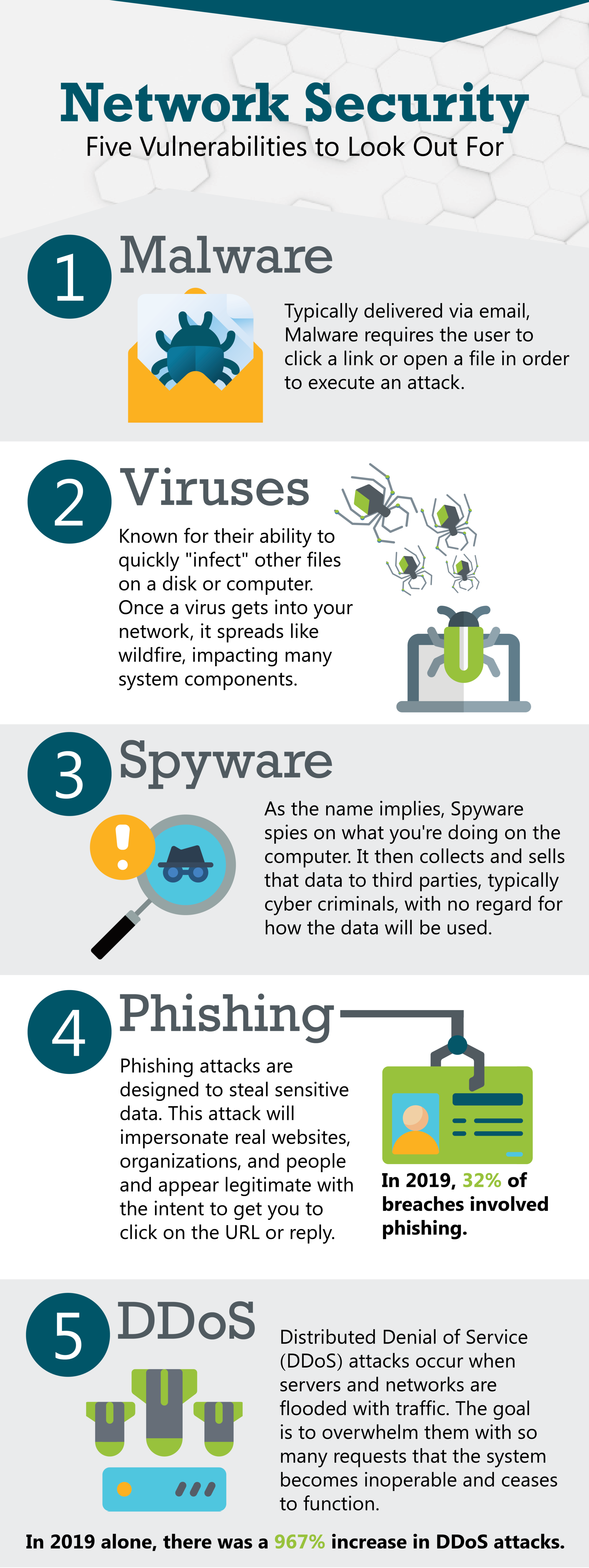
What Are The Security Vulnerabilities . A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. We review the 7 most common types of vulnerabilities including: Misconfigurations, unsecured apis, zero days, and unpatched. Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. After exploiting a vulnerability, a cyberattack. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. Find out how to identify and fix. A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack.
from www.lightedge.com
After exploiting a vulnerability, a cyberattack. We review the 7 most common types of vulnerabilities including: Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. Find out how to identify and fix. Misconfigurations, unsecured apis, zero days, and unpatched. A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack.
Network Security Vulnerabilities Infographic LightEdge Solutions
What Are The Security Vulnerabilities A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. Find out how to identify and fix. A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. Misconfigurations, unsecured apis, zero days, and unpatched. We review the 7 most common types of vulnerabilities including: Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack. After exploiting a vulnerability, a cyberattack. A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that.
From techartisans.io
Security Insights Common Vulnerabilities Demystified What Are The Security Vulnerabilities A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack. A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. Learn what a security vulnerability. What Are The Security Vulnerabilities.
From gcore.com
10 Common Security Vulnerabilities Gcore What Are The Security Vulnerabilities Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. A vulnerability is a weakness in an it system that can be exploited. What Are The Security Vulnerabilities.
From www.spiceworks.com
What Is a Security Vulnerability? Definition, Types, and Best Practices What Are The Security Vulnerabilities We review the 7 most common types of vulnerabilities including: Misconfigurations, unsecured apis, zero days, and unpatched. Find out how to identify and fix. After exploiting a vulnerability, a cyberattack. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. Learn what a security vulnerability is, how it differs. What Are The Security Vulnerabilities.
From www.businesstechweekly.com
Vulnerability Assessments 4 Crucial Steps for Identifying What Are The Security Vulnerabilities After exploiting a vulnerability, a cyberattack. Find out how to identify and fix. Misconfigurations, unsecured apis, zero days, and unpatched. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of. What Are The Security Vulnerabilities.
From www.calyptix.com
Top 10 Security Vulnerabilities of 2017 What Are The Security Vulnerabilities A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack. A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. Misconfigurations, unsecured apis, zero days, and unpatched. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal. What Are The Security Vulnerabilities.
From vulert.com
Understanding Security Vulnerabilities Definition & Types What Are The Security Vulnerabilities A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack. Misconfigurations, unsecured apis, zero days, and unpatched. After exploiting a vulnerability, a cyberattack. A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. A vulnerability in cybersecurity refers to a. What Are The Security Vulnerabilities.
From www.pandasecurity.com
What is a Vulnerability Assessment? Panda Security What Are The Security Vulnerabilities Misconfigurations, unsecured apis, zero days, and unpatched. Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. A vulnerability in cybersecurity refers to a weakness or flaw in a. What Are The Security Vulnerabilities.
From www.spiceworks.com
What Is a Security Vulnerability? Definition, Types, and Best Practices What Are The Security Vulnerabilities A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. Find out how to identify and fix. Misconfigurations, unsecured apis, zero days, and unpatched. After exploiting a vulnerability, a cyberattack.. What Are The Security Vulnerabilities.
From www.balbix.com
The 9 Types of Security Vulnerabilities Balbix What Are The Security Vulnerabilities A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. After exploiting a vulnerability, a cyberattack. Misconfigurations, unsecured apis, zero days, and unpatched. Find out how to identify and fix. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. A vulnerability is a. What Are The Security Vulnerabilities.
From www.compuquip.com
4 Steps to Improve Your Vulnerability Management Process What Are The Security Vulnerabilities Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. After exploiting a vulnerability, a cyberattack. Find out how to identify and fix. A. What Are The Security Vulnerabilities.
From www.comparitech.com
25+ Cyber Security Vulnerability Statistics and Facts of 2024 What Are The Security Vulnerabilities After exploiting a vulnerability, a cyberattack. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. Misconfigurations, unsecured apis, zero days, and unpatched. We review the 7 most common. What Are The Security Vulnerabilities.
From www.n-ix.com
6 types of security vulnerabilities in NiX What Are The Security Vulnerabilities Find out how to identify and fix. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. Learn what a security vulnerability is, how it differs from an exploit and. What Are The Security Vulnerabilities.
From www.lanworks.com
Vulnerability Assessment Lanworks What Are The Security Vulnerabilities A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack. Misconfigurations, unsecured apis, zero days, and unpatched. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. After exploiting a vulnerability, a cyberattack. A vulnerability is a weakness that can be exploited by cybercriminals. What Are The Security Vulnerabilities.
From www.spiceworks.com
What Is a Security Vulnerability? Definition, Types, and Best Practices What Are The Security Vulnerabilities After exploiting a vulnerability, a cyberattack. Misconfigurations, unsecured apis, zero days, and unpatched. We review the 7 most common types of vulnerabilities including: Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. Find. What Are The Security Vulnerabilities.
From www.pinterest.com
The Top 10 Security Vulnerabilities for Applications What Are The Security Vulnerabilities Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. We review the 7 most common types of vulnerabilities including: Security vulnerabilities are weaknesses. What Are The Security Vulnerabilities.
From www.itechcode.com
What You Should Know about the Most Common Causes of Security What Are The Security Vulnerabilities We review the 7 most common types of vulnerabilities including: A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. After exploiting a vulnerability, a cyberattack. Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications. What Are The Security Vulnerabilities.
From debricked.com
What is a security vulnerability? Debricked What Are The Security Vulnerabilities A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack. We review the 7 most common types of vulnerabilities including: Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or. What Are The Security Vulnerabilities.
From www.lightedge.com
Network Security Vulnerabilities Infographic LightEdge Solutions What Are The Security Vulnerabilities Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. Find out how to identify and fix. Misconfigurations, unsecured apis, zero days, and unpatched. After exploiting a vulnerability, a cyberattack. A vulnerability is a weakness in an it system that can be exploited by. What Are The Security Vulnerabilities.
From www.atyourbusiness.com
5 Common Security Vulnerabilities and Threats a Business Will Face What Are The Security Vulnerabilities A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. After exploiting a vulnerability, a cyberattack. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. We review the 7 most common types of vulnerabilities including: A vulnerability is a weakness that can be exploited. What Are The Security Vulnerabilities.
From www.patterndrive.com
Top 10 Security Vulnerabilities You Must Know Pattern Drive Private What Are The Security Vulnerabilities After exploiting a vulnerability, a cyberattack. A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. A vulnerability is a weakness that can be. What Are The Security Vulnerabilities.
From trainings.internshala.com
Vulnerability in Cyber Security Types and Causes What Are The Security Vulnerabilities After exploiting a vulnerability, a cyberattack. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. We review the 7 most common types of vulnerabilities including: A vulnerability in cybersecurity refers to a weakness. What Are The Security Vulnerabilities.
From thecyphere.com
What Is Cyber Security Vulnerability? What Are The Security Vulnerabilities Misconfigurations, unsecured apis, zero days, and unpatched. We review the 7 most common types of vulnerabilities including: After exploiting a vulnerability, a cyberattack. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. Find out how to identify and fix. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system. What Are The Security Vulnerabilities.
From www.manageengine.com
Vulnerability Assessment Tools & Checklists ManageEngine What Are The Security Vulnerabilities A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. Find out how to identify and fix. Misconfigurations, unsecured apis, zero days, and unpatched. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. A vulnerability is a weakness in an it system that can. What Are The Security Vulnerabilities.
From theenterpriseworld.com
Top 9 Common Business site Security Vulnerabilities The Enterprise What Are The Security Vulnerabilities A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. Find out how to. What Are The Security Vulnerabilities.
From technofaq.org
Six Security Vulnerabilities You Can, and Should, Prevent Techno FAQ What Are The Security Vulnerabilities A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. We review the 7 most common types of vulnerabilities including: A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack. A vulnerability in cybersecurity refers to a weakness. What Are The Security Vulnerabilities.
From www.firstpoint-mg.com
Top 7 IoT Cyber Security Vulnerabilities for 2022 FirstPoint What Are The Security Vulnerabilities A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. After exploiting a vulnerability, a cyberattack. Misconfigurations, unsecured apis, zero days, and unpatched. We review the 7 most common types of. What Are The Security Vulnerabilities.
From www.stanfieldit.com
Cyber Security Vulnerabilities Your Should Be Aware Of What Are The Security Vulnerabilities A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. After exploiting a vulnerability, a cyberattack. We review the 7 most common types of vulnerabilities including: Find out how to identify. What Are The Security Vulnerabilities.
From www.itsasap.com
What is a Security Vulnerability? (Definition, Types, and Remediation) What Are The Security Vulnerabilities Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack. Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications. What Are The Security Vulnerabilities.
From www.theknowledgeacademy.com
What is Vulnerability in Cyber Security With Example? What Are The Security Vulnerabilities A vulnerability is a weakness in an it system that can be exploited by an attacker to deliver a successful attack. After exploiting a vulnerability, a cyberattack. We review the 7 most common types of vulnerabilities including: Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. A vulnerability in cybersecurity refers to a weakness. What Are The Security Vulnerabilities.
From www.cybersecuriosity.com
What is Vulnerability Assessment CyberSecuriosity Professional What Are The Security Vulnerabilities Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. Misconfigurations, unsecured apis, zero days, and unpatched. Find out how to identify and fix. A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. A vulnerability is a weakness in an it system that can. What Are The Security Vulnerabilities.
From www.appknox.com
Top 10 Cyber Security Vulnerabilities Used by Cyber Criminals What Are The Security Vulnerabilities Find out how to identify and fix. Misconfigurations, unsecured apis, zero days, and unpatched. After exploiting a vulnerability, a cyberattack. A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. Learn what a security vulnerability. What Are The Security Vulnerabilities.
From intellipaat.com
Vulnerability in Cyber Security The Guide for Beginners What Are The Security Vulnerabilities Find out how to identify and fix. A vulnerability in cybersecurity refers to a weakness or flaw in a system, network, application, or even human behavior that. A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. A vulnerability is a weakness in an it system that can be. What Are The Security Vulnerabilities.
From www.globaltechcouncil.org
What are the Types of Cyber Security Vulnerabilities? Global Tech Council What Are The Security Vulnerabilities Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. We review the 7 most common types of vulnerabilities including: Misconfigurations, unsecured apis, zero days,. What Are The Security Vulnerabilities.
From datafloq.com
Why Your Big Data & IoT Security Are Vulnerable (And What to Do About What Are The Security Vulnerabilities A cybersecurity vulnerability is any weakness within an organization’s information systems, internal controls, or system processes that can be exploited by. Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. A vulnerability is a weakness that can be exploited by cybercriminals to gain. What Are The Security Vulnerabilities.
From www.bitlyft.com
What Is Vulnerability Management? How Does It Work What Are The Security Vulnerabilities After exploiting a vulnerability, a cyberattack. Learn what a security vulnerability is, how it differs from an exploit and a threat, and what types of vulnerabilities exist in web applications and websites. We review the 7 most common types of vulnerabilities including: Find out how to identify and fix. Misconfigurations, unsecured apis, zero days, and unpatched. A cybersecurity vulnerability is. What Are The Security Vulnerabilities.