Amp Detection Name . This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Www.cisco.com amp for endpoints user guide. If you are looking for a description what a vioc means in detail, take. Afterwards, you may want to explore the console’s abilities to restore. Use these resources to familiarize yourself with the community: Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect.
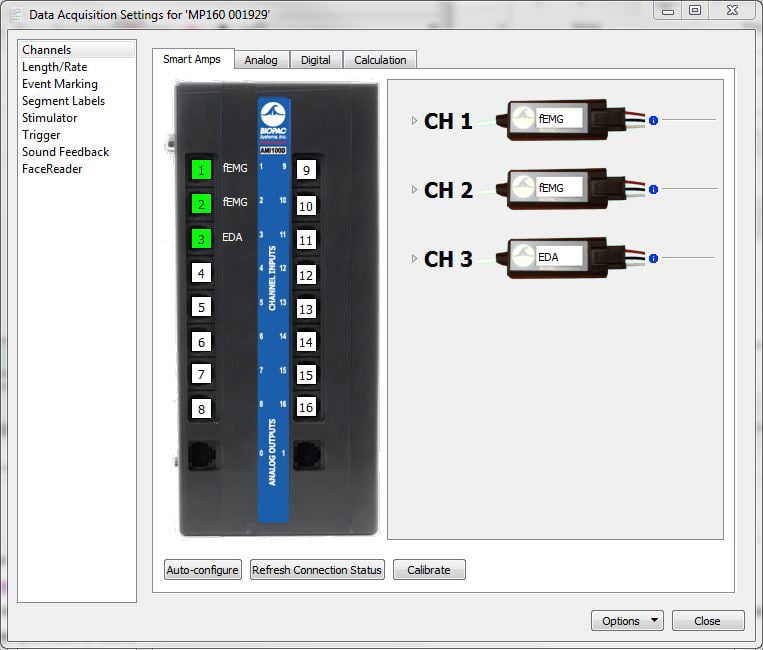
from www.biopac.com
Use these resources to familiarize yourself with the community: Afterwards, you may want to explore the console’s abilities to restore. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. If you are looking for a description what a vioc means in detail, take. Www.cisco.com amp for endpoints user guide. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect.
EMG Electromyogram Smart Amplifier EMG100D Research BIOPAC
Amp Detection Name Afterwards, you may want to explore the console’s abilities to restore. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. If you are looking for a description what a vioc means in detail, take. Afterwards, you may want to explore the console’s abilities to restore. Use these resources to familiarize yourself with the community: This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Www.cisco.com amp for endpoints user guide.
From www.laserse.com
Photodiode Amplifier Module Light Intensity Detection Module Illuminance Meter LaserSE Amp Detection Name If you are looking for a description what a vioc means in detail, take. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Www.cisco.com amp for endpoints user guide. Afterwards, you may want to explore the console’s abilities to restore. This document describes the steps to create a. Amp Detection Name.
From www.slideshare.net
Utility Detection & Mapping Amp Detection Name If you are looking for a description what a vioc means in detail, take. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Afterwards, you may want to explore the console’s abilities to restore. Www.cisco.com amp for endpoints user guide. This document describes. Amp Detection Name.
From www.mdpi.com
Electronics Free FullText A CMOS DoubleDemodulation LockIn Amplifier for Stimulated Raman Amp Detection Name Use these resources to familiarize yourself with the community: Www.cisco.com amp for endpoints user guide. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. If you are looking for a description what a vioc means in detail, take. Afterwards, you may want to explore the console’s abilities to. Amp Detection Name.
From www.sampleinst.com
时间分辨 SPM_Sample Instruments Amp Detection Name Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. If you are looking for a description what a vioc means in detail,. Amp Detection Name.
From www.edn.com
Design a DSP lockin amplifier, Part 1 Background EDN Amp Detection Name Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. If you are looking for a description what a vioc means in detail, take. Www.cisco.com amp for endpoints user guide. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability. Amp Detection Name.
From primewirecable.com
Amp Detection 50ft 12/3 SJTW Visual Amperage Detection 3Outlet Cord — Prime Wire & Cable Inc. Amp Detection Name Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. If you are looking for a description what a vioc means in detail, take. Afterwards, you may want to explore the console’s abilities to restore. Use these resources to familiarize yourself with the community: Www.cisco.com amp for endpoints user. Amp Detection Name.
From www.heyisensors.com
Professional Rgb Color Sensor Amplifier & Detection Head All In One Amp Detection Name Afterwards, you may want to explore the console’s abilities to restore. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Use these resources to familiarize yourself with the community: Find the samples of the naming convention patterns of threats collected in secure endpoint. Amp Detection Name.
From www.researchgate.net
Measurement of cAMP phosphodiesterase activity. (A) PDE reaction... Download Scientific Diagram Amp Detection Name Afterwards, you may want to explore the console’s abilities to restore. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. If you are looking for a description. Amp Detection Name.
From www.electricautomationnetwork.com
E3NXCA21 2M 671057 E3NX0003F OMRON Amplifier Detection Ma.. Amp Detection Name Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. This document describes the steps to create a simple custom detection list to. Amp Detection Name.
From www.rackyrax.com
APC NBPD0123 surveillance & detection Amp Detection Name If you are looking for a description what a vioc means in detail, take. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Afterwards, you may want. Amp Detection Name.
From www.circuitbasics.com
Ultimate Guide to OpAmps Part 1 Circuit Basics Amp Detection Name If you are looking for a description what a vioc means in detail, take. Afterwards, you may want to explore the console’s abilities to restore. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Amp’s vulnerable software feature shows you all the software on your endpoints that can. Amp Detection Name.
From primewirecable.com
Amp Detection 2ft 12/3 STW 3Outlet Adapter with Visual Amperage Detec — Prime Wire & Cable Inc. Amp Detection Name Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Www.cisco.com amp for endpoints user guide. If you are looking for a description. Amp Detection Name.
From primewirecable.com
Amp Detection 100ft 12/3 SJTW 3Outlet Cord with Visual Amperage Detec — Prime Wire & Cable Inc. Amp Detection Name Use these resources to familiarize yourself with the community: If you are looking for a description what a vioc means in detail, take. Www.cisco.com amp for endpoints user guide. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Afterwards, you may want to explore the console’s abilities to. Amp Detection Name.
From www.studocu.com
2001 9 Communication Manual1 (6) EXPERIMENT 1 GENERATION & DETECTION OF BPSK AIM To design Amp Detection Name If you are looking for a description what a vioc means in detail, take. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Use these resources to familiarize yourself with the community: Www.cisco.com amp for endpoints user guide. Afterwards, you may want to. Amp Detection Name.
From primewirecable.com
Amp Detection 50ft 12/3 SJTW Visual Amperage Detection 3Outlet Cord — Prime Wire & Cable Inc. Amp Detection Name Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Www.cisco.com amp for endpoints user guide. If you are looking for a description. Amp Detection Name.
From electronics360.globalspec.com
Logarithmic Amplifier Chip Design and Application Considerations Electronics360 Amp Detection Name Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Afterwards, you may want to explore the console’s abilities to restore. If you are looking for a description what a vioc means in detail, take. Find the samples of the naming convention patterns of. Amp Detection Name.
From www.researchgate.net
Defect detection using OTM method for operational amplifier with... Download Scientific Diagram Amp Detection Name Use these resources to familiarize yourself with the community: This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Afterwards, you may want to explore the console’s abilities. Amp Detection Name.
From www.cisco.com
Configure a Simple Custom Detection List on the AMP for Endpoints Portal Cisco Amp Detection Name Afterwards, you may want to explore the console’s abilities to restore. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Www.cisco.com amp for endpoints user guide. Use these resources to familiarize yourself with the community: This document describes the steps to create a simple custom detection list to. Amp Detection Name.
From www.youtube.com
Peak Detector Circuit Explained YouTube Amp Detection Name If you are looking for a description what a vioc means in detail, take. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Www.cisco.com amp for endpoints. Amp Detection Name.
From eureka.patsnap.com
AMP detection improvement method based on machine learning Eureka Patsnap develop Amp Detection Name This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Use these resources to familiarize yourself with the community: Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. If you are looking for a description what a. Amp Detection Name.
From www.heyisensors.com
Professional Rgb Color Sensor Amplifier & Detection Head All In One Amp Detection Name Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. If you are looking for a description what a vioc means in detail, take. Use these resources to familiarize yourself with the community: Afterwards, you may want to explore the console’s abilities to restore.. Amp Detection Name.
From www.slideshare.net
Utility Detection & Mapping Amp Detection Name Www.cisco.com amp for endpoints user guide. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Use these resources to familiarize yourself with. Amp Detection Name.
From www.slideshare.net
Utility Detection & Mapping Amp Detection Name Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. If you are looking for a description what a vioc means in detail,. Amp Detection Name.
From www.searchenginejournal.com
How to Test Your AMP Pages The Complete Guide Amp Detection Name Www.cisco.com amp for endpoints user guide. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Use these resources to familiarize yourself with the community: This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. If you are. Amp Detection Name.
From www.researchgate.net
A schematic of an optical amplification and detection system. The input... Download Scientific Amp Detection Name Afterwards, you may want to explore the console’s abilities to restore. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. This document. Amp Detection Name.
From www.aliexpress.com
10PCSINA240CurrentDetectionAmplifierCurrentVoltageMonitoringBidirectionalCurrent Amp Detection Name Www.cisco.com amp for endpoints user guide. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. This document describes the steps to create. Amp Detection Name.
From slidetodoc.com
Signal Detection and How to Build an Audio Amp Detection Name If you are looking for a description what a vioc means in detail, take. Afterwards, you may want to explore the console’s abilities to restore. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Www.cisco.com amp for endpoints user guide. Use these resources to familiarize yourself with the. Amp Detection Name.
From www.biopac.com
EMG Electromyogram Smart Amplifier EMG100D Research BIOPAC Amp Detection Name Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Www.cisco.com amp for endpoints user guide. Use these resources to familiarize yourself with the community: Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis. Amp Detection Name.
From www.circuitstoday.com
Zero Crossing Detector Circuit Diagram Working and Waveform Amp Detection Name If you are looking for a description what a vioc means in detail, take. Www.cisco.com amp for endpoints user guide. Afterwards, you may want to explore the console’s abilities to restore. Use these resources to familiarize yourself with the community: Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use. Amp Detection Name.
From www.slideshare.net
Introduction to Scanning Tunneling Microscopy Amp Detection Name If you are looking for a description what a vioc means in detail, take. Use these resources to familiarize yourself with the community: Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. Www.cisco.com amp for endpoints user guide. Find the samples of the. Amp Detection Name.
From www.researchgate.net
Sketch maps for the PVDF sensor and the related detection system (a)... Download Scientific Amp Detection Name If you are looking for a description what a vioc means in detail, take. Find the samples of the naming convention patterns of threats collected in secure endpoint to help with threat analysis that protect. Afterwards, you may want to explore the console’s abilities to restore. This document describes the steps to create a simple custom detection list to detect,. Amp Detection Name.
From www.researchgate.net
AMP detection with colloidal gold immunochromatographic strip assay... Download Scientific Diagram Amp Detection Name Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Use these resources to familiarize yourself with the community: If you are looking. Amp Detection Name.
From www.researchgate.net
Application of a chemiluminescence‐based AMP detection system as a... Download Scientific Diagram Amp Detection Name If you are looking for a description what a vioc means in detail, take. Afterwards, you may want to explore the console’s abilities to restore. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Www.cisco.com amp for endpoints user guide. Find the samples of the naming convention patterns. Amp Detection Name.
From www.researchgate.net
Defect detection using IOI method for operational amplifier with... Download Scientific Diagram Amp Detection Name Afterwards, you may want to explore the console’s abilities to restore. Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. If you are looking for a description what a vioc means in detail, take. This document describes the steps to create a simple. Amp Detection Name.
From www.mdpi.com
Sensors Free FullText Lockin AmplifierBased Impedance Detection of Tissue Type Using a Amp Detection Name Amp’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. This document describes the steps to create a simple custom detection list to detect, block and quarantine specific files to prevent. Afterwards, you may want to explore the console’s abilities to restore. Www.cisco.com amp. Amp Detection Name.