Kong Keycloak Authentication . Wondering how to secure apis and services using openid connect? Authentication is delegated to keycloak. Clients apps are registered into keycloak and provide the ability to an user to claim an access token. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Set up kong oauth token authentication. Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the.
from tech.aufomm.com
Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Authentication is delegated to keycloak. Set up kong oauth token authentication. Clients apps are registered into keycloak and provide the ability to an user to claim an access token. Wondering how to secure apis and services using openid connect? Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the.
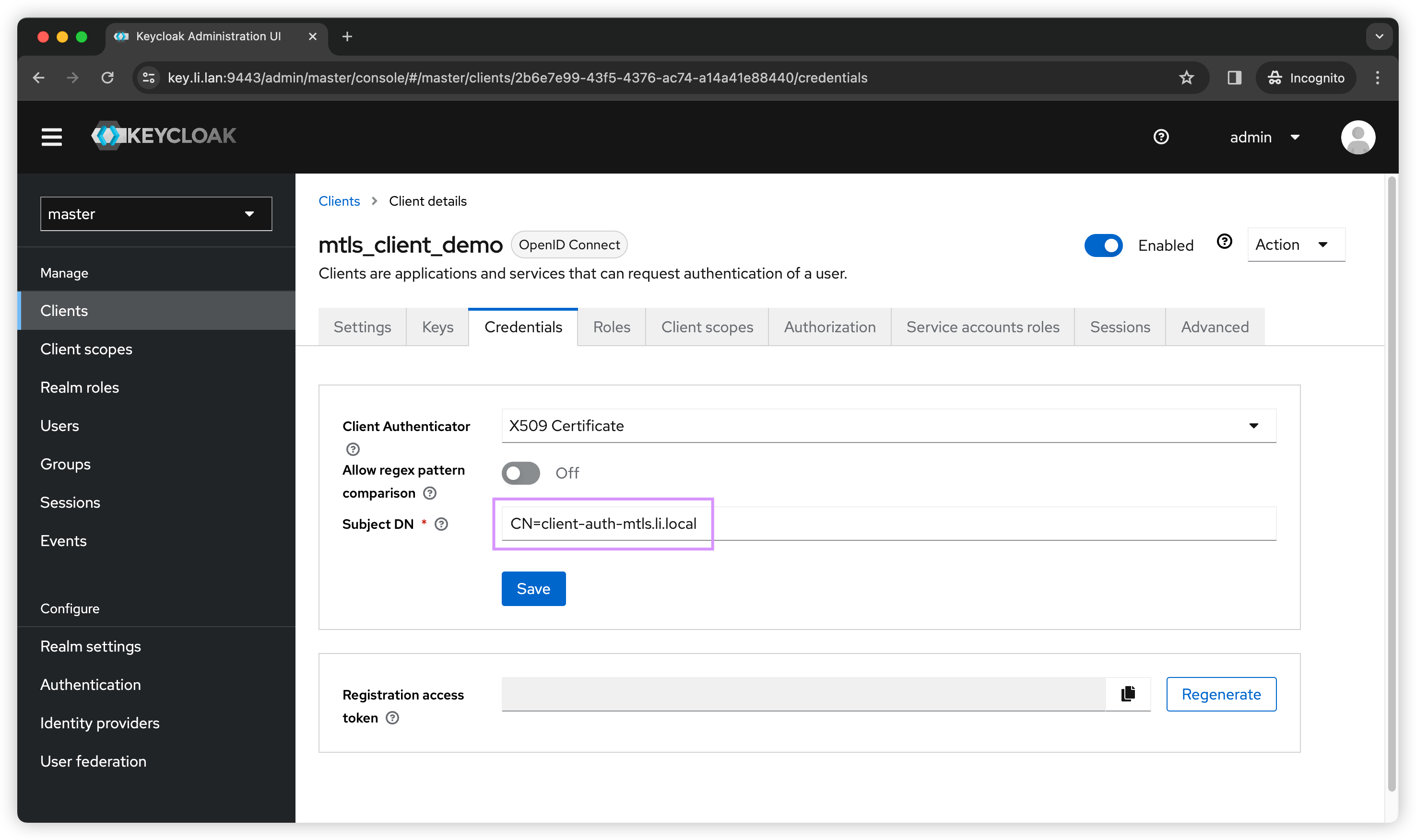
How to Use CertificateBound Access Token With Kong and Keycloak
Kong Keycloak Authentication Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Set up kong oauth token authentication. Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Wondering how to secure apis and services using openid connect? Authentication is delegated to keycloak. Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Clients apps are registered into keycloak and provide the ability to an user to claim an access token.
From awesomeopensource.com
Springboot Kong Keycloak Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to. Kong Keycloak Authentication.
From tech.aufomm.com
How to Use CertificateBound Access Token With Kong and Keycloak Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Clients apps are registered into keycloak and provide the ability to an user to claim an access token. Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Using the keycloak and kong gateway configuration from the prerequisites, set up. Kong Keycloak Authentication.
From github.com
Kong, OIDC and Keycloak Authentication fails with an error "KONG Error Kong Keycloak Authentication Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Clients apps are registered into keycloak and provide the ability to an. Kong Keycloak Authentication.
From faun.pub
Securing the application with Kong & Keycloak 101 by Harsh Manvar Kong Keycloak Authentication Clients apps are registered into keycloak and provide the ability to an user to claim an access token. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Authentication is delegated to keycloak. Create a confidential client kong with private_key_jwt. Kong Keycloak Authentication.
From faun.pub
Kong JWT scope base auth with Keycloak by Harsh Manvar FAUN Publication Kong Keycloak Authentication Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Using the keycloak and kong gateway configuration from the prerequisites,. Kong Keycloak Authentication.
From stackoverflow.com
Passing Bearer token from kong to keycloak to be authenticated and then Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Authentication is delegated to keycloak. Wondering how to secure apis and services using openid connect? Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Using the keycloak and kong. Kong Keycloak Authentication.
From awesomeopensource.com
Kong Konga Keycloak Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Set up kong oauth token authentication. Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Clients apps are registered into keycloak and provide the ability to an user to claim an access token. Authentication is delegated to keycloak. Currently,. Kong Keycloak Authentication.
From faun.pub
Securing the application with Kong & Keycloak 101 by Harsh Manvar Kong Keycloak Authentication Authentication is delegated to keycloak. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Create a confidential client kong. Kong Keycloak Authentication.
From www.jerney.io
Securing APIs with Kong and Keycloak Part 1 Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Wondering how to secure apis and services using openid connect? Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys. Kong Keycloak Authentication.
From www.jerney.io
Securing APIs with Kong and Keycloak Part 2 Kong Keycloak Authentication Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Kong easily integrates with identity providers (idps), like keycloak, to. Kong Keycloak Authentication.
From faun.pub
Securing the application with Kong & Keycloak 101 by Harsh Manvar Kong Keycloak Authentication Set up kong oauth token authentication. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Create a confidential client kong with private_key_jwt authentication. Kong Keycloak Authentication.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Kong Keycloak Authentication Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Set up kong oauth token authentication. Wondering how to secure apis and services using openid connect? Currently, when end users try to. Kong Keycloak Authentication.
From www.jerney.io
Securing APIs with Kong and Keycloak Part 1 Kong Keycloak Authentication Wondering how to secure apis and services using openid connect? Set up kong oauth token authentication. Clients apps are registered into keycloak and provide the ability to an user to claim an access token. Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Authentication is delegated to keycloak. Kong easily integrates. Kong Keycloak Authentication.
From tech.aufomm.com
How to Use CertificateBound Access Token With Kong and Keycloak Kong Keycloak Authentication Set up kong oauth token authentication. Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Wondering how to secure apis and services using openid connect? Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Authentication is delegated to keycloak. Currently, when end users try. Kong Keycloak Authentication.
From tech.aufomm.com
How to Use CertificateBound Access Token With Kong and Keycloak Kong Keycloak Authentication Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Wondering how to secure apis and services using openid connect? Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Kong easily integrates with identity providers (idps), like keycloak, to secure and. Kong Keycloak Authentication.
From hitec2022.github.io
Kong에 키클락 연동 (OIDC) hitec Dev Kong Keycloak Authentication Authentication is delegated to keycloak. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Set up kong oauth token authentication. Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of. Kong Keycloak Authentication.
From www.jerney.io
Securing APIs with Kong and Keycloak Part 1 Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Using the. Kong Keycloak Authentication.
From github.com
GitHub Advanc2d/kongmsakeycloak Keycloak으로 Kong OIDC plugin 적용과 Kong Keycloak Authentication Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Wondering how to secure apis and services using openid connect?. Kong Keycloak Authentication.
From qiita.com
Keycloakを使ってAPI GatewayでAPIをアクセス制限する Qiita Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Authentication is delegated to keycloak. Set up kong oauth token authentication. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Currently, when end users try to hit one of the backend services through. Kong Keycloak Authentication.
From tech.aufomm.com
How to Use CertificateBound Access Token With Kong and Keycloak Kong Keycloak Authentication Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Authentication is delegated to keycloak. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Wondering how to secure apis and services using openid connect? Clients. Kong Keycloak Authentication.
From faun.pub
Kong JWT scope base auth with Keycloak by Harsh Manvar FAUN Publication Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is. Kong Keycloak Authentication.
From github.com
GitHub d4rkstar/kongkongakeycloak short tutorial to install kong Kong Keycloak Authentication Wondering how to secure apis and services using openid connect? Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Set up kong oauth token authentication. Authentication is delegated to keycloak. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate. Kong Keycloak Authentication.
From www.youtube.com
How to Use the Kong Gateway Key Authentication Plugin YouTube Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Wondering how to secure apis and services using openid connect? Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Authentication is delegated to keycloak. Create a confidential client kong with private_key_jwt authentication and. Kong Keycloak Authentication.
From www.jerney.io
Securing APIs with Kong and Keycloak Part 1 Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Wondering how to secure apis and services using openid connect? Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the.. Kong Keycloak Authentication.
From github.com
GitHub thanhduongv/kongapigatewaykeycloak Kong Keycloak Authentication Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Authentication is delegated to keycloak. Currently, when end users try to hit one of the backend services through kong using. Kong Keycloak Authentication.
From cycykum.medium.com
Securing an API with Kong and Keycloak using OAuth 2.0 Bearer only Kong Keycloak Authentication Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Set up kong oauth token authentication. Wondering how to secure apis and services using openid connect? Clients apps are registered into keycloak and provide the ability. Kong Keycloak Authentication.
From www.devoperandi.com
Kong API Gateway Kong Keycloak Authentication Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Wondering how to secure apis and services using openid connect? Clients apps are registered. Kong Keycloak Authentication.
From www.youtube.com
Kong Keycloak Integration with Custom Plugin in lua YouTube Kong Keycloak Authentication Clients apps are registered into keycloak and provide the ability to an user to claim an access token. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Using the keycloak and kong gateway configuration from the prerequisites, set up. Kong Keycloak Authentication.
From www.jerney.io
Securing APIs with Kong and Keycloak Part 1 Kong Keycloak Authentication Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Wondering how to secure apis and services using openid connect? Using the keycloak and kong gateway. Kong Keycloak Authentication.
From dev.to
Securing your site via OIDC, powered by Kong and KeyCloak DEV Community Kong Keycloak Authentication Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Authentication is delegated to keycloak. Wondering how to secure apis and services using openid connect? Set up kong oauth token authentication. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the. Clients apps are registered into. Kong Keycloak Authentication.
From github.com
GitHub Advanc2d/kongmsakeycloak Keycloak으로 Kong OIDC plugin 적용과 Kong Keycloak Authentication Wondering how to secure apis and services using openid connect? Create a confidential client kong with private_key_jwt authentication and configure keycloak to download the public keys from [the. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Authentication is delegated to keycloak. Using the keycloak and kong gateway configuration. Kong Keycloak Authentication.
From faun.pub
Securing the application with Kong & Keycloak 101 by Harsh Manvar Kong Keycloak Authentication Authentication is delegated to keycloak. Clients apps are registered into keycloak and provide the ability to an user to claim an access token. Set up kong oauth token authentication. Kong easily integrates with identity providers (idps), like keycloak, to secure and govern apis. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid. Kong Keycloak Authentication.
From blog.csdn.net
通过Keycloak API理解OAuth2与OpenID Connect_keycloak和oauth2_nklinsirui的博客CSDN博客 Kong Keycloak Authentication Clients apps are registered into keycloak and provide the ability to an user to claim an access token. Authentication is delegated to keycloak. Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Kong easily integrates with identity providers (idps),. Kong Keycloak Authentication.
From stackoverflow.com
kong Is keycloak behind api gateway a good practice? Stack Overflow Kong Keycloak Authentication Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Set up kong oauth token authentication. Quick sharing on how you can further secure your api or endpoints with oidc, and powered by kong and keycloak. Using the keycloak and. Kong Keycloak Authentication.
From github.com
GitHub afoth/kongkeycloackreactadminexample Example how to use a Kong Keycloak Authentication Currently, when end users try to hit one of the backend services through kong using a web browser, the end user is required to authenticate with keycloak first before the. Using the keycloak and kong gateway configuration from the prerequisites, set up an instance of the openid connect plugin with. Kong easily integrates with identity providers (idps), like keycloak, to. Kong Keycloak Authentication.