Port Scanning Penetration Testing . After completing first phase (reconnaissance) of penetration testing by penetration tester, they will enter into second. In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is. Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant port scanning techniques for a particular situation. First perform a network sweep to gain a list of potential targets. Network scanning, & how to. Port scan is a technique hackers use to discover weak points in a network. Discover port scanning techniques, the difference between port scanning vs. Scanning is usually performed hastily, so take your time. Penetration testing (pentesting) of ftp (file transfer protocol) involves assessing and exploiting vulnerabilities within an ftp. In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities.
from www.varonis.com
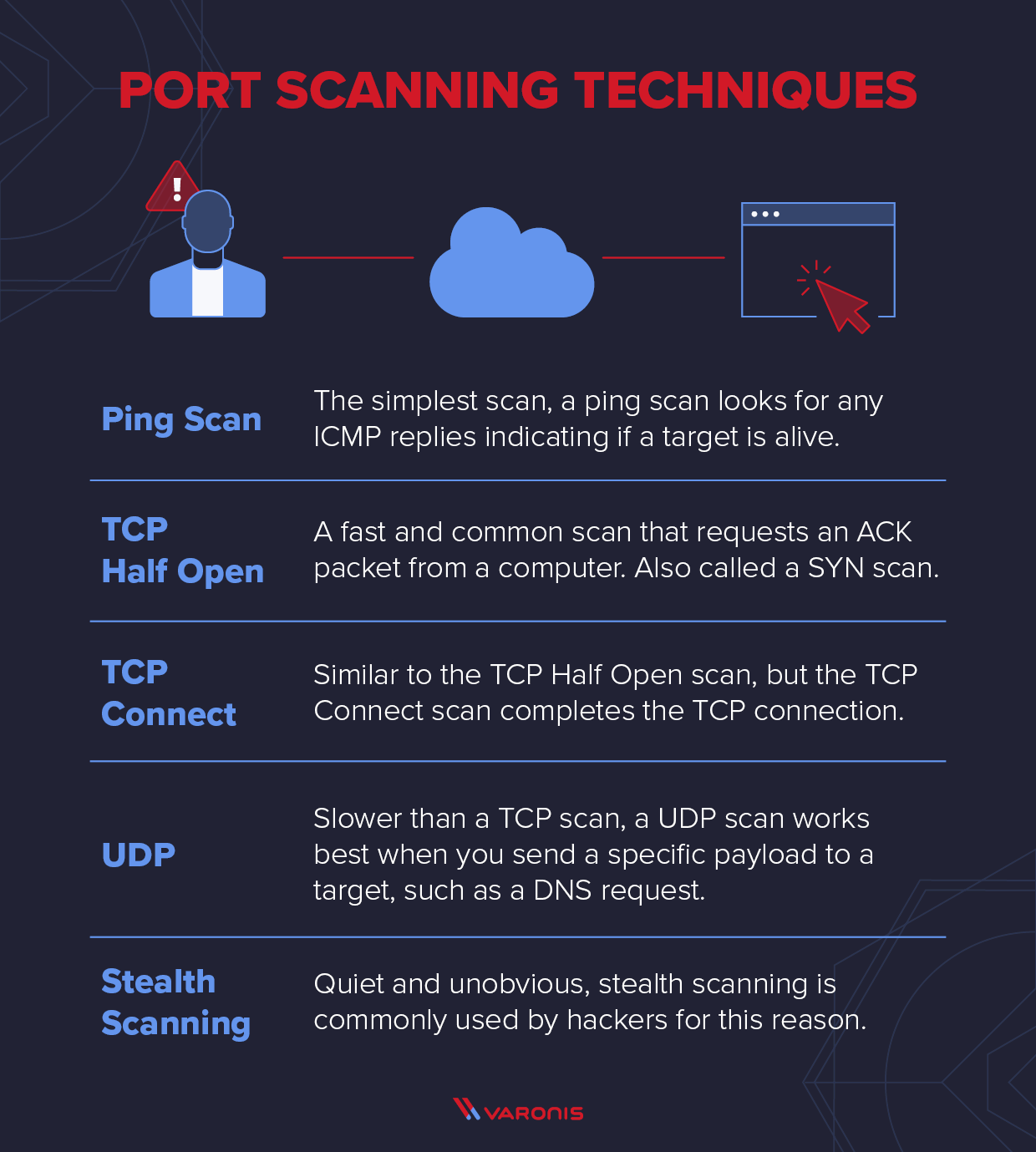
Port scan is a technique hackers use to discover weak points in a network. First perform a network sweep to gain a list of potential targets. In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. Discover port scanning techniques, the difference between port scanning vs. After completing first phase (reconnaissance) of penetration testing by penetration tester, they will enter into second. Scanning is usually performed hastily, so take your time. Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant port scanning techniques for a particular situation. Network scanning, & how to. By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is. Penetration testing (pentesting) of ftp (file transfer protocol) involves assessing and exploiting vulnerabilities within an ftp.
What is a Port Scanner and How Does it Work?
Port Scanning Penetration Testing In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. After completing first phase (reconnaissance) of penetration testing by penetration tester, they will enter into second. In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. Port scan is a technique hackers use to discover weak points in a network. First perform a network sweep to gain a list of potential targets. Network scanning, & how to. Penetration testing (pentesting) of ftp (file transfer protocol) involves assessing and exploiting vulnerabilities within an ftp. In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. Scanning is usually performed hastily, so take your time. By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is. Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant port scanning techniques for a particular situation. Discover port scanning techniques, the difference between port scanning vs.
From www.semanticscholar.org
Figure 4 from Testing Active Reconnaissance Phase Port Scanning Penetration Testing Scanning is usually performed hastily, so take your time. Port scan is a technique hackers use to discover weak points in a network. Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant port scanning techniques for a particular situation. Discover port scanning techniques, the difference between. Port Scanning Penetration Testing.
From www.slideserve.com
PPT Cyber Operation and Testing Scanning Cliff Zou Port Scanning Penetration Testing In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. First perform a network sweep to gain a list of potential targets. Network scanning, & how to. Scanning is usually performed hastily, so take your time. In this article, we’ll discuss the responsibilities of a penetration tester and outline. Port Scanning Penetration Testing.
From github.com
GitHub NikamSugat/PortScanner Simple Port Scanner The Simple Port Port Scanning Penetration Testing Port scan is a technique hackers use to discover weak points in a network. Scanning is usually performed hastily, so take your time. First perform a network sweep to gain a list of potential targets. Network scanning, & how to. In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning. Port Scanning Penetration Testing.
From www.researchgate.net
(PDF) Testing Active Reconnaissance Phase Optimized Port Port Scanning Penetration Testing Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant port scanning techniques for a particular situation. In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. Penetration testing (pentesting) of ftp (file transfer protocol) involves. Port Scanning Penetration Testing.
From www.indusface.com
8 Best site Testing Tools Indusface Blog Port Scanning Penetration Testing Scanning is usually performed hastily, so take your time. Port scan is a technique hackers use to discover weak points in a network. By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is. In this article, we’ll discuss the responsibilities of a penetration tester and. Port Scanning Penetration Testing.
From www.eccouncil.org
What Are Network Ports and Port Scanning Techniques? ECCouncil Port Scanning Penetration Testing In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. Network scanning, & how to. Discover port scanning techniques, the difference between port scanning vs. After completing first phase (reconnaissance) of penetration testing by penetration tester, they will enter into second. Due to possible vulnerabilities associated with network ports,. Port Scanning Penetration Testing.
From www.studypool.com
SOLUTION 0729 port and vulnerability scanning packet sniffing Port Scanning Penetration Testing Port scan is a technique hackers use to discover weak points in a network. In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is.. Port Scanning Penetration Testing.
From www.slideserve.com
PPT Testing Report PowerPoint Presentation, free download Port Scanning Penetration Testing Port scan is a technique hackers use to discover weak points in a network. In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. Scanning is usually performed hastily, so take your time.. Port Scanning Penetration Testing.
From www.scribd.com
A Comprehensive Guide to Conducting a Successful Network Port Scanning Penetration Testing In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. Scanning is usually performed hastily, so take your time. Port scan is a technique hackers use to discover weak points in a network.. Port Scanning Penetration Testing.
From www.varonis.com
What is a Port Scanner and How Does it Work? Port Scanning Penetration Testing After completing first phase (reconnaissance) of penetration testing by penetration tester, they will enter into second. Port scan is a technique hackers use to discover weak points in a network. In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can. Port Scanning Penetration Testing.
From cipherssecurity.com
How To Use NMAP For Testing Port Scanning Penetration Testing In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. By running the port scan, we can get the information like what all ports are open, what service is running on each port,. Port Scanning Penetration Testing.
From www.researchgate.net
(PDF) Testing Active Reconnaissance Phase Optimized Port Port Scanning Penetration Testing In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. After completing. Port Scanning Penetration Testing.
From securitywing.com
15 Testing ToolsOpen Source securitywing Port Scanning Penetration Testing In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant. Port Scanning Penetration Testing.
From www.varonis.com
What is a Port Scanner and How Does it Work? Port Scanning Penetration Testing In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. Port scan is a technique hackers use to discover weak points in a network. First perform a network sweep to gain a list of potential targets. Scanning is usually performed hastily, so take your time. After completing first phase. Port Scanning Penetration Testing.
From telegra.ph
Online Test Telegraph Port Scanning Penetration Testing Network scanning, & how to. In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance. Port Scanning Penetration Testing.
From www.youtube.com
Tryhackme Advanced Port Scan Jr. Path YouTube Port Scanning Penetration Testing Penetration testing (pentesting) of ftp (file transfer protocol) involves assessing and exploiting vulnerabilities within an ftp. Network scanning, & how to. Port scan is a technique hackers use to discover weak points in a network. Discover port scanning techniques, the difference between port scanning vs. Scanning is usually performed hastily, so take your time. Due to possible vulnerabilities associated with. Port Scanning Penetration Testing.
From www.youtube.com
How to Scan Open Port Using Kali Linux Testing Tools NMAP Port Scanning Penetration Testing Discover port scanning techniques, the difference between port scanning vs. In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. In this paper we are showing traffic accountability and time to complete the. Port Scanning Penetration Testing.
From www.youtube.com
Testing with Nmap Scanning for UDP Ports YouTube Port Scanning Penetration Testing First perform a network sweep to gain a list of potential targets. After completing first phase (reconnaissance) of penetration testing by penetration tester, they will enter into second. Port scan is a technique hackers use to discover weak points in a network. By running the port scan, we can get the information like what all ports are open, what service. Port Scanning Penetration Testing.
From slideplayer.com
Testing 10/12/2018 Testing. ppt download Port Scanning Penetration Testing Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant port scanning techniques for a particular situation. Scanning is usually performed hastily, so take your time. Network scanning, & how to. By running the port scan, we can get the information like what all ports are open,. Port Scanning Penetration Testing.
From www.paloaltonetworks.in
What is a Port Scan? Palo Alto Networks Port Scanning Penetration Testing Scanning is usually performed hastily, so take your time. Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant port scanning techniques for a particular situation. After completing first phase (reconnaissance) of penetration testing by penetration tester, they will enter into second. In this paper we are. Port Scanning Penetration Testing.
From securityonline.info
Ports scanning using Metasploit Port Scanning Penetration Testing In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. Discover port scanning techniques, the difference between port scanning vs. Scanning is usually performed hastily, so take your time. Penetration testing (pentesting) of. Port Scanning Penetration Testing.
From subscription.packtpub.com
testing standards Securing Network Infrastructure Port Scanning Penetration Testing Scanning is usually performed hastily, so take your time. After completing first phase (reconnaissance) of penetration testing by penetration tester, they will enter into second. Network scanning, & how to. Penetration testing (pentesting) of ftp (file transfer protocol) involves assessing and exploiting vulnerabilities within an ftp. Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals. Port Scanning Penetration Testing.
From www.youtube.com
3 Port Scanning Ethical Hacking & Testing Course YouTube Port Scanning Penetration Testing Discover port scanning techniques, the difference between port scanning vs. Scanning is usually performed hastily, so take your time. First perform a network sweep to gain a list of potential targets. In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that. Port Scanning Penetration Testing.
From www.vrogue.co
What Is Testing And Its Methodology vrogue.co Port Scanning Penetration Testing After completing first phase (reconnaissance) of penetration testing by penetration tester, they will enter into second. In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. Discover port scanning techniques, the difference between. Port Scanning Penetration Testing.
From www.scribd.com
Port and Vulnerability Scanning Packet Sniffing Intrusion Detection and Port Scanning Penetration Testing First perform a network sweep to gain a list of potential targets. In this article, we’ll discuss the responsibilities of a penetration tester and outline the five penetration testing phases, in addition to looking at some popular penetration testing tools that can be used to examine systems for vulnerabilities. Port scan is a technique hackers use to discover weak points. Port Scanning Penetration Testing.
From www.softactivity.com
The 5 Best Testing Tools to Use on Your Network SoftActivity Port Scanning Penetration Testing Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant port scanning techniques for a particular situation. Scanning is usually performed hastily, so take your time. By running the port scan, we can get the information like what all ports are open, what service is running on. Port Scanning Penetration Testing.
From www.youtube.com
Port Scanning the Internal Network | Internal Network Port Scanning Penetration Testing Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant port scanning techniques for a particular situation. Network scanning, & how to. In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. After completing first phase. Port Scanning Penetration Testing.
From www.computertechreviews.com
What is Port Scanning (Port Scan)? Definition, Types and More Port Scanning Penetration Testing By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is. First perform a network sweep to gain a list of potential targets. Discover port scanning techniques, the difference between port scanning vs. In this paper we are showing traffic accountability and time to complete the. Port Scanning Penetration Testing.
From thecyphere.com
Network Testing Services CREST Approved Port Scanning Penetration Testing By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is. Discover port scanning techniques, the difference between port scanning vs. Port scan is a technique hackers use to discover weak points in a network. Network scanning, & how to. Scanning is usually performed hastily, so. Port Scanning Penetration Testing.
From www.thesecuritybuddy.com
A Guide To Port Scanning Using Nmap The Security Buddy Port Scanning Penetration Testing In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. Penetration testing (pentesting) of ftp (file transfer protocol) involves assessing and exploiting vulnerabilities within an ftp. Scanning is usually performed hastily, so take your time. First perform a network sweep to gain a list of potential targets. In this. Port Scanning Penetration Testing.
From www.youtube.com
Testing _2 Port Scanning with your own script ! YouTube Port Scanning Penetration Testing In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. First perform a network sweep to gain a list of potential targets. By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is. Scanning is. Port Scanning Penetration Testing.
From www.semanticscholar.org
Figure 1 from Testing Active Reconnaissance Phase Port Scanning Penetration Testing Scanning is usually performed hastily, so take your time. Due to possible vulnerabilities associated with network ports, penetration testers and other cybersecurity professionals must understand the importance of using the most relevant port scanning techniques for a particular situation. Port scan is a technique hackers use to discover weak points in a network. Penetration testing (pentesting) of ftp (file transfer. Port Scanning Penetration Testing.
From www.hacking.reviews
AutoPentestDRL Automated Testing Using Deep Port Scanning Penetration Testing In this paper we are showing traffic accountability and time to complete the specific task during reconnaissance phase active scanning with. First perform a network sweep to gain a list of potential targets. Penetration testing (pentesting) of ftp (file transfer protocol) involves assessing and exploiting vulnerabilities within an ftp. In this article, we’ll discuss the responsibilities of a penetration tester. Port Scanning Penetration Testing.
From gr33namow.gitbook.io
Port scanning Testing Student v2 Port Scanning Penetration Testing By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is. First perform a network sweep to gain a list of potential targets. Discover port scanning techniques, the difference between port scanning vs. After completing first phase (reconnaissance) of penetration testing by penetration tester, they will. Port Scanning Penetration Testing.
From www.youtube.com
Armitage + Metasploit for testing from port scanning to Port Scanning Penetration Testing By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is. Discover port scanning techniques, the difference between port scanning vs. Port scan is a technique hackers use to discover weak points in a network. Network scanning, & how to. First perform a network sweep to. Port Scanning Penetration Testing.