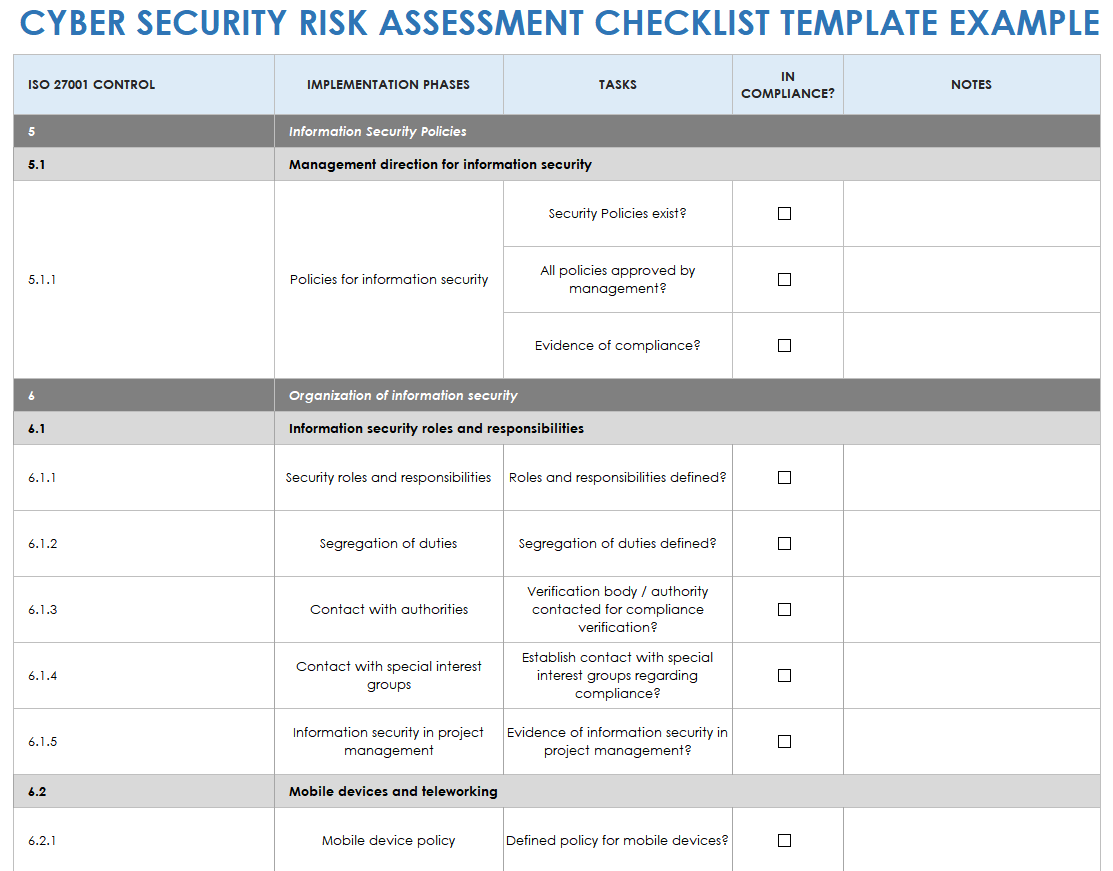
System Security Assessment Checklist . A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Use the following checklist to conduct information security risk assessment questionnaires. Resources relevant to organizations with regulating or regulated aspects. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Information security risk assessment questionnaire checklist. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Axio cybersecurity program assessment tool.
from www.smartsheet.com
Resources relevant to organizations with regulating or regulated aspects. Use the following checklist to conduct information security risk assessment questionnaires. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Information security risk assessment questionnaire checklist. Axio cybersecurity program assessment tool. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment.
Free Cybersecurity Risk Assessment Templates Smartsheet
System Security Assessment Checklist A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Information security risk assessment questionnaire checklist. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Axio cybersecurity program assessment tool. Resources relevant to organizations with regulating or regulated aspects. Use the following checklist to conduct information security risk assessment questionnaires. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your.
From www.sampletemplates.com
FREE 6+ Security Assessment Templates in PDF MS Word System Security Assessment Checklist Use the following checklist to conduct information security risk assessment questionnaires. Resources relevant to organizations with regulating or regulated aspects. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Axio cybersecurity program assessment tool. Information security risk assessment questionnaire checklist. A cyber security risk. System Security Assessment Checklist.
From www.slideteam.net
Information Technology Security Assessment Checklist With Status System Security Assessment Checklist Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Resources relevant to organizations with regulating or regulated aspects. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Use the. System Security Assessment Checklist.
From www.aquasec.com
Cloud Security Assessment 8Step Process and Checklist System Security Assessment Checklist Use the following checklist to conduct information security risk assessment questionnaires. Information security risk assessment questionnaire checklist. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Resources relevant to organizations with regulating or regulated aspects. Axio cybersecurity program assessment tool. A cyber security risk. System Security Assessment Checklist.
From www.databreachtoday.com
Vendor Security Assessment Checklist DataBreachToday System Security Assessment Checklist Axio cybersecurity program assessment tool. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Resources relevant to organizations with regulating or regulated aspects. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Information security risk assessment questionnaire checklist.. System Security Assessment Checklist.
From www.pinterest.co.uk
Building Security Checklist Awesome 28 Of Blank Security Checklist System Security Assessment Checklist Information security risk assessment questionnaire checklist. Axio cybersecurity program assessment tool. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Resources relevant to organizations with regulating or regulated. System Security Assessment Checklist.
From www.slideteam.net
Cyber Security Risk Assessment Checklist Ppt Powerpoint Presentation System Security Assessment Checklist Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Axio cybersecurity program assessment tool. Resources relevant to organizations with regulating or regulated aspects. Use the following checklist to conduct. System Security Assessment Checklist.
From barokoks.github.io
Security Requirements Check List for Information TECHNOLOGY and System Security Assessment Checklist Axio cybersecurity program assessment tool. Resources relevant to organizations with regulating or regulated aspects. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Use the following checklist to conduct information security risk assessment questionnaires. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities. System Security Assessment Checklist.
From connecteam.com
Facility Security Assessment Checklist Template Free PDF Download System Security Assessment Checklist Axio cybersecurity program assessment tool. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Use the following checklist to conduct information security risk assessment questionnaires. Information security risk assessment questionnaire checklist. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough. System Security Assessment Checklist.
From securityauditginkan.blogspot.com
Security Audit Physical Security Audit Checklist Template System Security Assessment Checklist Axio cybersecurity program assessment tool. Use the following checklist to conduct information security risk assessment questionnaires. Information security risk assessment questionnaire checklist. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to. System Security Assessment Checklist.
From www.docformats.com
Security Assessment Template 18+ (Word, Excel & PDF Format) System Security Assessment Checklist Axio cybersecurity program assessment tool. Use the following checklist to conduct information security risk assessment questionnaires. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes. System Security Assessment Checklist.
From anela-tek.com
Cloud Security Assessment Checklist AnelaTek Solutions System Security Assessment Checklist Axio cybersecurity program assessment tool. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Resources relevant to organizations with regulating or regulated aspects. Information security risk assessment questionnaire checklist. Use the following checklist to conduct information security risk assessment questionnaires. Using a cyber security. System Security Assessment Checklist.
From www.bizmanualz.com
IT Security Assessment Checklist Template Word System Security Assessment Checklist Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Use the following checklist to conduct information security risk assessment questionnaires. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Axio cybersecurity program assessment tool. Resources relevant to. System Security Assessment Checklist.
From www.sampletemplates.com
FREE 6+ Security Assessment Templates in PDF MS Word System Security Assessment Checklist Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Axio cybersecurity program assessment tool. Resources relevant to organizations with regulating or regulated aspects. Information security risk assessment questionnaire checklist. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment.. System Security Assessment Checklist.
From www.pinterest.com
Security Assessment Checklist Template Assessment checklist, Security System Security Assessment Checklist Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Resources relevant to organizations with regulating or regulated aspects. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Information security. System Security Assessment Checklist.
From www.template.net
IT Security Assessment Checklist Template in Word, PDF, Google Docs System Security Assessment Checklist Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Axio cybersecurity program assessment tool. Use the following checklist to conduct information security risk assessment questionnaires. Resources relevant to organizations with regulating or regulated aspects. A cyber security risk assessment checklist serves as a roadmap. System Security Assessment Checklist.
From www.slideteam.net
Security Risk Management Assessment Checklist Steps Set Up Advanced System Security Assessment Checklist Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Information security risk assessment questionnaire checklist. Axio cybersecurity program assessment tool. Use the following checklist to conduct information security risk assessment questionnaires. Resources relevant to organizations with regulating or regulated aspects. Using a cyber security. System Security Assessment Checklist.
From www.sampletemplates.com
FREE 6+ Security Assessment Templates in PDF MS Word System Security Assessment Checklist Resources relevant to organizations with regulating or regulated aspects. Use the following checklist to conduct information security risk assessment questionnaires. Axio cybersecurity program assessment tool. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Information security risk assessment questionnaire checklist. Our cyber security assessment checklist. System Security Assessment Checklist.
From safetyculture.com
Facility Security Assessment Checklist PDF SafetyCulture System Security Assessment Checklist A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Information security risk assessment questionnaire checklist. Use the following checklist to conduct information security risk assessment questionnaires. Axio cybersecurity program assessment tool. Resources relevant to organizations with regulating or regulated aspects. Our cyber security assessment checklist will allow you to improve your risk management,. System Security Assessment Checklist.
From hyperproof.io
Conducting an Information Security Risk Assessment Hyperproof System Security Assessment Checklist Resources relevant to organizations with regulating or regulated aspects. Information security risk assessment questionnaire checklist. Axio cybersecurity program assessment tool. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Use the following checklist to conduct information security risk assessment questionnaires. Using a cyber security risk assessment checklist can help you understand your risks. System Security Assessment Checklist.
From mungfali.com
Security Risk Assessment Checklist Template System Security Assessment Checklist Use the following checklist to conduct information security risk assessment questionnaires. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Axio cybersecurity program assessment tool. Resources relevant to organizations with regulating or regulated aspects. Information security risk assessment questionnaire checklist. A cyber security risk assessment. System Security Assessment Checklist.
From www.pinterest.com
Browse Our Example of It Security Audit Checklist Template for Free System Security Assessment Checklist Axio cybersecurity program assessment tool. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Resources relevant to organizations with regulating or regulated aspects. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Using a cyber security risk. System Security Assessment Checklist.
From www.sampletemplates.com
FREE 12+ Sample Security Risk Assessment Templates in PDF MS Word Excel System Security Assessment Checklist Use the following checklist to conduct information security risk assessment questionnaires. Resources relevant to organizations with regulating or regulated aspects. Information security risk assessment questionnaire checklist. Axio cybersecurity program assessment tool. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Using a cyber security risk assessment checklist can help you understand your risks. System Security Assessment Checklist.
From www.datamyte.com
What and How to Make a Network Security Checklist? DataMyte System Security Assessment Checklist Information security risk assessment questionnaire checklist. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Resources relevant to organizations with regulating or regulated aspects. Use the following checklist. System Security Assessment Checklist.
From www.smartsheet.com
Free ISO 27001 Checklists and Templates Smartsheet System Security Assessment Checklist Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Use the following checklist to conduct information security risk assessment questionnaires. Resources relevant to organizations with regulating or regulated aspects. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment.. System Security Assessment Checklist.
From www.pinterest.co.uk
Get Our Image of Security Assessment Checklist Template for Free System Security Assessment Checklist Axio cybersecurity program assessment tool. Information security risk assessment questionnaire checklist. Resources relevant to organizations with regulating or regulated aspects. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Use the following checklist to conduct information security risk assessment questionnaires. Using a cyber security risk assessment checklist can help you understand your risks. System Security Assessment Checklist.
From www.researchgate.net
11 Simple Assessment Checklist for Application Security Architecture System Security Assessment Checklist Resources relevant to organizations with regulating or regulated aspects. Use the following checklist to conduct information security risk assessment questionnaires. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate. System Security Assessment Checklist.
From www.bizmanualz.com
IT Security Assessment Checklist Template System Security Assessment Checklist Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Use the following checklist to conduct information security risk assessment questionnaires. Resources relevant to organizations with regulating or regulated aspects.. System Security Assessment Checklist.
From www.sampletemplates.com
FREE 11+ Sample IT Risk Assessment Templates in PDF MS Word Excel System Security Assessment Checklist Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Information security risk assessment questionnaire checklist. Resources relevant to organizations with regulating or regulated aspects. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Use the following checklist. System Security Assessment Checklist.
From www.docformats.com
Security Assessment Template 18+ (Word, Excel & PDF Format) System Security Assessment Checklist Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Use the following checklist to conduct information security risk assessment questionnaires. Axio cybersecurity program assessment tool. Information security risk assessment questionnaire checklist. Our cyber security assessment checklist will allow you to improve your risk management, help. System Security Assessment Checklist.
From www.pinterest.com
Security Assessment Checklist Template Assessment checklist, Security System Security Assessment Checklist Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. A cyber security risk assessment checklist serves as a roadmap for. System Security Assessment Checklist.
From dremelmicro.com
Security Risk Assessment Checklist Template System Security Assessment Checklist Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Use the following checklist to conduct information security risk assessment questionnaires. Information security risk assessment questionnaire checklist. Axio cybersecurity program assessment tool. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough. System Security Assessment Checklist.
From www.smartsheet.com
Free Cybersecurity Risk Assessment Templates Smartsheet System Security Assessment Checklist Information security risk assessment questionnaire checklist. Axio cybersecurity program assessment tool. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Resources relevant to organizations with regulating or regulated aspects. Using a cyber security risk assessment checklist can help you understand your risks and strategically. System Security Assessment Checklist.
From sprinto.com
ISO 27001 Audit Checklist [Updated] Sprinto System Security Assessment Checklist Information security risk assessment questionnaire checklist. Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. Axio cybersecurity program assessment tool.. System Security Assessment Checklist.
From www.securityhq.com
Cyber Security Checklist [Infographic] SecurityHQ System Security Assessment Checklist Axio cybersecurity program assessment tool. Our cyber security assessment checklist will allow you to improve your risk management, help you identify threats and vulnerabilities for rapid remediation, and elevate your. A cyber security risk assessment checklist serves as a roadmap for conducting a thorough security assessment. Use the following checklist to conduct information security risk assessment questionnaires. Information security risk. System Security Assessment Checklist.
From www.sampletemplates.com
FREE 12+ Sample Security Risk Assessment Templates in PDF MS Word Excel System Security Assessment Checklist Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the. Use the following checklist to conduct information security risk assessment questionnaires. Resources relevant to organizations with regulating or regulated aspects. Information security risk assessment questionnaire checklist. Our cyber security assessment checklist will allow you to improve. System Security Assessment Checklist.