Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location . Using strong firewall and security. Some specific recommended actions for securing your remote access include: Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. How to mitigate risk of overbroad vpn and jump server access. Whether the network threats are intentional or not, they're still predictable. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Encrypting data to prevent theft.
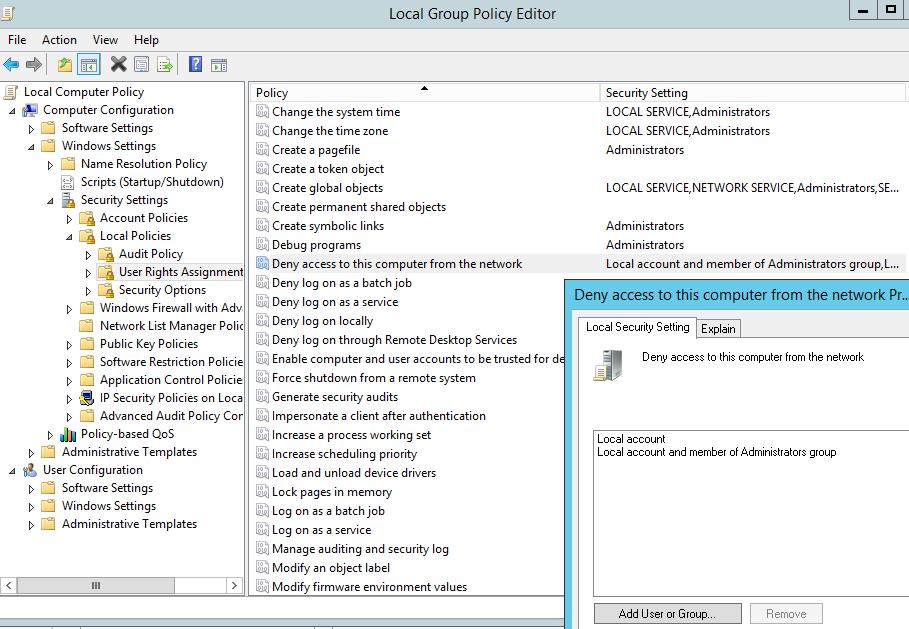
from woshub.com
How to mitigate risk of overbroad vpn and jump server access. Using strong firewall and security. Encrypting data to prevent theft. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Some specific recommended actions for securing your remote access include: Whether the network threats are intentional or not, they're still predictable. Using a zero trust remote access solution that can provide direct access to edge devices without having to open.
Blocking Remote Network Access for Local Accounts Windows OS Hub
Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Whether the network threats are intentional or not, they're still predictable. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Some specific recommended actions for securing your remote access include: Using strong firewall and security. Encrypting data to prevent theft. How to mitigate risk of overbroad vpn and jump server access. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized.
From www.remote-accesss.com
Remote Access Breaches Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Encrypting data to prevent theft. Using strong firewall and security. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Whether the network threats are intentional or not, they're still predictable. How to mitigate risk of overbroad vpn and jump server access. Some specific recommended actions for securing your remote access. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From blog.techprognosis.com
Secure Remote Access Keeping Business Going with Remote Work Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Some specific recommended actions for securing your remote access include: Encrypting data to prevent theft. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Whether the network threats are intentional or not, they're still predictable. How to mitigate risk of overbroad vpn and jump server access. Using a zero trust remote access. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.itpromentor.com
How to securely deploy Remote Desktop Services (RDS) with the Gateway Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location How to mitigate risk of overbroad vpn and jump server access. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Some specific recommended actions for securing your remote access include: Whether the network threats are intentional or not, they're still predictable. Encrypting data to prevent theft. Using a zero trust remote access. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From slideplayer.com
and ppt download Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location How to mitigate risk of overbroad vpn and jump server access. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Using strong firewall and security. Encrypting data to prevent theft. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Some specific recommended. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From networkwalks.com
Firewalls and VPNs Networkwalks Academy Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. How to mitigate risk of overbroad vpn and jump server access. Some specific recommended actions for securing your remote access include: Encrypting data to prevent theft. Using strong firewall and security. Using a zero trust remote access solution that can provide direct access. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From blogs.arubanetworks.com
Remote Access Points Network Beyond the Corporate Campus Aruba Blogs Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Whether the network threats are intentional or not, they're still predictable. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Some specific recommended actions for securing your remote access include: How to mitigate risk of overbroad vpn and jump server access. Encrypting data to prevent theft. Remote access security (sometimes. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From sensusinc.com
Remote System Access The Covid19 Factor and Business’s New Reality Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location How to mitigate risk of overbroad vpn and jump server access. Using strong firewall and security. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Some specific recommended actions for securing your remote access include: Encrypting data to prevent theft. Using a zero trust remote access solution that can provide direct access. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.beyondtrust.com
Privileged Remote Access (onpremises) security Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Encrypting data to prevent theft. Whether the network threats are intentional or not, they're still predictable. Some specific recommended actions for securing your remote access include: How to mitigate risk of overbroad vpn and jump server access. Using strong firewall and security. Using a zero trust remote access solution that can provide direct access to edge devices without having to. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.dnsstuff.com
Network Problems How to Troubleshoot (With Tools) DNSstuff Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Using strong firewall and security. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Some specific recommended actions for securing your remote access include: How to mitigate risk of overbroad vpn and jump server access. Whether the network threats are intentional or not, they're still predictable. Encrypting data to prevent. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.oodlestechnologies.com
Using Blockchain Technology to Strengthen IoT Security Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Some specific recommended actions for securing your remote access include: Whether the network threats are intentional or not, they're still predictable. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Encrypting data to prevent theft. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.perplexity.ai
Cyber security in 5G network Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Using strong firewall and security. Encrypting data to prevent theft. How to mitigate risk of overbroad vpn and jump server access. Some specific recommended actions for securing your remote access include: Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Whether the network threats are intentional or not, they're still predictable. Using. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.getastra.com
Blockchain Security Issues A Complete Guide Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location How to mitigate risk of overbroad vpn and jump server access. Some specific recommended actions for securing your remote access include: Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Using strong firewall. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.alamy.com
Global network flat vector illustration. Wireless access Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Using strong firewall and security. Some specific recommended actions for securing your remote access include: Encrypting data to prevent theft. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. How to mitigate risk. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.beyondtrust.com
Understand the architecture of BeyondTrust Secure Remote Access Cloud Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Whether the network threats are intentional or not, they're still predictable. Some specific recommended actions for securing your remote access include: Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Encrypting data to. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.watchguard.com
Remote Access Point Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Whether the network threats are intentional or not, they're still predictable. Some specific recommended actions for securing your remote access include: Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Using strong firewall and security. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.cowraphoenix.com.au
Ability Network Acquires Squire Park Cafe The Cowra Phoenix Cowra Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Whether the network threats are intentional or not, they're still predictable. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Encrypting data to prevent theft. How to mitigate risk of overbroad vpn and. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From rublon.com
How to Set Up Remote Desktop Gateway Rublon Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location How to mitigate risk of overbroad vpn and jump server access. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Using strong firewall and security. Whether the network threats are intentional or not, they're still predictable. Using a zero trust remote access solution that can provide direct access to edge devices without. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.conceptdraw.com
Remote Networking Diagrams Quickly Create Professional Remote Network Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Encrypting data to prevent theft. Some specific recommended actions for securing your remote access include: How to mitigate risk of overbroad vpn and jump server access. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Whether the network threats are intentional or not, they're still predictable. Using strong firewall and. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.techtarget.com
Remote access vs. sitetosite VPN What's the difference? TechTarget Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Some specific recommended actions for securing your remote access include: Whether the network threats are intentional or not, they're still predictable. Encrypting data to. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From blog.airdroid.com
6 Examples of How Remote Access Can Benefit You Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Using strong firewall and security. How to mitigate risk of overbroad vpn and jump server access. Encrypting data to prevent theft. Whether the network threats are intentional or not, they're still predictable. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Using a zero trust remote access solution that can provide direct. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.conceptdraw.com
Remote Networking Diagrams Quickly Create Professional Remote Network Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Some specific recommended actions for securing your remote access include: Using strong firewall and security. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Whether the network threats are intentional or not, they're. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.vrogue.co
Remote Access Authentication vrogue.co Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location How to mitigate risk of overbroad vpn and jump server access. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Encrypting data to prevent theft. Whether the network threats are intentional or not, they're still predictable. Some specific recommended actions for securing your remote access include: Using strong firewall and. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.alphr.com
Enable Remote Desktop Access in Windows 10 to Log Into Your PC From Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Whether the network threats are intentional or not, they're still predictable. Using strong firewall and security. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Some specific recommended actions for securing your remote access include: Encrypting data to prevent theft. How to mitigate risk of overbroad vpn and jump server. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.pinterest.com
Remote Access VPN The office network. It provides your team the Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location How to mitigate risk of overbroad vpn and jump server access. Some specific recommended actions for securing your remote access include: Using strong firewall and security. Whether the network threats are intentional or not, they're still predictable. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Using a zero trust remote access. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.mdpi.com
Sensors Free FullText Network Threat Detection Using Machine/Deep Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location How to mitigate risk of overbroad vpn and jump server access. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Using strong firewall and security. Encrypting data to prevent theft. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Whether the network. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.greyson.com
Remote Access VPN Guide Greyson Technologies Florida Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Using strong firewall and security. Some specific recommended actions for securing your remote access include: Encrypting data to prevent theft. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Whether the network threats. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.businesstechweekly.com
Remote Network Access Understanding Remote Network Access Protocols Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Using strong firewall and security. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Encrypting data to prevent theft. Whether the network threats are intentional or not, they're still predictable. Some specific recommended. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.conceptdraw.com
Remote Networking Diagrams Quickly Create Professional Remote Network Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Whether the network threats are intentional or not, they're still predictable. Using strong firewall and security. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Some specific recommended actions for securing your remote access include: Encrypting data to prevent theft. Using a zero trust remote access solution that can provide direct access. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.youtube.com
Basic VPN Remote Access using IPsec in Cisco Packet Tracer_Part01 YouTube Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Using strong firewall and security. Some specific recommended actions for securing your remote access include: Whether the network threats are intentional or not, they're still predictable. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Encrypting data to prevent theft. Remote access security (sometimes called “secure remote access”) comprises technologies. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From apstorm.co.uk
Remote Access Solutions ApStorm Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Whether the network threats are intentional or not, they're still predictable. How to mitigate risk of overbroad vpn and jump server access. Encrypting data to prevent theft. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Using strong firewall and security. Using a zero trust remote access solution that can provide direct. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.networkdefenseblog.com
Network Design Scenario 3 Remote Access VPN Design Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Encrypting data to prevent theft. Whether the network threats are intentional or not, they're still predictable. Using strong firewall and security. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. How to mitigate. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From www.vrogue.co
Remote Network Access A Definitive Guide vrogue.co Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Some specific recommended actions for securing your remote access include: Using strong firewall and security. Encrypting data to prevent theft. How to mitigate risk of overbroad vpn and jump server access. Whether the network threats are intentional or not, they're still predictable. Using a zero trust remote access solution that can provide direct access to edge devices without having to. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From tryrdp.com
What is the Remote Desktop Protocol (RDP)? Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Using strong firewall and security. Encrypting data to prevent theft. How to mitigate risk of overbroad vpn and jump server access. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Some specific recommended actions for securing your remote access include: Whether the network threats are intentional or not, they're still predictable. Using. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From community.sophos.com
help. access point in a remote branch unable to reach controller in hq Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location How to mitigate risk of overbroad vpn and jump server access. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Encrypting data to prevent theft. Whether the network threats are intentional or not, they're still predictable. Some specific recommended actions for securing your remote access include: Remote access security (sometimes. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.
From woshub.com
Blocking Remote Network Access for Local Accounts Windows OS Hub Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location Encrypting data to prevent theft. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Some specific recommended actions for securing your remote access include: Using strong firewall and security. Using a zero trust remote access solution that can provide direct access to edge devices without having to open. Whether the network threats. Security Issues Surrounding The Ability Of Users To Access The Network From A Remote Location.