public key cryptography implementation. This allows for the secure transmission of information between. You’ll see that it only takes. Sign Message Gpg.
From 9to5answer.com
[Solved] gpg WARNING message was not integrity 9to5Answer Sign Message Gpg Given a signed document, you can either check the signature or check the signature and recover the original document. It takes 1 step to encrypt and sign. This allows for the secure transmission of information between. Gpg, or gnu privacy guard, is a public key cryptography implementation. You’ll see that it only takes 1 step to decrypt and verify, as. Sign Message Gpg.
From www.claws-mail.org
Claws Mail GPG plugin Sign Message Gpg This allows for the secure transmission of information between. Gpg, or gnu privacy guard, is a public key cryptography implementation. It takes 1 step to encrypt and sign. You’ll see that it only takes 1 step to decrypt and verify, as well. Given a signed document, you can either check the signature or check the signature and recover the original. Sign Message Gpg.
From keestalkstech.com
Setup GPG signing on Windows KeesTalksTech Sign Message Gpg This allows for the secure transmission of information between. Gpg, or gnu privacy guard, is a public key cryptography implementation. Given a signed document, you can either check the signature or check the signature and recover the original document. You’ll see that it only takes 1 step to decrypt and verify, as well. It takes 1 step to encrypt and. Sign Message Gpg.
From andrewmatveychuk.com
How to sign your commits with GPG, Git and YubiKey Sign Message Gpg You’ll see that it only takes 1 step to decrypt and verify, as well. View the fingerprint of a key, after confirming the key is authentic, sign the key. This allows for the secure transmission of information between. Given a signed document, you can either check the signature or check the signature and recover the original document. Gpg, or gnu. Sign Message Gpg.
From github.blog
GPG signature verification The GitHub Blog Sign Message Gpg Given a signed document, you can either check the signature or check the signature and recover the original document. View the fingerprint of a key, after confirming the key is authentic, sign the key. It takes 1 step to encrypt and sign. This allows for the secure transmission of information between. You’ll see that it only takes 1 step to. Sign Message Gpg.
From www.comparitech.com
What is public key cryptography, how does it work and what are its uses? Sign Message Gpg This allows for the secure transmission of information between. It takes 1 step to encrypt and sign. Given a signed document, you can either check the signature or check the signature and recover the original document. You’ll see that it only takes 1 step to decrypt and verify, as well. Gpg, or gnu privacy guard, is a public key cryptography. Sign Message Gpg.
From www.youtube.com
gpg WARNING message was not integrity protected (3 Solutions!!) YouTube Sign Message Gpg Given a signed document, you can either check the signature or check the signature and recover the original document. You’ll see that it only takes 1 step to decrypt and verify, as well. This allows for the secure transmission of information between. It takes 1 step to encrypt and sign. View the fingerprint of a key, after confirming the key. Sign Message Gpg.
From www.alamy.com
Gpg tech logo hires stock photography and images Alamy Sign Message Gpg Given a signed document, you can either check the signature or check the signature and recover the original document. It takes 1 step to encrypt and sign. This allows for the secure transmission of information between. You’ll see that it only takes 1 step to decrypt and verify, as well. View the fingerprint of a key, after confirming the key. Sign Message Gpg.
From chive.ch
GPG with Agent on OS X Sign your commits! Kim Thoenen Sign Message Gpg This allows for the secure transmission of information between. You’ll see that it only takes 1 step to decrypt and verify, as well. It takes 1 step to encrypt and sign. Gpg, or gnu privacy guard, is a public key cryptography implementation. View the fingerprint of a key, after confirming the key is authentic, sign the key. Given a signed. Sign Message Gpg.
From alfredmyers.com
error gpg failed to sign the data Alfred Myers Sign Message Gpg View the fingerprint of a key, after confirming the key is authentic, sign the key. It takes 1 step to encrypt and sign. You’ll see that it only takes 1 step to decrypt and verify, as well. This allows for the secure transmission of information between. Given a signed document, you can either check the signature or check the signature. Sign Message Gpg.
From confluence.atlassian.com
Setup GPG to sign commits within SourceTree Sourcetree Atlassian Documentation Sign Message Gpg Given a signed document, you can either check the signature or check the signature and recover the original document. It takes 1 step to encrypt and sign. Gpg, or gnu privacy guard, is a public key cryptography implementation. You’ll see that it only takes 1 step to decrypt and verify, as well. This allows for the secure transmission of information. Sign Message Gpg.
From www.comparitech.com
What is public key cryptography, how does it work and what are its uses? Sign Message Gpg This allows for the secure transmission of information between. Given a signed document, you can either check the signature or check the signature and recover the original document. You’ll see that it only takes 1 step to decrypt and verify, as well. It takes 1 step to encrypt and sign. Gpg, or gnu privacy guard, is a public key cryptography. Sign Message Gpg.
From docs.github.com
Adding a GPG key to your GitHub account GitHub Docs Sign Message Gpg This allows for the secure transmission of information between. Given a signed document, you can either check the signature or check the signature and recover the original document. View the fingerprint of a key, after confirming the key is authentic, sign the key. You’ll see that it only takes 1 step to decrypt and verify, as well. Gpg, or gnu. Sign Message Gpg.
From www.youtube.com
How to generate an OpenPGP Signed Message with GPG? YouTube Sign Message Gpg This allows for the secure transmission of information between. It takes 1 step to encrypt and sign. View the fingerprint of a key, after confirming the key is authentic, sign the key. Given a signed document, you can either check the signature or check the signature and recover the original document. Gpg, or gnu privacy guard, is a public key. Sign Message Gpg.
From allabouttesting.org
Quick Tutorial How to Sign and Verify a file with gpg All About Testing Sign Message Gpg This allows for the secure transmission of information between. Gpg, or gnu privacy guard, is a public key cryptography implementation. View the fingerprint of a key, after confirming the key is authentic, sign the key. You’ll see that it only takes 1 step to decrypt and verify, as well. It takes 1 step to encrypt and sign. Given a signed. Sign Message Gpg.
From www.isitayush.dev
Why you should sign your commits with gpg. Ayush Gupta Sign Message Gpg It takes 1 step to encrypt and sign. View the fingerprint of a key, after confirming the key is authentic, sign the key. This allows for the secure transmission of information between. You’ll see that it only takes 1 step to decrypt and verify, as well. Given a signed document, you can either check the signature or check the signature. Sign Message Gpg.
From www.digicert.com
Secure GPG Signing That Works DigiCert Now Supports the GPG Keyring in DigiCert Software Trust Sign Message Gpg It takes 1 step to encrypt and sign. Gpg, or gnu privacy guard, is a public key cryptography implementation. This allows for the secure transmission of information between. View the fingerprint of a key, after confirming the key is authentic, sign the key. You’ll see that it only takes 1 step to decrypt and verify, as well. Given a signed. Sign Message Gpg.
From laramatic.com
Ezpinegpgsignandencrypt Command Laramatic Sign Message Gpg This allows for the secure transmission of information between. It takes 1 step to encrypt and sign. View the fingerprint of a key, after confirming the key is authentic, sign the key. Gpg, or gnu privacy guard, is a public key cryptography implementation. You’ll see that it only takes 1 step to decrypt and verify, as well. Given a signed. Sign Message Gpg.
From github.com
GitHub GuyErreich/gpgsigndemo Sign Message Gpg This allows for the secure transmission of information between. It takes 1 step to encrypt and sign. Gpg, or gnu privacy guard, is a public key cryptography implementation. View the fingerprint of a key, after confirming the key is authentic, sign the key. Given a signed document, you can either check the signature or check the signature and recover the. Sign Message Gpg.
From ioflood.com
Mastering GPG Command How to Install and Use in Linux Sign Message Gpg Given a signed document, you can either check the signature or check the signature and recover the original document. Gpg, or gnu privacy guard, is a public key cryptography implementation. View the fingerprint of a key, after confirming the key is authentic, sign the key. This allows for the secure transmission of information between. You’ll see that it only takes. Sign Message Gpg.
From smarttech101.com
How to encrypt and Sign your files using GPG SmartTech101 Sign Message Gpg This allows for the secure transmission of information between. Gpg, or gnu privacy guard, is a public key cryptography implementation. View the fingerprint of a key, after confirming the key is authentic, sign the key. Given a signed document, you can either check the signature or check the signature and recover the original document. It takes 1 step to encrypt. Sign Message Gpg.
From slideplayer.com
CSE Computer Networks Prof. Aaron Striegel Department of Computer Science & Engineering Sign Message Gpg You’ll see that it only takes 1 step to decrypt and verify, as well. View the fingerprint of a key, after confirming the key is authentic, sign the key. It takes 1 step to encrypt and sign. Gpg, or gnu privacy guard, is a public key cryptography implementation. This allows for the secure transmission of information between. Given a signed. Sign Message Gpg.
From www.youtube.com
Use GPG to sign packages and encrypt data YouTube Sign Message Gpg View the fingerprint of a key, after confirming the key is authentic, sign the key. Gpg, or gnu privacy guard, is a public key cryptography implementation. It takes 1 step to encrypt and sign. This allows for the secure transmission of information between. Given a signed document, you can either check the signature or check the signature and recover the. Sign Message Gpg.
From hypecycles.com
Everything you wanted to know about GPG but were scared to ask Hype Cycles Sign Message Gpg It takes 1 step to encrypt and sign. Given a signed document, you can either check the signature or check the signature and recover the original document. Gpg, or gnu privacy guard, is a public key cryptography implementation. View the fingerprint of a key, after confirming the key is authentic, sign the key. This allows for the secure transmission of. Sign Message Gpg.
From varrette.gforge.uni.lu
Tutorial GPG Sebastien Varrette, PhD. Sign Message Gpg This allows for the secure transmission of information between. View the fingerprint of a key, after confirming the key is authentic, sign the key. Gpg, or gnu privacy guard, is a public key cryptography implementation. You’ll see that it only takes 1 step to decrypt and verify, as well. It takes 1 step to encrypt and sign. Given a signed. Sign Message Gpg.
From coderscay.blogspot.com
How to Encrypt and Decrypt the files and text using GPG/PGP tool Sign Message Gpg It takes 1 step to encrypt and sign. You’ll see that it only takes 1 step to decrypt and verify, as well. Given a signed document, you can either check the signature or check the signature and recover the original document. This allows for the secure transmission of information between. View the fingerprint of a key, after confirming the key. Sign Message Gpg.
From olporsignal.weebly.com
How does gpg mail work olporsignal Sign Message Gpg View the fingerprint of a key, after confirming the key is authentic, sign the key. Given a signed document, you can either check the signature or check the signature and recover the original document. Gpg, or gnu privacy guard, is a public key cryptography implementation. You’ll see that it only takes 1 step to decrypt and verify, as well. It. Sign Message Gpg.
From www.cloudwithchris.com
Using GPG Keys to sign Git Commits Part 3 Cloud With Chris Sign Message Gpg View the fingerprint of a key, after confirming the key is authentic, sign the key. This allows for the secure transmission of information between. Gpg, or gnu privacy guard, is a public key cryptography implementation. Given a signed document, you can either check the signature or check the signature and recover the original document. You’ll see that it only takes. Sign Message Gpg.