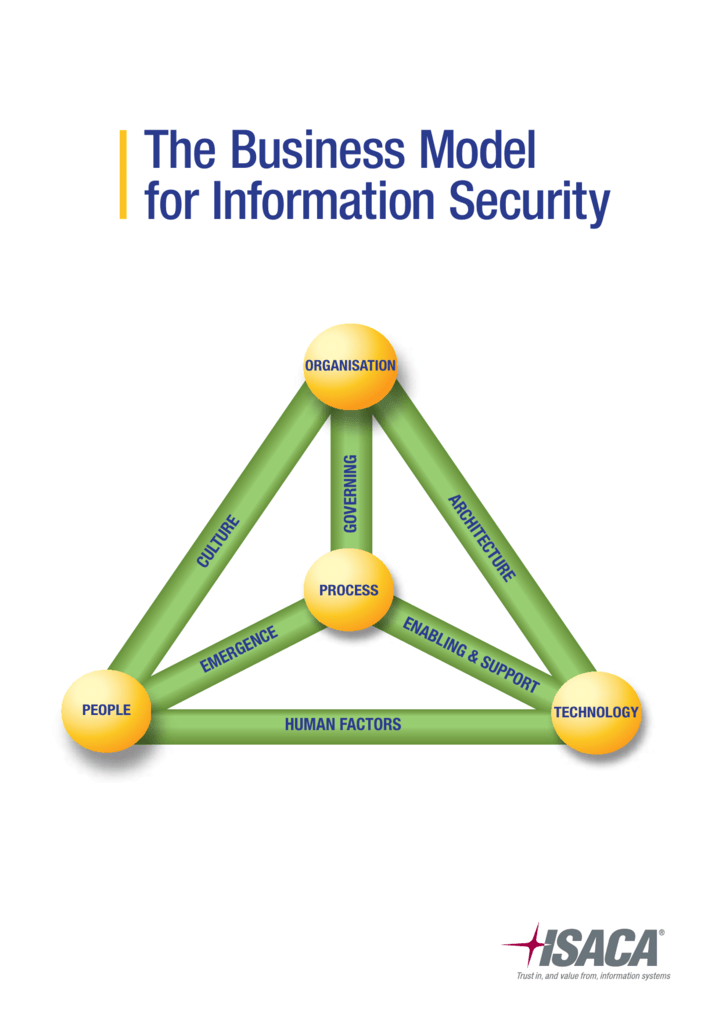
Modeling Information Security . “a structured representation of all the information that affects the security of an application. Information security models encompass various approaches, including multilevel security. a security model in information security is a framework or a systematic approach that describes how various security mechanisms. In essence, it is a view of the application and its. what are security models? the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or.
from studylib.net
a security model in information security is a framework or a systematic approach that describes how various security mechanisms. In essence, it is a view of the application and its. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. Information security models encompass various approaches, including multilevel security. “a structured representation of all the information that affects the security of an application. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. what are security models?
The Business Model for Information Security
Modeling Information Security threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. what are security models? “a structured representation of all the information that affects the security of an application. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. Information security models encompass various approaches, including multilevel security. a security model in information security is a framework or a systematic approach that describes how various security mechanisms. In essence, it is a view of the application and its. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify.
From fpov.com
Integrated Security Model Future Point Of View Modeling Information Security a security model in information security is a framework or a systematic approach that describes how various security mechanisms. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. Information security models encompass various approaches, including multilevel security. what are security models? “a structured representation of all the. Modeling Information Security.
From www.sketchbubble.com
Business Model for Information Security PowerPoint Template PPT Slides Modeling Information Security In essence, it is a view of the application and its. what are security models? a security model in information security is a framework or a systematic approach that describes how various security mechanisms. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. threat modeling is the. Modeling Information Security.
From enterprisesecurityposhibure.blogspot.com
Enterprise Security Enterprise Security Model Modeling Information Security Information security models encompass various approaches, including multilevel security. In essence, it is a view of the application and its. what are security models? a security model in information security is a framework or a systematic approach that describes how various security mechanisms. “a structured representation of all the information that affects the security of an application.. Modeling Information Security.
From www.slideserve.com
PPT Information Security PowerPoint Presentation, free download ID Modeling Information Security Information security models encompass various approaches, including multilevel security. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. “a structured representation of all the information that affects the. Modeling Information Security.
From 1stopinfosecurity.blogspot.com
1StopInfosecurity Information Security What is Threat Modeling Modeling Information Security “a structured representation of all the information that affects the security of an application. In essence, it is a view of the application and its. Information security models encompass various approaches, including multilevel security. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. the cia (confidentiality,. Modeling Information Security.
From securityboulevard.com
Security Maturity Models (Part 1 of 2) Security Boulevard Modeling Information Security “a structured representation of all the information that affects the security of an application. what are security models? In essence, it is a view of the application and its. Information security models encompass various approaches, including multilevel security. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network. Modeling Information Security.
From www.slideserve.com
PPT Security Framework For Cloud Computing PowerPoint Presentation Modeling Information Security “a structured representation of all the information that affects the security of an application. what are security models? In essence, it is a view of the application and its. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. Information security models encompass various approaches, including multilevel. Modeling Information Security.
From www.infotech.com
Develop a Security Operations Strategy InfoTech Research Group Modeling Information Security a security model in information security is a framework or a systematic approach that describes how various security mechanisms. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. Information security models encompass various approaches, including multilevel security. “a structured representation of all the information that affects the security. Modeling Information Security.
From www.researchgate.net
Information security management model Download Scientific Diagram Modeling Information Security Information security models encompass various approaches, including multilevel security. In essence, it is a view of the application and its. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given. Modeling Information Security.
From krebsonsecurity.com
What’s Your Security Maturity Level? Krebs on Security Modeling Information Security “a structured representation of all the information that affects the security of an application. Information security models encompass various approaches, including multilevel security. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide. Modeling Information Security.
From www.vrogue.co
The Osi Model Explained And How To Easily Remember It vrogue.co Modeling Information Security what are security models? a security model in information security is a framework or a systematic approach that describes how various security mechanisms. Information security models encompass various approaches, including multilevel security. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. threat modeling is a. Modeling Information Security.
From solatatech.com
The Security Operating Model A Strategic Approach For Building a More Modeling Information Security the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. In essence, it is a view of the application and its. what are security models? a security model in information security is a framework or a systematic approach that describes how various security mechanisms. Information security models. Modeling Information Security.
From developer.salesforce.com
Salesforce Data Security Model — Explained Visually Salesforce Modeling Information Security threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. a security model in information security is a framework or a systematic approach that describes how various security mechanisms. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s. Modeling Information Security.
From www.joetheitguy.com
ITSM Basics Know Your Information Security Threats! Joe The IT Guy Modeling Information Security what are security models? threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. In essence, it is a view of the application and its. Information security models encompass various approaches, including multilevel security. the cia (confidentiality, integrity, availability) triad is a widely used information security model. Modeling Information Security.
From security-architect.com
Security Governance Models and Structures Security Architects Partners Modeling Information Security Information security models encompass various approaches, including multilevel security. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. what are security models? threat modeling is the process. Modeling Information Security.
From www.csoonline.com
Threat modeling explained A process for anticipating cyber attacks Modeling Information Security Information security models encompass various approaches, including multilevel security. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. what are security models? threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. the cia (confidentiality, integrity, availability). Modeling Information Security.
From www.jirasekonsecurity.com
Vladimir Jirasek on Security and Technology Security model business Modeling Information Security Information security models encompass various approaches, including multilevel security. In essence, it is a view of the application and its. “a structured representation of all the information that affects the security of an application. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. the cia (confidentiality,. Modeling Information Security.
From www.tuexperto.com
G DATA Layered Security, protección contra amenazas para empresas Modeling Information Security In essence, it is a view of the application and its. Information security models encompass various approaches, including multilevel security. a security model in information security is a framework or a systematic approach that describes how various security mechanisms. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network. Modeling Information Security.
From github.com
GitHub 0x736E/threatmodelling Threat Modelling Assets (STRIDE Modeling Information Security Information security models encompass various approaches, including multilevel security. what are security models? threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. In essence, it is a view of the application and its. the cia (confidentiality, integrity, availability) triad is a widely used information security model. Modeling Information Security.
From www.eccouncil.org
What is Cyber Threat Modeling Importance of Threat Modeling ECCouncil Modeling Information Security what are security models? In essence, it is a view of the application and its. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. “a structured representation. Modeling Information Security.
From www.bartleby.com
Types of Security Models bartleby Modeling Information Security the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. Information security models encompass various approaches, including multilevel security. In essence, it is a view of the application and its. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify.. Modeling Information Security.
From michaelonsecurity.blogspot.com
Michael on Security Security Maturity Models (Part 1 of 2) Modeling Information Security what are security models? threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. the cia (confidentiality, integrity, availability) triad is a widely used information security model that. Modeling Information Security.
From www.dreamstime.com
Information Security Model Three Main Components Mind Map, Text Concept Modeling Information Security Information security models encompass various approaches, including multilevel security. “a structured representation of all the information that affects the security of an application. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. what are security models? a security model in information security is a framework or a. Modeling Information Security.
From www.slideserve.com
PPT Security Modeling PowerPoint Presentation, free download ID884918 Modeling Information Security Information security models encompass various approaches, including multilevel security. “a structured representation of all the information that affects the security of an application. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect. Modeling Information Security.
From www.appknox.com
Organizational Dynamics for Info Security & Security Models Modeling Information Security the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. a security model in information security is a framework or a systematic approach that describes how various security mechanisms. “a structured representation of all the information that affects the security of an application. threat modeling is. Modeling Information Security.
From www.nissatech.com
Information Security Nissatech Innovation Centre Modeling Information Security threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. Information security models encompass various approaches, including multilevel security. “a structured representation of all the information that affects the security of an application. threat modeling is a structured process through which it pros can identify potential security. Modeling Information Security.
From solatatech.com
The Security Operating Model A Strategic Approach For Building a More Modeling Information Security Information security models encompass various approaches, including multilevel security. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. In essence, it is a view of the application and its.. Modeling Information Security.
From www.infosectrain.com
What is Information Security Lifecycle Management? InfosecTrain Modeling Information Security Information security models encompass various approaches, including multilevel security. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. In essence, it is a view of the application and its. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify.. Modeling Information Security.
From csmgsc300.blogspot.com
CS Computer Information Systems & Technology Systems Modeling Information Security “a structured representation of all the information that affects the security of an application. In essence, it is a view of the application and its. Information security models encompass various approaches, including multilevel security. threat modeling is a structured process through which it pros can identify potential security threats and vulnerabilities, quantify. a security model in information. Modeling Information Security.
From www.slideserve.com
PPT Security Modeling PowerPoint Presentation, free download ID884918 Modeling Information Security threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. In essence, it is a view of the application and its. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. what are security models? a. Modeling Information Security.
From enterprisesecurityposhibure.blogspot.com
Enterprise Security Enterprise Security Model Modeling Information Security Information security models encompass various approaches, including multilevel security. In essence, it is a view of the application and its. a security model in information security is a framework or a systematic approach that describes how various security mechanisms. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts. Modeling Information Security.
From terrapsychology.com
Build an IT Information Security Strategy InfoTec... (2022) Modeling Information Security threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. In essence, it is a view of the application and its. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. Information security models encompass various approaches, including. Modeling Information Security.
From www.studypool.com
SOLUTION Network security model Studypool Modeling Information Security what are security models? Information security models encompass various approaches, including multilevel security. “a structured representation of all the information that affects the security of an application. the cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and. threat modeling is the process of identifying and sharing. Modeling Information Security.
From searchsecurity.techtarget.com
Cybersecurity maturity model lays out four readiness levels Modeling Information Security In essence, it is a view of the application and its. a security model in information security is a framework or a systematic approach that describes how various security mechanisms. Information security models encompass various approaches, including multilevel security. what are security models? the cia (confidentiality, integrity, availability) triad is a widely used information security model that. Modeling Information Security.
From studylib.net
The Business Model for Information Security Modeling Information Security a security model in information security is a framework or a systematic approach that describes how various security mechanisms. threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or. In essence, it is a view of the application and its. threat modeling is a structured process through. Modeling Information Security.