Bike Hack The Box Walkthrough . Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture and edit. Tech tools in our tool database. This is a simple walkthrough for completing the bike. To find the open tcp ports, we run the command nmap. In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). This box is an introduction into sql database injection. Video walkthrough for the bike machine from tier one of the @hackthebox starting. Learn how to complete bike in hackthebox in this tutorial. Our journey begins with a simple nmap scan. Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. Htb labs — tier 0— “fawn” machine walkthrough | by: Learn the basics of penetration testing: This challenge was a great…
from www.ctfiot.com
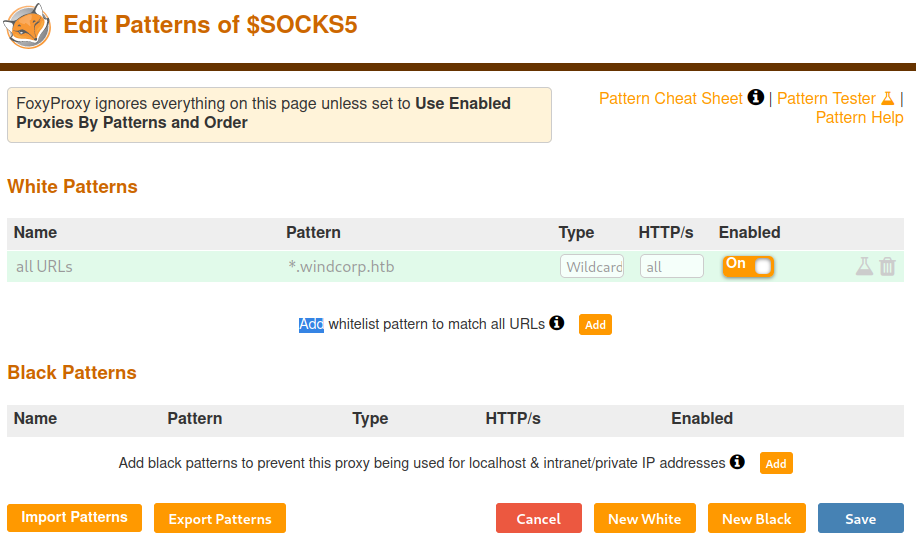
In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture and edit. Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. Learn the basics of penetration testing: This is a simple walkthrough for completing the bike. Video walkthrough for the bike machine from tier one of the @hackthebox starting. Htb labs — tier 0— “fawn” machine walkthrough | by: Tech tools in our tool database. Learn how to complete bike in hackthebox in this tutorial. This box is an introduction into sql database injection.
Hack the Box Walkthroughs Anubis Using SliverC2 CTF导航
Bike Hack The Box Walkthrough In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture and edit. Learn how to complete bike in hackthebox in this tutorial. Learn the basics of penetration testing: This challenge was a great… This is a simple walkthrough for completing the bike. Video walkthrough for the bike machine from tier one of the @hackthebox starting. In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture and edit. This box is an introduction into sql database injection. Tech tools in our tool database. Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). Our journey begins with a simple nmap scan. Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. To find the open tcp ports, we run the command nmap. Htb labs — tier 0— “fawn” machine walkthrough | by:
From www.youtube.com
BIKE HACK Share the Wear YouTube Bike Hack The Box Walkthrough In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). This box is an introduction into sql database injection. Learn the basics of penetration testing: Htb labs — tier 0— “fawn” machine walkthrough | by: Video walkthrough for the bike machine from tier one of the @hackthebox starting.. Bike Hack The Box Walkthrough.
From www.youtube.com
Hack The Box Walkthrough Crocodile YouTube Bike Hack The Box Walkthrough This challenge was a great… Htb labs — tier 0— “fawn” machine walkthrough | by: In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). Learn the basics of penetration testing: Video walkthrough for the bike machine from tier one of the @hackthebox starting. This box is an. Bike Hack The Box Walkthrough.
From erichogue.ca
Hack The Box Walkthrough Encoding Eric Hogue's Blog Bike Hack The Box Walkthrough Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. This challenge was a great… In this blog post, i’ll walk you through the steps i took to. Bike Hack The Box Walkthrough.
From regan-o.medium.com
[HTB] Writeup Photobomb Hack the Box Walkthrough Tutorial Beginner Bike Hack The Box Walkthrough Tech tools in our tool database. Our journey begins with a simple nmap scan. This challenge was a great… In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture. Bike Hack The Box Walkthrough.
From medium.com
List Hack The Box Walkthroughs Curated by Cooper Timewell Medium Bike Hack The Box Walkthrough Our journey begins with a simple nmap scan. Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. Tech tools in our tool database. This is a simple walkthrough for completing the bike. To find the open tcp ports, we run the command nmap. Htb labs — tier 0—. Bike Hack The Box Walkthrough.
From heartburn.dev
Hack the Box Walkthroughs Hathor Bike Hack The Box Walkthrough Tech tools in our tool database. Video walkthrough for the bike machine from tier one of the @hackthebox starting. This challenge was a great… Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. This is a simple walkthrough for completing the bike. In this blog post, i’ll walk. Bike Hack The Box Walkthrough.
From erichogue.ca
Hack The Box Walkthrough Health Eric Hogue's Blog Bike Hack The Box Walkthrough This box is an introduction into sql database injection. Our journey begins with a simple nmap scan. Learn the basics of penetration testing: In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction. Bike Hack The Box Walkthrough.
From medium.com
Devel — Hack The Box — Walkthrough by Cooper Timewell Medium Bike Hack The Box Walkthrough Htb labs — tier 0— “fawn” machine walkthrough | by: To find the open tcp ports, we run the command nmap. Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. This is a simple walkthrough for completing the bike. This challenge was a great… Learn how to complete. Bike Hack The Box Walkthrough.
From medium.com
Hack The Box Walkthrough Legacy. Hack The Box is an online platform Bike Hack The Box Walkthrough In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). Video walkthrough for the bike machine from tier one of the @hackthebox starting. Learn how to complete bike in hackthebox in this tutorial. This challenge was a great… Tech tools in our tool database. Htb labs — tier. Bike Hack The Box Walkthrough.
From d3u5vu1t.medium.com
Hack the Box Busqueda Walkthrough by D3u5Vu1t Medium Bike Hack The Box Walkthrough Video walkthrough for the bike machine from tier one of the @hackthebox starting. Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. Learn the basics of penetration testing: This is a simple walkthrough for completing the bike. This box is an introduction into sql database injection. In this. Bike Hack The Box Walkthrough.
From hajirs-blog.gitbook.io
Sau My Pentesting Journey Bike Hack The Box Walkthrough This is a simple walkthrough for completing the bike. Learn the basics of penetration testing: This challenge was a great… This box is an introduction into sql database injection. In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture and edit. Our journey begins with a simple nmap scan. Learn how. Bike Hack The Box Walkthrough.
From erichogue.ca
Hack The Box Walkthrough Shoppy Eric Hogue's Blog Bike Hack The Box Walkthrough Learn how to complete bike in hackthebox in this tutorial. Tech tools in our tool database. In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). Our journey begins with a simple nmap scan. To find the open tcp ports, we run the command nmap. This challenge was. Bike Hack The Box Walkthrough.
From fdlucifer.github.io
HackTheBoxwalkthrough[routerspace] fdvoid0's blog Bike Hack The Box Walkthrough Video walkthrough for the bike machine from tier one of the @hackthebox starting. In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). Our journey begins with a simple nmap scan. In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy. Bike Hack The Box Walkthrough.
From www.youtube.com
Hack The Box Walkthrough Crocodile YouTube Bike Hack The Box Walkthrough Learn the basics of penetration testing: Htb labs — tier 0— “fawn” machine walkthrough | by: In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). This challenge was a great… This box is an introduction into sql database injection. Our journey begins with a simple nmap scan.. Bike Hack The Box Walkthrough.
From www.hackingarticles.in
Hack the Box Help Walkthrough Hacking Articles Bike Hack The Box Walkthrough Learn how to complete bike in hackthebox in this tutorial. Learn the basics of penetration testing: Tech tools in our tool database. This is a simple walkthrough for completing the bike. Htb labs — tier 0— “fawn” machine walkthrough | by: Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier. Bike Hack The Box Walkthrough.
From fdlucifer.github.io
HackTheBoxwalkthrough[catch] fdvoid0's blog Bike Hack The Box Walkthrough Video walkthrough for the bike machine from tier one of the @hackthebox starting. Htb labs — tier 0— “fawn” machine walkthrough | by: In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture and edit. This is a simple walkthrough for completing the bike. Tech tools in our tool database. To. Bike Hack The Box Walkthrough.
From medium.com
Hack the Box Zipping Walkthrough by Al Azhar Rizqi Medium Bike Hack The Box Walkthrough Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. This challenge was a great… This is a simple walkthrough for completing the bike. This box is an. Bike Hack The Box Walkthrough.
From www.youtube.com
ACCESS (Hack The Box) Walkthrough LIVE HACKING!! YouTube Bike Hack The Box Walkthrough Learn how to complete bike in hackthebox in this tutorial. Htb labs — tier 0— “fawn” machine walkthrough | by: Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack. Bike Hack The Box Walkthrough.
From erichogue.ca
Hack The Box Walkthrough Socket Eric Hogue's Blog Bike Hack The Box Walkthrough Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. Learn how to complete bike in hackthebox in this tutorial. In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). Video walkthrough for the bike machine from. Bike Hack The Box Walkthrough.
From medium.com
Precious — Hack The Box Machine Walkthrough by Mike Zylka Medium Bike Hack The Box Walkthrough Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. This box is an introduction into sql database injection. To find the open tcp ports, we run the command nmap. Our journey begins with a simple nmap scan. In this guide, we’ll walk through using burpsuite, a powerful web. Bike Hack The Box Walkthrough.
From heartburn.dev
Hack the Box Walkthroughs Hathor Bike Hack The Box Walkthrough Learn how to complete bike in hackthebox in this tutorial. Htb labs — tier 0— “fawn” machine walkthrough | by: This challenge was a great… Learn the basics of penetration testing: To find the open tcp ports, we run the command nmap. This is a simple walkthrough for completing the bike. This box is an introduction into sql database injection.. Bike Hack The Box Walkthrough.
From erichogue.ca
Hack The Box Walkthrough PC Eric Hogue's Blog Bike Hack The Box Walkthrough Learn the basics of penetration testing: Tech tools in our tool database. Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. This is a simple walkthrough for completing the bike. To find the open tcp ports, we run the command nmap. In this guide, we’ll walk through using. Bike Hack The Box Walkthrough.
From erichogue.ca
Hack The Box Walkthrough Inject Eric Hogue's Blog Bike Hack The Box Walkthrough Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. Htb labs — tier 0— “fawn” machine walkthrough | by: Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. In this guide, we’ll walk through using burpsuite,. Bike Hack The Box Walkthrough.
From dante-cyber.medium.com
Bike Hack The Box Walkthrough by D.M. Medium Bike Hack The Box Walkthrough Learn how to complete bike in hackthebox in this tutorial. In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). Tech tools in our tool database. Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. Htb. Bike Hack The Box Walkthrough.
From heartburn.dev
Hack the Box Walkthroughs Hathor Bike Hack The Box Walkthrough Learn the basics of penetration testing: Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. This box is an introduction into sql database injection. Tech tools in our tool database. Learn how to complete bike in hackthebox in this tutorial. Introduction we have captured 6 flags from the. Bike Hack The Box Walkthrough.
From www.youtube.com
Escape (HACK THE BOX) walkthrough YouTube Bike Hack The Box Walkthrough Video walkthrough for the bike machine from tier one of the @hackthebox starting. Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. Our journey begins with a simple nmap scan. Learn how to complete bike in hackthebox in this tutorial. To find the open tcp ports, we run. Bike Hack The Box Walkthrough.
From www.ctfiot.com
Hack the Box Walkthroughs Anubis Using SliverC2 CTF导航 Bike Hack The Box Walkthrough Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. Htb labs — tier 0— “fawn” machine walkthrough | by: Learn the basics of penetration testing: This is a simple walkthrough for completing the bike. In this blog post, i’ll walk you through the steps i took to solve. Bike Hack The Box Walkthrough.
From erichogue.ca
Hack The Box Walkthrough Antique Eric Hogue's Blog Bike Hack The Box Walkthrough This is a simple walkthrough for completing the bike. Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. Tech tools in our tool database. This box is an introduction into sql database injection. In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction. Bike Hack The Box Walkthrough.
From heartburn.dev
Hack the Box Walkthroughs Anubis Using SliverC2 Bike Hack The Box Walkthrough Learn how to complete bike in hackthebox in this tutorial. This box is an introduction into sql database injection. Video walkthrough for the bike machine from tier one of the @hackthebox starting. In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture and edit. This is a simple walkthrough for completing. Bike Hack The Box Walkthrough.
From systemweakness.com
Hack The Box Secret Walkthrough. A walkthrough of the Secret box on Bike Hack The Box Walkthrough In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). Video walkthrough for the bike machine from tier one of the @hackthebox starting. Htb labs — tier 0— “fawn” machine walkthrough | by: Tech tools in our tool database. Learn the basics of penetration testing: To find the. Bike Hack The Box Walkthrough.
From www.youtube.com
Redeemer Hack The Box // Walkthrough & Solution // Kali Linux YouTube Bike Hack The Box Walkthrough To find the open tcp ports, we run the command nmap. In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture and edit. Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. Htb labs — tier 0— “fawn” machine. Bike Hack The Box Walkthrough.
From erichogue.ca
Hack The Box Walkthrough Armageddon Eric Hogue's Blog Bike Hack The Box Walkthrough This challenge was a great… In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture and edit. Our journey begins with a simple nmap scan. Learn the basics of penetration testing: Learn how to complete bike in hackthebox in this tutorial. Video walkthrough for the bike machine from tier one of. Bike Hack The Box Walkthrough.
From medium.com
Hack The Box Unified walkthrough🫴🫳 by soulxploit Medium Bike Hack The Box Walkthrough Introduction we have captured 6 flags from the tier 0 series, and are on the 1st of the tier 1 series. Tech tools in our tool database. In this guide, we’ll walk through using burpsuite, a powerful web vulnerability scanner, in conjunction with foxyproxy to capture and edit. Our journey begins with a simple nmap scan. This is a simple. Bike Hack The Box Walkthrough.
From erichogue.ca
Hack The Box Walkthrough Interface Eric Hogue's Blog Bike Hack The Box Walkthrough This challenge was a great… This box is an introduction into sql database injection. Htb labs — tier 0— “fawn” machine walkthrough | by: To find the open tcp ports, we run the command nmap. In this blog post, i’ll walk you through the steps i took to solve the “cap” box on hack the box (htb). Learn the basics. Bike Hack The Box Walkthrough.
From heartburn.dev
Hack the Box Walkthroughs Hathor Bike Hack The Box Walkthrough Cyberalp0 the machine covers some tasks that will give you a walkthrough into finally finding the flag and solving the machine. Htb labs — tier 0— “fawn” machine walkthrough | by: This is a simple walkthrough for completing the bike. Video walkthrough for the bike machine from tier one of the @hackthebox starting. Tech tools in our tool database. In. Bike Hack The Box Walkthrough.