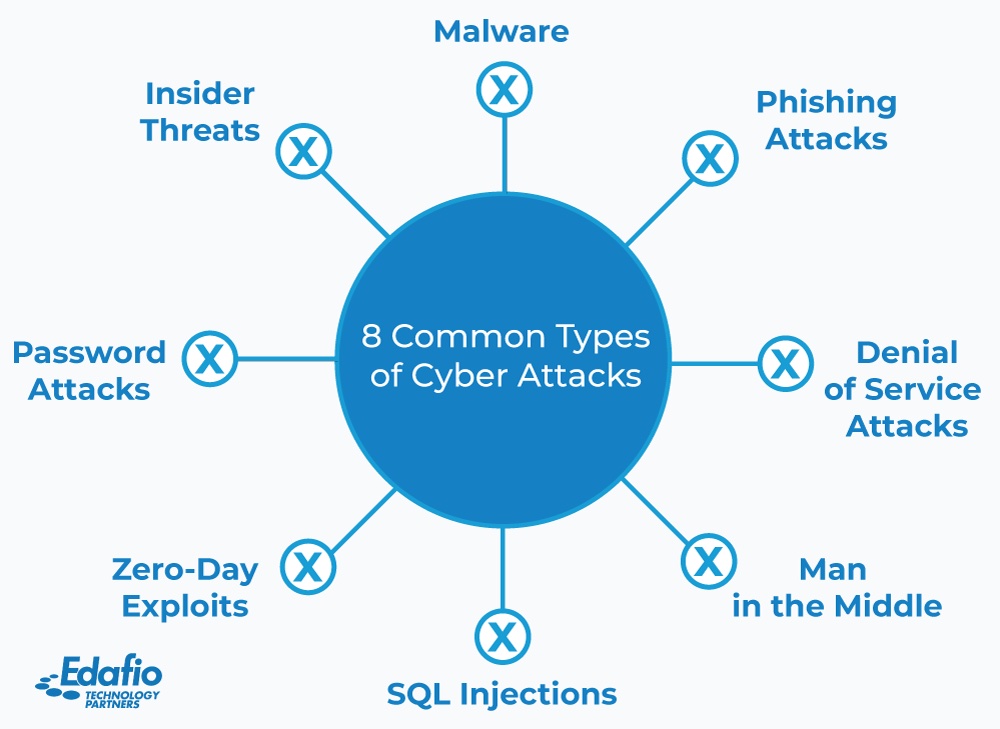
Top Cyber Security Attack Vectors . A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. 23 common attack vector examples. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack.
from www.vrogue.co
23 common attack vector examples. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network.
The 10 Most Common Types Of Cyberattacks The Isg vrogue.co
Top Cyber Security Attack Vectors Today's most common attack vectors to disrupt a system’s availability or gain initial access to. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. 23 common attack vector examples. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target.
From cyvatar.ai
What is a cyberattack vector? Avoid these 10 common attack vectors Top Cyber Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. In this guide, we’ll explore what attack vectors are, their impact on system security, and the. Top Cyber Security Attack Vectors.
From detectify.com
Attack Vector Ultimate Guide Detectify Top Cyber Security Attack Vectors A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Today's most common. Top Cyber Security Attack Vectors.
From www.intertek.com
Connected Vehicle Cybersecurity Threats Part 2 Top Cyber Security Attack Vectors In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this guide,. Top Cyber Security Attack Vectors.
From www.sprintzeal.com
Top 15 Cybersecurity Threats in 2024 Sprintzeal Top Cyber Security Attack Vectors A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. An attack vector is the method or combination. Top Cyber Security Attack Vectors.
From www.akamai.com
What Is Cybersecurity or Cyber Security? Akamai Top Cyber Security Attack Vectors 23 common attack vector examples. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. A. Top Cyber Security Attack Vectors.
From www.vecteezy.com
Cyber Security Illustration 1397516 Vector Art at Vecteezy Top Cyber Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. 23 common attack vector examples. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. In this. Top Cyber Security Attack Vectors.
From clearvpn.com
Top 10 Cybersecurity Threats For 2023 ClearVPN Top Cyber Security Attack Vectors 23 common attack vector examples. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt. Top Cyber Security Attack Vectors.
From www.researchgate.net
The overview of some common types of cyber attacks. Download Top Cyber Security Attack Vectors In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. An attack vector is the method or combination. Top Cyber Security Attack Vectors.
From www.wallarm.com
What is an Attack Vector? Examples, Definition, Meaning ⚠️ Top Cyber Security Attack Vectors 23 common attack vector examples. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to. Top Cyber Security Attack Vectors.
From www.gov.uk
Common Cyber Attacks Summary GOV.UK Top Cyber Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. 23 common attack vector examples. In this. Top Cyber Security Attack Vectors.
From www.shutterstock.com
Vector Banner General Cyber Security Attacks Stock Vector (Royalty Free Top Cyber Security Attack Vectors In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their. Top Cyber Security Attack Vectors.
From www.freepik.com
Free Vector Protect against cyber attacks infographic Top Cyber Security Attack Vectors A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. 23 common attack vector examples. An attack vector. Top Cyber Security Attack Vectors.
From www.vectorstock.com
Cyber attack icons set flat style Royalty Free Vector Image Top Cyber Security Attack Vectors In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. A threat. Top Cyber Security Attack Vectors.
From www.freepik.com
Cyber attack Vectors & Illustrations for Free Download Freepik Top Cyber Security Attack Vectors A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. 23 common attack vector examples. An attack vector is the method or combination of methods that cybercriminals use. Top Cyber Security Attack Vectors.
From webz.io
Discover The Top 10 Cybersecurity Attack Vectors z.io Top Cyber Security Attack Vectors 23 common attack vector examples. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this. Top Cyber Security Attack Vectors.
From unifiedguru.com
7 Cyber Attack Vectors & How to Protect Them Unified Networking Top Cyber Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. In. Top Cyber Security Attack Vectors.
From www.fotolia.com
"Cyber attack and protection color flat icons set. Vector illustration Top Cyber Security Attack Vectors In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their. Top Cyber Security Attack Vectors.
From www.youtube.com
15Get To Know Attack Vectors And Types YouTube Top Cyber Security Attack Vectors 23 common attack vector examples. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use. Top Cyber Security Attack Vectors.
From www.trendmicro.com
7 Cyber Attack Vectors & How to Protect Them Trend Micro (US) Top Cyber Security Attack Vectors A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. 23 common attack vector examples. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in. Top Cyber Security Attack Vectors.
From www.balbix.com
8 Common Types of Cyber Attack Vectors and How to Avoid Them Balbix Top Cyber Security Attack Vectors In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. 23 common attack vector examples. In this guide, we’ll explore what attack vectors are, their impact on system. Top Cyber Security Attack Vectors.
From www.trendmicro.com
7 Cyber Attack Vectors & How to Protect Them Trend Micro (US) Top Cyber Security Attack Vectors Today's most common attack vectors to disrupt a system’s availability or gain initial access to. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. 23 common attack vector examples. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. A. Top Cyber Security Attack Vectors.
From www.cyberlearning.ro
Analyzing CyberThreats and Attack Vectors CyberLearning Academy Top Cyber Security Attack Vectors An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this guide, we’ll explore what attack. Top Cyber Security Attack Vectors.
From www.freepik.com
Free Vector Protect against cyber attacks infographic Top Cyber Security Attack Vectors In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their. Top Cyber Security Attack Vectors.
From blog.invgate.com
14 Most Common Types of Cyber Attacks (and How to Prevent Them) Top Cyber Security Attack Vectors 23 common attack vector examples. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this guide, we’ll explore what attack vectors are, their impact on system. Top Cyber Security Attack Vectors.
From www.freepik.com
Protect against cyber attacks design Free Vector Top Cyber Security Attack Vectors Today's most common attack vectors to disrupt a system’s availability or gain initial access to. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. 23 common attack vector examples. A. Top Cyber Security Attack Vectors.
From unifiedguru.com
7 Cyber Attack Vectors & How to Protect Them Unified Networking Top Cyber Security Attack Vectors A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their. Top Cyber Security Attack Vectors.
From cyvatar.ai
What is a cyberattack vector? Avoid these 10 common attack vectors Top Cyber Security Attack Vectors A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a. Top Cyber Security Attack Vectors.
From www.vrogue.co
The 10 Most Common Types Of Cyberattacks The Isg vrogue.co Top Cyber Security Attack Vectors 23 common attack vector examples. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences. Top Cyber Security Attack Vectors.
From expel.com
Top Attack Vectors January 2022 Expel Top Cyber Security Attack Vectors Today's most common attack vectors to disrupt a system’s availability or gain initial access to. 23 common attack vector examples. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. In this. Top Cyber Security Attack Vectors.
From www.insightsonindia.com
Meaning and Types of Cybersecurity Threats INSIGHTS IAS Simplifying Top Cyber Security Attack Vectors Today's most common attack vectors to disrupt a system’s availability or gain initial access to. 23 common attack vector examples. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this. Top Cyber Security Attack Vectors.
From insights.sca.health
Understanding CyberAttack Vectors in Healthcare SCA Health Insights Top Cyber Security Attack Vectors A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. Today's most common attack vectors to disrupt a system’s availability or gain initial access to. An attack vector is the method or combination. Top Cyber Security Attack Vectors.
From www.securitymadesimple.org
Top 7 Popular Cyber Threat Models for identifying threat actors Top Cyber Security Attack Vectors In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. 23 common attack. Top Cyber Security Attack Vectors.
From securityboulevard.com
The InfoSec Guide to Attack Vectors Security Boulevard Top Cyber Security Attack Vectors In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their target. 23 common attack vector examples. A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. An attack vector is the method or combination of methods that cybercriminals use. Top Cyber Security Attack Vectors.
From support.aiesec.org
Cyber Security Threats and Attacks AIESEC Help Center Top Cyber Security Attack Vectors A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. An attack vector is the method or combination of methods that cybercriminals use to breach or infiltrate a victim’s network. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate. Top Cyber Security Attack Vectors.
From www.vecteezy.com
Cyber Attack Illustration concept. Flat illustration isolated on white Top Cyber Security Attack Vectors A threat vector, often used interchangeably with an attack vector, refers to the specific methods or pathways that. In this guide, we’ll explore what attack vectors are, their impact on system security, and the differences between attack. In this blog post, we’ll take a look at 12 common attack vectors that threat actors use in an attempt to infiltrate their. Top Cyber Security Attack Vectors.