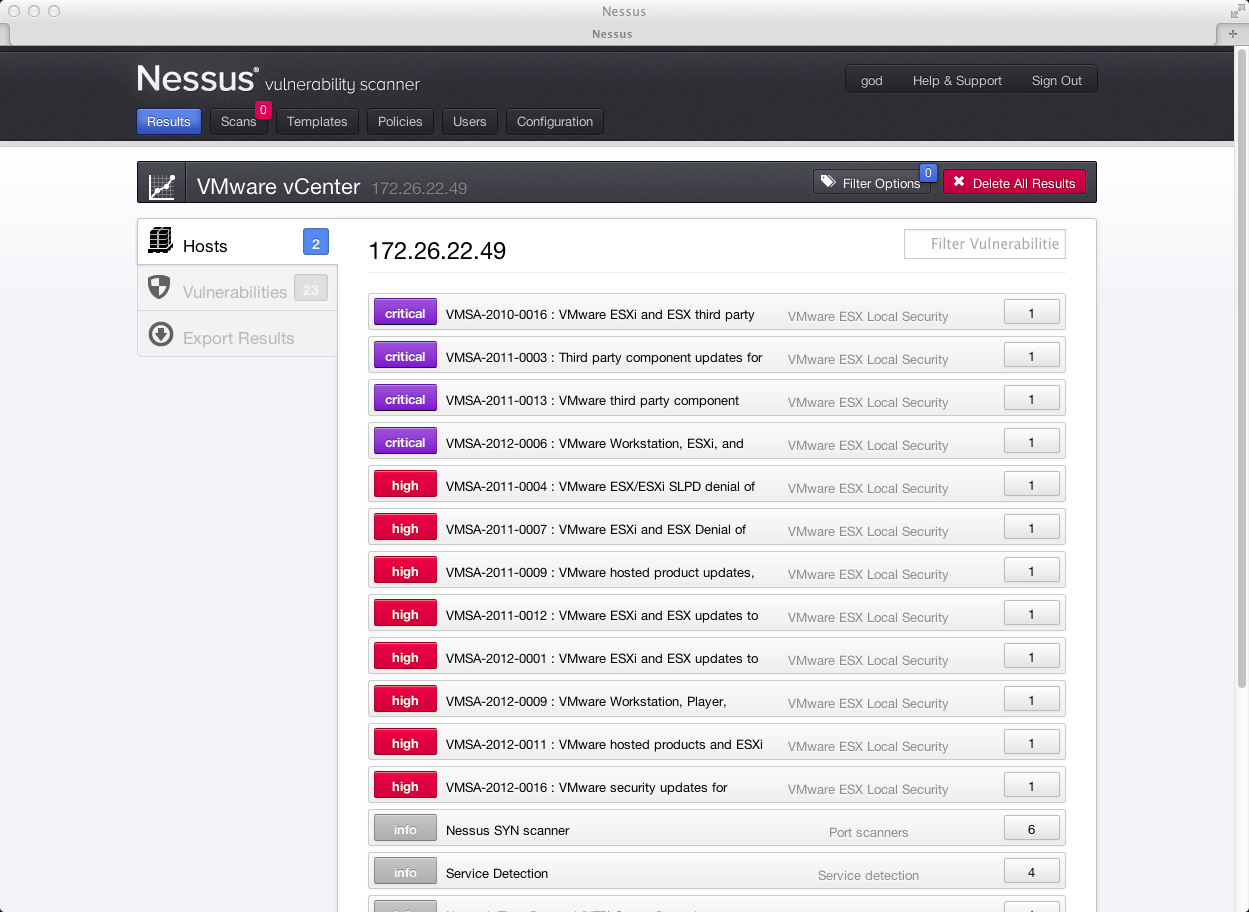
Security Scan Tenable . Tenable recommends running credentialed scans whenever possible. A deeply divided approach to seeing and doing. Clear, actionable insight into data with highly customizable dashboards,. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. You can perform two types of scans using tenable products: Credentialed scans provide your organization with a more accurate snapshot of. There may be additional settings in. Immediate visibility into your network with unlimited nessus scanners. Tenable one solves the central challenge of modern security: Tenable nessus professional will help automate the. This allows the user to evaluate and secure their systems. This article outlines the process of a vulnerability scan primarily in nessus. Tenable nessus is the most comprehensive vulnerability scanner on the market today. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. Discovery scans and assessment scans.
from www.tenable.com
This article outlines the process of a vulnerability scan primarily in nessus. Tenable one solves the central challenge of modern security: Tenable nessus is the most comprehensive vulnerability scanner on the market today. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. This allows the user to evaluate and secure their systems. There may be additional settings in. Clear, actionable insight into data with highly customizable dashboards,. Immediate visibility into your network with unlimited nessus scanners. Tenable nessus professional will help automate the. A deeply divided approach to seeing and doing.
Nessus Features Tenable Network Security
Security Scan Tenable There may be additional settings in. Tenable recommends running credentialed scans whenever possible. Clear, actionable insight into data with highly customizable dashboards,. This article outlines the process of a vulnerability scan primarily in nessus. This allows the user to evaluate and secure their systems. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. Tenable nessus is the most comprehensive vulnerability scanner on the market today. Immediate visibility into your network with unlimited nessus scanners. Tenable one solves the central challenge of modern security: Credentialed scans provide your organization with a more accurate snapshot of. A deeply divided approach to seeing and doing. You can perform two types of scans using tenable products: Discovery scans and assessment scans. Tenable nessus professional will help automate the. There may be additional settings in.
From advisionit.com
Tenable Nessus Vulnerability Assessment Scanner Security Scan Tenable This article outlines the process of a vulnerability scan primarily in nessus. Immediate visibility into your network with unlimited nessus scanners. Discovery scans and assessment scans. Tenable nessus professional will help automate the. A deeply divided approach to seeing and doing. Tenable one solves the central challenge of modern security: You can perform two types of scans using tenable products:. Security Scan Tenable.
From avleonov.com
Tenable SecurityCenter and its API Alexander V. Leonov Security Scan Tenable This allows the user to evaluate and secure their systems. Discovery scans and assessment scans. Tenable nessus professional will help automate the. Credentialed scans provide your organization with a more accurate snapshot of. Tenable recommends running credentialed scans whenever possible. A deeply divided approach to seeing and doing. This article outlines the process of a vulnerability scan primarily in nessus.. Security Scan Tenable.
From www.tenable.com
How to Run a Vulnerability Scan with Nessus Tenable Blog Security Scan Tenable Credentialed scans provide your organization with a more accurate snapshot of. Tenable one solves the central challenge of modern security: Tenable nessus is the most comprehensive vulnerability scanner on the market today. A deeply divided approach to seeing and doing. This article outlines the process of a vulnerability scan primarily in nessus. Vulnerability assessment is a process that identifies and. Security Scan Tenable.
From www.tenable.com
Personalizing Your Tenable.io Scans Blog Tenable® Security Scan Tenable Immediate visibility into your network with unlimited nessus scanners. Credentialed scans provide your organization with a more accurate snapshot of. A deeply divided approach to seeing and doing. This allows the user to evaluate and secure their systems. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for. Security Scan Tenable.
From aws.amazon.com
AWS Marketplace Tenable Core + Tenable.io App Scanning Security Scan Tenable A deeply divided approach to seeing and doing. You can perform two types of scans using tenable products: There may be additional settings in. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. Security content automation protocol (scap) scan is method for using known standards to. Security Scan Tenable.
From www.tenable.com
Nessus Vulnerability Scanner Network Security Solution Tenable® Security Scan Tenable There may be additional settings in. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. Tenable nessus professional will help automate the. Discovery scans and assessment scans. You can perform two types of scans using tenable products: Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning. Security Scan Tenable.
From docs.tenable.com
Add a Tenable Vulnerability Management Scanner (Tenable Security Center Security Scan Tenable There may be additional settings in. You can perform two types of scans using tenable products: Tenable nessus is the most comprehensive vulnerability scanner on the market today. A deeply divided approach to seeing and doing. This article outlines the process of a vulnerability scan primarily in nessus. Credentialed scans provide your organization with a more accurate snapshot of. Vulnerability. Security Scan Tenable.
From avleonov.com
Tenable SecurityCenter and its API Alexander V. Leonov Security Scan Tenable This article outlines the process of a vulnerability scan primarily in nessus. This allows the user to evaluate and secure their systems. Credentialed scans provide your organization with a more accurate snapshot of. Immediate visibility into your network with unlimited nessus scanners. Tenable nessus professional will help automate the. A deeply divided approach to seeing and doing. Vulnerability assessment is. Security Scan Tenable.
From docs.tenable.com
Get Started with Tenable App Scanning (Tenable App Scanning) Security Scan Tenable Tenable nessus is the most comprehensive vulnerability scanner on the market today. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. You can perform two types of scans using tenable products: Discovery scans and assessment scans. Tenable recommends running credentialed scans whenever possible. Tenable nessus professional. Security Scan Tenable.
From www.youtube.com
Nessus Professional by Tenable Network Security Technical Overview Security Scan Tenable Immediate visibility into your network with unlimited nessus scanners. Clear, actionable insight into data with highly customizable dashboards,. Credentialed scans provide your organization with a more accurate snapshot of. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. Tenable nessus professional will help automate the. Tenable nessus is the most comprehensive. Security Scan Tenable.
From thehackernews.com
Tenable Release Nessus 5.0 vulnerability scanner Security Scan Tenable This allows the user to evaluate and secure their systems. Tenable recommends running credentialed scans whenever possible. Tenable one solves the central challenge of modern security: A deeply divided approach to seeing and doing. This article outlines the process of a vulnerability scan primarily in nessus. Tenable nessus is the most comprehensive vulnerability scanner on the market today. Security content. Security Scan Tenable.
From www.infoguard.ch
Tenable Network Security Vulnerability Management InfoGuard Security Scan Tenable Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. Tenable nessus professional will help automate the. There may be additional settings in. A deeply divided approach to seeing and doing. You can perform two types of scans using tenable products: Vulnerability assessment is a process that identifies and evaluates network vulnerabilities. Security Scan Tenable.
From www.youtube.com
Launch a Credentialed Scan in Tenable.io YouTube Security Scan Tenable Tenable one solves the central challenge of modern security: You can perform two types of scans using tenable products: This article outlines the process of a vulnerability scan primarily in nessus. This allows the user to evaluate and secure their systems. There may be additional settings in. Discovery scans and assessment scans. Credentialed scans provide your organization with a more. Security Scan Tenable.
From github.com
GitHub tenable/containersecurityaction Tenable's Container Security Scan Tenable This article outlines the process of a vulnerability scan primarily in nessus. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. You can perform two types of scans using tenable products: Tenable one solves the central challenge of modern security: This allows the user to evaluate. Security Scan Tenable.
From avleonov.com
Tenable Nessus registration, installation, scanning and reporting Security Scan Tenable There may be additional settings in. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. Credentialed scans provide your organization with a more accurate snapshot of. Tenable nessus professional will help automate the. Discovery scans and assessment scans. Tenable recommends running credentialed scans whenever possible. Security. Security Scan Tenable.
From www.tenable.com
PCI Internal Vulnerability Scanning Report SC Report Template Tenable™ Security Scan Tenable A deeply divided approach to seeing and doing. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. You can perform two types of scans using tenable products: Tenable nessus is the most comprehensive vulnerability scanner on the market today. Tenable nessus professional will help automate the. This article outlines the process. Security Scan Tenable.
From docs.tenable.com
Tenable Security Center Architecture (Tenable Security Center 6.1.x) Security Scan Tenable Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. Tenable recommends running credentialed scans whenever possible. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. You can perform two types of scans using tenable products: Tenable one. Security Scan Tenable.
From www.e-spincorp.com
Tenable Vulnerability Management (formerly Tenable.io) ESPIN Group Security Scan Tenable Credentialed scans provide your organization with a more accurate snapshot of. Tenable nessus is the most comprehensive vulnerability scanner on the market today. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. This allows the user to evaluate and secure their systems. Tenable one solves the central challenge of modern security:. Security Scan Tenable.
From www.youtube.com
Perform a Malware Scan in Tenable.sc YouTube Security Scan Tenable A deeply divided approach to seeing and doing. You can perform two types of scans using tenable products: Tenable one solves the central challenge of modern security: Tenable nessus is the most comprehensive vulnerability scanner on the market today. This article outlines the process of a vulnerability scan primarily in nessus. Clear, actionable insight into data with highly customizable dashboards,.. Security Scan Tenable.
From www.youtube.com
Basic Scan Results Analysis in Tenable.sc YouTube Security Scan Tenable Immediate visibility into your network with unlimited nessus scanners. Tenable nessus professional will help automate the. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. Credentialed scans provide your organization with a more accurate snapshot of. Discovery scans and assessment scans. Vulnerability assessment is a process that identifies and evaluates network. Security Scan Tenable.
From www.youtube.com
Launch a Compliance Scan in Tenable.sc YouTube Security Scan Tenable Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. Tenable recommends running credentialed scans whenever possible. Tenable nessus professional will help automate the. Clear, actionable insight into data with highly customizable dashboards,. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire. Security Scan Tenable.
From www.tenable.com
Endpoint Security with Nessus® Agents Blog Tenable® Security Scan Tenable Credentialed scans provide your organization with a more accurate snapshot of. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. Tenable nessus professional will help automate the. There may be additional settings in. Tenable one solves the central challenge of modern security: This allows the user to evaluate and secure their. Security Scan Tenable.
From www.youtube.com
Launch a Credentialed Scan in Tenable.sc YouTube Security Scan Tenable Clear, actionable insight into data with highly customizable dashboards,. This article outlines the process of a vulnerability scan primarily in nessus. A deeply divided approach to seeing and doing. This allows the user to evaluate and secure their systems. Tenable nessus is the most comprehensive vulnerability scanner on the market today. Discovery scans and assessment scans. Tenable recommends running credentialed. Security Scan Tenable.
From www.tenable.com
Nessus Vulnerability Scanner Network Security Solution Tenable® Security Scan Tenable This allows the user to evaluate and secure their systems. Discovery scans and assessment scans. Tenable nessus professional will help automate the. Tenable recommends running credentialed scans whenever possible. Credentialed scans provide your organization with a more accurate snapshot of. Immediate visibility into your network with unlimited nessus scanners. You can perform two types of scans using tenable products: Tenable. Security Scan Tenable.
From fr.tenable.com
ACAS Scan Quick Credential Debug Scan Tenable® Security Scan Tenable You can perform two types of scans using tenable products: A deeply divided approach to seeing and doing. Tenable recommends running credentialed scans whenever possible. Immediate visibility into your network with unlimited nessus scanners. This allows the user to evaluate and secure their systems. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring. Security Scan Tenable.
From www.youtube.com
Perform a Malware Scan in Tenable.io YouTube Security Scan Tenable Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. This article outlines the process of a vulnerability scan primarily in nessus. Tenable nessus is the most comprehensive vulnerability. Security Scan Tenable.
From www.youtube.com
Tenable SecurityCenter Technical Overview YouTube Security Scan Tenable Credentialed scans provide your organization with a more accurate snapshot of. This allows the user to evaluate and secure their systems. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. Discovery scans and assessment scans. Immediate visibility into your network with unlimited nessus scanners. Tenable recommends. Security Scan Tenable.
From docs.tenable.com
Scan Zones (Tenable Security Center 6.4.x) Security Scan Tenable Immediate visibility into your network with unlimited nessus scanners. This article outlines the process of a vulnerability scan primarily in nessus. Tenable recommends running credentialed scans whenever possible. Tenable one solves the central challenge of modern security: Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks.. Security Scan Tenable.
From www.tenable.com
Credentialed Windows Scanning SC Dashboard Tenable® Security Scan Tenable You can perform two types of scans using tenable products: Discovery scans and assessment scans. Tenable nessus is the most comprehensive vulnerability scanner on the market today. Tenable nessus professional will help automate the. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. This allows the user to evaluate and secure. Security Scan Tenable.
From www.tenable.com
Industrial Security Vulnerability Scanner Tenable® Security Scan Tenable Immediate visibility into your network with unlimited nessus scanners. Clear, actionable insight into data with highly customizable dashboards,. You can perform two types of scans using tenable products: Credentialed scans provide your organization with a more accurate snapshot of. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. Tenable nessus is. Security Scan Tenable.
From advisionit.com
Tenable Nessus Vulnerability Assessment Scanner Security Scan Tenable There may be additional settings in. This allows the user to evaluate and secure their systems. Tenable recommends running credentialed scans whenever possible. Discovery scans and assessment scans. You can perform two types of scans using tenable products: This article outlines the process of a vulnerability scan primarily in nessus. Immediate visibility into your network with unlimited nessus scanners. Tenable. Security Scan Tenable.
From www.jcount.com
Tenable Network Security Raises 250M Security Scan Tenable Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. You can perform two types of scans using tenable products: Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. Clear, actionable insight into data with highly customizable dashboards,.. Security Scan Tenable.
From www.tenable.com
Nessus Features Tenable Network Security Security Scan Tenable A deeply divided approach to seeing and doing. Clear, actionable insight into data with highly customizable dashboards,. Security content automation protocol (scap) scan is method for using known standards to run vulnerability and compliance scans. This allows the user to evaluate and secure their systems. Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and. Security Scan Tenable.
From docs.tenable.com
Dashboard (Tenable Nessus 10.8) Security Scan Tenable You can perform two types of scans using tenable products: Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. Tenable nessus professional will help automate the. Immediate visibility into your network with unlimited nessus scanners. There may be additional settings in. Tenable one solves the central. Security Scan Tenable.
From www.youtube.com
Launch a Compliance Scan in Tenable.io YouTube Security Scan Tenable This article outlines the process of a vulnerability scan primarily in nessus. Clear, actionable insight into data with highly customizable dashboards,. There may be additional settings in. Discovery scans and assessment scans. Immediate visibility into your network with unlimited nessus scanners. Tenable one solves the central challenge of modern security: Tenable recommends running credentialed scans whenever possible. Tenable nessus is. Security Scan Tenable.