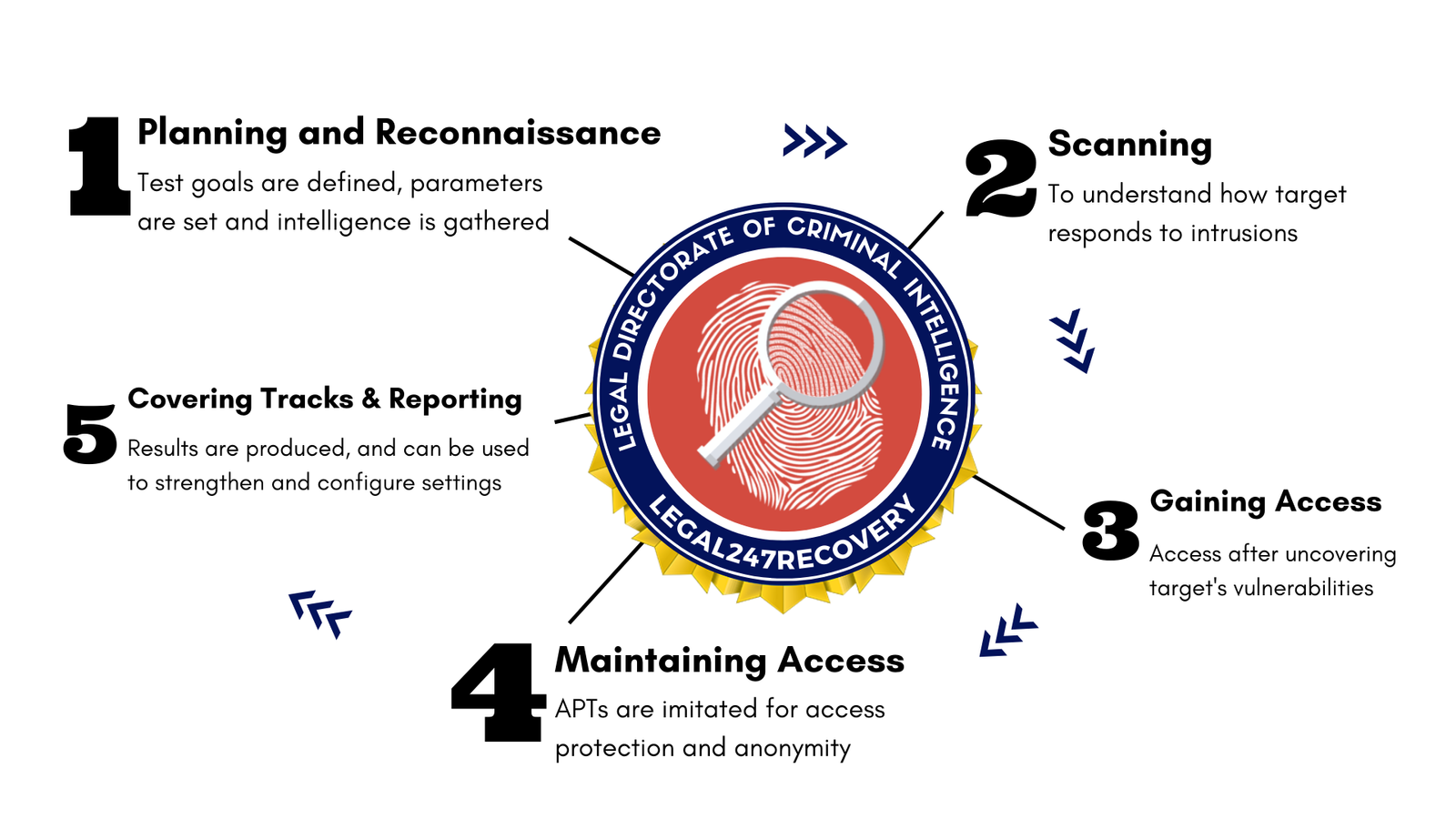
Pen Testing Techniques . Penetration testers are also often responsible for. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. They resemble some of the tools a real hacker would. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords.
from www.legal247recovery.com
They resemble some of the tools a real hacker would. Penetration testers are also often responsible for. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system.
Social Engineering on Accounts and Databases Legal247recovery
Pen Testing Techniques Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. They resemble some of the tools a real hacker would. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Penetration testers are also often responsible for. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks.
From montecampo.co.jp
ソフトウェアテストにおけるセキュリティテストの基本を理解する 株式会社モンテカンポ Pen Testing Techniques Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. They resemble some of the tools a real hacker would. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testing is a cybersecurity forensics technique used to assess an organization's network. Pen Testing Techniques.
From www.seriun.co.uk
Why choose Pen Testing for your business? Seriun IT Support Pen Testing Techniques Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Penetration testing (or pen testing) is a. Pen Testing Techniques.
From www.iansresearch.com
A Guide to Automated Pen Testing Tools IANS Research Pen Testing Techniques Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Penetration testers are also often responsible for. They resemble some of the tools. Pen Testing Techniques.
From sprinto.com
What is Testing? Importance & Types Sprinto Pen Testing Techniques Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Penetration testers are also often responsible for. They resemble some of the tools a real hacker would. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a cybersecurity forensics technique used to assess an organization's. Pen Testing Techniques.
From op-c.net
Pen Testing Essential for Security, Not Just Compliance Pen Testing Techniques Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Penetration testing (or pen testing) is a simulation of a cyberattack that tests. Pen Testing Techniques.
From kratikal.com
Types of Testing Techniques Black, White and Gray Box Pen Testing Techniques A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testers are also often responsible for. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal.. Pen Testing Techniques.
From www.effectivesoft.com
Black Box Testing EffectiveSoft Pen Testing Techniques Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. They resemble some of the tools a real hacker would. Penetration testers are also often responsible for. Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. Penetration testing is a technique. Pen Testing Techniques.
From litelesite.wordpress.com
Set up your Pen Testing/Hacking Lab Network using a Single System litele Pen Testing Techniques Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. They resemble some of the tools a real hacker would. Penetration testers are also often responsible for. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a cybersecurity forensics technique used to assess an organization's. Pen Testing Techniques.
From intigrow.com
Manual vs Automated Pen Testing Pen Testing Techniques Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. Penetration testing is a technique used. Pen Testing Techniques.
From avord.co.uk
Understanding the Testing Process and how to conduct a test Pen Testing Techniques Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testers are also often responsible for.. Pen Testing Techniques.
From www.eccouncil.org
Learn Advanced Testing Techniques in the CPENT Course EC Pen Testing Techniques Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. They resemble some of the tools a real hacker would. Penetration testers are also often responsible for. A penetration test, or pen test, is a security test that launches. Pen Testing Techniques.
From techodrom.com
How to Conduct a Successful Test Techodrom Pen Testing Techniques Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. Penetration testers are also often responsible for. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. A penetration test, or pen test, is a security test that launches a mock cyberattack. Pen Testing Techniques.
From www.linkedin.com
The Significance of Pen Testing in Achieving ISO 27001 Certification Pen Testing Techniques Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal.. Pen Testing Techniques.
From www.digitaldefense.com
When to Use Testing Software, Services, or Both Pen Testing Techniques Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. They resemble some of the tools a real hacker would. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in. Pen Testing Techniques.
From www.iso-registration.com
Pen testing services KVQA Asssesment Pen Testing Techniques Penetration testers are also often responsible for. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. They resemble some of the tools a real hacker would. A penetration test, or pen. Pen Testing Techniques.
From www.legal247recovery.com
Social Engineering on Accounts and Databases Legal247recovery Pen Testing Techniques Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Penetration testing is a cybersecurity forensics technique. Pen Testing Techniques.
From www.mindpointgroup.com
Why Should My Company Consider Pen Testing? Pen Testing Techniques Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. Penetration testers are also often responsible for. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. A penetration test, or pen test, is a security test that launches a mock cyberattack. Pen Testing Techniques.
From go.sikich.com
How to Maximize Your Pen Tests inar Pen Testing Techniques Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Penetration testers are also often responsible for. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. They resemble some of the tools. Pen Testing Techniques.
From www.scribd.com
Chp1 Pen Testing PDF Pen Testing Techniques Penetration testers are also often responsible for. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. They resemble some of the tools a real hacker would. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. A penetration test, or pen test, is a security test that launches. Pen Testing Techniques.
From medium.com
testing, also known as pen testing, is a type of security Pen Testing Techniques Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Penetration. Pen Testing Techniques.
From www.techtarget.com
Pen testing guide Types, steps, methodologies and frameworks TechTarget Pen Testing Techniques Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. They resemble some of the tools a real hacker would. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testers are also often responsible. Pen Testing Techniques.
From purplesec.us
Testing Methodologies 4 Step Framework Pen Testing Techniques Penetration testers are also often responsible for. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. They resemble some of the tools a real hacker would. Penetration testing is a technique. Pen Testing Techniques.
From awainfosec.com
Choosing the Right Mobile App Pen Testing Technique AWA International Pen Testing Techniques Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. Penetration testers are also often responsible for. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and. Pen Testing Techniques.
From thedevcraft.com
Dast Vs Pen Testing The Dev Craft Pen Testing Techniques Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testers are also often responsible for. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Penetration testing (or pen testing) is. Pen Testing Techniques.
From qualysec.com
Exploring the Diverse Arsenal of Testing Types Pen Testing Techniques Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a cybersecurity forensics technique. Pen Testing Techniques.
From cybercatch.com
PenTest Powered by CyberCatch Pen Testing Techniques Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. They resemble some of the tools a real hacker would. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in. Pen Testing Techniques.
From jerait.co.uk
Pen Test Life Cycle How To Triumph Jera IT Pen Testing Techniques A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Penetration testing is a cybersecurity forensics technique. Pen Testing Techniques.
From www.researchgate.net
(PDF) An Empirical Comparison of PenTesting Tools for Detecting Pen Testing Techniques Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testing (or pen testing) is a. Pen Testing Techniques.
From es.scribd.com
Procedure for Dye Testing (Kn) Rev1 Pen Testing Techniques A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses.. Pen Testing Techniques.
From aegtraining.com
Lead Pen Test Professional Training Exam Certification Pen Testing Techniques Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Penetration testers are also often responsible for. Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Penetration testing (or pen testing) is. Pen Testing Techniques.
From www.redlegg.com
Resource Library Pen Testing Techniques Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. They resemble some of the tools. Pen Testing Techniques.
From www.coursereport.com
What Is Testing? Course Report Pen Testing Techniques Penetration testers are also often responsible for. Penetration testing is a cybersecurity forensics technique used to assess an organization's network perimeter and internal. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. They resemble some of the tools a real hacker would. Penetration testing is a technique used in cybersecurity to identify vulnerabilities. Pen Testing Techniques.
From www.torii-security.fr
Tests d’intrusion tout ce qu’il faut savoir Torii Security Pen Testing Techniques Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. They resemble some of the tools a real hacker would. A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testing (or pen testing) is a simulation of a cyberattack that. Pen Testing Techniques.
From dokumen.tips
(PDF) Pen Testing Framework for IoT Devices DOKUMEN.TIPS Pen Testing Techniques Penetration testing is a technique used in cybersecurity to identify vulnerabilities in applications or networks. Penetration testers are also often responsible for. Pen test tools verify security loopholes by scanning data encryption techniques and testing logins and passwords. They resemble some of the tools a real hacker would. Penetration testing (or pen testing) is a simulation of a cyberattack that. Pen Testing Techniques.
From www.chilmarkresearch.com
Whitebox testing as a type of testing Chilmark Research Pen Testing Techniques A penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Penetration testing (or pen testing) is a simulation of a cyberattack that tests a computer system, network, or application for security weaknesses. Penetration testers are also often responsible for. Penetration testing is a technique used in cybersecurity to. Pen Testing Techniques.