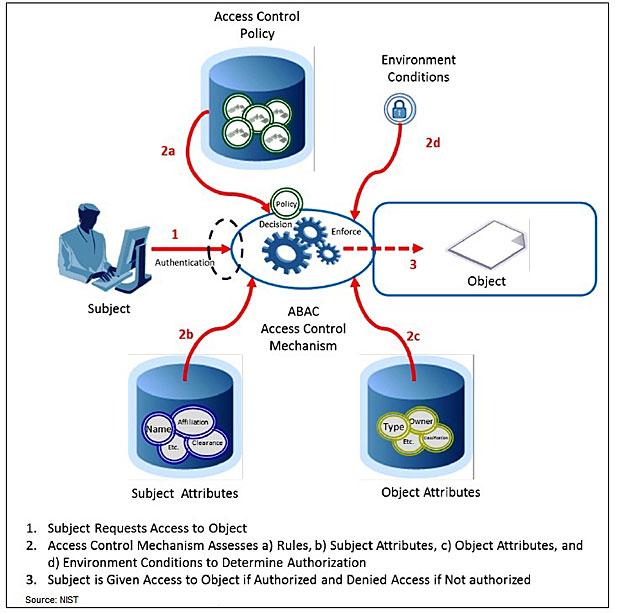
Nist Policy Based Access Control . Abac is a logical access control methodology where authorization to perform a set of. Organizations planning to implement an access control system should consider three abstractions: This document provides federal agencies with a definition of attribute based access control (abac). This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Section 2 gives overviews of the basic. Access control policies, models, and. Policy machine and next generation access control. In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. To solve the interoperability and policy enforcement problems of today’s access. Section 1 states the purpose and scope of attributes used for access control systems.
from www.govinfosecurity.com
This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Section 2 gives overviews of the basic. In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. Policy machine and next generation access control. Access control policies, models, and. This document provides federal agencies with a definition of attribute based access control (abac). Organizations planning to implement an access control system should consider three abstractions: A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. Abac is a logical access control methodology where authorization to perform a set of. To solve the interoperability and policy enforcement problems of today’s access.
NIST Guide Aims to Ease Access Control GovInfoSecurity
Nist Policy Based Access Control This document provides federal agencies with a definition of attribute based access control (abac). A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. Abac is a logical access control methodology where authorization to perform a set of. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. To solve the interoperability and policy enforcement problems of today’s access. Section 2 gives overviews of the basic. This document provides federal agencies with a definition of attribute based access control (abac). Organizations planning to implement an access control system should consider three abstractions: Policy machine and next generation access control. Section 1 states the purpose and scope of attributes used for access control systems. In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. Access control policies, models, and.
From www.resmo.com
9 Access Control Best Practices Resmo Nist Policy Based Access Control Section 2 gives overviews of the basic. Policy machine and next generation access control. This document provides federal agencies with a definition of attribute based access control (abac). In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. To solve the interoperability and policy enforcement problems of today’s. Nist Policy Based Access Control.
From old.sermitsiaq.ag
Nist 800 53 Access Control Policy Template Nist Policy Based Access Control Section 1 states the purpose and scope of attributes used for access control systems. To solve the interoperability and policy enforcement problems of today’s access. In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. A strategy for managing user access to one or more systems, where the. Nist Policy Based Access Control.
From www.nist.gov
Access Control System and Process for Managing and Enforcing an Nist Policy Based Access Control To solve the interoperability and policy enforcement problems of today’s access. A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. Section 2 gives overviews of the basic. Section 1 states the purpose and scope of attributes used for access control systems. In addition to. Nist Policy Based Access Control.
From dokumen.tips
(PDF) Chapter 1 Access Control NIST 1 Access Control Nist Policy Based Access Control This document provides federal agencies with a definition of attribute based access control (abac). Policy machine and next generation access control. Organizations planning to implement an access control system should consider three abstractions: A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. Abac is. Nist Policy Based Access Control.
From www.nextlabs.com
What is PolicyBased Access Control (PBAC)? NextLabs Nist Policy Based Access Control Section 1 states the purpose and scope of attributes used for access control systems. Access control policies, models, and. To solve the interoperability and policy enforcement problems of today’s access. Abac is a logical access control methodology where authorization to perform a set of. Organizations planning to implement an access control system should consider three abstractions: Section 2 gives overviews. Nist Policy Based Access Control.
From www.csi-tools.com
The NIST framework for SAP Access Security, with CSI tools' help. Nist Policy Based Access Control Section 2 gives overviews of the basic. Policy machine and next generation access control. Abac is a logical access control methodology where authorization to perform a set of. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. In addition to the service mesh features, the capabilities of the access control model play. Nist Policy Based Access Control.
From issecuritysolutions.com
Logical Access Administration Policies NIST AC1 Buy 100 Security Nist Policy Based Access Control To solve the interoperability and policy enforcement problems of today’s access. A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. Organizations planning to implement an access control system should consider three abstractions: Section 1 states the purpose and scope of attributes used for access. Nist Policy Based Access Control.
From vdocuments.mx
RoleBased Access Control NIST · RoleBased Access Control Overview Nist Policy Based Access Control Organizations planning to implement an access control system should consider three abstractions: In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. Section 1 states the purpose and scope of attributes used for access control systems. Access control policies, models, and. Abac is a logical access control methodology. Nist Policy Based Access Control.
From issecuritysolutions.com
Identity Access Control Policies NIST AC1 and IA1 Nist Policy Based Access Control Section 2 gives overviews of the basic. A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. Abac is a logical access control methodology where authorization to perform a set of. Section 1 states the purpose and scope of attributes used for access control systems.. Nist Policy Based Access Control.
From templates.esad.edu.br
Nist 800171 Access Control Policy Template Nist Policy Based Access Control Section 1 states the purpose and scope of attributes used for access control systems. In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. Section 2 gives overviews of the basic. Access control policies, models, and. This document provides federal agencies with a definition of attribute based access. Nist Policy Based Access Control.
From nordlayer.com
PolicyBased Access Control A Complete Guide NordLayer Learn Nist Policy Based Access Control Section 2 gives overviews of the basic. Abac is a logical access control methodology where authorization to perform a set of. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This document provides federal agencies with a definition of attribute based access control (abac). In addition to the service mesh features, the. Nist Policy Based Access Control.
From www.nist.gov
MEP Centers Aid Manufacturers on Cybersecurity NIST Nist Policy Based Access Control In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. Policy machine and next generation access control. This document provides federal agencies with a definition of attribute based access control (abac). A strategy for managing user access to one or more systems, where the business roles of users. Nist Policy Based Access Control.
From www.archtis.com
NIST SP 800162 Attribute Based Access Control (ABAC) Guide archTIS Nist Policy Based Access Control In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. Policy machine and next generation access control. A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. Section 1 states the purpose and. Nist Policy Based Access Control.
From australiancybersecuritymagazine.com.au
Attributebased Access Control NIST Draft SP 800204B is Available for Nist Policy Based Access Control Section 1 states the purpose and scope of attributes used for access control systems. Section 2 gives overviews of the basic. A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. Organizations planning to implement an access control system should consider three abstractions: To solve. Nist Policy Based Access Control.
From pdfslide.net
(PPT) NIST Standard for RoleBased Access Control Nist Policy Based Access Control In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Section 1 states the purpose and scope of attributes used for access control systems. To solve the interoperability and policy enforcement. Nist Policy Based Access Control.
From hailee-bogspotramsey.blogspot.com
Nist Risk Management Framework Nist Policy Based Access Control To solve the interoperability and policy enforcement problems of today’s access. This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control methodology where authorization to perform a set of. Access control policies, models, and. Section 1 states the purpose and scope of attributes used for access control systems. Organizations planning. Nist Policy Based Access Control.
From sprinto.com
An Ultimate Guide to NIST Access Controls Requirements Sprinto Nist Policy Based Access Control Access control policies, models, and. Section 2 gives overviews of the basic. Policy machine and next generation access control. To solve the interoperability and policy enforcement problems of today’s access. In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. A strategy for managing user access to one. Nist Policy Based Access Control.
From prntbl.concejomunicipaldechinu.gov.co
Nist Remote Access Policy Template prntbl.concejomunicipaldechinu.gov.co Nist Policy Based Access Control Section 1 states the purpose and scope of attributes used for access control systems. Section 2 gives overviews of the basic. In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. A strategy for managing user access to one or more systems, where the business roles of users. Nist Policy Based Access Control.
From blog.plainid.com
Policy Based Access Control 5 Key Features Nist Policy Based Access Control To solve the interoperability and policy enforcement problems of today’s access. Organizations planning to implement an access control system should consider three abstractions: Access control policies, models, and. Section 2 gives overviews of the basic. This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control methodology where authorization to perform. Nist Policy Based Access Control.
From www.cloudauditcontrols.com
Cloud Audit Controls Quick Flyby of Access Control Mechanisms (Models) Nist Policy Based Access Control Section 1 states the purpose and scope of attributes used for access control systems. Section 2 gives overviews of the basic. In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. A strategy for managing user access to one or more systems, where the business roles of users. Nist Policy Based Access Control.
From ipkeys.com
Access Control Policy & Procedures Template [w/ Examples] Nist Policy Based Access Control This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This document provides federal agencies with a definition of attribute based access control (abac). A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. Organizations planning to implement. Nist Policy Based Access Control.
From www.stealthlabs.com
What is NIST Compliance? Key Steps to NIST Compliant Nist Policy Based Access Control This document provides federal agencies with a definition of attribute based access control (abac). Organizations planning to implement an access control system should consider three abstractions: To solve the interoperability and policy enforcement problems of today’s access. In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. Section. Nist Policy Based Access Control.
From complianceforge.com
Policy & Standards Template NIST 80053 R5 (high) Nist Policy Based Access Control This document provides federal agencies with a definition of attribute based access control (abac). Access control policies, models, and. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Organizations planning to implement an access control system should consider three abstractions: Abac is a logical access control methodology where authorization to perform a. Nist Policy Based Access Control.
From www.govinfosecurity.com
NIST Guide Aims to Ease Access Control GovInfoSecurity Nist Policy Based Access Control Abac is a logical access control methodology where authorization to perform a set of. A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. This document provides federal agencies with a definition of attribute based access control (abac). Section 2 gives overviews of the basic.. Nist Policy Based Access Control.
From kanini.com
5 functions of NIST Cybersecurity (CSF) Framework KANINI Nist Policy Based Access Control This document provides federal agencies with a definition of attribute based access control (abac). This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Policy machine and next generation access control. Access control policies, models, and. Organizations planning to implement an access control system should consider three abstractions: Section 2 gives overviews of. Nist Policy Based Access Control.
From cashier.mijndomein.nl
Access Control Policy Template Nist Nist Policy Based Access Control Access control policies, models, and. To solve the interoperability and policy enforcement problems of today’s access. Organizations planning to implement an access control system should consider three abstractions: Policy machine and next generation access control. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Section 2 gives overviews of the basic. This. Nist Policy Based Access Control.
From www.enzoic.com
NIST Password Guidelines Best Practices Revealed Enzoic Nist Policy Based Access Control Section 2 gives overviews of the basic. To solve the interoperability and policy enforcement problems of today’s access. A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access. Policy machine and next generation access control. This document provides federal agencies with a definition of attribute. Nist Policy Based Access Control.
From www.techtarget.com
How to use the NIST framework for cloud security TechTarget Nist Policy Based Access Control Section 1 states the purpose and scope of attributes used for access control systems. This document provides federal agencies with a definition of attribute based access control (abac). This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Access control policies, models, and. A strategy for managing user access to one or more. Nist Policy Based Access Control.
From www.nccoe.nist.gov
Identity and Access Management NIST SP 18002 Nist Policy Based Access Control To solve the interoperability and policy enforcement problems of today’s access. Access control policies, models, and. Organizations planning to implement an access control system should consider three abstractions: This document provides federal agencies with a definition of attribute based access control (abac). This publication provides a catalog of security and privacy controls for information systems and organizations to protect. In. Nist Policy Based Access Control.
From www.comparitech.com
NIST Cybersecurity Framework Guide 2024 Core, Implementation & Profile Nist Policy Based Access Control This document provides federal agencies with a definition of attribute based access control (abac). Section 1 states the purpose and scope of attributes used for access control systems. Section 2 gives overviews of the basic. To solve the interoperability and policy enforcement problems of today’s access. Organizations planning to implement an access control system should consider three abstractions: In addition. Nist Policy Based Access Control.
From www.youtube.com
NIST SP 80053, Revision 5 Security Controls for Information Systems Nist Policy Based Access Control This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Organizations planning to implement an access control system should consider three abstractions: Abac is a logical access control methodology where authorization to perform a set of. Section 2 gives overviews of the basic. Section 1 states the purpose and scope of attributes used. Nist Policy Based Access Control.
From 3columns.io
NIST Framework Guide for SaaS Security Compliance 3Columns Nist Policy Based Access Control Section 2 gives overviews of the basic. Section 1 states the purpose and scope of attributes used for access control systems. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to. Nist Policy Based Access Control.
From www.slideserve.com
PPT Access Control PowerPoint Presentation, free download ID829739 Nist Policy Based Access Control Organizations planning to implement an access control system should consider three abstractions: In addition to the service mesh features, the capabilities of the access control model play an important role in the authentication and. Section 2 gives overviews of the basic. This document provides federal agencies with a definition of attribute based access control (abac). Access control policies, models, and.. Nist Policy Based Access Control.
From www.techtarget.com
What is NIST? Everything You Should Know About NIST Compliance Nist Policy Based Access Control This document provides federal agencies with a definition of attribute based access control (abac). Organizations planning to implement an access control system should consider three abstractions: Access control policies, models, and. Abac is a logical access control methodology where authorization to perform a set of. To solve the interoperability and policy enforcement problems of today’s access. Section 1 states the. Nist Policy Based Access Control.
From dokumen.tips
(PDF) Guide to Attribute Based Access Control (ABAC) Definition and Nist Policy Based Access Control Section 2 gives overviews of the basic. Access control policies, models, and. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This document provides federal agencies with a definition of attribute based access control (abac). To solve the interoperability and policy enforcement problems of today’s access. In addition to the service mesh. Nist Policy Based Access Control.