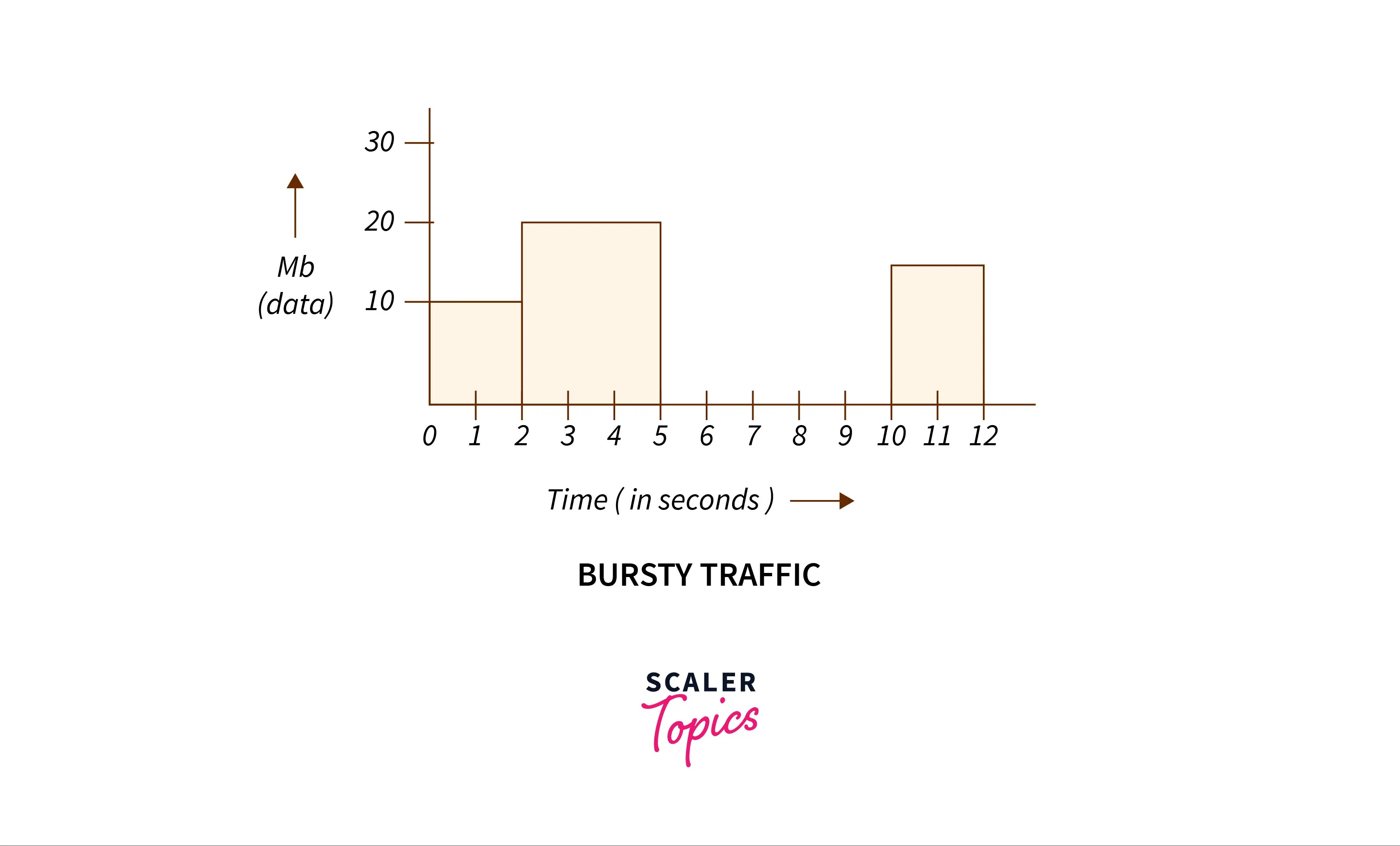
Leaky Bucket Algorithm Ppt . Suppose we have a bucket in which we are pouring water, at random points. (b) a leaky bucket with packets. Pcr and the cdvt, and the relationship b.w. 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. Generic cell rate algorithm (gcra) used to define conformance with respect to the. 44 the leaky bucket algorithm (a) a leaky bucket with water. There are 2 types of traffic shaping algorithms: The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Leaky bucket algorithm— presentation transcript: Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. 11/15/2018 tanenbaum chapter 5 network The document summarizes two algorithms for regulating network traffic: Pcr and the cdvt, and the relationship.
from www.scaler.com
44 the leaky bucket algorithm (a) a leaky bucket with water. There are 2 types of traffic shaping algorithms: 11/15/2018 tanenbaum chapter 5 network Suppose we have a bucket in which we are pouring water, at random points. The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. (b) a leaky bucket with packets. Leaky bucket algorithm— presentation transcript: The document summarizes two algorithms for regulating network traffic: Pcr and the cdvt, and the relationship. Pcr and the cdvt, and the relationship b.w.
Leaky Bucket Algorithm Scalar Topics
Leaky Bucket Algorithm Ppt Generic cell rate algorithm (gcra) used to define conformance with respect to the. Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. Pcr and the cdvt, and the relationship b.w. Leaky bucket algorithm— presentation transcript: Generic cell rate algorithm (gcra) used to define conformance with respect to the. 11/15/2018 tanenbaum chapter 5 network Suppose we have a bucket in which we are pouring water, at random points. The document summarizes two algorithms for regulating network traffic: 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. Pcr and the cdvt, and the relationship. (b) a leaky bucket with packets. 44 the leaky bucket algorithm (a) a leaky bucket with water. The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. There are 2 types of traffic shaping algorithms:
From www.geeksforgeeks.org
Rate Limiting Algorithms System Design Leaky Bucket Algorithm Ppt (b) a leaky bucket with packets. Pcr and the cdvt, and the relationship. Suppose we have a bucket in which we are pouring water, at random points. Leaky bucket algorithm— presentation transcript: Generic cell rate algorithm (gcra) used to define conformance with respect to the. The document summarizes two algorithms for regulating network traffic: Pcr and the cdvt, and the. Leaky Bucket Algorithm Ppt.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Ppt (b) a leaky bucket with packets. The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. There are 2 types of traffic shaping algorithms: Leaky bucket algorithm— presentation transcript: Pcr and the cdvt, and the relationship b.w. The document summarizes two algorithms for regulating network traffic: Generic cell rate algorithm (gcra) •. Leaky Bucket Algorithm Ppt.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Ppt Pcr and the cdvt, and the relationship. Pcr and the cdvt, and the relationship b.w. The document summarizes two algorithms for regulating network traffic: There are 2 types of traffic shaping algorithms: 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. Generic cell rate algorithm (gcra) • used to define conformance with respect. Leaky Bucket Algorithm Ppt.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Ppt Leaky bucket algorithm— presentation transcript: The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Pcr and the cdvt, and the relationship. Generic cell rate algorithm (gcra) used to define conformance with respect to the. (b) a leaky bucket with packets. Pcr and the cdvt, and the relationship b.w. Generic cell rate. Leaky Bucket Algorithm Ppt.
From slideplayer.com
Introduction to Computer Networks ppt download Leaky Bucket Algorithm Ppt 44 the leaky bucket algorithm (a) a leaky bucket with water. Pcr and the cdvt, and the relationship. Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Leaky bucket algorithm—. Leaky Bucket Algorithm Ppt.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm Ppt The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. There are 2 types of traffic shaping algorithms: Generic cell rate algorithm (gcra) used to define conformance with respect to the. 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. 44 the leaky bucket algorithm. Leaky Bucket Algorithm Ppt.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Ppt Pcr and the cdvt, and the relationship. 11/15/2018 tanenbaum chapter 5 network (b) a leaky bucket with packets. Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. There are 2 types of traffic shaping algorithms: 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate. Leaky Bucket Algorithm Ppt.
From www.sketchbubble.com
Leaky Bucket PowerPoint and Google Slides Template PPT Slides Leaky Bucket Algorithm Ppt (b) a leaky bucket with packets. Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. Leaky bucket algorithm— presentation transcript: The document summarizes two algorithms for regulating network traffic: 44 the leaky bucket algorithm (a) a leaky bucket with water. The leaky bucket algorithm models traffic as water. Leaky Bucket Algorithm Ppt.
From www.slideserve.com
PPT Outline PowerPoint Presentation, free download ID6256891 Leaky Bucket Algorithm Ppt 11/15/2018 tanenbaum chapter 5 network Suppose we have a bucket in which we are pouring water, at random points. Pcr and the cdvt, and the relationship b.w. 44 the leaky bucket algorithm (a) a leaky bucket with water. (b) a leaky bucket with packets. 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network.. Leaky Bucket Algorithm Ppt.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Leaky Bucket Algorithm Ppt Pcr and the cdvt, and the relationship. Suppose we have a bucket in which we are pouring water, at random points. The document summarizes two algorithms for regulating network traffic: 11/15/2018 tanenbaum chapter 5 network (b) a leaky bucket with packets. Generic cell rate algorithm (gcra) used to define conformance with respect to the. 44 the leaky bucket algorithm (a). Leaky Bucket Algorithm Ppt.
From merkantilaklubben.org
Top 118+ Token bucket algorithm animation Leaky Bucket Algorithm Ppt Generic cell rate algorithm (gcra) used to define conformance with respect to the. The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. 44 the leaky bucket algorithm (a) a leaky bucket with water. Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define. Leaky Bucket Algorithm Ppt.
From www.youtube.com
Mastering the Leaky Bucket Algorithm A StepbyStep Guide? algorithm Leaky Bucket Algorithm Ppt 11/15/2018 tanenbaum chapter 5 network 44 the leaky bucket algorithm (a) a leaky bucket with water. (b) a leaky bucket with packets. There are 2 types of traffic shaping algorithms: Pcr and the cdvt, and the relationship. Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. The document. Leaky Bucket Algorithm Ppt.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID3653615 Leaky Bucket Algorithm Ppt 11/15/2018 tanenbaum chapter 5 network (b) a leaky bucket with packets. There are 2 types of traffic shaping algorithms: Pcr and the cdvt, and the relationship. The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Leaky bucket algorithm— presentation transcript: Suppose we have a bucket in which we are pouring water,. Leaky Bucket Algorithm Ppt.
From slideplayer.com
Congestion Control Evaluation in Dynamic Network ppt download Leaky Bucket Algorithm Ppt The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. 44 the leaky bucket algorithm (a) a leaky bucket with water. Generic cell rate algorithm (gcra) used to define conformance with respect to the. There are 2 types of traffic shaping algorithms: Pcr and the cdvt, and the relationship b.w. Leaky bucket. Leaky Bucket Algorithm Ppt.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID3653615 Leaky Bucket Algorithm Ppt Pcr and the cdvt, and the relationship b.w. The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. Leaky bucket algorithm— presentation transcript: The document summarizes two algorithms for regulating network traffic: 11/15/2018 tanenbaum chapter 5. Leaky Bucket Algorithm Ppt.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Ppt The document summarizes two algorithms for regulating network traffic: Generic cell rate algorithm (gcra) used to define conformance with respect to the. The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Pcr and the cdvt, and the relationship. 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate. Leaky Bucket Algorithm Ppt.
From www.slideserve.com
PPT ATM CONGESTION CONTROL PowerPoint Presentation, free download Leaky Bucket Algorithm Ppt Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. Suppose we have a bucket in which we are pouring water, at random points. There are 2 types of traffic shaping algorithms: Pcr and the cdvt, and the relationship b.w. Leaky bucket algorithm— presentation transcript: 11/15/2018 tanenbaum chapter 5. Leaky Bucket Algorithm Ppt.
From www.sketchbubble.com
Leaky Bucket PowerPoint and Google Slides Template PPT Slides Leaky Bucket Algorithm Ppt The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Pcr and the cdvt, and the relationship. The document summarizes two algorithms for regulating network traffic: 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. (b) a leaky bucket with packets. Generic cell rate algorithm. Leaky Bucket Algorithm Ppt.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Ppt 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. Pcr and the cdvt, and the relationship b.w. The document summarizes two algorithms for regulating network traffic: There are 2 types of traffic shaping algorithms: Leaky bucket algorithm— presentation transcript: Suppose we have a bucket in which we are pouring water, at random points.. Leaky Bucket Algorithm Ppt.
From exyypouit.blob.core.windows.net
Leaky Bucket Model at Nellie Shepler blog Leaky Bucket Algorithm Ppt Suppose we have a bucket in which we are pouring water, at random points. 44 the leaky bucket algorithm (a) a leaky bucket with water. 11/15/2018 tanenbaum chapter 5 network The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Generic cell rate algorithm (gcra) • used to define conformance with respect. Leaky Bucket Algorithm Ppt.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID3009018 Leaky Bucket Algorithm Ppt Suppose we have a bucket in which we are pouring water, at random points. The document summarizes two algorithms for regulating network traffic: There are 2 types of traffic shaping algorithms: 11/15/2018 tanenbaum chapter 5 network 44 the leaky bucket algorithm (a) a leaky bucket with water. 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate. Leaky Bucket Algorithm Ppt.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Ppt 11/15/2018 tanenbaum chapter 5 network 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. Leaky bucket algorithm— presentation transcript: The document summarizes two algorithms for regulating network traffic: 44 the leaky bucket algorithm (a) a leaky bucket with water. (b) a leaky bucket with packets. There are 2 types of traffic shaping algorithms:. Leaky Bucket Algorithm Ppt.
From cejtsymb.blob.core.windows.net
Difference Between Leaky Bucket And Token Bucket at Kathryn Rivera blog Leaky Bucket Algorithm Ppt Generic cell rate algorithm (gcra) used to define conformance with respect to the. Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. Pcr and the cdvt, and the relationship. 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. Suppose we have. Leaky Bucket Algorithm Ppt.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Leaky Bucket Algorithm Ppt Pcr and the cdvt, and the relationship b.w. 11/15/2018 tanenbaum chapter 5 network (b) a leaky bucket with packets. Pcr and the cdvt, and the relationship. Suppose we have a bucket in which we are pouring water, at random points. 44 the leaky bucket algorithm (a) a leaky bucket with water. 2 leaky bucket algorithm • the leaky bucket algorithm. Leaky Bucket Algorithm Ppt.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Leaky Bucket Algorithm Ppt The document summarizes two algorithms for regulating network traffic: 11/15/2018 tanenbaum chapter 5 network 44 the leaky bucket algorithm (a) a leaky bucket with water. Leaky bucket algorithm— presentation transcript: Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. Suppose we have a bucket in which we are. Leaky Bucket Algorithm Ppt.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Ppt 44 the leaky bucket algorithm (a) a leaky bucket with water. Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. 11/15/2018 tanenbaum chapter 5 network (b) a leaky bucket with packets. The document summarizes two algorithms for regulating network traffic: The leaky bucket algorithm models traffic as water. Leaky Bucket Algorithm Ppt.
From www.code4it.dev
Davide's Code and Architecture Notes 4 algorithms to implement Rate Leaky Bucket Algorithm Ppt Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. Pcr and the cdvt, and the relationship. Pcr and the cdvt, and the relationship b.w. There are 2 types of traffic shaping algorithms: 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network.. Leaky Bucket Algorithm Ppt.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Algorithm Ppt The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Suppose we have a bucket in which we are pouring water, at random points. Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define the relationship b.w. Leaky bucket algorithm— presentation transcript: Pcr and. Leaky Bucket Algorithm Ppt.
From kladkpvbq.blob.core.windows.net
Token Bucket Scheme at Andrea Arrant blog Leaky Bucket Algorithm Ppt The document summarizes two algorithms for regulating network traffic: 11/15/2018 tanenbaum chapter 5 network Pcr and the cdvt, and the relationship b.w. Pcr and the cdvt, and the relationship. There are 2 types of traffic shaping algorithms: The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. (b) a leaky bucket with. Leaky Bucket Algorithm Ppt.
From www.youtube.com
Congestion Control using Traffic Shaping in TCP, Leaky Bucket Algorithm Leaky Bucket Algorithm Ppt The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Suppose we have a bucket in which we are pouring water, at random points. 11/15/2018 tanenbaum chapter 5 network Generic cell rate algorithm (gcra) used to define conformance with respect to the. (b) a leaky bucket with packets. 44 the leaky bucket. Leaky Bucket Algorithm Ppt.
From www.youtube.com
Leaky And Token Bucket Algorithms YouTube Leaky Bucket Algorithm Ppt 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. There are 2 types of traffic shaping algorithms: Pcr and the cdvt, and the relationship b.w. Leaky bucket algorithm— presentation transcript: 11/15/2018 tanenbaum chapter 5 network (b) a leaky bucket with packets. 44 the leaky bucket algorithm (a) a leaky bucket with water. Pcr. Leaky Bucket Algorithm Ppt.
From cejtsymb.blob.core.windows.net
Difference Between Leaky Bucket And Token Bucket at Kathryn Rivera blog Leaky Bucket Algorithm Ppt Pcr and the cdvt, and the relationship b.w. There are 2 types of traffic shaping algorithms: 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. 11/15/2018 tanenbaum chapter 5 network The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Suppose we have a bucket. Leaky Bucket Algorithm Ppt.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Ppt The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. The document summarizes two algorithms for regulating network traffic: Suppose we have a bucket in which we are pouring water, at random points. 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. Pcr and the. Leaky Bucket Algorithm Ppt.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm Ppt 2 leaky bucket algorithm • the leaky bucket algorithm used to control rate in a network. The document summarizes two algorithms for regulating network traffic: Generic cell rate algorithm (gcra) used to define conformance with respect to the. 44 the leaky bucket algorithm (a) a leaky bucket with water. 11/15/2018 tanenbaum chapter 5 network Generic cell rate algorithm (gcra) •. Leaky Bucket Algorithm Ppt.
From dev.to
Rate Limiter in System Design. Part 2 Commonly Used Algorithms DEV Leaky Bucket Algorithm Ppt The leaky bucket algorithm models traffic as water entering a bucket with a hole, limiting output to a. Leaky bucket algorithm— presentation transcript: There are 2 types of traffic shaping algorithms: 44 the leaky bucket algorithm (a) a leaky bucket with water. Generic cell rate algorithm (gcra) • used to define conformance with respect to the traffic contract • define. Leaky Bucket Algorithm Ppt.