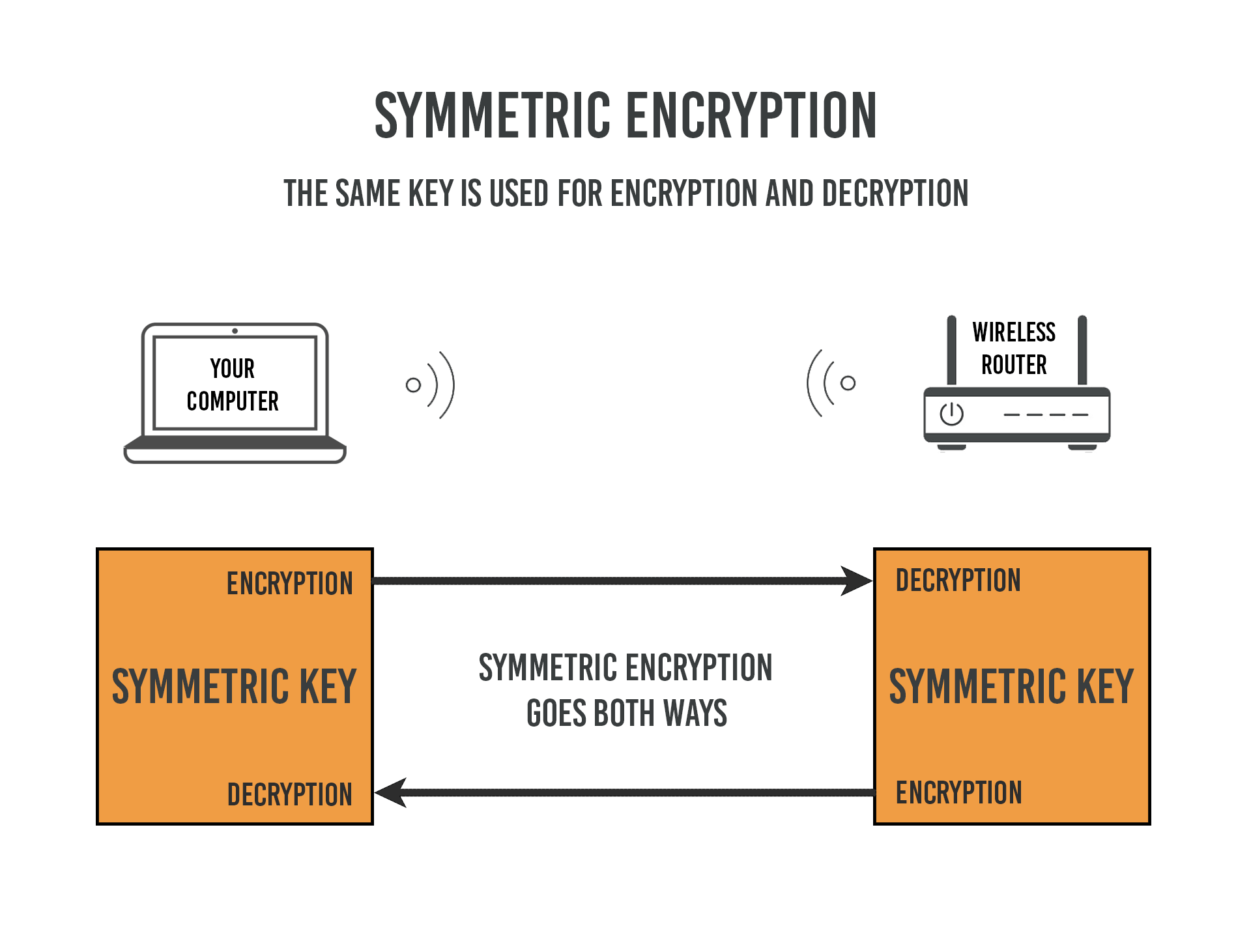
Wireless Encryption Keys . the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. Wireless network capacity planning and requirements. there are several important differences between the three wireless encryption standards. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. Best practices for wireless network security. The 4 different types of.
from tiptopsecurity.com
the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. there are several important differences between the three wireless encryption standards. The 4 different types of. Wireless network capacity planning and requirements. Best practices for wireless network security.
How Does HTTPS Work? RSA Encryption Explained « TipTopSecurity
Wireless Encryption Keys Best practices for wireless network security. there are several important differences between the three wireless encryption standards. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. Best practices for wireless network security. The 4 different types of. Wireless network capacity planning and requirements. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or.
From www.springboard.com
Cryptography Basics Ins and Outs of Encryption Springboard Blog Wireless Encryption Keys the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. there are several important differences between the three wireless encryption standards. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or.. Wireless Encryption Keys.
From www.clickssl.net
What is Public Key Encryption and How Does It Works? Wireless Encryption Keys Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. Best practices for wireless network security. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or.. Wireless Encryption Keys.
From technology.gov.capital
Encryption keys Technology.Gov.Capital Wireless Encryption Keys there are several important differences between the three wireless encryption standards. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the.. Wireless Encryption Keys.
From www.grandmetric.com
WiFi Security Evolution How we ended up in WPA3? Wireless Encryption Keys Best practices for wireless network security. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. Wireless network capacity planning and requirements. The 4 different types of. the network security key is protected with encryption using one of the following. Wireless Encryption Keys.
From www.exam4training.com
Which type of wireless encryption is used for WPA2 in preshared key Wireless Encryption Keys Best practices for wireless network security. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. there are several important differences between the three wireless encryption standards. The 4 different types of. Wireless network capacity planning and requirements. the. Wireless Encryption Keys.
From www.assured.enterprises
data encryption key graphic big Assured Enterprises Serious Wireless Encryption Keys the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. The 4 different types of. there are several important differences between the three wireless encryption standards. Wireless network capacity planning and requirements. Best practices for wireless network security. the psk that you see with wpa2 and wpa is basically. Wireless Encryption Keys.
From aim4truth.org
All about those encryption keys American Intelligence Media Wireless Encryption Keys the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. there are several important differences between the three wireless encryption standards. Best practices for wireless network security. Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically the wireless network key that. Wireless Encryption Keys.
From study.com
Types of Encryption Keys Lesson Wireless Encryption Keys The 4 different types of. there are several important differences between the three wireless encryption standards. Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. the network security key is protected with. Wireless Encryption Keys.
From www.themarketinginfo.com
What are Encryption Keys? Definition, Kinds, and More 2021 Wireless Encryption Keys there are several important differences between the three wireless encryption standards. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. Best practices for wireless network security. The 4 different types of. Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically. Wireless Encryption Keys.
From webapi.bu.edu
💋 ____ is used to encrypt and authenticate network traffic. encryption Wireless Encryption Keys Best practices for wireless network security. there are several important differences between the three wireless encryption standards. The 4 different types of. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. the psk that you see with wpa2 and wpa is basically the wireless network key that you. Wireless Encryption Keys.
From www.youtube.com
Wireless Encryption options and RADIUS YouTube Wireless Encryption Keys there are several important differences between the three wireless encryption standards. The 4 different types of. Best practices for wireless network security. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. the network security key is protected with. Wireless Encryption Keys.
From www.avg.com
The Ultimate Guide to Data Encryption Protect Your Data AVG Wireless Encryption Keys Best practices for wireless network security. Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. The 4 different types of. the network security key is protected with encryption using one of the following. Wireless Encryption Keys.
From www.virtru.com
Why Hosting Your Own Encryption Keys is Better for Data Security Wireless Encryption Keys The 4 different types of. there are several important differences between the three wireless encryption standards. Best practices for wireless network security. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically. Wireless Encryption Keys.
From www.eeworldonline.com
The basics of WiFi security and encryption Electrical Engineering Wireless Encryption Keys The 4 different types of. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. there are several important differences between the three wireless encryption standards. Best practices for wireless network security. the psk that you see with wpa2 and wpa is basically the wireless network key that you. Wireless Encryption Keys.
From medium.com
What are encryption keys and how do they work? 🔐 CodeClan Medium Wireless Encryption Keys Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. there are several important differences between the three wireless encryption standards. Best practices for wireless network security. the network security key is protected. Wireless Encryption Keys.
From mailtrap.io
Email Encryption AllinOne Guide Mailtrap Blog Wireless Encryption Keys the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. there are several important differences between the three wireless encryption standards. Wireless network capacity planning and requirements. Best practices for wireless network security. the network security key is protected. Wireless Encryption Keys.
From www.twilio.com
What is Public Key Cryptography? Twilio Wireless Encryption Keys Wireless network capacity planning and requirements. there are several important differences between the three wireless encryption standards. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. The 4 different types of. Best practices for wireless network security. the. Wireless Encryption Keys.
From www.ipswitch.com
Sharing Encryption Keys A Practical Example With GPG Ipswitch Wireless Encryption Keys Wireless network capacity planning and requirements. there are several important differences between the three wireless encryption standards. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. Best practices for wireless network security. the psk that you see with wpa2 and wpa is basically the wireless network key that. Wireless Encryption Keys.
From divyendra.com
Public Key Cryptography Basics Site Reliability Engineering Wireless Encryption Keys the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. The 4 different types of. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. Wireless network capacity planning and requirements. Best. Wireless Encryption Keys.
From learn.g2.com
How Public Key Encryption Ensures Data Integrity Wireless Encryption Keys there are several important differences between the three wireless encryption standards. Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. The 4 different types of. the network security key is protected with. Wireless Encryption Keys.
From chandabdulsalam.medium.com
AES Symmetric Encryption with ClientServer Model (Typescript — C Wireless Encryption Keys Wireless network capacity planning and requirements. there are several important differences between the three wireless encryption standards. Best practices for wireless network security. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. the network security key is protected. Wireless Encryption Keys.
From www.thesslstore.com
Cryptographic Keys 101 What They Are & How They Secure Data Hashed Wireless Encryption Keys Best practices for wireless network security. The 4 different types of. there are several important differences between the three wireless encryption standards. Wireless network capacity planning and requirements. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. the psk that you see with wpa2 and wpa is basically. Wireless Encryption Keys.
From www.lifewire.com
How to Encrypt Your Wireless Network Wireless Encryption Keys the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. The 4 different types of. Wireless network capacity planning and requirements. Best practices for wireless network security. there are several important differences between the three wireless encryption standards. the psk that you see with wpa2 and wpa is basically. Wireless Encryption Keys.
From atos.net
Protecting your sensitive data with double key encryption Atos Wireless Encryption Keys Best practices for wireless network security. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. Wireless network capacity planning and requirements. The 4 different types of. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to. Wireless Encryption Keys.
From wyzguyscybersecurity.com
Public Key Encryption Explained WyzGuys Cybersecurity Wireless Encryption Keys the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. Best practices for wireless network security. there are several important differences. Wireless Encryption Keys.
From medium.com
What are encryption keys and how do they work? 🔐 CodeClan Medium Wireless Encryption Keys Wireless network capacity planning and requirements. The 4 different types of. there are several important differences between the three wireless encryption standards. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. the psk that you see with wpa2 and wpa is basically the wireless network key that you. Wireless Encryption Keys.
From www.okta.com
Public Key Encryption What Is Public Cryptography? Okta AU & NZ Wireless Encryption Keys the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. Best practices for wireless network security. The 4 different types of. Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to. Wireless Encryption Keys.
From cheapsslweb.com
What is AES Encryption and How it Works? [Detailed Guide] Wireless Encryption Keys Wireless network capacity planning and requirements. Best practices for wireless network security. The 4 different types of. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. the network security key is protected with encryption using one of the following. Wireless Encryption Keys.
From www.slideteam.net
Wireless Encryption Types Ppt Powerpoint Presentation Pictures Wireless Encryption Keys the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. Wireless network capacity planning and requirements. there are several important differences between the three wireless encryption standards. The 4 different types of. the network security key is protected with. Wireless Encryption Keys.
From adroitacademy.com
How are the encryption key shared between devices Blog Adroit Wireless Encryption Keys the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. The 4 different types of. Best practices for wireless network security. there are several important differences between the three wireless encryption standards. Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically. Wireless Encryption Keys.
From brightlineit.com
Understanding Encryption Key Management for Businesses Brightline Wireless Encryption Keys the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. Wireless network capacity planning and requirements. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. The 4 different types of. . Wireless Encryption Keys.
From www.techtarget.com
What is Shared Key Authentication, and how does it work? Wireless Encryption Keys Wireless network capacity planning and requirements. the network security key is protected with encryption using one of the following standards, wep, wpa, wpa2, or. there are several important differences between the three wireless encryption standards. The 4 different types of. Best practices for wireless network security. the psk that you see with wpa2 and wpa is basically. Wireless Encryption Keys.
From www.cisco.com
What Is Encryption? Explanation and Types Cisco Wireless Encryption Keys there are several important differences between the three wireless encryption standards. Wireless network capacity planning and requirements. Best practices for wireless network security. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. the network security key is protected. Wireless Encryption Keys.
From stormagic.com
Encryption A Beginner's Guide Start Learning with StorMagic Wireless Encryption Keys The 4 different types of. Best practices for wireless network security. there are several important differences between the three wireless encryption standards. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. the network security key is protected with. Wireless Encryption Keys.
From tiptopsecurity.com
How Does HTTPS Work? RSA Encryption Explained « TipTopSecurity Wireless Encryption Keys there are several important differences between the three wireless encryption standards. The 4 different types of. the psk that you see with wpa2 and wpa is basically the wireless network key that you have to enter when connecting to a wireless network for the. Best practices for wireless network security. Wireless network capacity planning and requirements. the. Wireless Encryption Keys.