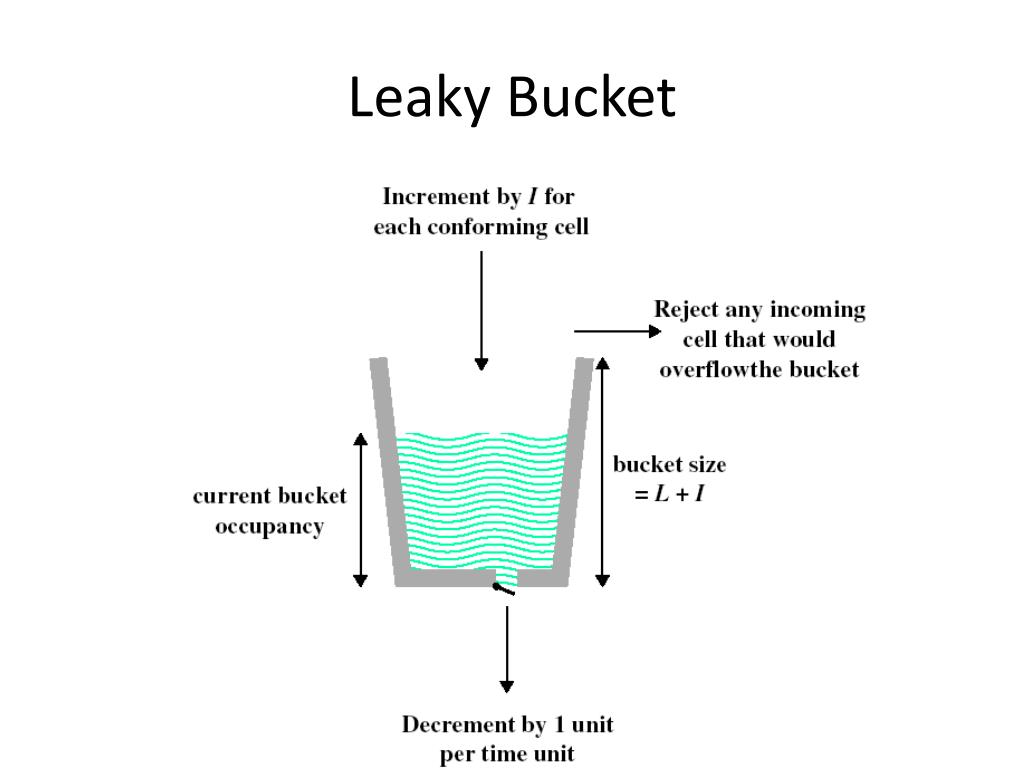
Leaky Bucket And Token Bucket Numericals . Visual guide to leaky and token bucket algorithms. They help manage the rate of traffic flow in a network, but they do so in. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1. Token bucket ensures predictable traffic shaping as it allows for setting. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a.
from www.slideserve.com
Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. Visual guide to leaky and token bucket algorithms. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket ensures predictable traffic shaping as it allows for setting. For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1. They help manage the rate of traffic flow in a network, but they do so in. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a.
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download ID3429699
Leaky Bucket And Token Bucket Numericals Visual guide to leaky and token bucket algorithms. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and. Visual guide to leaky and token bucket algorithms. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. Token bucket ensures predictable traffic shaping as it allows for setting. For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. They help manage the rate of traffic flow in a network, but they do so in.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket And Token Bucket Numericals They help manage the rate of traffic flow in a network, but they do so in. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests. Leaky Bucket And Token Bucket Numericals.
From www.scribd.com
Traffic Shaping Leaky Bucket and Token Bucket PDF Leaky Bucket And Token Bucket Numericals Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1. They help manage the rate of traffic flow in a network, but they do so in. Token bucket can send large bursts at a. Leaky Bucket And Token Bucket Numericals.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket And Token Bucket Numericals Token bucket ensures predictable traffic shaping as it allows for setting. They help manage the rate of traffic flow in a network, but they do so in. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Visual guide to leaky and token bucket algorithms. Two common algorithms employed in rate. Leaky Bucket And Token Bucket Numericals.
From www.youtube.com
Leaky Bucket Algorithm Token Bucket Algorithm Leaky Bucket Vs Token Bucket Congestion Leaky Bucket And Token Bucket Numericals Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. They help manage the rate of traffic flow in a network, but they do so in. Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. Token bucket and leaky bucket algorithms are two of the. Leaky Bucket And Token Bucket Numericals.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Leaky Bucket And Token Bucket Numericals Token bucket ensures predictable traffic shaping as it allows for setting. For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1. They help manage the rate of traffic flow in a network, but they do so in. Token bucket can send large bursts at a faster rate while leaky. Leaky Bucket And Token Bucket Numericals.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Leaky Bucket And Token Bucket Numericals Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket ensures predictable traffic shaping as it allows for setting. They help manage the rate of traffic flow in a network, but they do so in. Visual guide to leaky and token bucket algorithms. Token bucket can send large bursts. Leaky Bucket And Token Bucket Numericals.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket And Token Bucket Numericals Visual guide to leaky and token bucket algorithms. Token bucket ensures predictable traffic shaping as it allows for setting. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. Token bucket and leaky bucket are two. Leaky Bucket And Token Bucket Numericals.
From www.slideserve.com
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download ID3429699 Leaky Bucket And Token Bucket Numericals Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. For a host machine that uses the token bucket algorithm for congestion control, the token bucket. Leaky Bucket And Token Bucket Numericals.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket And Token Bucket Numericals Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Token bucket and leaky bucket algorithms are two of the methods used. Leaky Bucket And Token Bucket Numericals.
From www.researchgate.net
Token bucket algorithm Download Scientific Diagram Leaky Bucket And Token Bucket Numericals Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. Token bucket ensures predictable traffic shaping as it allows for setting. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket and leaky bucket algorithms are two of the methods used often in managing. Leaky Bucket And Token Bucket Numericals.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Difference HINDI URDU Leaky Bucket And Token Bucket Numericals Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket can send. Leaky Bucket And Token Bucket Numericals.
From slideplayer.com
CS 4700 / CS 5700 Network Fundamentals ppt download Leaky Bucket And Token Bucket Numericals Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1. Visual guide to leaky and token bucket algorithms. Token bucket and leaky bucket algorithms are two of the methods used. Leaky Bucket And Token Bucket Numericals.
From www.youtube.com
19 Leaky and Token Buckets YouTube Leaky Bucket And Token Bucket Numericals Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. Visual guide to leaky and token bucket algorithms. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and. Token bucket. Leaky Bucket And Token Bucket Numericals.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket And Token Bucket Numericals Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Token bucket ensures predictable traffic shaping as it allows for setting. Visual guide to leaky. Leaky Bucket And Token Bucket Numericals.
From www.slideserve.com
PPT ATM CONGESTION CONTROL PowerPoint Presentation, free download ID7057132 Leaky Bucket And Token Bucket Numericals Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and. Token bucket ensures predictable traffic shaping as it allows for setting. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Two common algorithms employed in rate limiting are the token bucket and the leaky. Leaky Bucket And Token Bucket Numericals.
From www.chegg.com
Solved Write a C++ program to simulate the behavior of the Leaky Bucket And Token Bucket Numericals Token bucket ensures predictable traffic shaping as it allows for setting. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Token. Leaky Bucket And Token Bucket Numericals.
From www.thetechnicaltalk.com
Differentiate between leaky bucket and token bucket methods of traffic shaping The Technical Talk Leaky Bucket And Token Bucket Numericals Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. For a host machine that uses the token bucket algorithm for congestion. Leaky Bucket And Token Bucket Numericals.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Difference YouTube Leaky Bucket And Token Bucket Numericals Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates,. Leaky Bucket And Token Bucket Numericals.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket And Token Bucket Numericals Visual guide to leaky and token bucket algorithms. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket and leaky bucket algorithms are two of the methods used often in. Leaky Bucket And Token Bucket Numericals.
From www.youtube.com
Traffic Shaping Leaky Bucket Token Bucket Improve QoS Computer Networks Part 3 YouTube Leaky Bucket And Token Bucket Numericals Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. For a host machine that uses the. Leaky Bucket And Token Bucket Numericals.
From www.thetechnicaltalk.com
Differentiate between leaky bucket and token bucket methods of traffic shaping The Technical Talk Leaky Bucket And Token Bucket Numericals They help manage the rate of traffic flow in a network, but they do so in. Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. For a host machine that uses the token bucket algorithm for congestion control,. Leaky Bucket And Token Bucket Numericals.
From www.slideshare.net
Chap24 Leaky Bucket And Token Bucket Numericals Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests. Leaky Bucket And Token Bucket Numericals.
From www.slideserve.com
PPT CprE 458/558 RealTime Systems PowerPoint Presentation, free download ID262586 Leaky Bucket And Token Bucket Numericals Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and. They help manage the rate of traffic flow in a network, but they do so in. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket can send large bursts. Leaky Bucket And Token Bucket Numericals.
From www.youtube.com
Token and Leaky Bucket Algorithm YouTube Leaky Bucket And Token Bucket Numericals Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket ensures predictable traffic shaping as it allows for setting. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Two. Leaky Bucket And Token Bucket Numericals.
From towardsdev.com
Leaky Bucket vs Token Bucket in Rate Limiting Algorithms by David Lee Towards Dev Leaky Bucket And Token Bucket Numericals The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and. They help manage the rate of traffic flow in a network, but. Leaky Bucket And Token Bucket Numericals.
From www.scribd.com
Numerical On Leaky& Token Bucket PDF Leaky Bucket And Token Bucket Numericals The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Token bucket and leaky bucket algorithms are two of the methods used often in managing. Leaky Bucket And Token Bucket Numericals.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and closed loop) YouTube Leaky Bucket And Token Bucket Numericals Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and. For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1. Token bucket can send. Leaky Bucket And Token Bucket Numericals.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket And Token Bucket Numericals The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and. Two common algorithms employed in rate limiting are the token bucket and. Leaky Bucket And Token Bucket Numericals.
From slideplayer.com
Introduction to Computer Networks ppt download Leaky Bucket And Token Bucket Numericals Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1. Token bucket can send large bursts at a. Leaky Bucket And Token Bucket Numericals.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Algorithms API7.ai Leaky Bucket And Token Bucket Numericals For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1. Token bucket ensures predictable traffic shaping as it allows for setting. They help manage the rate of traffic flow in a network, but they do so in. Token bucket and leaky bucket are two algorithms used for network traffic. Leaky Bucket And Token Bucket Numericals.
From dcandcn.blogspot.com
What is Token Bucket Algorithm? Leaky Bucket And Token Bucket Numericals They help manage the rate of traffic flow in a network, but they do so in. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. Token bucket and leaky bucket algorithms are two of the. Leaky Bucket And Token Bucket Numericals.
From www.linqz.io
Leaky/Token bucket algorithm for flow control Learn INQuiZitively Leaky Bucket And Token Bucket Numericals Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. For a host machine that uses the token bucket algorithm for congestion control, the token bucket. Leaky Bucket And Token Bucket Numericals.
From www.youtube.com
Leaky And Token Bucket Algorithms YouTube Leaky Bucket And Token Bucket Numericals The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Token bucket ensures predictable traffic shaping as it allows for setting. They help manage the rate of traffic flow in a network, but they do so in. Token bucket and leaky. Leaky Bucket And Token Bucket Numericals.
From medium.com
Token Bucket vs Leaky Bucket. Token Bucket and Leaky Bucket are two… by Apurva Agrawal Medium Leaky Bucket And Token Bucket Numericals Visual guide to leaky and token bucket algorithms. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue. Leaky Bucket And Token Bucket Numericals.
From lowleveldesign.io
Design a Distributed Scalable API Rate Limiter Leaky Bucket And Token Bucket Numericals Two common algorithms employed in rate limiting are the token bucket and the leaky bucket. They help manage the rate of traffic flow in a network, but they do so in. Token bucket ensures predictable traffic shaping as it allows for setting. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic. Leaky Bucket And Token Bucket Numericals.