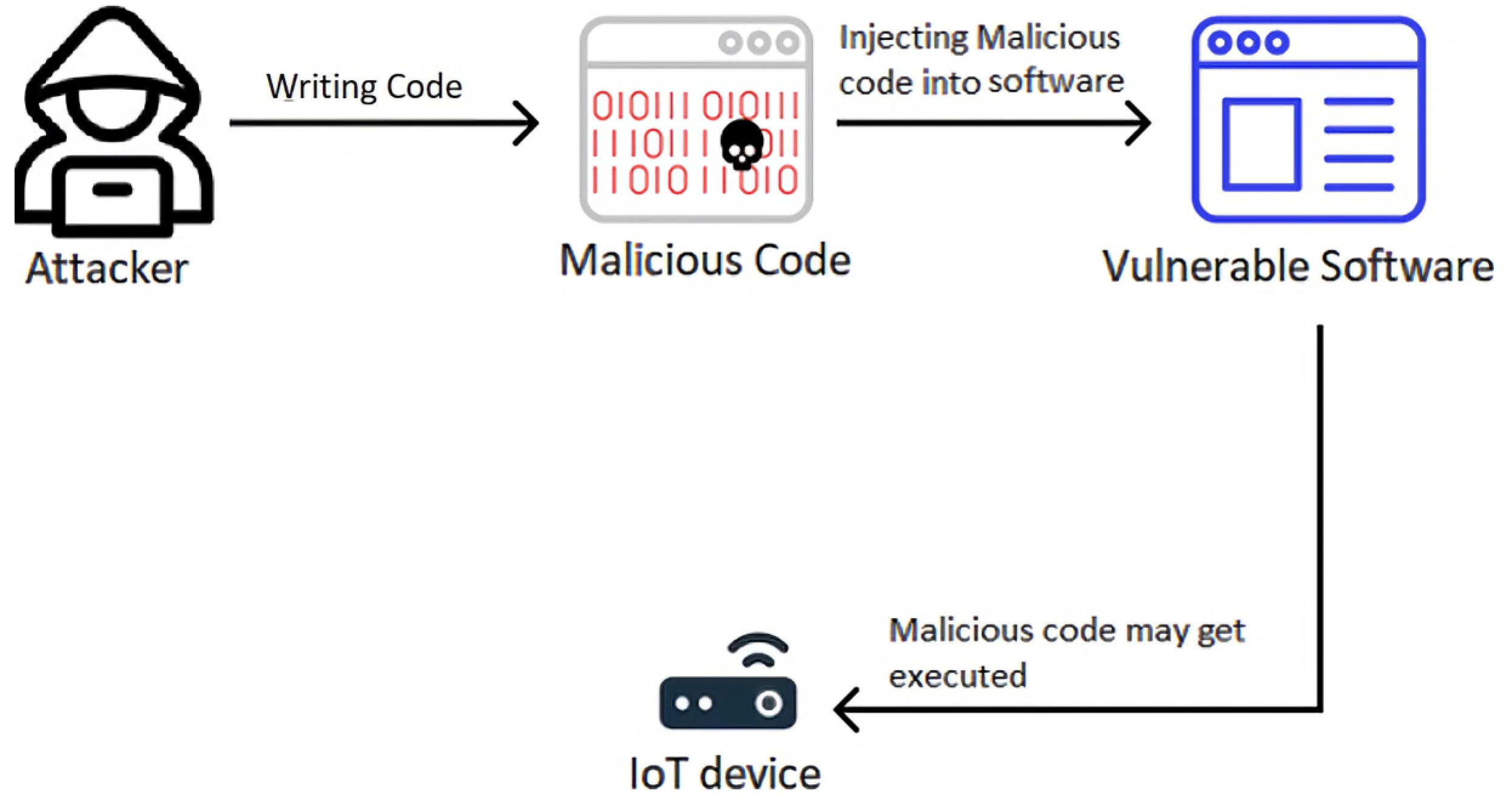
Injection Source Code . The application then interprets or executes the code,. code injection refers to attacks that involve injecting malicious code into an application. We will begin by exploiting a code injection. an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. vulnerabilities leading to code injection are a significant concern in software development. in this lesson, you will learn how code injection works and how to protect your applications against it. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing.
from www.mdpi.com
code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. vulnerabilities leading to code injection are a significant concern in software development. The application then interprets or executes the code,. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. in this lesson, you will learn how code injection works and how to protect your applications against it. We will begin by exploiting a code injection. code injection refers to attacks that involve injecting malicious code into an application.
Sensors Free FullText Code Injection Attacks in WirelessBased of Things (IoT) A
Injection Source Code The application then interprets or executes the code,. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. vulnerabilities leading to code injection are a significant concern in software development. code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. The application then interprets or executes the code,. an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. We will begin by exploiting a code injection. in this lesson, you will learn how code injection works and how to protect your applications against it. code injection refers to attacks that involve injecting malicious code into an application.
From informationsecurityasia.com
What is Code Injection? Injection Source Code in this lesson, you will learn how code injection works and how to protect your applications against it. The application then interprets or executes the code,. code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. vulnerabilities leading to code injection are a significant concern in software development. . Injection Source Code.
From www.globaldots.com
How to Prevent SQL Injection Attacks? Best Practices GlobalDots Injection Source Code in this lesson, you will learn how code injection works and how to protect your applications against it. code injection refers to attacks that involve injecting malicious code into an application. vulnerabilities leading to code injection are a significant concern in software development. The application then interprets or executes the code,. We will begin by exploiting a. Injection Source Code.
From www.mdpi.com
Sensors Free FullText Code Injection Attacks in WirelessBased of Things (IoT) A Injection Source Code in this lesson, you will learn how code injection works and how to protect your applications against it. We will begin by exploiting a code injection. vulnerabilities leading to code injection are a significant concern in software development. code injection differs from command injection in that an attacker is only limited by the functionality of the injected. Injection Source Code.
From www.thesecuritybuddy.com
What is the code injection attack? The Security Buddy Injection Source Code an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. code injection refers to attacks that involve injecting malicious code into an application. The application then interprets or executes the code,. code injection, also known as remote code execution or code evaluation, involves modifying an executable or. Injection Source Code.
From gridinsoft.com
Code Injection Software Attack Examples and Prevention Gridinsoft Injection Source Code in this lesson, you will learn how code injection works and how to protect your applications against it. code injection refers to attacks that involve injecting malicious code into an application. The application then interprets or executes the code,. vulnerabilities leading to code injection are a significant concern in software development. We will begin by exploiting a. Injection Source Code.
From brightsec.com
PHP Code Injection Examples and 4 Prevention Tips Injection Source Code an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. We will begin by exploiting a code injection. code injection refers to attacks that involve injecting malicious code into an application. vulnerabilities leading to code injection are a significant concern in software development. The application then interprets. Injection Source Code.
From www.sourcecodester.com
SQL Injection Attack(hacking) Free source code, tutorials and articles Injection Source Code The application then interprets or executes the code,. code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. vulnerabilities leading to code injection are a significant concern in software. Injection Source Code.
From www.studocu.com
Injection Code Cheat Sheet INJECTION Cheat Sheet 20526 Injection, therapeutic, carpal Injection Source Code code injection refers to attacks that involve injecting malicious code into an application. The application then interprets or executes the code,. in this lesson, you will learn how code injection works and how to protect your applications against it. vulnerabilities leading to code injection are a significant concern in software development. an injection flaw is a. Injection Source Code.
From www.youtube.com
SQL Injection Tutorial [The Code] Part 2/4 YouTube Injection Source Code in this lesson, you will learn how code injection works and how to protect your applications against it. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. . Injection Source Code.
From un-wantedbitch.blogspot.com
injections and infusions coding cheat sheet Injection Source Code code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. We will begin by exploiting a code injection. in this lesson, you will learn how code injection works and how to protect your applications against it. vulnerabilities leading to code injection are a significant concern in software. Injection Source Code.
From 44con.com
Code injections from beginner to advanced for defenders and attackers 44CON Injection Source Code code injection refers to attacks that involve injecting malicious code into an application. code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. vulnerabilities leading to code injection are a significant concern in software development. The application then interprets or executes the code,. an injection flaw is a. Injection Source Code.
From www.youtube.com
What is Code Injection and how to prevent it? YouTube Injection Source Code code injection refers to attacks that involve injecting malicious code into an application. code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. We will begin by exploiting a. Injection Source Code.
From github.com
GitHub patchedcodes/sampleinjection Injection Source Code code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. The application then interprets or executes the code,. in this lesson, you will learn how code injection works and. Injection Source Code.
From sourceht.com
What is Windows Code Injection? Injection Source Code in this lesson, you will learn how code injection works and how to protect your applications against it. an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. We will begin by exploiting a code injection. vulnerabilities leading to code injection are a significant concern in software. Injection Source Code.
From www.invicti.com
What is Code Injection and How to Prevent It Invicti Injection Source Code The application then interprets or executes the code,. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. We will begin by exploiting a code injection. in this lesson, you will learn how code injection works and how to protect your applications against it. code injection, also. Injection Source Code.
From www.slideserve.com
PPT CODE INJECTION PowerPoint Presentation, free download ID8838955 Injection Source Code code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. in this lesson, you will learn how code injection works and how to protect your applications against it. code injection refers to attacks that involve injecting malicious code into an application. an injection flaw is a. Injection Source Code.
From cyware.com
SQL Injection is Still a Critical Attack Vector Cyware Alerts Hacker News Injection Source Code vulnerabilities leading to code injection are a significant concern in software development. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. an injection flaw is a vulnerability. Injection Source Code.
From www.slideserve.com
PPT Code Injection and Software Cracking’s Effect on Network Security PowerPoint Presentation Injection Source Code vulnerabilities leading to code injection are a significant concern in software development. in this lesson, you will learn how code injection works and how to protect your applications against it. The application then interprets or executes the code,. code injection differs from command injection in that an attacker is only limited by the functionality of the injected. Injection Source Code.
From un-wantedbitch.blogspot.com
injections and infusions coding cheat sheet Injection Source Code vulnerabilities leading to code injection are a significant concern in software development. The application then interprets or executes the code,. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. code injection refers to attacks that involve injecting malicious code into an application. code injection, also. Injection Source Code.
From www.slideserve.com
PPT Code Injection PowerPoint Presentation, free download ID2752810 Injection Source Code We will begin by exploiting a code injection. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. vulnerabilities leading to code injection are a significant concern. Injection Source Code.
From br.pinterest.com
What is SQL Injection and How to Prevent in PHP Sql injection, Open source code, Sql Injection Source Code code injection refers to attacks that involve injecting malicious code into an application. code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. in this lesson, you will. Injection Source Code.
From www.youtube.com
INJECTION INFUSION CodingGuidelines_CPT Coding_Clinical Examples medicalcoding CPC Injection Source Code vulnerabilities leading to code injection are a significant concern in software development. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. in this lesson, you will learn how code injection works and how to protect your applications against it. an injection flaw is a vulnerability. Injection Source Code.
From www.aapc.com
Joint Aspiration/Injection Coding AAPC Knowledge Center Injection Source Code The application then interprets or executes the code,. We will begin by exploiting a code injection. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. in this lesson, you will learn how code injection works and how to protect your applications against it. vulnerabilities leading to. Injection Source Code.
From www.pinterest.com
Dependency Injection, Android Studio, Source Code, Injections, Programming, Coding, Pure Injection Source Code vulnerabilities leading to code injection are a significant concern in software development. We will begin by exploiting a code injection. an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. code injection refers to attacks that involve injecting malicious code into an application. code injection, also. Injection Source Code.
From cocomelonc.github.io
Code injection via memory sections and ZwQueueApcThread. Simple C++ malware example. Injection Source Code an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. code injection refers to attacks that involve injecting malicious code into an application. in this lesson,. Injection Source Code.
From www.geeksforgeeks.org
Basic SQL Injection and Mitigation with Example Injection Source Code We will begin by exploiting a code injection. an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. vulnerabilities leading to code injection are a significant concern. Injection Source Code.
From ghost.org
Ghost Code Injection for Analytics Tracking & Meta Tags Injection Source Code vulnerabilities leading to code injection are a significant concern in software development. in this lesson, you will learn how code injection works and how to protect your applications against it. We will begin by exploiting a code injection. code injection refers to attacks that involve injecting malicious code into an application. an injection flaw is a. Injection Source Code.
From www.cyberranges.com
WHAT IS CODE INJECTION AND HOW YOU CAN AVOID IT Injection Source Code The application then interprets or executes the code,. code injection refers to attacks that involve injecting malicious code into an application. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. We will begin by exploiting a code injection. code injection, also known as remote code execution. Injection Source Code.
From ademploy19.gitlab.io
How To Prevent Sql Code Injection Attacks Ademploy19 Injection Source Code We will begin by exploiting a code injection. an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. code injection refers to attacks that involve injecting malicious code into an application. in this lesson, you will learn how code injection works and how to protect your applications. Injection Source Code.
From www.mdpi.com
Sensors Free FullText Code Injection Attacks in WirelessBased of Things (IoT) A Injection Source Code an injection flaw is a vulnerability which allows an attacker to relay malicious code through an application to another system. vulnerabilities leading to code injection are a significant concern in software development. We will begin by exploiting a code injection. The application then interprets or executes the code,. code injection, also known as remote code execution or. Injection Source Code.
From cocomelonc.github.io
Code injection via undocumented Native API functions. Simple C++ example. Injection Source Code code injection refers to attacks that involve injecting malicious code into an application. in this lesson, you will learn how code injection works and how to protect your applications against it. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. We will begin by exploiting a. Injection Source Code.
From www.satutrik.com
Tutorial Sql Injection Satu Trik Injection Source Code code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. The application then interprets or executes the code,. vulnerabilities leading to code injection are a significant concern in software development. code injection refers to attacks that involve injecting malicious code into an application. code injection differs from command. Injection Source Code.
From cocomelonc.github.io
Code injection via ZwCreateSection. Simple C++ malware example. Injection Source Code The application then interprets or executes the code,. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. code injection refers to attacks that involve injecting malicious code into an application. in this lesson, you will learn how code injection works and how to protect your applications. Injection Source Code.
From lassatasty.weebly.com
Microsoft source code analyzer for sql injection tool lassatasty Injection Source Code code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. code injection refers to attacks that involve injecting malicious code into an application. The application then interprets or executes the code,. vulnerabilities leading to code injection are a significant concern in software development. We will begin by exploiting a. Injection Source Code.
From cocomelonc.github.io
Code injection via memory sections. Simple C++ example. Injection Source Code code injection, also known as remote code execution or code evaluation, involves modifying an executable or script containing. in this lesson, you will learn how code injection works and how to protect your applications against it. code injection differs from command injection in that an attacker is only limited by the functionality of the injected language. . Injection Source Code.