What Is Cgi Bin Jarrewrite Sh . Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. Let’s examine how these vulnerabilities can be exploited.
from filmlifestyle.com
Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited.
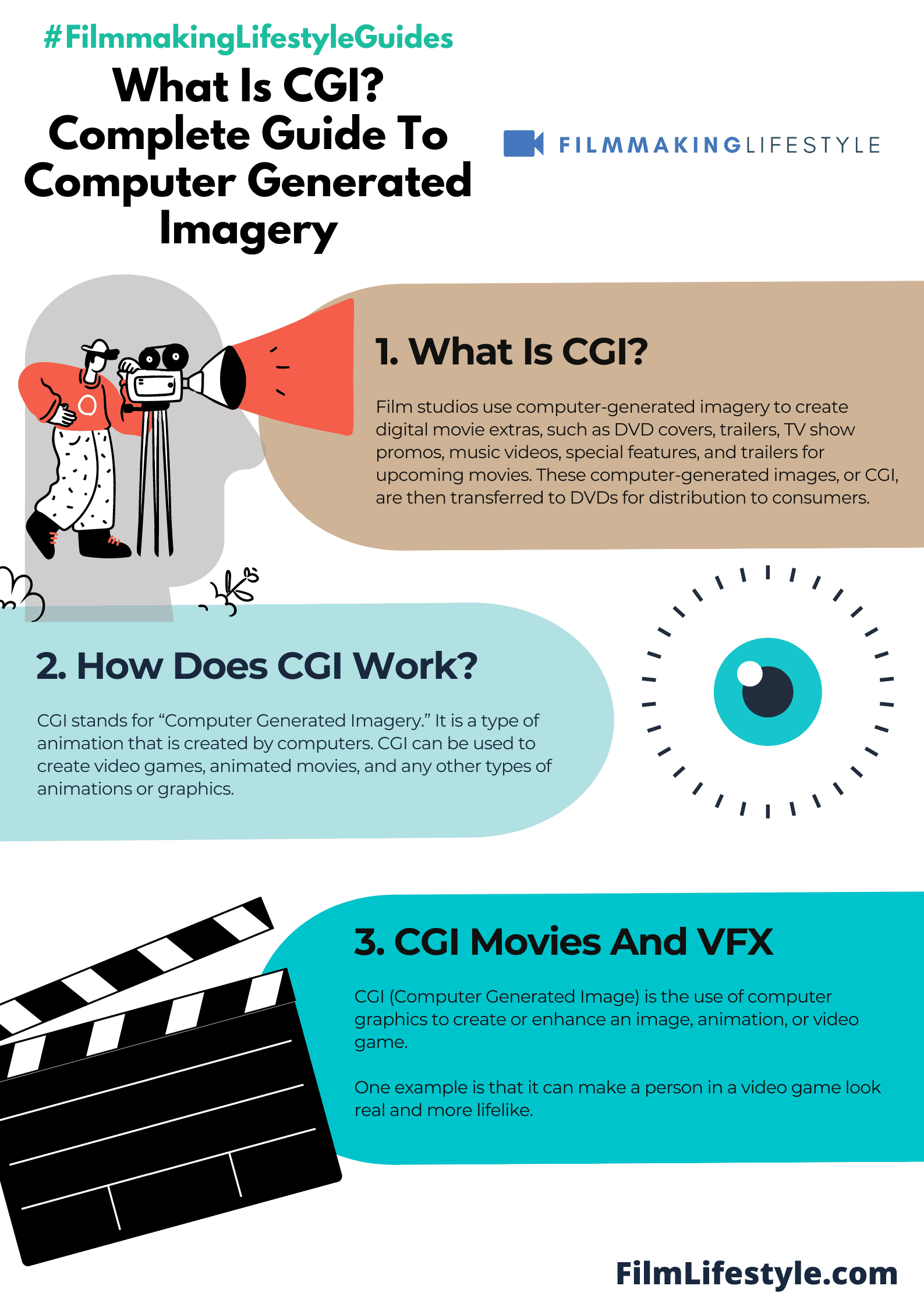
What Is CGI? Complete Guide To Computer Generated Imagery
What Is Cgi Bin Jarrewrite Sh Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry.
From www.slideshare.net
http//authorities.loc.gov/cgibin/Pwebrecon.cgi? AuthRecID=969701&v1… What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From huggingface.co
cgibin (cgibin) What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From buaq.net
【漏洞预警】SonicWall SSLVPN What Is Cgi Bin Jarrewrite Sh Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From www.vrogue.co
What Is Cgi Bin And What Does It Do Liquid vrogue.co What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. What Is Cgi Bin Jarrewrite Sh.
From 3dheven.com
What is CGI Animation and How Does it Work? 3DHEVEN What Is Cgi Bin Jarrewrite Sh Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From filmlifestyle.com
What Is CGI? Complete Guide To Computer Generated Imagery What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From 3dheven.com
What is CGI Animation and How Does it Work? 3DHEVEN What Is Cgi Bin Jarrewrite Sh Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From www.pinterest.com
cgibin courses displaycourselesson.cgi?clid=1421&aff=0 What Is Cgi Bin Jarrewrite Sh Below are a few examples of common requests captured in our telemetry. Let’s examine how these vulnerabilities can be exploited. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From www.linkedin.com
“Unlocking the Magic Exploring the Power and Purpose of CGI Bin in What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From www.makeuseof.com
The Linux Bourne Shell Explained What Is Cgi Bin Jarrewrite Sh Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From nerdytutorials.com
How to Resolve the '/bin/sh 1 source not found' Issue What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From www.vrogue.co
What Is Cgi Bin And What Does It Do Liquid vrogue.co What Is Cgi Bin Jarrewrite Sh Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From www.epidemicsound.com
What is CGI and How Has It Changed Movies, Animation & Content? What Is Cgi Bin Jarrewrite Sh Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From www.vrogue.co
What Is Cgi Bin And What Does It Do Liquid vrogue.co What Is Cgi Bin Jarrewrite Sh Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From www.vrogue.co
What Is Cgi Explanation About The Cgi Bin File Slviki vrogue.co What Is Cgi Bin Jarrewrite Sh Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From www.slideserve.com
PPT Perl, servers (apache) and web applications (cgibin What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From slviki.org
What is CGI? explanation about the CGIbin file What Is Cgi Bin Jarrewrite Sh Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From github.com
CGIBIN/index.cgi at master · Fishezzz/CGIBIN · GitHub What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From falloffthewall.com
What is CGI and how is it used in TV Ads? What Is Cgi Bin Jarrewrite Sh Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. What Is Cgi Bin Jarrewrite Sh.
From www.vrogue.co
What Is Cgi Bin And What Does It Do Liquid vrogue.co What Is Cgi Bin Jarrewrite Sh Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From internetoflearning.org
What is CGI Animation? Everything You Know to Know KIGI What Is Cgi Bin Jarrewrite Sh Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. What Is Cgi Bin Jarrewrite Sh.
From fdocuments.ec
Configurar CGIBIN Con Xampp [PDF Document] What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. What Is Cgi Bin Jarrewrite Sh.
From www.youtube.com
"Run Perl CGI Script on server with cPanel" [cgibin] YouTube What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. What Is Cgi Bin Jarrewrite Sh.
From faroutmagazine.co.uk
A timeline of the history of CGI in the movies What Is Cgi Bin Jarrewrite Sh Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From slviki.org
What is CGI? explanation about the CGIbin file What Is Cgi Bin Jarrewrite Sh Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From www.studyglance.in
CGI vs Servlet SERVLET Tutorial Study Glance What Is Cgi Bin Jarrewrite Sh Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. What Is Cgi Bin Jarrewrite Sh.
From www.researchgate.net
Logs from the start of the system, available via the HTTP server What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From illustrationagent.com
What is CGI and how to use it in your marketing campaigns What Is Cgi Bin Jarrewrite Sh Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. What Is Cgi Bin Jarrewrite Sh.
From www.liquidweb.com
What is CGIBin and What Does it Do? Liquid What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. What Is Cgi Bin Jarrewrite Sh.
From www.linkedin.com
Dynamic Brilliance Navigating CGIBin and Unleashing Interactivity What Is Cgi Bin Jarrewrite Sh Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From falloffthewall.com
What is CGI and how is it used in TV Ads? What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From knowledge.1-grid.com
cPanel Running Python Scrips 1grid Knowledge Base What Is Cgi Bin Jarrewrite Sh Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Let’s examine how these vulnerabilities can be exploited. What Is Cgi Bin Jarrewrite Sh.
From blog.csdn.net
SonicWall SSLV**远程命令执行漏洞CSDN博客 What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From www.vrogue.co
What Is Cgi Explanation About The Cgi Bin File Slviki vrogue.co What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Below are a few examples of common requests captured in our telemetry. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. What Is Cgi Bin Jarrewrite Sh.
From www.studyglance.in
CGI vs Servlet SERVLET Tutorial Study Glance What Is Cgi Bin Jarrewrite Sh Let’s examine how these vulnerabilities can be exploited. Most of the exploitations are targeted toward two specific paths:/etc/passwd and /bin/sh. Below are a few examples of common requests captured in our telemetry. What Is Cgi Bin Jarrewrite Sh.