Function Level Access Control Example . There are a few ways that function level access controls can creep into an organization. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. By exploiting it, an attacker, who could be. How do missing function level access control exploits work? This granular control is essential for ensuring that users can. For example, function level access can be left. This video explains everything you need to know about missing function level access control, including the definition, impact, and.
from cie-group.com
For example, function level access can be left. This granular control is essential for ensuring that users can. How do missing function level access control exploits work? The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. This video explains everything you need to know about missing function level access control, including the definition, impact, and. There are a few ways that function level access controls can creep into an organization. By exploiting it, an attacker, who could be.
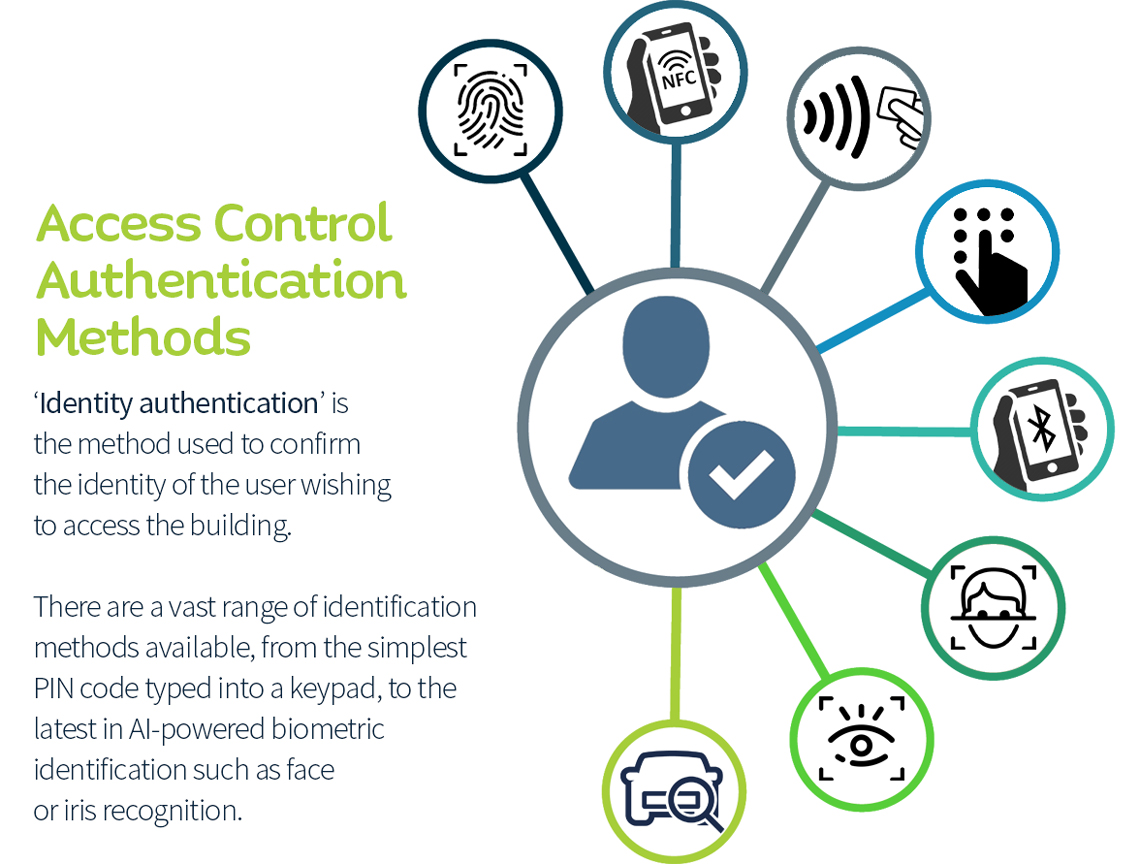
How to design an Access Control system
Function Level Access Control Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. This video explains everything you need to know about missing function level access control, including the definition, impact, and. How do missing function level access control exploits work? For example, function level access can be left. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. This granular control is essential for ensuring that users can. There are a few ways that function level access controls can creep into an organization. By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. By exploiting it, an attacker, who could be.
From slideplayer.com
Introduction to Information Security ppt download Function Level Access Control Example By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. For example, function level access can be left. There are a few ways that function level access controls can creep into an organization. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. This. Function Level Access Control Example.
From khatabook.com
What is Functional Level Strategy? Meaning & Examples Function Level Access Control Example This video explains everything you need to know about missing function level access control, including the definition, impact, and. There are a few ways that function level access controls can creep into an organization. By exploiting it, an attacker, who could be. For example, function level access can be left. This granular control is essential for ensuring that users can.. Function Level Access Control Example.
From www.collidu.com
Role Based Access Control PowerPoint and Google Slides Template PPT Function Level Access Control Example By exploiting it, an attacker, who could be. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. There are a few ways that function level access controls can creep into an organization. How do missing function level access control exploits work? By exploiting it, an attacker, who could be. Function Level Access Control Example.
From kemptechnologies.com
OWASP Top Ten Series Missing Function Level Access Control Kemp Function Level Access Control Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. This video explains everything you need to know about missing function level access control, including the definition, impact, and. There are a few ways that function level access controls can creep into an organization. By exploiting it, an attacker, who could be.. Function Level Access Control Example.
From www.c-sharpcorner.com
Missing Function Level Access Control And Its Prevention Mechanism Function Level Access Control Example There are a few ways that function level access controls can creep into an organization. This granular control is essential for ensuring that users can. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. How do missing function level access control exploits work? The missing function level access control vulnerability allows. Function Level Access Control Example.
From www.c-sharpcorner.com
Missing Function Level Access Control And Its Prevention Mechanism Function Level Access Control Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. This granular control is. Function Level Access Control Example.
From www.technochops.com
Missing Function Level Access Control (FLAC) With Examples Function Level Access Control Example For example, function level access can be left. How do missing function level access control exploits work? This granular control is essential for ensuring that users can. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. This video explains everything you need to know about missing function level access. Function Level Access Control Example.
From www.youtube.com
Missing Function Level Access Control Explained YouTube Function Level Access Control Example This granular control is essential for ensuring that users can. There are a few ways that function level access controls can creep into an organization. How do missing function level access control exploits work? By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. Missing function level access control, an owasp top. Function Level Access Control Example.
From www.youtube.com
OWASP Top 10 A7 Missing functionlevel access control YouTube Function Level Access Control Example The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. By exploiting it, an attacker, who could be. For example, function level access can be left. This video explains everything you need. Function Level Access Control Example.
From www.slideserve.com
PPT Drupal Security Awareness (2) PowerPoint Presentation, free Function Level Access Control Example By exploiting it, an attacker, who could be. There are a few ways that function level access controls can creep into an organization. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. This granular control is essential for ensuring that users can. By exploiting it, an attacker, who could. Function Level Access Control Example.
From www.youtube.com
Ejercicio Goat Missing Function Level Access Control YouTube Function Level Access Control Example For example, function level access can be left. By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. There are a few ways that function level access controls can creep into an organization. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them. Function Level Access Control Example.
From www.youtube.com
ZKBio CVSecurity Tutorial How to set Access Level (Access Control Function Level Access Control Example This granular control is essential for ensuring that users can. This video explains everything you need to know about missing function level access control, including the definition, impact, and. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. By exploiting it, an attacker, who could be. There are a. Function Level Access Control Example.
From www.youtube.com
OWASP TOP 10 A7 Missing Function Level Access Control YouTube Function Level Access Control Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. By exploiting it, an attacker, who could be. For example, function level access can be left. How do missing function level access control exploits work? This granular control is essential for ensuring that users can. There are a few ways that function. Function Level Access Control Example.
From www.semanticscholar.org
Research and Optimization on Access Control Mechanism of Linux Function Level Access Control Example How do missing function level access control exploits work? The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. This video explains everything you need to know about missing function level access control, including the definition, impact, and. By exploiting it, an attacker, who could be. There are a few. Function Level Access Control Example.
From www.slideserve.com
PPT application security Sebastian Lopienski CERN Deputy Computer Function Level Access Control Example By exploiting it, an attacker, who could be. How do missing function level access control exploits work? There are a few ways that function level access controls can creep into an organization. This granular control is essential for ensuring that users can. By exploiting it, an attacker, who could be an existing user of the application, is able to escalate.. Function Level Access Control Example.
From cie-group.com
How to design an Access Control system Function Level Access Control Example For example, function level access can be left. How do missing function level access control exploits work? By exploiting it, an attacker, who could be. This granular control is essential for ensuring that users can. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. There are a few ways that function. Function Level Access Control Example.
From jaycemeowcunningham.blogspot.com
What Function Describe the Uses of an Access Control List Function Level Access Control Example By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. By exploiting it, an attacker, who could be. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks. Function Level Access Control Example.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Function Level Access Control Example By exploiting it, an attacker, who could be. There are a few ways that function level access controls can creep into an organization. This video explains everything you need to know about missing function level access control, including the definition, impact, and. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets. Function Level Access Control Example.
From www.technochops.com
Missing Function Level Access Control (FLAC) With Examples Function Level Access Control Example There are a few ways that function level access controls can creep into an organization. For example, function level access can be left. This granular control is essential for ensuring that users can. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. How do missing function level access control exploits work?. Function Level Access Control Example.
From www.slideshare.net
19 owasp top 10 a7missing function level access control Function Level Access Control Example This granular control is essential for ensuring that users can. This video explains everything you need to know about missing function level access control, including the definition, impact, and. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. By exploiting it, an attacker, who could be. Missing function level. Function Level Access Control Example.
From www.youtube.com
What is Missing Function Level Access Control? OWASP Top 10 2013 Function Level Access Control Example For example, function level access can be left. This video explains everything you need to know about missing function level access control, including the definition, impact, and. How do missing function level access control exploits work? This granular control is essential for ensuring that users can. The missing function level access control vulnerability allows users to perform functions that should. Function Level Access Control Example.
From www.slideserve.com
PPT The OWASP Way PowerPoint Presentation, free download ID3040471 Function Level Access Control Example By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. This granular control is essential for ensuring that users can. There are a few ways that function level access controls can creep. Function Level Access Control Example.
From www.slideshare.net
A7 Missing Function Level Access Control PPT Function Level Access Control Example By exploiting it, an attacker, who could be. This video explains everything you need to know about missing function level access control, including the definition, impact, and. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. How do missing function level access control exploits work? The missing function level access control. Function Level Access Control Example.
From www.slideserve.com
PPT OWASP Top10 2013 PowerPoint Presentation, free download ID1688525 Function Level Access Control Example There are a few ways that function level access controls can creep into an organization. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. By exploiting it, an attacker, who could be. By exploiting it, an attacker, who could be an existing user of the application, is able to. Function Level Access Control Example.
From www.slideserve.com
PPT OWASP Vulnerabilities and Auditing PowerPoint Presentation Function Level Access Control Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. By exploiting it, an attacker, who could be. For example, function level access can be left. This video explains everything you need to know about missing function level access control, including the definition, impact, and. This granular control is essential for ensuring. Function Level Access Control Example.
From www.researchgate.net
Outline of missing function level access control (MFLAC) vulnerability Function Level Access Control Example The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. There are a few ways that function level access controls can creep into an organization. By exploiting it, an attacker, who could. Function Level Access Control Example.
From www.atatus.com
RoleBased Access Control Definition, Implementation & More Function Level Access Control Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. How do missing function level access control exploits work? There are a few ways that function level access controls can creep into an organization.. Function Level Access Control Example.
From www.scribd.com
Missing Functional Level Access Control OWASP App Top 10 PDF Function Level Access Control Example For example, function level access can be left. This video explains everything you need to know about missing function level access control, including the definition, impact, and. How do missing function level access control exploits work? This granular control is essential for ensuring that users can. By exploiting it, an attacker, who could be an existing user of the application,. Function Level Access Control Example.
From subscription.packtpub.com
Functional access level control Mastering Kali Linux for Function Level Access Control Example There are a few ways that function level access controls can creep into an organization. How do missing function level access control exploits work? For example, function level access can be left. This video explains everything you need to know about missing function level access control, including the definition, impact, and. By exploiting it, an attacker, who could be. By. Function Level Access Control Example.
From houseofit.ph
How To Level Up Your Access Control System Function Level Access Control Example For example, function level access can be left. This video explains everything you need to know about missing function level access control, including the definition, impact, and. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication. Function Level Access Control Example.
From www.researchgate.net
Functional Architecture of the Access Control subsystem Download Function Level Access Control Example This granular control is essential for ensuring that users can. There are a few ways that function level access controls can creep into an organization. By exploiting it, an attacker, who could be. For example, function level access can be left. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. How. Function Level Access Control Example.
From www.slideserve.com
PPT Access control models and policies PowerPoint Presentation, free Function Level Access Control Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. This video explains everything you need to know about missing function level access control, including the definition, impact, and. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. By exploiting it,. Function Level Access Control Example.
From www.researchgate.net
Threat tree showing missing Function Level Access Control threats Function Level Access Control Example By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. This granular control is essential for ensuring that users can. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access. Missing function level access control, an owasp top 10 vulnerability, occurs when. Function Level Access Control Example.
From www.youtube.com
[A1] Missing Function Level Access Control Goat YouTube Function Level Access Control Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. There are a few ways that function level access controls can creep into an organization. How do missing function level access control exploits work? By exploiting it, an attacker, who could be. This video explains everything you need to know about missing. Function Level Access Control Example.
From www.youtube.com
OWASP A7 Missing Function Level Access Control IT 6873 Presentation Function Level Access Control Example By exploiting it, an attacker, who could be an existing user of the application, is able to escalate. For example, function level access can be left. There are a few ways that function level access controls can creep into an organization. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are. The. Function Level Access Control Example.