Length Extension Attack Use . A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. What is a length extension attack? In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a type of attack where an attacker can use the length of a hashed.
from www.studocu.com
What is a length extension attack? In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a type of attack where an attacker can use the length of a hashed. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that.
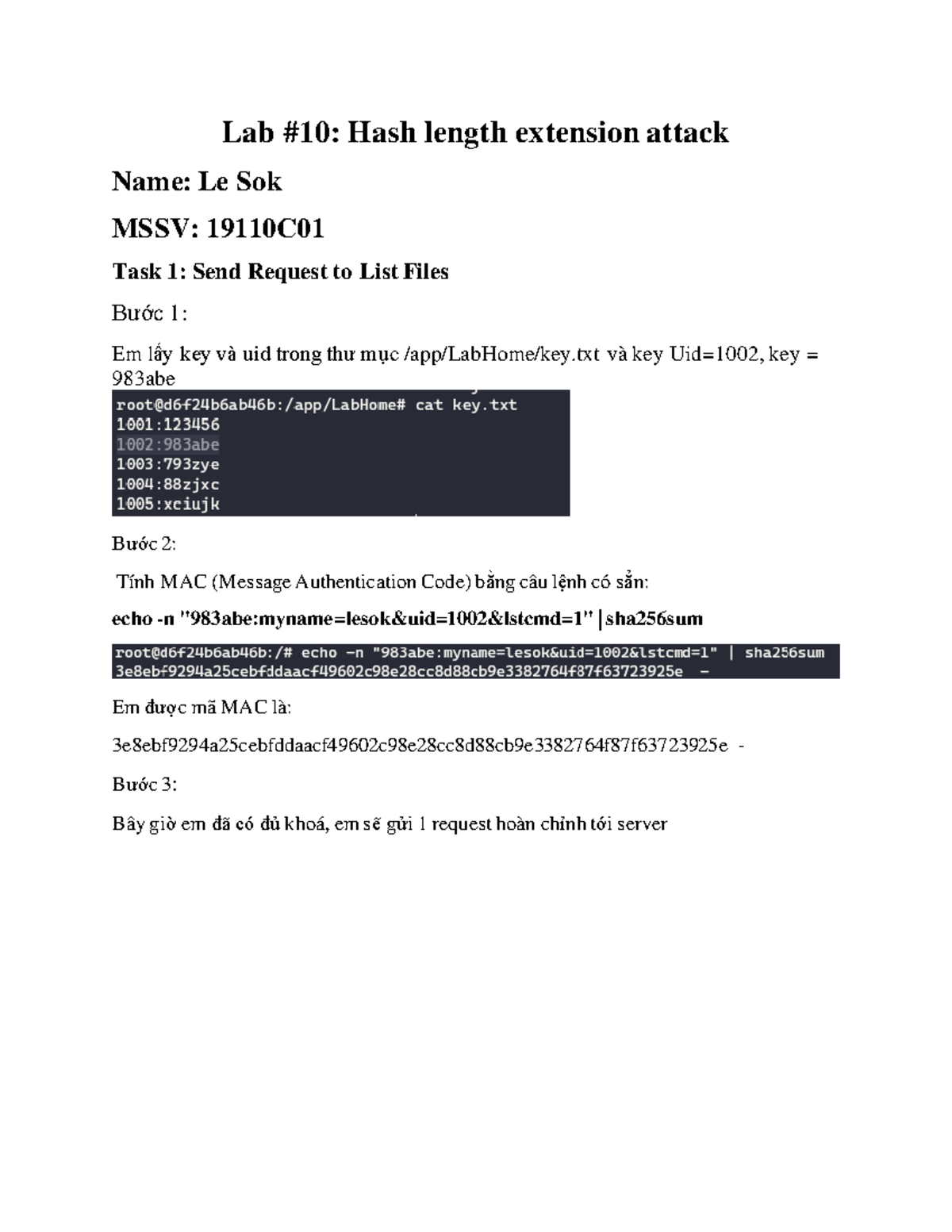
Hash Length Extension Attack Lab Lab 10 Hash length extension attack Name Le Sok MSSV
Length Extension Attack Use Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. What is a length extension attack? A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a type of attack where an attacker can use the length of a hashed. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that.
From fyoeetxik.blob.core.windows.net
Length Extension Attack Md5 Python at Edwin Whiting blog Length Extension Attack Use In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension. Length Extension Attack Use.
From fyoeetxik.blob.core.windows.net
Length Extension Attack Md5 Python at Edwin Whiting blog Length Extension Attack Use A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. What is a. Length Extension Attack Use.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free download ID1618604 Length Extension Attack Use Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a type of attack where an attacker can use the length of a hashed. What is a length extension attack? In describing this, i’ll note that there are some meaningful differences between sha1 and md4,. Length Extension Attack Use.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free download ID1618604 Length Extension Attack Use A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. What is a length extension attack? Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions,. Length Extension Attack Use.
From slideplayer.com
OneWay Hash Functions ppt download Length Extension Attack Use Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. What is a. Length Extension Attack Use.
From www.slideshare.net
Hash length extension attacks PPT Length Extension Attack Use What is a length extension attack? Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. A length extension attack is a type of attack where an attacker can use the length of. Length Extension Attack Use.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free download ID1618604 Length Extension Attack Use What is a length extension attack? A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as. Length Extension Attack Use.
From www.studocu.com
Crypto Hash Length Ext Hash Length Extension Attack Lab Copyright © 2019 by Wenliang Du. This Length Extension Attack Use A length extension attack is a type of attack where an attacker can use the length of a hashed. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. In describing this, i’ll. Length Extension Attack Use.
From www.slideserve.com
PPT Cryptography Crash Course PowerPoint Presentation, free download ID2199875 Length Extension Attack Use A length extension attack is a type of attack where an attacker can use the length of a hashed. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. What is a length. Length Extension Attack Use.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free download ID1618604 Length Extension Attack Use Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. What is a length extension attack? In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a type of attack where an attacker can use. Length Extension Attack Use.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free download ID1618604 Length Extension Attack Use A length extension attack is a type of attack where an attacker can use the length of a hashed. What is a length extension attack? A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness,. Length Extension Attack Use.
From danq.me
Length Extension Attack Demonstration (Video) Dan Q Length Extension Attack Use Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. What is a length extension attack? In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a type of attack where an attacker can use. Length Extension Attack Use.
From www.studocu.com
Hash Length Extension Attack Lab Lab 10 Hash length extension attack Name Le Sok MSSV Length Extension Attack Use Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a type of attack where an attacker can use the length of a hashed. What is a length extension attack? A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage. Length Extension Attack Use.
From www.synopsys.com
a SHA1 MAC using a lengthextension attack in Python Synopsys Length Extension Attack Use A length extension attack is a type of attack where an attacker can use the length of a hashed. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. What is a length. Length Extension Attack Use.
From studylib.net
Hash Length Extension Attacks Explained Length Extension Attack Use Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a type of attack where an attacker can use the length of a hashed. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. What is a length. Length Extension Attack Use.
From coinmarketcap.com
The Hidden Risks of Hash Functions Length Extension Attacks and ServerSide Security Length Extension Attack Use Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a type of attack where an attacker can use the length of a hashed. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. What. Length Extension Attack Use.
From www.slideserve.com
PPT Cryptography Crash Course PowerPoint Presentation, free download ID2199875 Length Extension Attack Use In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. What is a length extension attack? A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking. Length Extension Attack Use.
From www.studypool.com
SOLUTION Hash length extension attack questions Studypool Length Extension Attack Use A length extension attack is a type of attack where an attacker can use the length of a hashed. What is a length extension attack? Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. In describing this, i’ll note that there are some meaningful differences between sha1 and md4,. Length Extension Attack Use.
From github.com
GitHub leesangmin144/lengthextensionattack Length Extension Attack Use A length extension attack is a type of attack where an attacker can use the length of a hashed. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. In describing this, i’ll. Length Extension Attack Use.
From github.com
GitHub PortSwigger/lengthextensionattacks Length extension attacks in Burp Suite Length Extension Attack Use A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a type of attack where an attacker can use the length of a hashed. Length extension attacks are. Length Extension Attack Use.
From www.youtube.com
Length Extension Attack YouTube Length Extension Attack Use A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. What is a length extension attack? Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as. Length Extension Attack Use.
From slides.com
Hash Length Extension Attacks Length Extension Attack Use A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. What is a length extension attack? Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions,. Length Extension Attack Use.
From hxenhqlet.blob.core.windows.net
Length Extension Attack Write Up at Emilia Reeves blog Length Extension Attack Use A length extension attack is a type of attack where an attacker can use the length of a hashed. What is a length extension attack? Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage. Length Extension Attack Use.
From medium.com
The Partial Preimage Technique. How to Use Length Extension Attacks For… by sCrypt Coinmonks Length Extension Attack Use A length extension attack is a type of attack where an attacker can use the length of a hashed. What is a length extension attack? A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically. Length Extension Attack Use.
From danq.me
Length Extension Attack Demonstration Dan Q Length Extension Attack Use What is a length extension attack? Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. A length extension attack is a type of attack where an attacker can use the length of. Length Extension Attack Use.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free download ID1618604 Length Extension Attack Use In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a type of attack where an attacker can use the length of a hashed. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A. Length Extension Attack Use.
From www.youtube.com
Mastering Length Extension Attacks Exploiting Hash Functions YouTube Length Extension Attack Use What is a length extension attack? A length extension attack is a type of attack where an attacker can use the length of a hashed. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage. Length Extension Attack Use.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free download ID1618604 Length Extension Attack Use In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. What is a length extension attack? A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions,. Length Extension Attack Use.
From github.com
GitHub charliejuc/length_extension_attack_sha256 Laboratory to test length extension attack Length Extension Attack Use What is a length extension attack? A length extension attack is a type of attack where an attacker can use the length of a hashed. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically. Length Extension Attack Use.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free download ID1618604 Length Extension Attack Use What is a length extension attack? In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. A length extension attack is a type of attack where an attacker can use the length of. Length Extension Attack Use.
From hxenhqlet.blob.core.windows.net
Length Extension Attack Write Up at Emilia Reeves blog Length Extension Attack Use Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a type of attack where an attacker can use the length of a hashed. What is a length extension attack? A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage. Length Extension Attack Use.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free download ID1618604 Length Extension Attack Use Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. What is a length extension attack? A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as. Length Extension Attack Use.
From keepcoding.io
¿Qué es un length extension attack? KeepCoding Bootcamps Length Extension Attack Use A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. A length extension attack is a type of attack where an attacker can use the length of a hashed. Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. In describing this, i’ll. Length Extension Attack Use.
From www.youtube.com
Length Extension Attack Final YouTube Length Extension Attack Use A length extension attack is a type of attack where an attacker can use the length of a hashed. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking advantage of their. In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. Length extension attacks are. Length Extension Attack Use.
From www.slideserve.com
PPT 2 Length Extension Attack PowerPoint Presentation, free download ID1618604 Length Extension Attack Use In describing this, i’ll note that there are some meaningful differences between sha1 and md4, such as endianness, digest length,. What is a length extension attack? Length extension attacks are a type of cryptographic attack that exploit the properties of certain hash functions, specifically those that. A length extension attack is a sophisticated cryptographic exploit that targets hash functions, taking. Length Extension Attack Use.