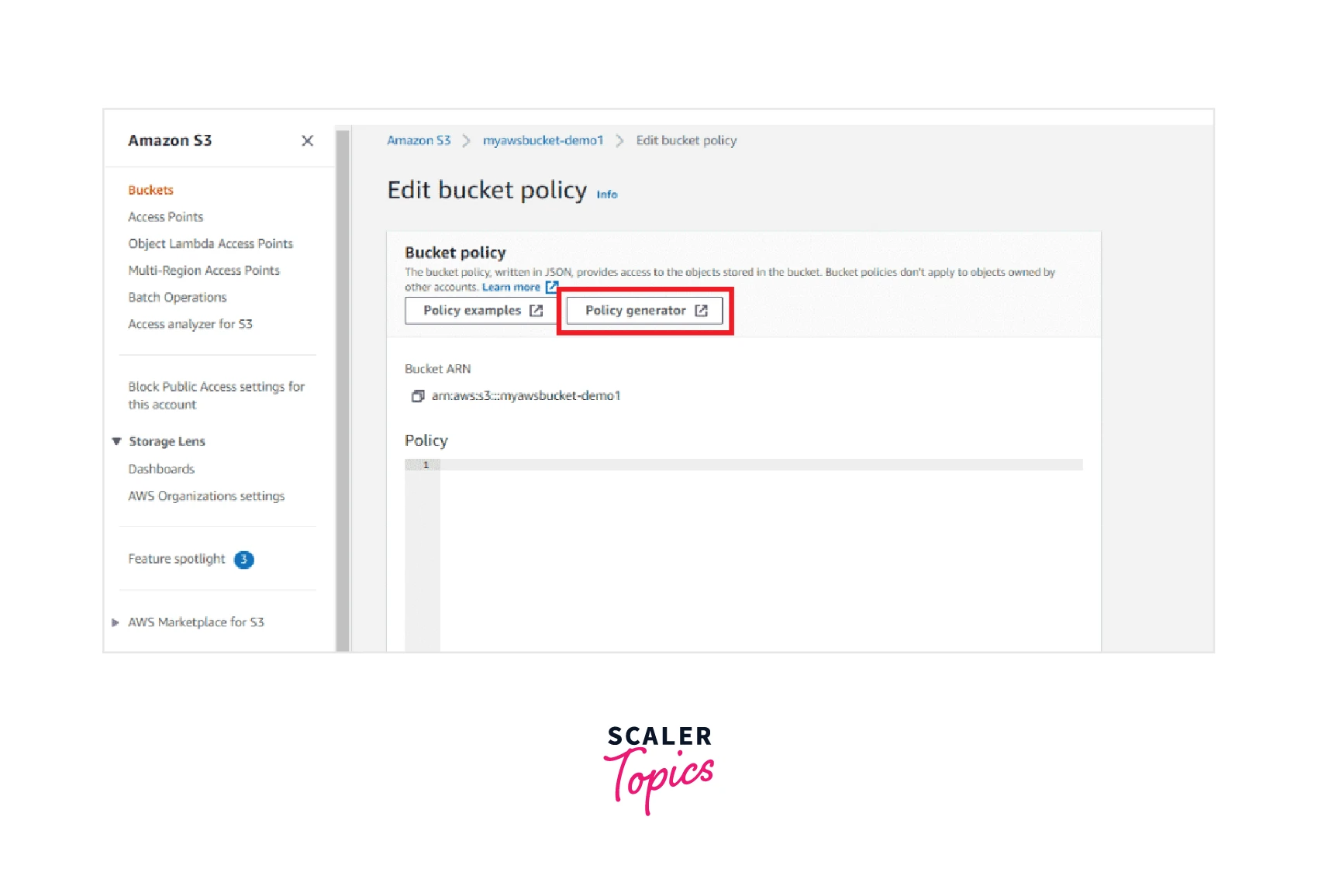
S3 Bucket Policy Wildcard Principal . The danger here is that if you specify principal: For more information about condition. * in your policy, you’ve just authorized any aws customer to access your bucket. For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: * (which effectively means anyone). S3 bucket policies contain five key.
from www.scaler.com
The danger here is that if you specify principal: For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. S3 bucket policies contain five key. * (which effectively means anyone). Identify amazon s3 bucket policies that allow a wildcard identity such as principal: To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. For more information about condition. * in your policy, you’ve just authorized any aws customer to access your bucket.
S3 Bucket Policy Scaler Topics
S3 Bucket Policy Wildcard Principal For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. The danger here is that if you specify principal: When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. * (which effectively means anyone). For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. * in your policy, you’ve just authorized any aws customer to access your bucket. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. For more information about condition. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: S3 bucket policies contain five key.
From bluexp.netapp.com
S3 Access for Objects With Different Permissions in an S3 Bucket S3 Bucket Policy Wildcard Principal * in your policy, you’ve just authorized any aws customer to access your bucket. For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: When you specify users in a principal element, you cannot use a wildcard (*) to mean. S3 Bucket Policy Wildcard Principal.
From openvpn.net
Tutorial Configure AWS S3 bucket for CloudConnexa Log Streaming S3 Bucket Policy Wildcard Principal * (which effectively means anyone). * in your policy, you’ve just authorized any aws customer to access your bucket. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. To grant or deny. S3 Bucket Policy Wildcard Principal.
From exobasjsp.blob.core.windows.net
Bucket Policy Principals at Donald Buenrostro blog S3 Bucket Policy Wildcard Principal * in your policy, you’ve just authorized any aws customer to access your bucket. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: For more information about condition. When you specify users. S3 Bucket Policy Wildcard Principal.
From stackoverflow.com
node.js Configuring AWS S3 bucket policies Stack Overflow S3 Bucket Policy Wildcard Principal For more information about condition. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. * in your policy, you’ve just authorized any aws customer to access your bucket. S3 bucket policies contain five key. * (which effectively means anyone). When you specify users in a. S3 Bucket Policy Wildcard Principal.
From exobasjsp.blob.core.windows.net
Bucket Policy Principals at Donald Buenrostro blog S3 Bucket Policy Wildcard Principal For more information about condition. * in your policy, you’ve just authorized any aws customer to access your bucket. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. The danger here is that if you specify principal: To. S3 Bucket Policy Wildcard Principal.
From exonfoezl.blob.core.windows.net
S3 Bucket Policy Null Condition at Ned Jones blog S3 Bucket Policy Wildcard Principal For more information about condition. For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. * in your policy, you’ve just authorized any aws customer to access your bucket. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: When you specify users in a principal element, you cannot use. S3 Bucket Policy Wildcard Principal.
From klafcwoph.blob.core.windows.net
S3 Bucket Policy Resource at Shelby Sullivan blog S3 Bucket Policy Wildcard Principal For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. S3 bucket policies contain five key. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
S3 Bucket Policies YouTube S3 Bucket Policy Wildcard Principal The danger here is that if you specify principal: When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. * (which effectively means anyone). * in your policy, you’ve just authorized any aws customer to access your bucket. For policies that use amazon s3 condition keys for object and bucket operations, see. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
Creating S3 Bucket and S3 Bucket Policy using AWS Cloud Formation YouTube S3 Bucket Policy Wildcard Principal * (which effectively means anyone). For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. For more information about condition. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. The danger here is that if you specify principal:. S3 Bucket Policy Wildcard Principal.
From exonfoezl.blob.core.windows.net
S3 Bucket Policy Null Condition at Ned Jones blog S3 Bucket Policy Wildcard Principal S3 bucket policies contain five key. For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. For more information about condition. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. * in your policy, you’ve just authorized any. S3 Bucket Policy Wildcard Principal.
From medium.com
S3. bucket policy hands on — by Pradeep Dhanush Medium S3 Bucket Policy Wildcard Principal To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. * in your policy, you’ve just authorized any aws customer to access your bucket. Identify amazon s3 bucket policies that allow a. S3 Bucket Policy Wildcard Principal.
From dev.to
AWS S3 Master Classes AWS S3 Bucket Policy AWS S3 Tutorial S3 Bucket Policy Wildcard Principal To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. * in your policy, you’ve just authorized any aws customer to access your bucket. For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. To grant or deny permissions to a set of. S3 Bucket Policy Wildcard Principal.
From stackoverflow.com
amazon web services AWS S3 Bucket what is the difference between S3 Bucket Policy Wildcard Principal For more information about condition. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate. S3 Bucket Policy Wildcard Principal.
From turbot.com
S3 bucket policies support for custom policies and guardrails S3 Bucket Policy Wildcard Principal To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. For more information about condition. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: * (which effectively means anyone). To grant or deny permissions to a set of objects, you can use wildcard characters (*) in. S3 Bucket Policy Wildcard Principal.
From www.scaler.com
S3 Bucket Policy Scaler Topics S3 Bucket Policy Wildcard Principal When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: * in your policy, you’ve just authorized any aws customer to access your bucket. To grant or deny permissions to a set of objects, you can use wildcard characters. S3 Bucket Policy Wildcard Principal.
From joikwjjgz.blob.core.windows.net
Aws S3 Cross Account Bucket Policy at Lawrence Meyer blog S3 Bucket Policy Wildcard Principal S3 bucket policies contain five key. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. For more information about condition. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. For policies that use amazon s3 condition keys for object and. S3 Bucket Policy Wildcard Principal.
From devsday.ru
AWS Cross Account S3 Access Through Lambda Functions DevsDay.ru S3 Bucket Policy Wildcard Principal For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. S3 bucket policies contain five key. Identify amazon s3 bucket policies that allow a wildcard identity such as principal:. S3 Bucket Policy Wildcard Principal.
From medium.com
Troubleshooting S3 bucket policies by Teri Radichel Cloud Security S3 Bucket Policy Wildcard Principal To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. For more information about condition. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. S3 bucket policies contain five key. For policies that use amazon s3 condition. S3 Bucket Policy Wildcard Principal.
From laptrinhx.com
How to Use Bucket Policies and Apply DefenseinDepth to Help Secure S3 Bucket Policy Wildcard Principal To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. For more information about condition. S3 bucket policies contain five key. * in your policy, you’ve just authorized any aws customer to access your bucket. To prevent access to your amazon s3 buckets made by aws. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
AWS S3 Tutorial (Part 3) How to set up Access Control on S3 ? IAM S3 Bucket Policy Wildcard Principal When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. * (which effectively means anyone). For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions.. S3 Bucket Policy Wildcard Principal.
From joiaqjpdx.blob.core.windows.net
Aws S3 Storage Policy at Rochelle Koch blog S3 Bucket Policy Wildcard Principal For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. The danger here is that if you specify principal: To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. S3 bucket policies contain five key. * in your policy,. S3 Bucket Policy Wildcard Principal.
From stackoverflow.com
Amazon S3 Change bucket policy with Java SDK Stack Overflow S3 Bucket Policy Wildcard Principal For more information about condition. S3 bucket policies contain five key. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: * (which effectively means anyone). When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. To prevent access to your amazon s3 buckets made by aws identity and. S3 Bucket Policy Wildcard Principal.
From exobasjsp.blob.core.windows.net
Bucket Policy Principals at Donald Buenrostro blog S3 Bucket Policy Wildcard Principal Identify amazon s3 bucket policies that allow a wildcard identity such as principal: * (which effectively means anyone). For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. * in your policy, you’ve just authorized any aws customer to access your bucket. To prevent access to your amazon s3 buckets made by aws. S3 Bucket Policy Wildcard Principal.
From medium.com
AWS DVA9 S3 Advanced. IAM Policies, Bucket Policies, ACLs, S3… by S3 Bucket Policy Wildcard Principal To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. * (which effectively means anyone). For policies that use amazon s3 condition keys for object and. S3 Bucket Policy Wildcard Principal.
From klafcwoph.blob.core.windows.net
S3 Bucket Policy Resource at Shelby Sullivan blog S3 Bucket Policy Wildcard Principal * (which effectively means anyone). For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. S3 bucket policies contain five key. For more information about condition. When you specify. S3 Bucket Policy Wildcard Principal.
From exobasjsp.blob.core.windows.net
Bucket Policy Principals at Donald Buenrostro blog S3 Bucket Policy Wildcard Principal For more information about condition. For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. * (which effectively means anyone). To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. To prevent access to your amazon s3 buckets made. S3 Bucket Policy Wildcard Principal.
From blog.quickapi.cloud
如何使用S3生命周期策略清空大型S3 Bucket How to Empty Large S3 Buckets using S3 S3 Bucket Policy Wildcard Principal * in your policy, you’ve just authorized any aws customer to access your bucket. For more information about condition. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns). S3 Bucket Policy Wildcard Principal.
From loehxsikb.blob.core.windows.net
Aws S3 Bucket Policy Default Deny at Phyllis Sears blog S3 Bucket Policy Wildcard Principal Identify amazon s3 bucket policies that allow a wildcard identity such as principal: For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. S3 bucket policies contain five key. For more information about condition. *. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
Create S3 bucket Upload files Create S3 Bucket Policy Enable S3 Bucket Policy Wildcard Principal The danger here is that if you specify principal: When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: * in your policy, you’ve just authorized any aws customer to access your bucket. For policies that use amazon s3. S3 Bucket Policy Wildcard Principal.
From exoaxdnop.blob.core.windows.net
S3 List Bucket Policy Example at Linda Benedetto blog S3 Bucket Policy Wildcard Principal The danger here is that if you specify principal: S3 bucket policies contain five key. To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. * in your policy, you’ve just authorized any aws customer to access your bucket. For policies that use amazon s3 condition keys for object and. S3 Bucket Policy Wildcard Principal.
From simplypsychology.org
kedély meglátásokkal Ártatlan aws s3 bucket arn Kölcsönadó Tömbje kiéhezett S3 Bucket Policy Wildcard Principal * (which effectively means anyone). For more information about condition. S3 bucket policies contain five key. The danger here is that if you specify principal: To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. When you specify users in a principal element, you cannot use a wildcard (*) to. S3 Bucket Policy Wildcard Principal.
From www.youtube.com
S3 bucket policy to make it Public YouTube S3 Bucket Policy Wildcard Principal To prevent access to your amazon s3 buckets made by aws identity and access management (iam) entities, designate specific permissions. The danger here is that if you specify principal: For more information about condition. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. * (which effectively means anyone). For policies that. S3 Bucket Policy Wildcard Principal.
From exodkftil.blob.core.windows.net
Aws S3 Bucket Policies Examples at Guy Deaton blog S3 Bucket Policy Wildcard Principal To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. S3 bucket policies contain five key. When you specify users in a principal element, you cannot use a wildcard (*) to mean all users. * in your policy, you’ve just authorized any aws customer to access. S3 Bucket Policy Wildcard Principal.
From towardsdatascience.com
How to Copy between Encrypted S3 Buckets Cross Account by Evan S3 Bucket Policy Wildcard Principal For more information about condition. Identify amazon s3 bucket policies that allow a wildcard identity such as principal: The danger here is that if you specify principal: For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. * in your policy, you’ve just authorized any aws customer to access your bucket. When you. S3 Bucket Policy Wildcard Principal.
From loehxsikb.blob.core.windows.net
Aws S3 Bucket Policy Default Deny at Phyllis Sears blog S3 Bucket Policy Wildcard Principal Identify amazon s3 bucket policies that allow a wildcard identity such as principal: To grant or deny permissions to a set of objects, you can use wildcard characters (*) in amazon resource names (arns) and other values. For more information about condition. For policies that use amazon s3 condition keys for object and bucket operations, see the following examples. *. S3 Bucket Policy Wildcard Principal.