Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws . A main route table is created by default. Controlling network access to your instances, for. clients must support the following: which of the following examples supports the cloud design principle design for failure and nothing will fail? which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. what happens when you use amazon virtual private cloud to create a new vpc. We require tls 1.2 and recommend tls 1.3.
from jayendrapatil.com
what happens when you use amazon virtual private cloud to create a new vpc. which of the following examples supports the cloud design principle design for failure and nothing will fail? Controlling network access to your instances, for. We require tls 1.2 and recommend tls 1.3. which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. clients must support the following: A main route table is created by default.
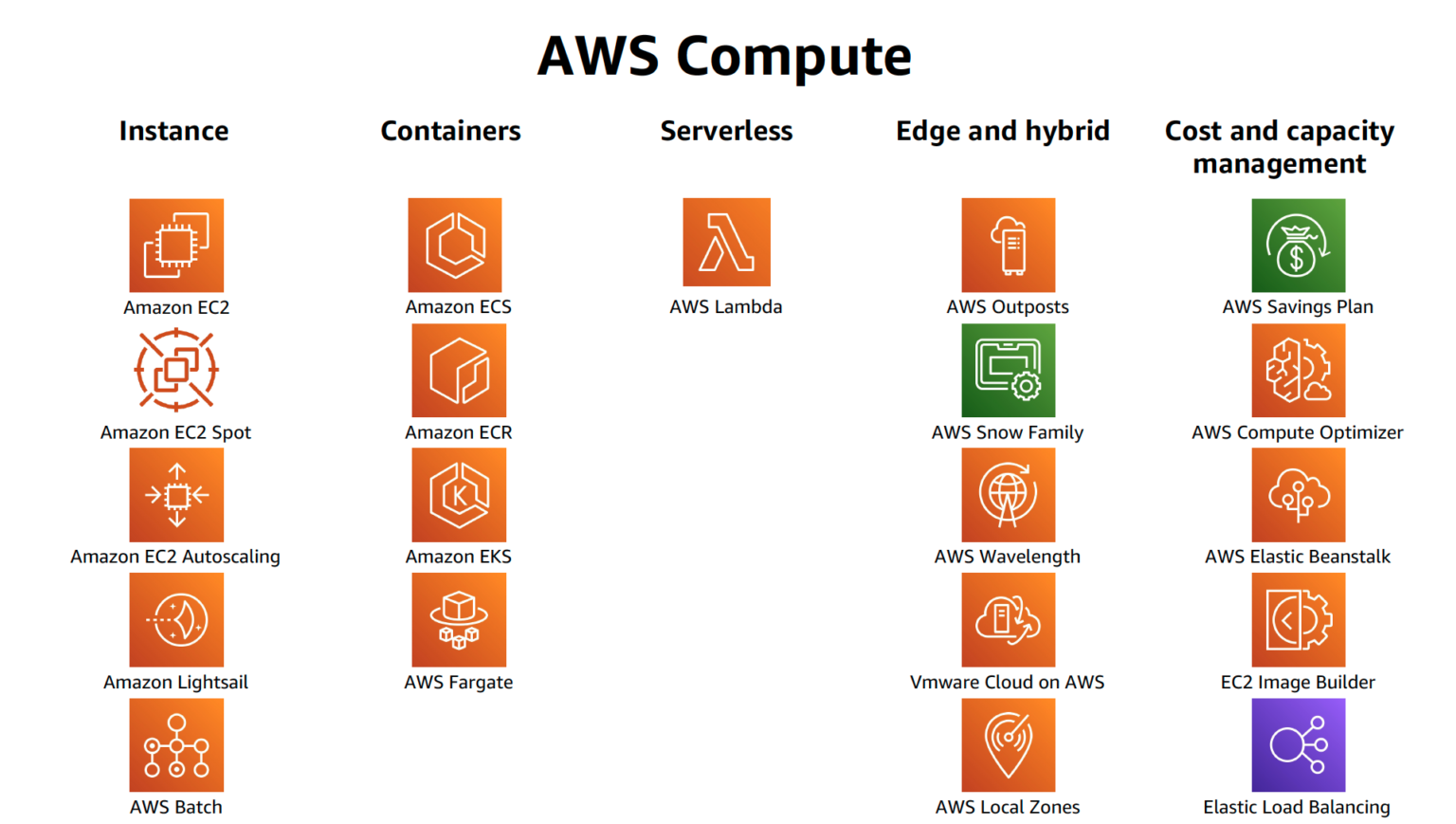
AWS Compute Services Cheat Sheet
Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws clients must support the following: what happens when you use amazon virtual private cloud to create a new vpc. A main route table is created by default. which of the following examples supports the cloud design principle design for failure and nothing will fail? which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. We require tls 1.2 and recommend tls 1.3. clients must support the following: Controlling network access to your instances, for.
From aws.amazon.com
Enable transparent connectivity to Oracle Data Guard environments using Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of the following examples supports the cloud design principle design for failure and nothing will fail? clients must support the following: Controlling network access to your instances, for. We require tls 1.2 and recommend tls 1.3. A main route table is created by default. what happens when you use amazon virtual private cloud to create a. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.bmc.com
Amazon’s Elastic File System (EFS) Explained BMC Software Blogs Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws We require tls 1.2 and recommend tls 1.3. which of the following examples supports the cloud design principle design for failure and nothing will fail? A main route table is created by default. Controlling network access to your instances, for. clients must support the following: what happens when you use amazon virtual private cloud to create a. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.whizlabs.com
Amazon Elastic Compute Cloud Guide Whizlabs Blog Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of the following examples supports the cloud design principle design for failure and nothing will fail? what happens when you use amazon virtual private cloud to create a new vpc. Controlling network access to your instances, for. We require tls 1.2 and recommend tls 1.3. clients must support the following: A main route table is created. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From info-savvy.com
Introduction of Amazon Elastic Compute Cloud (EC2) Infosavvy Security Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws We require tls 1.2 and recommend tls 1.3. A main route table is created by default. clients must support the following: what happens when you use amazon virtual private cloud to create a new vpc. which of the following examples supports the cloud design principle design for failure and nothing will fail? which of thee following. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.dustinward.cloud
Amazon Elastic Compute Cloud Guide Dustin Ward Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws what happens when you use amazon virtual private cloud to create a new vpc. clients must support the following: which of the following examples supports the cloud design principle design for failure and nothing will fail? We require tls 1.2 and recommend tls 1.3. Controlling network access to your instances, for. which of thee following can. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From info-savvy.com
Introduction of Amazon Elastic Compute Cloud (EC2) Infosavvy Security Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. Controlling network access to your instances, for. A main route table is created by default. We require tls 1.2 and recommend tls 1.3. what happens when you use amazon virtual private cloud to create a new vpc. clients. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.geeksforgeeks.org
What is Elastic Compute Cloud (EC2)? Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of the following examples supports the cloud design principle design for failure and nothing will fail? which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. Controlling network access to your instances, for. A main route table is created by default. what happens when you use amazon. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From morioh.com
Exploring Amazon EC2 (Elastic Compute Cloud) in AWS Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws clients must support the following: which of the following examples supports the cloud design principle design for failure and nothing will fail? Controlling network access to your instances, for. We require tls 1.2 and recommend tls 1.3. which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. . Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.smartdraw.com
AWS Diagram Learn What is a AWS Architecture Diagram and More Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws what happens when you use amazon virtual private cloud to create a new vpc. which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. We require tls 1.2 and recommend tls 1.3. which of the following examples supports the cloud design principle design for failure and nothing will. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From docs.aws.amazon.com
Amazon EFS How it works Amazon Elastic File System Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws what happens when you use amazon virtual private cloud to create a new vpc. A main route table is created by default. clients must support the following: which of the following examples supports the cloud design principle design for failure and nothing will fail? which of thee following can be used to protect amazon elastic compute. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From data-flair.training
Best AWS EC2 Tutorial (Amazon Elastic Compute Cloud) DataFlair Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws We require tls 1.2 and recommend tls 1.3. which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. which of the following examples supports the cloud design principle design for failure and nothing will fail? what happens when you use amazon virtual private cloud to create a new. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.youtube.com
How to Deploy to Amazon Elastic Compute Cloud Using AWS CodeDeploy In Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws A main route table is created by default. Controlling network access to your instances, for. what happens when you use amazon virtual private cloud to create a new vpc. We require tls 1.2 and recommend tls 1.3. clients must support the following: which of thee following can be used to protect amazon elastic compute cloud (amazon ec2). Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From medium.com
Elastic Compute Cloud(EC2) A Step by Step Guide by Kisan Tamang Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws clients must support the following: Controlling network access to your instances, for. which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. which of the following examples supports the cloud design principle design for failure and nothing will fail? We require tls 1.2 and recommend tls 1.3. A. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From pronteff.com
Explain Amazon EC2 (Elastic Compute Cloud)? Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws A main route table is created by default. what happens when you use amazon virtual private cloud to create a new vpc. which of the following examples supports the cloud design principle design for failure and nothing will fail? which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From subscription.packtpub.com
Amazon Elastic Compute Cloud Practical AWS Networking Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws what happens when you use amazon virtual private cloud to create a new vpc. which of the following examples supports the cloud design principle design for failure and nothing will fail? clients must support the following: which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. A. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From awstip.com
Designing and deploying a threetier architecture on Amazon Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws We require tls 1.2 and recommend tls 1.3. Controlling network access to your instances, for. clients must support the following: what happens when you use amazon virtual private cloud to create a new vpc. which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. A main route table. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.thenetworkdna.com
Introduction to Amazon Elastic Compute Cloud (Amazon EC2) The Network DNA Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws We require tls 1.2 and recommend tls 1.3. A main route table is created by default. Controlling network access to your instances, for. which of the following examples supports the cloud design principle design for failure and nothing will fail? clients must support the following: which of thee following can be used to protect amazon elastic compute. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.devopsschool.com
Amazon Elastic Service (Amazon EKS) Architecture Explained Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. We require tls 1.2 and recommend tls 1.3. Controlling network access to your instances, for. which of the following examples supports the cloud design principle design for failure and nothing will fail? clients must support the following: . Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From serverhealers.com
Amazon Elastic Compute Cloud (Ec2) Windows Instances • ServerHealers Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. which of the following examples supports the cloud design principle design for failure and nothing will fail? clients must support the following: A main route table is created by default. what happens when you use amazon virtual. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.devopsschool.com
Amazon Elastic Service (Amazon EKS) Architecture Explained Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of the following examples supports the cloud design principle design for failure and nothing will fail? Controlling network access to your instances, for. clients must support the following: what happens when you use amazon virtual private cloud to create a new vpc. which of thee following can be used to protect amazon elastic compute cloud. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From jayendrapatil.com
AWS Compute Services Cheat Sheet Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws A main route table is created by default. which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. Controlling network access to your instances, for. We require tls 1.2 and recommend tls 1.3. what happens when you use amazon virtual private cloud to create a new vpc. which. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From ipspecialist.net
Things You Should Know About Amazon Elastic Compute Cloud (EC2) Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws what happens when you use amazon virtual private cloud to create a new vpc. Controlling network access to your instances, for. which of the following examples supports the cloud design principle design for failure and nothing will fail? which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?.. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.testpreptraining.com
AWS Cloud ServiceSpecific Security Testprep Training Tutorials Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws A main route table is created by default. clients must support the following: which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. Controlling network access to your instances, for. which of the following examples supports the cloud design principle design for failure and nothing will fail? . Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From kyloot.com
Getting started with Elastic Cloud (Elasticsearch managed service) on Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws clients must support the following: Controlling network access to your instances, for. which of the following examples supports the cloud design principle design for failure and nothing will fail? A main route table is created by default. what happens when you use amazon virtual private cloud to create a new vpc. We require tls 1.2 and recommend. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.slideserve.com
PPT Amazon Elastic Compute Cloud PowerPoint Presentation, free Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. clients must support the following: We require tls 1.2 and recommend tls 1.3. which of the following examples supports the cloud design principle design for failure and nothing will fail? Controlling network access to your instances, for. A. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.whizlabs.com
Amazon Elastic Compute Cloud Guide Whizlabs Blog Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws what happens when you use amazon virtual private cloud to create a new vpc. We require tls 1.2 and recommend tls 1.3. clients must support the following: which of the following examples supports the cloud design principle design for failure and nothing will fail? Controlling network access to your instances, for. A main route table is created. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From docs.aws.amazon.com
Tutorial Erste Schritte mit AmazonEC2Instances für Linux Amazon Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of the following examples supports the cloud design principle design for failure and nothing will fail? which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. We require tls 1.2 and recommend tls 1.3. what happens when you use amazon virtual private cloud to create a new. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From hyperscalercloud.nl
Amazon Elastic Compute Cloud (EC2) and Amazon Elastic Load Balancing Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws clients must support the following: A main route table is created by default. Controlling network access to your instances, for. We require tls 1.2 and recommend tls 1.3. which of the following examples supports the cloud design principle design for failure and nothing will fail? which of thee following can be used to protect amazon elastic compute. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From blog.cloudthat.com
Amazon Elastic File System Configure Replication in AEFS CloudThat Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws Controlling network access to your instances, for. A main route table is created by default. what happens when you use amazon virtual private cloud to create a new vpc. We require tls 1.2 and recommend tls 1.3. which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. which. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From www.youtube.com
What is Amazon Elastic Compute Cloud (EC2) PASS AWS Certified Cloud Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of the following examples supports the cloud design principle design for failure and nothing will fail? We require tls 1.2 and recommend tls 1.3. what happens when you use amazon virtual private cloud to create a new vpc. clients must support the following: Controlling network access to your instances, for. A main route table is created. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From futransolutions.com
Introduction to AWS Architecture and components of AWS Architecture Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of the following examples supports the cloud design principle design for failure and nothing will fail? Controlling network access to your instances, for. what happens when you use amazon virtual private cloud to create a new vpc. clients must support the following: which of thee following can be used to protect amazon elastic compute cloud. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From 24x7itconnection.com
Amazon EC2 Instances Explained Elastic Cloud Compute Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws A main route table is created by default. clients must support the following: We require tls 1.2 and recommend tls 1.3. which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. which of the following examples supports the cloud design principle design for failure and nothing will fail?. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From hevodata.com
A QuickStart Guide to AWS High Availability and Its 3 Dimensions Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws clients must support the following: We require tls 1.2 and recommend tls 1.3. which of the following examples supports the cloud design principle design for failure and nothing will fail? what happens when you use amazon virtual private cloud to create a new vpc. A main route table is created by default. Controlling network access to your. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From docs.aws.amazon.com
Storage Amazon Elastic Compute Cloud Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws which of the following examples supports the cloud design principle design for failure and nothing will fail? which of thee following can be used to protect amazon elastic compute cloud (amazon ec2) instances hosted in aws?. clients must support the following: what happens when you use amazon virtual private cloud to create a new vpc. We. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.
From tekton.cloud
Introduction To Amazon Elastic Compute Cloud Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws clients must support the following: Controlling network access to your instances, for. which of the following examples supports the cloud design principle design for failure and nothing will fail? A main route table is created by default. We require tls 1.2 and recommend tls 1.3. what happens when you use amazon virtual private cloud to create a. Which Of The Following Can Be Used To Protect Amazon Elastic Compute Cloud Instances Hosted In Aws.