Transmission Encryption Key . This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. The key is shared between the sender and the recipient. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. Symmetric encryption uses a single key for both encryption and decryption. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement.
from tiptopsecurity.com
Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. The key is shared between the sender and the recipient. Symmetric encryption uses a single key for both encryption and decryption. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement.
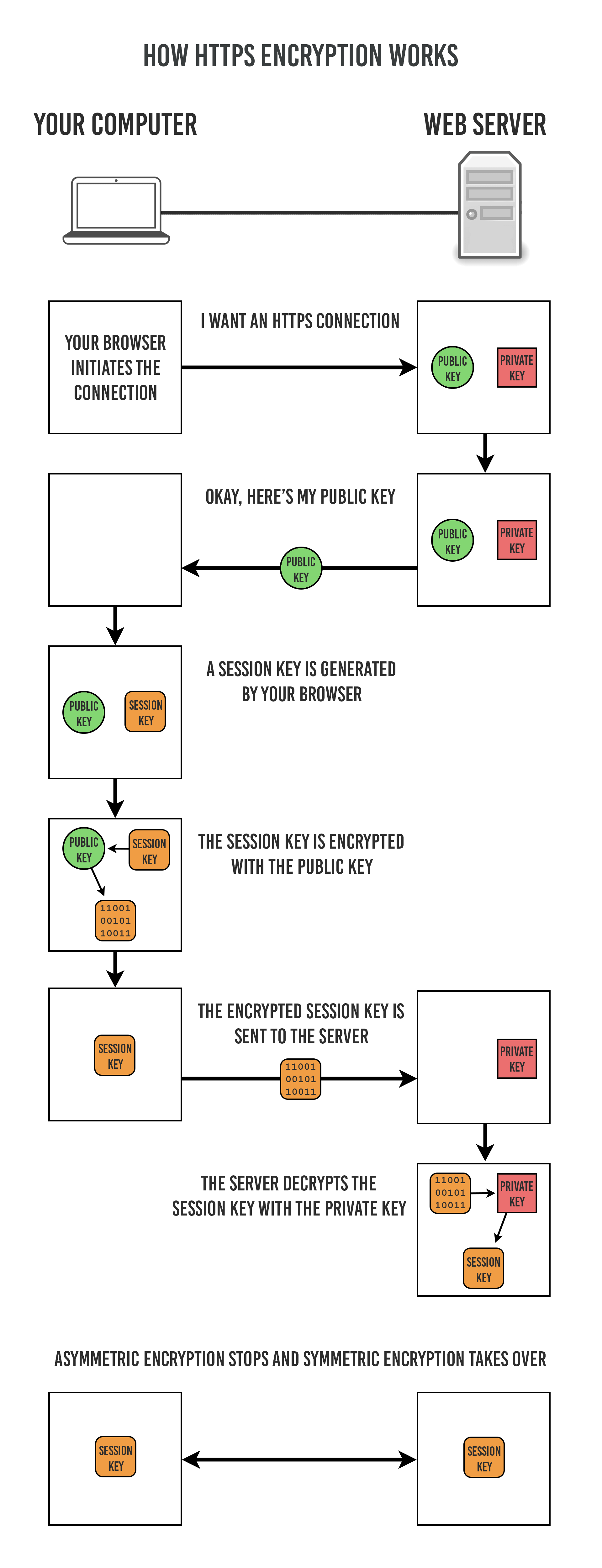
How Does HTTPS Work? RSA Encryption Explained « TipTopSecurity
Transmission Encryption Key When encrypting data, the sender uses the key to transform the plaintext into ciphertext. Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Symmetric encryption uses a single key for both encryption and decryption. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. The key is shared between the sender and the recipient.
From www.twilio.com
What is Public Key Cryptography? Twilio Transmission Encryption Key This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. Symmetric encryption uses a single key for both encryption and decryption. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Encryption keys (also called. Transmission Encryption Key.
From www.slideserve.com
PPT Information Security PowerPoint Presentation, free download ID Transmission Encryption Key This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Symmetric encryption uses a single key for both encryption and decryption. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. The key is shared between the sender and the recipient. When encrypting data, the sender uses the. Transmission Encryption Key.
From www.mdpi.com
JSAN Free FullText A Dynamic LightWeight Symmetric Encryption Transmission Encryption Key This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Symmetric encryption uses a single key for both encryption and decryption. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety.. Transmission Encryption Key.
From www.researchgate.net
The flow chart of the encryption process. Download Scientific Diagram Transmission Encryption Key This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Symmetric encryption uses a single key for both encryption and decryption. The key is shared between the sender and the recipient. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. When encrypting data, the sender uses the. Transmission Encryption Key.
From www.researchgate.net
Data encryption transmission model Download Scientific Diagram Transmission Encryption Key The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. The key is shared between the sender and the recipient. Symmetric encryption uses a single key for both encryption and decryption. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. This key management cheat. Transmission Encryption Key.
From www.researchgate.net
(a) Encryption transmission principle of optical fiber communication Transmission Encryption Key Symmetric encryption uses a single key for both encryption and decryption. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The key is shared. Transmission Encryption Key.
From tiptopsecurity.com
How Does HTTPS Work? RSA Encryption Explained « TipTopSecurity Transmission Encryption Key The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The key is shared between the sender and the recipient. Encryption. Transmission Encryption Key.
From www.researchgate.net
Schematic diagram of information transmission encryption system Transmission Encryption Key This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The recommendations below are provided as optional guidance to assist with achieving the data encryption. Transmission Encryption Key.
From www.slideserve.com
PPT Wireless networking PowerPoint Presentation, free download ID Transmission Encryption Key This key management cheat sheet provides developers with guidance for implementation of cryptographic key. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. The key is shared between the sender and the recipient. The recommendations. Transmission Encryption Key.
From www.sectigo.com
Public Key Cryptography Private vs Public Sectigo® Official Transmission Encryption Key Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The recommendations below are provided as optional guidance to. Transmission Encryption Key.
From www.encryptionconsulting.com
What is Key Management? How does Key Management work? Encryption Transmission Encryption Key Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Symmetric encryption uses a single key for both encryption and decryption. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. The. Transmission Encryption Key.
From www.researchgate.net
Encryption, transmission, and decryption process. Download Scientific Transmission Encryption Key The key is shared between the sender and the recipient. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. Symmetric encryption uses a single key for both encryption and decryption. When encrypting data, the. Transmission Encryption Key.
From best10vpn.com
Symmetric_key_encryption.svg Best 10 VPN Reviews Transmission Encryption Key This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The key is shared between the sender and the recipient. Symmetric encryption uses a single. Transmission Encryption Key.
From spinningsecurity.com
Public Key Cryptography 2022 Top Benefits, Applications & More Transmission Encryption Key This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The key is shared between the sender and the recipient. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. Encryption. Transmission Encryption Key.
From ico.org.uk
Types of encryption ICO Transmission Encryption Key When encrypting data, the sender uses the key to transform the plaintext into ciphertext. The key is shared between the sender and the recipient. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. This. Transmission Encryption Key.
From www.trentonsystems.com
Your AllinOne Guide to SelfEncrypting Drives (SEDs) Transmission Encryption Key When encrypting data, the sender uses the key to transform the plaintext into ciphertext. The key is shared between the sender and the recipient. Symmetric encryption uses a single key for both encryption and decryption. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. Encryption keys (also called cryptographic keys) are. Transmission Encryption Key.
From jessicaletitia.blogspot.com
Cryptography JessicaLetitia Transmission Encryption Key Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. Symmetric encryption uses a single key for both encryption and decryption. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The key is shared between the sender and the recipient. The recommendations below are provided. Transmission Encryption Key.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights Transmission Encryption Key The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. This document thoroughly explores encryption challenges relevant to. Transmission Encryption Key.
From learn.g2.com
How Public Key Encryption Ensures Data Integrity Transmission Encryption Key This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Symmetric encryption uses a single key for both encryption and decryption. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. The recommendations below are. Transmission Encryption Key.
From www.garykessler.net
An Overview of Cryptography Transmission Encryption Key The key is shared between the sender and the recipient. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. Symmetric encryption uses a single key for both encryption and decryption. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The recommendations below are provided as optional guidance to assist with. Transmission Encryption Key.
From o3schools.com
Ultimate Guide to Understanding What Symmetric Key Cryptography is 2023 Transmission Encryption Key This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. When encrypting data, the sender. Transmission Encryption Key.
From help.mypurecloud.com
Recording encryption key overview Genesys Cloud Resource Center Transmission Encryption Key Symmetric encryption uses a single key for both encryption and decryption. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. When encrypting data, the sender uses the key to transform the plaintext into ciphertext.. Transmission Encryption Key.
From ded9.com
Endtoend encryption; A way to secure communication? Transmission Encryption Key The key is shared between the sender and the recipient. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. Symmetric encryption uses a single key for both encryption and decryption. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. Encryption keys (also called. Transmission Encryption Key.
From www.thesslstore.com
Cryptographic Keys 101 What They Are & How They Secure Data Hashed Transmission Encryption Key This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. Symmetric encryption uses a single key for both encryption and decryption. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and. Transmission Encryption Key.
From trailhead.salesforce.com
Guard Data Transmission Salesforce Trailhead Transmission Encryption Key Symmetric encryption uses a single key for both encryption and decryption. The key is shared between the sender and the recipient. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. Encryption keys (also called cryptographic keys) are. Transmission Encryption Key.
From kinsta.com
What Is Data Encryption? Definition, Types, and Best Practices Kinsta® Transmission Encryption Key This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. When encrypting data, the sender uses the key to transform the. Transmission Encryption Key.
From www.researchgate.net
Schematic diagram of information transmission encryption system Transmission Encryption Key This key management cheat sheet provides developers with guidance for implementation of cryptographic key. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. The recommendations below are provided as optional guidance to assist with achieving. Transmission Encryption Key.
From www.okta.com
Public Key Encryption What Is Public Cryptography? Okta AU & NZ Transmission Encryption Key The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. The key is shared between the sender and the recipient. Symmetric. Transmission Encryption Key.
From www.appviewx.com
Asymmetric Encryption How Asymmetric Encryption Works Transmission Encryption Key This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The key is shared between the sender and the recipient. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. The recommendations below are provided. Transmission Encryption Key.
From www.proofpoint.com
What Is Encryption? Definition, Types & More Proofpoint US Transmission Encryption Key The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. This key management cheat sheet. Transmission Encryption Key.
From quizturbinates.z21.web.core.windows.net
What Is Layer 3 Encryption Transmission Encryption Key The key is shared between the sender and the recipient. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. Symmetric encryption uses a single key for both encryption and decryption. When encrypting data, the sender uses the key. Transmission Encryption Key.
From www.freecodecamp.org
What is Encryption at Rest? Explained for Security Beginners Transmission Encryption Key Symmetric encryption uses a single key for both encryption and decryption. Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. This. Transmission Encryption Key.
From www.scribd.com
DATA TRANSMISSION f3 PDF Key (Cryptography) Encryption Transmission Encryption Key This key management cheat sheet provides developers with guidance for implementation of cryptographic key. The key is shared between the sender and the recipient. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. Symmetric encryption uses a single key for both encryption and decryption. When encrypting data, the sender uses the. Transmission Encryption Key.
From www.researchgate.net
The transmission mechanism for cryptographical key Download Transmission Encryption Key This document thoroughly explores encryption challenges relevant to public safety lmr systems and provides the public safety. The recommendations below are provided as optional guidance to assist with achieving the data encryption in transit requirement. The key is shared between the sender and the recipient. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. This. Transmission Encryption Key.
From www.cisco.com
What Is Encryption? Explanation and Types Cisco Transmission Encryption Key Encryption keys (also called cryptographic keys) are the strings of bits generated to encode and decode data and voice transmissions. This key management cheat sheet provides developers with guidance for implementation of cryptographic key. Symmetric encryption uses a single key for both encryption and decryption. When encrypting data, the sender uses the key to transform the plaintext into ciphertext. This. Transmission Encryption Key.