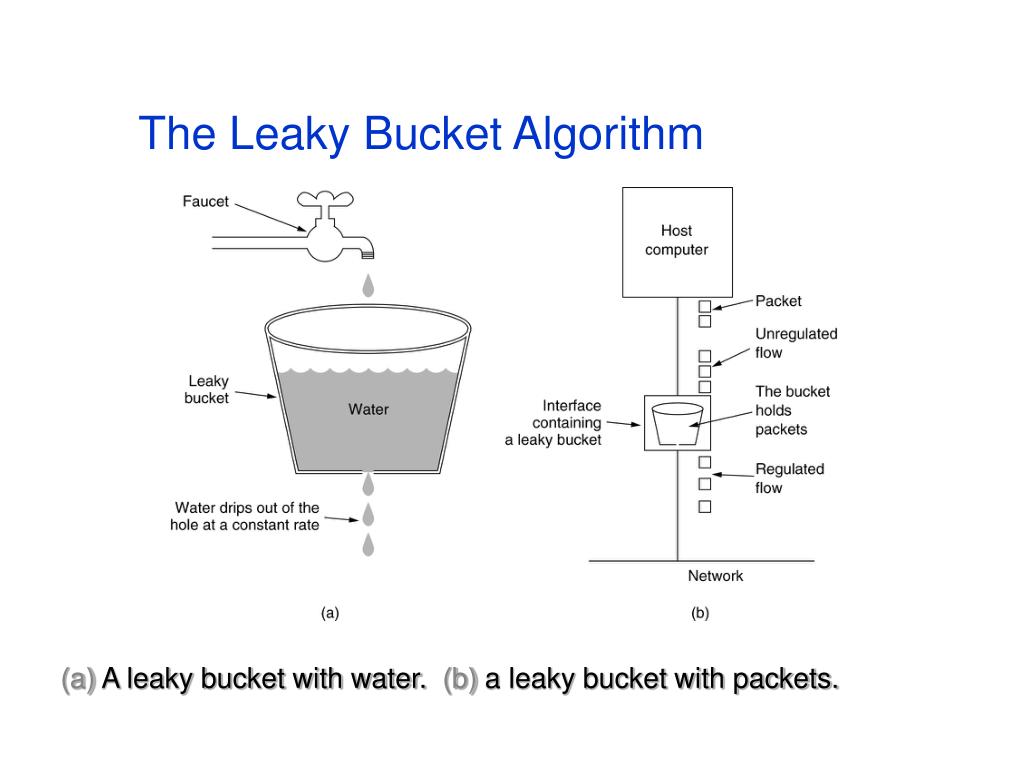
Leaky Bucket Java Implementation . Leaky bucket is a more robust algorithm compared to a token bucket. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. Discover the ins and outs of the leaky bucket algorithm for rate limiting. We will not go into the internal details of these algorithms as. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. However, it has a downside as well. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Packets that arrive first in. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. One such is leaky bucket. Learn how to implement it using java and choose the best strategy for your api traffic control.
from www.slideserve.com
However, it has a downside as well. One such is leaky bucket. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. We will not go into the internal details of these algorithms as. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Discover the ins and outs of the leaky bucket algorithm for rate limiting. Learn how to implement it using java and choose the best strategy for your api traffic control. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. Leaky bucket is a more robust algorithm compared to a token bucket. Packets that arrive first in.
PPT Flow Control PowerPoint Presentation, free download ID418287
Leaky Bucket Java Implementation The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. Packets that arrive first in. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. We will not go into the internal details of these algorithms as. Leaky bucket is a more robust algorithm compared to a token bucket. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Discover the ins and outs of the leaky bucket algorithm for rate limiting. Learn how to implement it using java and choose the best strategy for your api traffic control. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. One such is leaky bucket. However, it has a downside as well.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Java Implementation One such is leaky bucket. Packets that arrive first in. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. We will not go into the internal details of these algorithms as. Leaky bucket is a more robust. Leaky Bucket Java Implementation.
From www.slideserve.com
PPT Quality of Service Support PowerPoint Presentation, free download ID6577623 Leaky Bucket Java Implementation However, it has a downside as well. We will not go into the internal details of these algorithms as. Learn how to implement it using java and choose the best strategy for your api traffic control. Discover the ins and outs of the leaky bucket algorithm for rate limiting. The leaky bucket algorithm can be implemented using a fifo (first. Leaky Bucket Java Implementation.
From www.youtube.com
12. Leaky Bucket Algorithm Program VTU 5th Sem Computer Network Lab 15CSL57 YouTube Leaky Bucket Java Implementation The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. However, it has a downside as well. Packets that arrive first in. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. Leaky bucket is a more robust algorithm compared to. Leaky Bucket Java Implementation.
From medium.com
Rate Limiting Leaky Bucket Java Spring Boot AOP Implementation by sai karthik Medium Leaky Bucket Java Implementation However, it has a downside as well. Packets that arrive first in. Learn how to implement it using java and choose the best strategy for your api traffic control. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. We will not go into the internal details of these algorithms as. One such. Leaky Bucket Java Implementation.
From www.fatalerrors.org
Go Language Implementation of Current Limiting in Leakage Bucket and Token Bucket Leaky Bucket Java Implementation Discover the ins and outs of the leaky bucket algorithm for rate limiting. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. However, it has a downside as well. Leaky bucket is a more robust algorithm compared to a token bucket. We will not go into the internal details of these algorithms. Leaky Bucket Java Implementation.
From hechao.li
Rate Limiting Part 1 Leaky Bucket Java Implementation However, it has a downside as well. Learn how to implement it using java and choose the best strategy for your api traffic control. Discover the ins and outs of the leaky bucket algorithm for rate limiting. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The advantage of ratelimiting is having. Leaky Bucket Java Implementation.
From www.youtube.com
How Can I Implement Congestion Control with Leaky Bucket Algorithm in C/C++? YouTube Leaky Bucket Java Implementation The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Discover the ins and outs of the leaky bucket algorithm for rate limiting. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm can be implemented using a fifo (first in first. Leaky Bucket Java Implementation.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Algorithms API7.ai Leaky Bucket Java Implementation Learn how to implement it using java and choose the best strategy for your api traffic control. Packets that arrive first in. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The advantage of ratelimiting is having. Leaky Bucket Java Implementation.
From medium.com
Implementing Rate Limiting in Java from Scratch — Leaky Bucket and Token Bucket implementation Leaky Bucket Java Implementation The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. Learn how to implement it using java and choose the best strategy for your api traffic control. Packets that. Leaky Bucket Java Implementation.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5856654 Leaky Bucket Java Implementation However, it has a downside as well. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. Packets that arrive first in. We will not go into the internal details of these algorithms as. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Learn how to implement. Leaky Bucket Java Implementation.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Java Implementation The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. We will not go into the internal details of these algorithms as. Leaky bucket is a more robust algorithm compared to a token bucket. Discover the ins and outs of the leaky bucket algorithm for rate limiting. One such is leaky bucket. Learn how to. Leaky Bucket Java Implementation.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID569119 Leaky Bucket Java Implementation Discover the ins and outs of the leaky bucket algorithm for rate limiting. Learn how to implement it using java and choose the best strategy for your api traffic control. Leaky bucket is a more robust algorithm compared to a token bucket. Packets that arrive first in. The leaky bucket algorithm is a simple yet effective way to control data. Leaky Bucket Java Implementation.
From www.scribd.com
Write A Java Program For Congestion Control Using Leaky Bucket Algorithm PDF Computer Leaky Bucket Java Implementation The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. Leaky bucket is a more robust algorithm compared to a token bucket. One such is leaky bucket. We will. Leaky Bucket Java Implementation.
From crunchify.com
How to implement Bucket Sort Algorithm in Java? Detailed Explanation • Crunchify Leaky Bucket Java Implementation We will not go into the internal details of these algorithms as. Discover the ins and outs of the leaky bucket algorithm for rate limiting. However, it has a downside as well. Packets that arrive first in. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Leaky bucket is a more robust. Leaky Bucket Java Implementation.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Java Implementation Learn how to implement it using java and choose the best strategy for your api traffic control. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. One such is leaky bucket. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. We will not go. Leaky Bucket Java Implementation.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Java Implementation Discover the ins and outs of the leaky bucket algorithm for rate limiting. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Leaky bucket is a more robust algorithm compared to a token bucket. The advantage of. Leaky Bucket Java Implementation.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Java Implementation We will not go into the internal details of these algorithms as. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. However, it has a downside as well. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. Discover the. Leaky Bucket Java Implementation.
From blog.cloudflare.com
How we built rate limiting capable of scaling to millions of domains Leaky Bucket Java Implementation Packets that arrive first in. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. One such is leaky bucket. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Discover the ins and outs of the leaky bucket. Leaky Bucket Java Implementation.
From www.chegg.com
This is an implementation of a leaky bucket algorithm Leaky Bucket Java Implementation The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Discover the ins and outs of the leaky bucket algorithm for rate limiting. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. However, it has a downside as well. The leaky bucket algorithm can be. Leaky Bucket Java Implementation.
From medium.com
Leaky Bucket Algorithm Managing Data Flow in Networks 🌐 by Yeshwanth N Medium Leaky Bucket Java Implementation We will not go into the internal details of these algorithms as. Packets that arrive first in. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. One such is leaky bucket. Leaky bucket is a more robust algorithm compared to a token bucket. The leaky. Leaky Bucket Java Implementation.
From designcodesolve.com
Rate Limiting Token and Leaky Bucket Implementation and Explanation Leaky Bucket Java Implementation We will not go into the internal details of these algorithms as. Packets that arrive first in. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. Discover the ins and outs of the leaky bucket algorithm for rate limiting. However, it has a downside as well. Leaky bucket is a more robust algorithm compared. Leaky Bucket Java Implementation.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Java Implementation Packets that arrive first in. However, it has a downside as well. Leaky bucket is a more robust algorithm compared to a token bucket. Learn how to implement it using java and choose the best strategy for your api traffic control. Discover the ins and outs of the leaky bucket algorithm for rate limiting. We will not go into the. Leaky Bucket Java Implementation.
From www.slideshare.net
Chap24 Leaky Bucket Java Implementation We will not go into the internal details of these algorithms as. However, it has a downside as well. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. The leaky. Leaky Bucket Java Implementation.
From dailyjavaconcept.com
Implementation of Bucket Sort in Java Daily Java Concept Leaky Bucket Java Implementation Leaky bucket is a more robust algorithm compared to a token bucket. Packets that arrive first in. One such is leaky bucket. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. However, it has a downside as. Leaky Bucket Java Implementation.
From github.com
GitHub ShreyaRao09/LeakyBucketAlgorithmImplementation A Computer Graphics based project Leaky Bucket Java Implementation Learn how to implement it using java and choose the best strategy for your api traffic control. However, it has a downside as well. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky. Leaky Bucket Java Implementation.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Java Implementation The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. One such is leaky bucket. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Packets that arrive first in. We will not go into the internal details of. Leaky Bucket Java Implementation.
From www.researchgate.net
Intelligent leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Java Implementation Discover the ins and outs of the leaky bucket algorithm for rate limiting. Packets that arrive first in. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. Leaky bucket is a more robust algorithm compared to a token bucket. The leaky bucket algorithm can be. Leaky Bucket Java Implementation.
From awstip.com
AWS CDK & Leaky Bucket Manage Traffic Congestion AWS Tip Leaky Bucket Java Implementation The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. One such is leaky bucket. Learn how to implement it using java and choose the best strategy for your api traffic control. We will not go into the. Leaky Bucket Java Implementation.
From www.studocu.com
leaky bucket implementation include void main() { int outgoing, Studocu Leaky Bucket Java Implementation We will not go into the internal details of these algorithms as. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. However, it has a downside as well.. Leaky Bucket Java Implementation.
From medium.com
Implementing Rate Limiting in Java from Scratch — Leaky Bucket and Token Bucket implementation Leaky Bucket Java Implementation Discover the ins and outs of the leaky bucket algorithm for rate limiting. Packets that arrive first in. We will not go into the internal details of these algorithms as. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Learn how to implement it using java and choose the best strategy for. Leaky Bucket Java Implementation.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and closed loop) YouTube Leaky Bucket Java Implementation Packets that arrive first in. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Leaky bucket is a more robust algorithm compared to a token bucket. However, it has a downside as well. The leaky bucket algorithm can be implemented using a fifo (first in first out) queue. Discover the ins and. Leaky Bucket Java Implementation.
From www.slideserve.com
PPT Flow Control PowerPoint Presentation, free download ID418287 Leaky Bucket Java Implementation The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The advantage of ratelimiting is having control over the api, avoiding a denial of service attack by any intruder, and stopping your servers from. We will not go into the internal details of these algorithms as. Packets that arrive first in. Learn how. Leaky Bucket Java Implementation.
From www.slideserve.com
PPT Principles of Congestion Control PowerPoint Presentation, free download ID8677065 Leaky Bucket Java Implementation Learn how to implement it using java and choose the best strategy for your api traffic control. We will not go into the internal details of these algorithms as. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. The leaky bucket algorithm is a simple yet effective way to control data flow. Leaky Bucket Java Implementation.
From www.youtube.com
System Design Rate Limiter Leaky Bucket Implementation System Design Interview YouTube Leaky Bucket Java Implementation Leaky bucket is a more robust algorithm compared to a token bucket. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Learn how to implement it using java and choose the best strategy for your api traffic control. Packets that arrive first in. The leaky bucket algorithm is a simple yet effective. Leaky Bucket Java Implementation.
From www.geeksforgeeks.org
How to Design a Rate Limiter API Learn System Design Leaky Bucket Java Implementation Learn how to implement it using java and choose the best strategy for your api traffic control. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Packets that arrive first in. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. One such is leaky. Leaky Bucket Java Implementation.