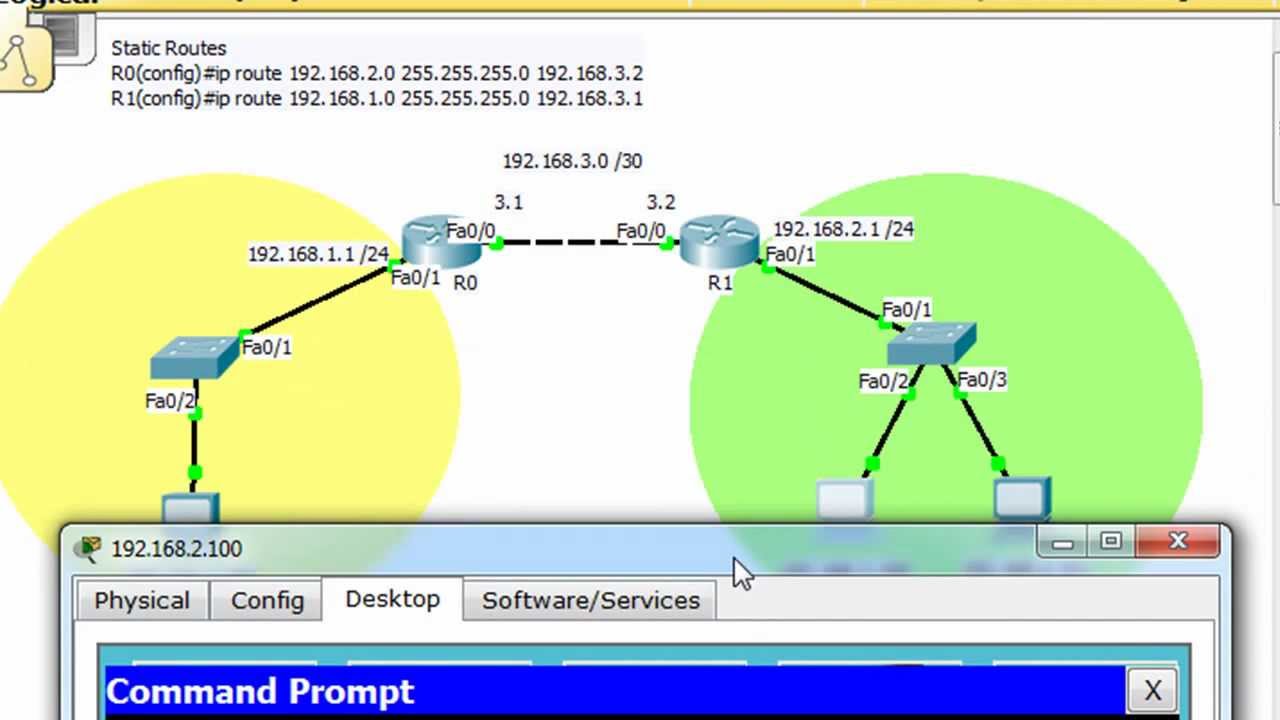
Access Control List Codes . By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. We have two commands to create a standard access list. Access control list explained with examples. Learn cisco acls configuration commands with their. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. This document describes how ip access control lists (acls) can filter network traffic. This tutorial explains how to configure cisco access control lists. Only two acls are permitted per network. It also contains brief descriptions of the.
from www.aga88.com
Learn cisco acls configuration commands with their. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. It also contains brief descriptions of the. This tutorial explains how to configure cisco access control lists. Access control list explained with examples. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. We have two commands to create a standard access list. Only two acls are permitted per network. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. This document describes how ip access control lists (acls) can filter network traffic.
Sicuro noioso screpolatura access control list packet tracer
Access Control List Codes By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Access control list explained with examples. We have two commands to create a standard access list. This tutorial explains how to configure cisco access control lists. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. Learn cisco acls configuration commands with their. Only two acls are permitted per network. This document describes how ip access control lists (acls) can filter network traffic. It also contains brief descriptions of the. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices.
From www.g2.com
What Is an Access Control List (ACL)? Types and Examples Access Control List Codes By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Learn cisco acls configuration commands with their. Only two acls are permitted per network. We have two commands to create a standard access list. Cisco acls are single or multiple permit/deny statements that filter. Access Control List Codes.
From pharmakondergi.com
An Access Control List ACL Download Scientific Diagram Access Control List Codes Only two acls are permitted per network. It also contains brief descriptions of the. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. We have two commands to create a standard access list. Cisco acls are single or multiple permit/deny statements that filter. Access Control List Codes.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator Access Control List Codes Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. Learn cisco acls configuration commands with their. Access control list explained with examples. Only two acls are permitted per network. It also contains brief descriptions of the. We have two commands to create a. Access Control List Codes.
From techcommunity.microsoft.com
Active Directory Access Control List Attacks and Defense Microsoft Access Control List Codes We have two commands to create a standard access list. Only two acls are permitted per network. It also contains brief descriptions of the. This tutorial explains how to configure cisco access control lists. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices.. Access Control List Codes.
From www.pynetlabs.com
What is Network Access Control List (ACL)? Labs Access Control List Codes This document describes how ip access control lists (acls) can filter network traffic. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Only two acls are permitted per network. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets. Access Control List Codes.
From www.slideserve.com
PPT Chap 5 Access Control Lists Learning Objectives PowerPoint Access Control List Codes Access control list explained with examples. It also contains brief descriptions of the. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. We have two commands to create a standard access list. Learn cisco acls configuration commands with their. This tutorial explains how. Access Control List Codes.
From tehrantrain.com
ACL (Access Control List) چیست؟ + فیلم آموزشی باشگاه شبکه و امنیت تهران Access Control List Codes This document describes how ip access control lists (acls) can filter network traffic. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Access control lists are made up of a set of rules used to configure and control access to resources such as. Access Control List Codes.
From read.cholonautas.edu.pe
What Is Access List And Its Types Printable Templates Free Access Control List Codes By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Only two acls are permitted per network. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. It also contains brief descriptions of the. This document. Access Control List Codes.
From www.sunnyvalley.io
What is an Access Control List? sunnyvalley.io Access Control List Codes Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. Only two acls are permitted per network. This document describes how ip access control lists (acls) can filter network traffic. Learn cisco acls configuration commands with their. It also contains brief descriptions of the.. Access Control List Codes.
From velog.io
Access Control Access Control List Codes By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Learn cisco acls configuration commands with their. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. Cisco. Access Control List Codes.
From viettuans.vn
Network Access Control là gì? Ứng dụng thực tiễn của Network Access Co Access Control List Codes This document describes how ip access control lists (acls) can filter network traffic. We have two commands to create a standard access list. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. Learn cisco acls configuration commands with their. By using extended access lists, you can effectively allow users access to. Access Control List Codes.
From www.slideserve.com
PPT Access Control Matrix PowerPoint Presentation, free download ID Access Control List Codes Access control list explained with examples. This tutorial explains how to configure cisco access control lists. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. This document describes how ip access control lists (acls) can filter network traffic. Learn cisco acls configuration commands. Access Control List Codes.
From www.slideserve.com
PPT Chapter IX File Systems PowerPoint Presentation, free download Access Control List Codes Only two acls are permitted per network. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. We have two commands to create a standard access. Access Control List Codes.
From networkwalks.com
ACL (Access Control List) Networkwalks Academy Access Control List Codes It also contains brief descriptions of the. Learn cisco acls configuration commands with their. This document describes how ip access control lists (acls) can filter network traffic. We have two commands to create a standard access list. Only two acls are permitted per network. Access control lists are made up of a set of rules used to configure and control. Access Control List Codes.
From www.slideserve.com
PPT Access Control Lists PowerPoint Presentation, free download ID Access Control List Codes Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. This tutorial explains how to configure cisco access control lists. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Access control list explained with examples.. Access Control List Codes.
From www.scribd.com
Online Access CodesUpdated 101510 PDF Textbook World Wide Access Control List Codes Learn cisco acls configuration commands with their. This document describes how ip access control lists (acls) can filter network traffic. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. It also contains brief descriptions of the. This tutorial explains how to configure cisco. Access Control List Codes.
From www.slideserve.com
PPT IPsec Network Layer Security PowerPoint Presentation, free Access Control List Codes Learn cisco acls configuration commands with their. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. It also contains brief descriptions of the. This tutorial explains how to configure cisco access control lists. We have two commands to create a standard access list.. Access Control List Codes.
From www.dolistore.com
Access Control List (ACL) Access Control List Codes This document describes how ip access control lists (acls) can filter network traffic. It also contains brief descriptions of the. Learn cisco acls configuration commands with their. Access control list explained with examples. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. We. Access Control List Codes.
From www.aga88.com
Sicuro noioso screpolatura access control list packet tracer Access Control List Codes By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. Learn cisco acls configuration commands with their. We have two commands to create a standard access. Access Control List Codes.
From www.slideserve.com
PPT Information Security Theory vs. Reality 0368447401, Winter Access Control List Codes This document describes how ip access control lists (acls) can filter network traffic. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. Access control list explained with examples. Only two acls are permitted per network. Access control lists are made up of a set of rules used to configure and control. Access Control List Codes.
From identitymanagementinstitute.org
Access Control Matrix and Capability List Identity Management Institute® Access Control List Codes Only two acls are permitted per network. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Access control list explained with examples. It also contains. Access Control List Codes.
From www.shutterstock.com
604 Access Control List Images, Stock Photos, 3D objects, & Vectors Access Control List Codes Learn cisco acls configuration commands with their. This tutorial explains how to configure cisco access control lists. Only two acls are permitted per network. We have two commands to create a standard access list. Access control list explained with examples. This document describes how ip access control lists (acls) can filter network traffic. Access control lists are made up of. Access Control List Codes.
From www.dreamstime.com
Access control list stock illustration. Illustration of render 93927876 Access Control List Codes We have two commands to create a standard access list. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or. Access Control List Codes.
From www.slideserve.com
PPT General OS Security Memory Protection and Access Control Access Control List Codes It also contains brief descriptions of the. Learn cisco acls configuration commands with their. This document describes how ip access control lists (acls) can filter network traffic. This tutorial explains how to configure cisco access control lists. Access control list explained with examples. Only two acls are permitted per network. Cisco acls are single or multiple permit/deny statements that filter. Access Control List Codes.
From www.ciscoforall.com
CCNA basic router commands for the 640607 exams » CiscoForAll Access Control List Codes Learn cisco acls configuration commands with their. This tutorial explains how to configure cisco access control lists. Only two acls are permitted per network. Access control list explained with examples. We have two commands to create a standard access list. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing. Access Control List Codes.
From budibase.com
RoleBased Access Control Ultimate Guide Access Control List Codes Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. This document describes how ip access control lists (acls) can filter network traffic. Only two acls. Access Control List Codes.
From www.youtube.com
What is ACL (Access Control List) YouTube Access Control List Codes By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. This tutorial explains how to configure cisco access control lists. Only two acls are permitted per network. Access control lists are made up of a set of rules used to configure and control access. Access Control List Codes.
From www.slideserve.com
PPT Access Control List PowerPoint Presentation, free download ID Access Control List Codes Learn cisco acls configuration commands with their. We have two commands to create a standard access list. Only two acls are permitted per network. This document describes how ip access control lists (acls) can filter network traffic. This tutorial explains how to configure cisco access control lists. Access control lists are made up of a set of rules used to. Access Control List Codes.
From www.wallarm.com
What is ACL? Examples and Types of Access Control List Access Control List Codes This document describes how ip access control lists (acls) can filter network traffic. Access control list explained with examples. Only two acls are permitted per network. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. This tutorial explains how to configure cisco access. Access Control List Codes.
From www.slideserve.com
PPT Access Control List PowerPoint Presentation, free download ID Access Control List Codes Learn cisco acls configuration commands with their. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. This document describes how ip access control lists (acls) can filter network traffic. We have two commands to create a standard access list. Cisco acls are single. Access Control List Codes.
From info.pivitglobal.com
A Complete Guide to Access Control Lists Types and Creation Methods Access Control List Codes We have two commands to create a standard access list. This document describes how ip access control lists (acls) can filter network traffic. Learn cisco acls configuration commands with their. It also contains brief descriptions of the. Only two acls are permitted per network. By using extended access lists, you can effectively allow users access to a physical lan and. Access Control List Codes.
From avopix.com
ACL Access Control List acronym. business Royalty Free Stock Vector Access Control List Codes Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. This tutorial explains how to configure cisco access. Access Control List Codes.
From www.pinterest.com
Access Input Mask Cheat Sheet Access database, Cheat sheets, Computer Access Control List Codes By using extended access lists, you can effectively allow users access to a physical lan and stop them from accessing specific hosts—or even specific services on. Learn cisco acls configuration commands with their. This document describes how ip access control lists (acls) can filter network traffic. We have two commands to create a standard access list. This tutorial explains how. Access Control List Codes.
From www.slideserve.com
PPT Access Control Lists PowerPoint Presentation, free download ID Access Control List Codes Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. Cisco acls are single or multiple permit/deny statements that filter inbound or outbound packets on a network interface. This document describes how ip access control lists (acls) can filter network traffic. Only two acls. Access Control List Codes.
From pediaa.com
What is the Difference Between Access Control List and Access Control Access Control List Codes This document describes how ip access control lists (acls) can filter network traffic. We have two commands to create a standard access list. It also contains brief descriptions of the. Access control list explained with examples. Only two acls are permitted per network. Learn cisco acls configuration commands with their. By using extended access lists, you can effectively allow users. Access Control List Codes.