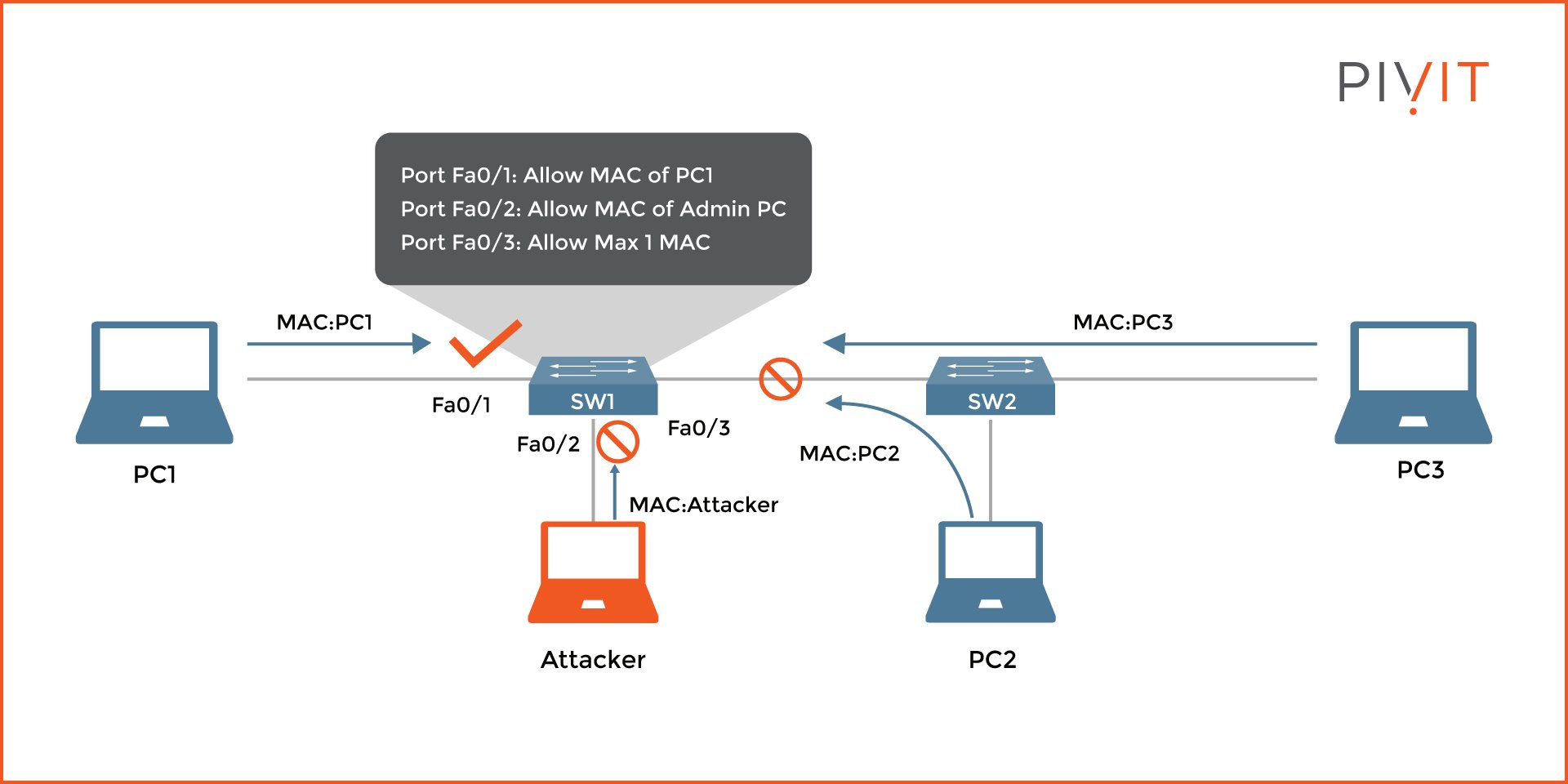
Port Security Cheat Sheet . It is used by network administrators and it professionals to help. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. 50 common ports you should know. 127 rows common ports and protocols cheat sheet. The following tables cover services (and malware) that use common tcp. The ports and protocols are just one of the topics you’ll need. So, we created this concise cheat sheet of common network ports and their.
from info.pivitglobal.com
By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. So, we created this concise cheat sheet of common network ports and their. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. The following tables cover services (and malware) that use common tcp. 127 rows common ports and protocols cheat sheet. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. The ports and protocols are just one of the topics you’ll need. It is used by network administrators and it professionals to help. 50 common ports you should know.
MustHave Port Security Simple but Efficient Layer 2 Protection
Port Security Cheat Sheet By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. 50 common ports you should know. 127 rows common ports and protocols cheat sheet. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. The following tables cover services (and malware) that use common tcp. It is used by network administrators and it professionals to help. So, we created this concise cheat sheet of common network ports and their. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. The ports and protocols are just one of the topics you’ll need.
From ja.scribd.com
Security+ Acronyms Cheat Sheet Port Security Cheat Sheet The following tables cover services (and malware) that use common tcp. 50 common ports you should know. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. 127 rows common ports. Port Security Cheat Sheet.
From getcheatsheet.blogspot.com
Security Plus Port Cheat Sheet Cheat Sheet Port Security Cheat Sheet The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. It is used by network administrators and it professionals to help. So, we created this. Port Security Cheat Sheet.
From medium.com
5 Minutes to Master TCP/UDP Protocol’s, along with server Firewall Port Security Cheat Sheet The ports and protocols are just one of the topics you’ll need. So, we created this concise cheat sheet of common network ports and their. It is used by network administrators and it professionals to help. 127 rows common ports and protocols cheat sheet. By using port security, users can limit the number of mac addresses that can be learned. Port Security Cheat Sheet.
From www.pdffiller.com
Security Plus Cheat Sheet Fill Online, Printable, Fillable, Blank Port Security Cheat Sheet The ports and protocols are just one of the topics you’ll need. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. 127 rows common ports and protocols cheat sheet. 50 common ports you should know. It’s a pain trying to memorize port numbers and their. Port Security Cheat Sheet.
From www.vrogue.co
Common Ports Cheat Sheet Awesome Mon Cyberkraft On Twitter I Know It S Port Security Cheat Sheet 127 rows common ports and protocols cheat sheet. The following tables cover services (and malware) that use common tcp. It is used by network administrators and it professionals to help. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. It’s a pain trying to memorize. Port Security Cheat Sheet.
From www.studypool.com
SOLUTION Common ports cheat sheet station x v1 Studypool Port Security Cheat Sheet By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. So, we created this concise cheat sheet of common network ports and their. It is used by network administrators and it professionals to help. 127 rows common ports and protocols cheat sheet. 50 common ports you. Port Security Cheat Sheet.
From subscription.packtpub.com
Secure Protocols and Their Use Cases CompTIA Security+ SY0601 Port Security Cheat Sheet The following tables cover services (and malware) that use common tcp. The ports and protocols are just one of the topics you’ll need. 127 rows common ports and protocols cheat sheet. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. It is used by network. Port Security Cheat Sheet.
From www.vrogue.co
Common Tcp Port Cheat Sheet Vrogue vrogue.co Port Security Cheat Sheet The following tables cover services (and malware) that use common tcp. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. The ports and protocols are just one of the topics you’ll need. By. Port Security Cheat Sheet.
From www.scribd.com
Cyberkraft Security 601 Ports and Protocols Reference Sheet PDF Port Security Cheat Sheet 50 common ports you should know. 127 rows common ports and protocols cheat sheet. So, we created this concise cheat sheet of common network ports and their. It is used by network administrators and it professionals to help. The ports and protocols are just one of the topics you’ll need. The common ports cheat sheet is a reference guide that. Port Security Cheat Sheet.
From www.pinterest.com
FTP Ports in 2021 Cyber security technology, Cisco networking, Ccna Port Security Cheat Sheet The ports and protocols are just one of the topics you’ll need. So, we created this concise cheat sheet of common network ports and their. 127 rows common ports and protocols cheat sheet. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. 50 common ports. Port Security Cheat Sheet.
From ipwithease.com
Common TCP/IP Well Known Port Numbers IP With Ease Port Security Cheat Sheet 127 rows common ports and protocols cheat sheet. 50 common ports you should know. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. The. Port Security Cheat Sheet.
From dat.perueduca.edu.pe
Security+ Ports Cheat Sheet Printable Templates Free Port Security Cheat Sheet 50 common ports you should know. The ports and protocols are just one of the topics you’ll need. 127 rows common ports and protocols cheat sheet. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. The following tables cover services (and malware) that use common. Port Security Cheat Sheet.
From hackeone.blogspot.com
TCP/IP common Port's cheet sheet HaCkeOne Cyber security News Port Security Cheat Sheet It is used by network administrators and it professionals to help. 50 common ports you should know. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. 127 rows common ports and protocols cheat sheet. The following tables cover services (and malware) that use common tcp. So, we created. Port Security Cheat Sheet.
From fitecgltzw.blogspot.com
Common Ports Cheat Sheet Security Ports Cheat Sheet Docsity Tcp/ip Port Security Cheat Sheet 50 common ports you should know. So, we created this concise cheat sheet of common network ports and their. The ports and protocols are just one of the topics you’ll need. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. The following tables cover services (and malware) that use common tcp. The common ports. Port Security Cheat Sheet.
From www.scribd.com
Common Ports Cheat Sheet A Comprehensive Guide to WellKnown Ports Port Security Cheat Sheet It’s a pain trying to memorize port numbers and their corresponding service names and protocols. The ports and protocols are just one of the topics you’ll need. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. The common ports cheat sheet is a reference guide. Port Security Cheat Sheet.
From studylib.net
Common Ports Cheat Sheet The Ultimate Ports & Protocols List Port Security Cheat Sheet It is used by network administrators and it professionals to help. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. 50 common ports you should know. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. The common ports cheat. Port Security Cheat Sheet.
From getcheatsheet.blogspot.com
Security Plus Port Cheat Sheet Cheat Sheet Port Security Cheat Sheet The following tables cover services (and malware) that use common tcp. The ports and protocols are just one of the topics you’ll need. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. By using port security, users can limit the number of mac addresses that can be learned. Port Security Cheat Sheet.
From www.stationx.net
Common Ports Cheat Sheet The Ultimate Ports & Protocols List Port Security Cheat Sheet The following tables cover services (and malware) that use common tcp. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. The ports and protocols. Port Security Cheat Sheet.
From www.pinterest.co.uk
Common Ports Cheat Sheet Networking basics, Computer network Port Security Cheat Sheet 127 rows common ports and protocols cheat sheet. The ports and protocols are just one of the topics you’ll need. The following tables cover services (and malware) that use common tcp. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. So, we created this concise. Port Security Cheat Sheet.
From mungfali.com
OSI Model Table Port Security Cheat Sheet So, we created this concise cheat sheet of common network ports and their. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. 50 common ports you should know. 127 rows common ports and protocols cheat sheet. The following tables cover services (and malware) that use common tcp. The. Port Security Cheat Sheet.
From www.stationx.net
Common Ports Cheat Sheet The Ultimate List Port Security Cheat Sheet The following tables cover services (and malware) that use common tcp. 127 rows common ports and protocols cheat sheet. So, we created this concise cheat sheet of common network ports and their. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. It’s a pain trying to memorize port. Port Security Cheat Sheet.
From info.pivitglobal.com
MustHave Port Security Simple but Efficient Layer 2 Protection Port Security Cheat Sheet 50 common ports you should know. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. The following tables cover services (and malware) that use common tcp. 127 rows common ports and protocols cheat sheet. It’s a pain trying to memorize port numbers and their corresponding service names and. Port Security Cheat Sheet.
From networkproguide.com
Common Ports Cheat Sheet NetworkProGuide Port Security Cheat Sheet 50 common ports you should know. The following tables cover services (and malware) that use common tcp. 127 rows common ports and protocols cheat sheet. So, we created this concise cheat sheet of common network ports and their. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. The ports and protocols are just one. Port Security Cheat Sheet.
From cybersecurityleituras.blogspot.com
Cyber Security Leituras, traduções e links wellknown ports Port Security Cheat Sheet 127 rows common ports and protocols cheat sheet. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. The common ports cheat sheet is a reference guide that provides a list. Port Security Cheat Sheet.
From blog.servermania.com
How does Port Security Work in a Network? ServerMania Port Security Cheat Sheet So, we created this concise cheat sheet of common network ports and their. 50 common ports you should know. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. The following. Port Security Cheat Sheet.
From www.scribd.com
Common Tcp Port Cheat Sheet Port Security Cheat Sheet It’s a pain trying to memorize port numbers and their corresponding service names and protocols. So, we created this concise cheat sheet of common network ports and their. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. The following tables cover services (and malware) that use common tcp.. Port Security Cheat Sheet.
From www.stationx.net
List of Common Ports Cheat Sheet Port Security Cheat Sheet It’s a pain trying to memorize port numbers and their corresponding service names and protocols. 50 common ports you should know. By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. The common ports cheat sheet is a reference guide that provides a list of commonly. Port Security Cheat Sheet.
From fitecgltzw.blogspot.com
Common Ports Cheat Sheet Security Ports Cheat Sheet Docsity Tcp/ip Port Security Cheat Sheet The ports and protocols are just one of the topics you’ll need. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. It is used by network administrators and it professionals to help. 127 rows common ports and protocols cheat sheet. By using port security, users can limit the number of mac addresses that can. Port Security Cheat Sheet.
From mavink.com
Printable Port Number Chart Port Security Cheat Sheet The following tables cover services (and malware) that use common tcp. It is used by network administrators and it professionals to help. So, we created this concise cheat sheet of common network ports and their. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. 127 rows common ports. Port Security Cheat Sheet.
From www.vrogue.co
Simple Common Ports Cheat Sheet Mon Ports From Common vrogue.co Port Security Cheat Sheet By using port security, users can limit the number of mac addresses that can be learned to a port, set static mac addresses, and. 50 common ports you should know. So, we created this concise cheat sheet of common network ports and their. It’s a pain trying to memorize port numbers and their corresponding service names and protocols. It is. Port Security Cheat Sheet.
From getcheatsheet.blogspot.com
Security Plus Port Cheat Sheet Cheat Sheet Port Security Cheat Sheet So, we created this concise cheat sheet of common network ports and their. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. 50 common ports you should know. The ports and protocols are just one of the topics you’ll need. By using port security, users can limit the. Port Security Cheat Sheet.
From www.ccnaacademy.com
Port Number Cheatsheets Port Security Cheat Sheet It is used by network administrators and it professionals to help. So, we created this concise cheat sheet of common network ports and their. The ports and protocols are just one of the topics you’ll need. 50 common ports you should know. By using port security, users can limit the number of mac addresses that can be learned to a. Port Security Cheat Sheet.
From infosecwriteups.com
Series of Network Fundamentals 5 (Ports & Protocols),to get started in Port Security Cheat Sheet It’s a pain trying to memorize port numbers and their corresponding service names and protocols. 50 common ports you should know. It is used by network administrators and it professionals to help. The common ports cheat sheet is a reference guide that provides a list of commonly used ports and their associated protocols. The following tables cover services (and malware). Port Security Cheat Sheet.
From studylib.net
SecurityPortsandProtocolsReferenceSheet Port Security Cheat Sheet The following tables cover services (and malware) that use common tcp. The ports and protocols are just one of the topics you’ll need. 50 common ports you should know. It is used by network administrators and it professionals to help. 127 rows common ports and protocols cheat sheet. It’s a pain trying to memorize port numbers and their corresponding service. Port Security Cheat Sheet.
From fitecgltzw.blogspot.com
Common Ports Cheat Sheet Security Ports Cheat Sheet Docsity Tcp/ip Port Security Cheat Sheet It’s a pain trying to memorize port numbers and their corresponding service names and protocols. So, we created this concise cheat sheet of common network ports and their. 50 common ports you should know. The following tables cover services (and malware) that use common tcp. It is used by network administrators and it professionals to help. The common ports cheat. Port Security Cheat Sheet.