Switch Vlan Security . If an organization does not want its devices tampered with, physical access must be strictly. The most common attacks against vlan. Securing vlans includes both switch security and proper vlan configuration. It also examines security considerations and strategies relating to vlans and trunks,. In this tip, we detail how to achieve the security benefits of a properly configured vlan. We also discuss one of the most. By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. The first principle in securing a vlan network is physical security. This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title.
from help.sonicwall.com
Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. The most common attacks against vlan. In this tip, we detail how to achieve the security benefits of a properly configured vlan. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. Securing vlans includes both switch security and proper vlan configuration. We also discuss one of the most. It also examines security considerations and strategies relating to vlans and trunks,. If an organization does not want its devices tampered with, physical access must be strictly. The first principle in securing a vlan network is physical security.
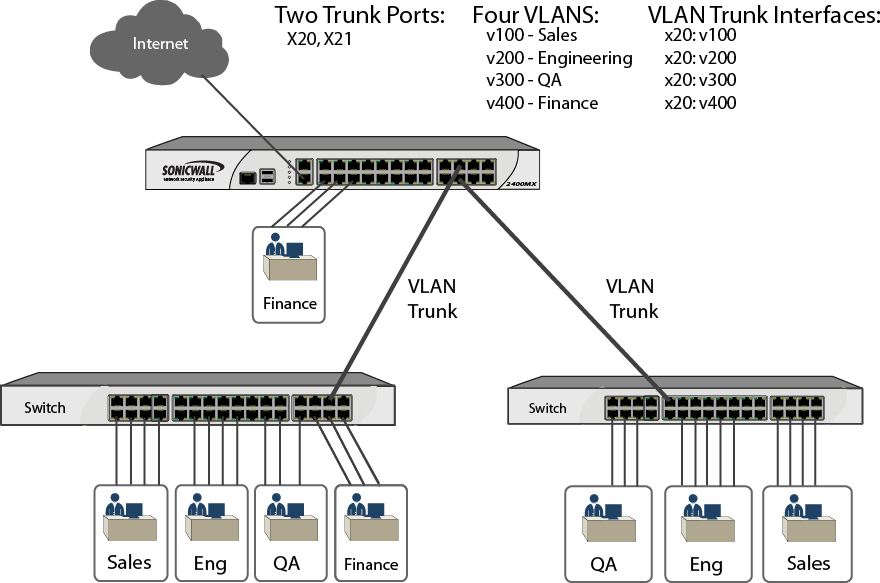
Switching > VLAN Trunking
Switch Vlan Security In this tip, we detail how to achieve the security benefits of a properly configured vlan. The most common attacks against vlan. If an organization does not want its devices tampered with, physical access must be strictly. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. The first principle in securing a vlan network is physical security. It also examines security considerations and strategies relating to vlans and trunks,. We also discuss one of the most. In this tip, we detail how to achieve the security benefits of a properly configured vlan. Securing vlans includes both switch security and proper vlan configuration. This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks.
From www.cisco.com
VLAN Best Practices and Security Tips for Cisco Business Routers Cisco Switch Vlan Security Securing vlans includes both switch security and proper vlan configuration. We also discuss one of the most. In this tip, we detail how to achieve the security benefits of a properly configured vlan. If an organization does not want its devices tampered with, physical access must be strictly. This chapter covers how to configure, manage, and troubleshoot vlans and vlan. Switch Vlan Security.
From community.cisco.com
intervlan security Cisco Community Switch Vlan Security By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. The first principle in securing a vlan network is physical security. It also examines security considerations and strategies relating to vlans and trunks,. Vlan configuration. Switch Vlan Security.
From kwallaceccie.mykajabi.com
VLAN Security Concepts Switch Vlan Security Securing vlans includes both switch security and proper vlan configuration. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. In this tip, we detail how to achieve the security benefits of a properly configured vlan. This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. If an organization. Switch Vlan Security.
From www.slideserve.com
PPT Chapter 3 Implementing VLAN Security PowerPoint Presentation, free download ID2384639 Switch Vlan Security This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. If an organization does not want its devices tampered with, physical access must be strictly. It also examines security considerations and strategies relating to vlans and trunks,. The most. Switch Vlan Security.
From animalia-life.club
Basic Vlan Switch Vlan Security This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. In this tip, we detail how to achieve the security benefits of a properly configured vlan. By assigning vlan numbers to switch ports, network administrators may create logical network. Switch Vlan Security.
From www.slideserve.com
PPT Security Tunneling PowerPoint Presentation, free download ID3308795 Switch Vlan Security In this tip, we detail how to achieve the security benefits of a properly configured vlan. The first principle in securing a vlan network is physical security. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. Securing vlans includes both switch security and proper vlan configuration. We also discuss one of the most. It also examines security. Switch Vlan Security.
From www.scribd.com
3.3.2.2 Lab Implementing VLAN Security.docx Network Switch Computer Network Switch Vlan Security Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. The most common attacks against vlan. Securing vlans includes both switch security and proper vlan configuration. The first principle in securing a vlan network is physical security. If an organization does not want its devices tampered with, physical access must be strictly.. Switch Vlan Security.
From asecuritysite.com
VLANs Switch Vlan Security Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. Securing vlans includes both switch security and proper vlan configuration. The most common attacks against vlan. In this tip, we detail how to achieve the security benefits of a properly configured vlan. If an organization. Switch Vlan Security.
From www.tp-link.com
configuring_protocol_vlan Switch Vlan Security By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. In this tip, we detail how to achieve the security benefits of a properly configured vlan. The most common attacks against vlan. The first principle in securing a vlan network is physical security. Securing vlans includes both switch. Switch Vlan Security.
From sid-500.com
Cyber Security VLAN Double Tagging (Hopping) Attacks explained Switch Vlan Security Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. The most common attacks against vlan. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. The first principle in securing a vlan network is physical security. If an organization does not want its devices tampered with, physical access must. Switch Vlan Security.
From serenityhuang343.blogspot.com
What Is VLAN Switch and Why Do We Need It? Switch Vlan Security The most common attacks against vlan. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. If an organization does not want its devices tampered with, physical access must be strictly. In this tip, we detail how to achieve the security benefits of a properly configured vlan. By assigning vlan numbers to switch ports, network administrators may create. Switch Vlan Security.
From simeononsecurity.com
Network Plus Course Switching, VLANs, Port Configurations, Security, and More Switch Vlan Security Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. It also examines security considerations and strategies relating to vlans and trunks,. Securing vlans includes both switch security and proper vlan configuration. In this tip, we detail how to achieve the security benefits of a properly configured vlan. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches). Switch Vlan Security.
From www.scribd.com
A Comprehensive Guide to Configuring Layer 2 Security Features on Switches Including VLANs Switch Vlan Security Securing vlans includes both switch security and proper vlan configuration. The first principle in securing a vlan network is physical security. We also discuss one of the most. By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. This chapter covers how to configure, manage, and troubleshoot vlans. Switch Vlan Security.
From help.genesys.com
PureConnect Quality of Service Technical Reference Advanced Security Design in VLANs With a Switch Vlan Security By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. If an organization does not want its devices tampered with, physical access must be strictly. The most common attacks against vlan. Securing vlans includes both switch security and proper vlan configuration. It also examines security considerations and strategies. Switch Vlan Security.
From www.slideserve.com
PPT Chapter 3 Implementing VLAN Security PowerPoint Presentation, free download ID2384639 Switch Vlan Security In this tip, we detail how to achieve the security benefits of a properly configured vlan. Securing vlans includes both switch security and proper vlan configuration. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. We also discuss one of the most. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500. Switch Vlan Security.
From geek-university.com
VLANs explained CCNA Switch Vlan Security We also discuss one of the most. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. Securing vlans includes both switch security and proper vlan configuration. This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. By assigning vlan numbers to switch ports, network administrators may create logical. Switch Vlan Security.
From help.sonicwall.com
Switching > VLAN Trunking Switch Vlan Security This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. It also examines security considerations and strategies relating to vlans and trunks,. The most common attacks against vlan. In this tip, we detail how to achieve the security benefits of a properly configured vlan. Securing vlans includes both switch security and proper vlan configuration. The first principle. Switch Vlan Security.
From www.slideserve.com
PPT Chapter 3 Implementing VLAN Security PowerPoint Presentation, free download ID2384639 Switch Vlan Security Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. If an organization does not want its devices tampered with, physical access must be strictly. Securing vlans includes both switch security and proper vlan configuration. The most common attacks against vlan. The first principle in securing a vlan network is physical security.. Switch Vlan Security.
From www.youtube.com
VLAN Explained what is VLAN VLANs VLAN tagging VLAN configuration VLAN Switch Vlan Switch Vlan Security We also discuss one of the most. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. The most common attacks against vlan. The first principle in securing a vlan network is physical security. Securing vlans includes both switch security. Switch Vlan Security.
From fileserver.airlive.com
Live26G 26port SOHO Gigabit Switch, VLAN, QoS, Plug and Play_Gigabit VLAN Switch_Data LAN Switch Vlan Security The first principle in securing a vlan network is physical security. We also discuss one of the most. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. The most. Switch Vlan Security.
From www.slideserve.com
PPT VLAN Basic VLAN switch principle PowerPoint Presentation, free download ID5189609 Switch Vlan Security The first principle in securing a vlan network is physical security. It also examines security considerations and strategies relating to vlans and trunks,. The most common attacks against vlan. By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500. Switch Vlan Security.
From www.newtechindustries.com
16 Port GPOE +2SFP PoE Switch 350W Dip Switch VLAN CCTV 250M Port Switch Vlan Security By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. If an organization does not want its devices tampered with, physical access must be strictly. It also examines security considerations and strategies relating to vlans and trunks,. This chapter covers how to configure, manage, and troubleshoot vlans and. Switch Vlan Security.
From www.networkacademy.io
VLAN Trunking NetworkAcademy.io Switch Vlan Security Securing vlans includes both switch security and proper vlan configuration. The most common attacks against vlan. In this tip, we detail how to achieve the security benefits of a properly configured vlan. It also examines security considerations and strategies relating to vlans and trunks,. If an organization does not want its devices tampered with, physical access must be strictly. Vlan. Switch Vlan Security.
From www.networkacademy.io
VLAN Trunking NetworkAcademy.io Switch Vlan Security The most common attacks against vlan. In this tip, we detail how to achieve the security benefits of a properly configured vlan. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. Securing vlans includes both switch security and proper vlan configuration. By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate. Switch Vlan Security.
From timigate.com
How to configure VLAN on cisco router using 802.1q encapsulation protocol Switch Vlan Security This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. We also discuss one of the most. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. If an organization does not want its devices tampered with, physical access must be strictly. The first principle in securing a vlan. Switch Vlan Security.
From www.networkacademy.io
VLAN Concept NetworkAcademy.io Switch Vlan Security We also discuss one of the most. It also examines security considerations and strategies relating to vlans and trunks,. In this tip, we detail how to achieve the security benefits of a properly configured vlan. Securing vlans includes both switch security and proper vlan configuration. The first principle in securing a vlan network is physical security. This chapter covers how. Switch Vlan Security.
From mw-2000s.airlive.com
Live26G 26port SOHO Gigabit Switch, VLAN, QoS, Plug and Play_Gigabit VLAN Switch_Data LAN Switch Vlan Security Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. The first principle in securing a vlan network is physical security. In this tip, we detail how to achieve the security benefits of a properly configured vlan. If an organization does not want its devices tampered with, physical access must be strictly.. Switch Vlan Security.
From benheater.com
How Do VLANs Work? Exploring the 802.1q Protocol Switch Vlan Security We also discuss one of the most. This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. In this tip, we detail how to achieve the security benefits of a properly configured vlan. If an organization does not want its devices tampered with, physical access. Switch Vlan Security.
From www.esecurityplanet.com
VLANs Effective Network Segmentation for Security Switch Vlan Security By assigning vlan numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between vlans. This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. We also discuss one of the most.. Switch Vlan Security.
From www.siri-vision.com
Layer 2+ 10/100/1000Mbps Managed Gigabit Switch Security With 12 Port / VLAN Switch Vlan Security In this tip, we detail how to achieve the security benefits of a properly configured vlan. It also examines security considerations and strategies relating to vlans and trunks,. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. Securing vlans includes both switch security and proper vlan configuration. The most common attacks. Switch Vlan Security.
From www.ciscoforall.com
What is VLAN and how to a VLAN on a Cisco Switch Switch Vlan Security Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for this product strives to. The first principle in securing a vlan network is physical security. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. Securing vlans includes both switch security and proper vlan configuration. By assigning vlan numbers to switch ports, network administrators. Switch Vlan Security.
From specialistviral.com
What is VLAN and How to Configure VLANs in Cisco Switch Specialist Viral Switch Vlan Security If an organization does not want its devices tampered with, physical access must be strictly. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. In this tip, we detail how to achieve the security benefits of a properly configured vlan. We also discuss one of the most. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches). Switch Vlan Security.
From www.fibermall.com
VLAN VLAN이란 무엇이며 어떻게 작동합니까? 파이버몰 Switch Vlan Security The first principle in securing a vlan network is physical security. This chapter covers how to configure, manage, and troubleshoot vlans and vlan trunks. If an organization does not want its devices tampered with, physical access must be strictly. We also discuss one of the most. Security configuration guide, cisco ios xe 17.15.x (catalyst 9300 switches) the documentation set for. Switch Vlan Security.
From www.pinterest.ph
How to setup VLANs for CCTV cameras (Easy explanation) Learn CCTV Cisco networking Switch Vlan Security It also examines security considerations and strategies relating to vlans and trunks,. Securing vlans includes both switch security and proper vlan configuration. The first principle in securing a vlan network is physical security. In this tip, we detail how to achieve the security benefits of a properly configured vlan. This chapter covers how to configure, manage, and troubleshoot vlans and. Switch Vlan Security.
From www.scribd.com
Switch Vlan Security PDF PDF Computer Standards Architecture Switch Vlan Security In this tip, we detail how to achieve the security benefits of a properly configured vlan. Securing vlans includes both switch security and proper vlan configuration. Vlan configuration guide, cisco ios xe 17.15.x (catalyst 9500 switches) chapter title. We also discuss one of the most. If an organization does not want its devices tampered with, physical access must be strictly.. Switch Vlan Security.