Windows Event Log Grok Pattern . Example configuration files for logstash. Contribute to siemonster/logstash development by creating an account on github. Even though your scope is specific to the commandline field, parsing. It seems that windows zip cannot extract specific files. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. The syntax for a grok pattern is %. Grok works by combining text patterns into something that matches your logs. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. If you can parse data with a regex, you can implement it with grok. Also, i found out that windows event log does not come in string. A logstash grok filter to parse and tokenize the message field of windows eventlog entries.
from www.manageengine.com
It seems that windows zip cannot extract specific files. If you can parse data with a regex, you can implement it with grok. Grok works by combining text patterns into something that matches your logs. Even though your scope is specific to the commandline field, parsing. Also, i found out that windows event log does not come in string. Example configuration files for logstash. The syntax for a grok pattern is %. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Contribute to siemonster/logstash development by creating an account on github.
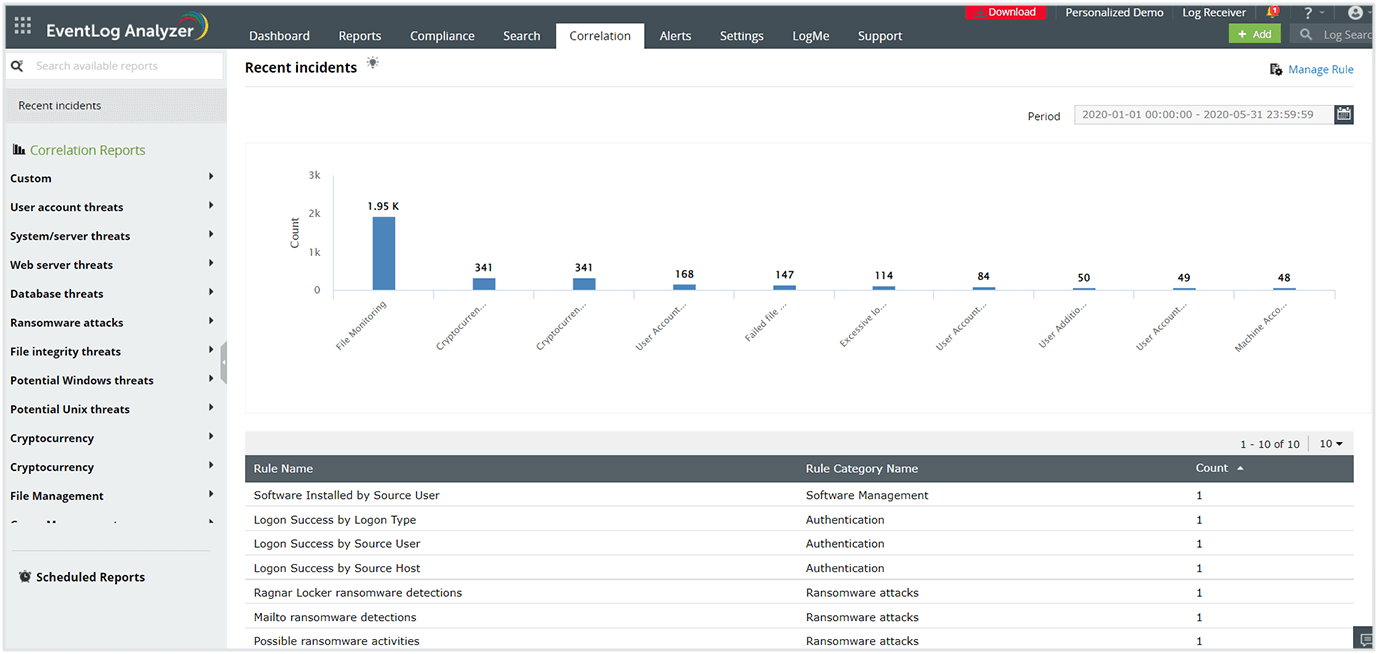
Windows Event Log Monitoring ManageEngine EventLog Analyzer
Windows Event Log Grok Pattern Also, i found out that windows event log does not come in string. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Even though your scope is specific to the commandline field, parsing. Example configuration files for logstash. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. Contribute to siemonster/logstash development by creating an account on github. It seems that windows zip cannot extract specific files. Grok works by combining text patterns into something that matches your logs. If you can parse data with a regex, you can implement it with grok. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. Also, i found out that windows event log does not come in string. The syntax for a grok pattern is %.
From www.wikihow.com
How to Check an IIS Event Log on Windows 7 Steps (with Pictures) Windows Event Log Grok Pattern It seems that windows zip cannot extract specific files. Even though your scope is specific to the commandline field, parsing. Example configuration files for logstash. Grok works by combining text patterns into something that matches your logs. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Contribute to siemonster/logstash development by creating an account on github. Also, i found out that windows event log. Windows Event Log Grok Pattern.
From blog.netwrix.com
Windows Event Log Forwarding with PowerShell Windows Event Log Grok Pattern Also, i found out that windows event log does not come in string. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. Even though your scope is specific to the commandline field, parsing. Grok works by combining text patterns into something that matches your logs. Contribute. Windows Event Log Grok Pattern.
From miteshsureja.blogspot.com
Mitesh Sureja's Blog How to Read/Write Windows Event Logs? Windows Event Log Grok Pattern It seems that windows zip cannot extract specific files. Even though your scope is specific to the commandline field, parsing. Grok works by combining text patterns into something that matches your logs. The syntax for a grok pattern is %. Also, i found out that windows event log does not come in string. Yes, you heard it right, elk (elasticsearch,. Windows Event Log Grok Pattern.
From diagramlibraryschemer.z19.web.core.windows.net
Event Viewer Windows 11 Logs Windows Event Log Grok Pattern Even though your scope is specific to the commandline field, parsing. Example configuration files for logstash. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. It seems that windows zip cannot extract specific files. Also, i found out that windows event log does not come in string. Yes, you. Windows Event Log Grok Pattern.
From www.layerstack.com
LayerStack Tutorials LayerStack How to check the Windows event logs Windows Event Log Grok Pattern Grok works by combining text patterns into something that matches your logs. Even though your scope is specific to the commandline field, parsing. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a. Windows Event Log Grok Pattern.
From trevojnui.ru
Windows service event log event Windows Event Log Grok Pattern Example configuration files for logstash. If you can parse data with a regex, you can implement it with grok. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. Contribute to siemonster/logstash development by creating an account on github. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Also, i found out that windows event log does not come. Windows Event Log Grok Pattern.
From fast-lisa.unibo.it
Write To Windows Event Log Command Line Flash Sales fastlisa.unibo.it Windows Event Log Grok Pattern If you can parse data with a regex, you can implement it with grok. Even though your scope is specific to the commandline field, parsing. The syntax for a grok pattern is %. Also, i found out that windows event log does not come in string. A logstash grok filter to parse and tokenize the message field of windows eventlog. Windows Event Log Grok Pattern.
From coralogix.com
Tutorial Logstash Grok Patterns with Examples Coralogix Windows Event Log Grok Pattern Contribute to siemonster/logstash development by creating an account on github. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. Also, i found out that windows event log does not come in string. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a. Windows Event Log Grok Pattern.
From www.windowscentral.com
How to use Event Viewer on Windows 10 Windows Central Windows Event Log Grok Pattern Example configuration files for logstash. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. If you can parse data with a regex, you can implement it. Windows Event Log Grok Pattern.
From coralogix.com
Tutorial Logstash Grok Patterns with Examples Coralogix Windows Event Log Grok Pattern If you can parse data with a regex, you can implement it with grok. Even though your scope is specific to the commandline field, parsing. Also, i found out that windows event log does not come in string. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries. Windows Event Log Grok Pattern.
From www.vkernel.ro
How to configure Windows Event Log Forwarding Windows Event Log Grok Pattern Even though your scope is specific to the commandline field, parsing. The syntax for a grok pattern is %. Example configuration files for logstash. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Also, i found out that windows event log does not come in string. If you can. Windows Event Log Grok Pattern.
From logz.io
Windows Event Log Analysis with Winlogbeat & Logz.io Windows Event Log Grok Pattern Also, i found out that windows event log does not come in string. Example configuration files for logstash. It seems that windows zip cannot extract specific files. If you can parse data with a regex, you can implement it with grok. The syntax for a grok pattern is %. Grok works by combining text patterns into something that matches your. Windows Event Log Grok Pattern.
From documentation.trendminer.com
How to get Windows event logs? Windows Event Log Grok Pattern %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. It seems that windows zip cannot extract specific files. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. Grok works by combining text patterns into something that matches your logs. Even though your scope is specific to the commandline field, parsing. Contribute to siemonster/logstash development by creating an account. Windows Event Log Grok Pattern.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log Grok Pattern Even though your scope is specific to the commandline field, parsing. Example configuration files for logstash. Grok works by combining text patterns into something that matches your logs. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. It seems that windows zip cannot extract specific files.. Windows Event Log Grok Pattern.
From mysupport.razer.com
How to export Windows Event Logs Windows Event Log Grok Pattern A logstash grok filter to parse and tokenize the message field of windows eventlog entries. It seems that windows zip cannot extract specific files. Example configuration files for logstash. Also, i found out that windows event log does not come in string. Grok works by combining text patterns into something that matches your logs. Contribute to siemonster/logstash development by creating. Windows Event Log Grok Pattern.
From www.hackthebox.com
5 Windows event log analysis tools (for beginner blue teamers) Windows Event Log Grok Pattern Even though your scope is specific to the commandline field, parsing. Also, i found out that windows event log does not come in string. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. A logstash grok filter to parse and tokenize the message field of windows. Windows Event Log Grok Pattern.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log Grok Pattern A logstash grok filter to parse and tokenize the message field of windows eventlog entries. If you can parse data with a regex, you can implement it with grok. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. Example configuration files for logstash. Also, i found. Windows Event Log Grok Pattern.
From narodnatribuna.info
Understanding The Windows Application Event Log Components Windows Event Log Grok Pattern Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. The syntax for a grok pattern is %. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. If you can parse data with a regex, you can implement it with grok. Grok works by combining text patterns into something that matches. Windows Event Log Grok Pattern.
From www.digitalcitizen.life
How to work with the Event Viewer in Windows Digital Citizen Windows Event Log Grok Pattern Even though your scope is specific to the commandline field, parsing. Example configuration files for logstash. Grok works by combining text patterns into something that matches your logs. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. Contribute to siemonster/logstash development by creating an account on github. It seems that windows zip cannot extract. Windows Event Log Grok Pattern.
From www.elastic.co
Getting Started with the Grok Debugger Kibana Guide [6.8] Elastic Windows Event Log Grok Pattern %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. Contribute to siemonster/logstash development by creating an account on github. Even though your scope is specific to the commandline field, parsing. If you can parse data with a regex, you can implement it with grok. Yes, you heard it right,. Windows Event Log Grok Pattern.
From www.tactig.com
How to Configure and Analyze Event Logs in Windows 10? Tactig Windows Event Log Grok Pattern %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Even though your scope is specific to the commandline field, parsing. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. Contribute to siemonster/logstash development by creating. Windows Event Log Grok Pattern.
From www.elastic.co
Debug grok expressions Kibana Guide [7.17] Elastic Windows Event Log Grok Pattern Also, i found out that windows event log does not come in string. Even though your scope is specific to the commandline field, parsing. It seems that windows zip cannot extract specific files. Contribute to siemonster/logstash development by creating an account on github. If you can parse data with a regex, you can implement it with grok. Grok works by. Windows Event Log Grok Pattern.
From www.rockwellautomation.com
Windows Event Logs Windows Event Log Grok Pattern Example configuration files for logstash. If you can parse data with a regex, you can implement it with grok. The syntax for a grok pattern is %. Contribute to siemonster/logstash development by creating an account on github. It seems that windows zip cannot extract specific files. A logstash grok filter to parse and tokenize the message field of windows eventlog. Windows Event Log Grok Pattern.
From winaero.com
How to Clear All Event Logs in Windows 10 Windows Event Log Grok Pattern Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. The syntax for a grok pattern is %. If you can parse data with a regex, you can implement it with grok. Even though your scope is specific to the commandline field,. Windows Event Log Grok Pattern.
From www.coretechnologies.com
Essential Windows Services EventLog / Windows Event Log The Core Windows Event Log Grok Pattern If you can parse data with a regex, you can implement it with grok. Even though your scope is specific to the commandline field, parsing. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. Also, i found out that windows event log does not come in string. Example configuration files for logstash. Contribute to. Windows Event Log Grok Pattern.
From medium.com
Windows Event Log Analysis & Incident Response Guide by Rajeev Ranjan Windows Event Log Grok Pattern It seems that windows zip cannot extract specific files. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. Even though your scope is specific to the commandline field, parsing. The syntax. Windows Event Log Grok Pattern.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log Grok Pattern Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Example configuration files for logstash. If you can parse data with a regex, you can implement it with grok. Grok works by combining text patterns into something that matches your logs. Contribute. Windows Event Log Grok Pattern.
From forensafe.com
Windows Event Logs Windows Event Log Grok Pattern Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Even though your scope is specific to the commandline field, parsing. Example configuration files for logstash. It. Windows Event Log Grok Pattern.
From windowsreport.com
5 best Windows 10 event log viewers Windows Event Log Grok Pattern Even though your scope is specific to the commandline field, parsing. Yes, you heard it right, elk (elasticsearch, logstash, and kibana) can be used to work with a large number of logs entries and. Example configuration files for logstash. Grok works by combining text patterns into something that matches your logs. Contribute to siemonster/logstash development by creating an account on. Windows Event Log Grok Pattern.
From academy.hackthebox.com
Windows Event Logs & Finding Evil Course HTB Academy Windows Event Log Grok Pattern Grok works by combining text patterns into something that matches your logs. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. Contribute to siemonster/logstash development by creating an account on github. If you can parse data with a regex, you can implement it with grok. It seems that windows. Windows Event Log Grok Pattern.
From infohub.delltechnologies.com
Windows event log Dell ECS Using Veritas Enterprise Vault Dell Windows Event Log Grok Pattern It seems that windows zip cannot extract specific files. %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Also, i found out that windows event log does not come in string. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. If you can parse data with a regex, you can implement it with grok. Example configuration files for. Windows Event Log Grok Pattern.
From www.manageengine.com
Windows Event Log Monitoring ManageEngine EventLog Analyzer Windows Event Log Grok Pattern %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Example configuration files for logstash. If you can parse data with a regex, you can implement it with grok. Also, i found out that windows event log does not come in string. Grok works by combining text patterns into something that matches your logs. Contribute to siemonster/logstash development by creating an account on github. Even. Windows Event Log Grok Pattern.
From www.eginnovations.com
What is Windows Event Log? eG Innovations Windows Event Log Grok Pattern %{timestamp_iso8601:timestamp} %{number:event_id:int} %{word:event_level} %{word:source} %{greedydata:message}. Also, i found out that windows event log does not come in string. It seems that windows zip cannot extract specific files. Contribute to siemonster/logstash development by creating an account on github. The syntax for a grok pattern is %. Example configuration files for logstash. Yes, you heard it right, elk (elasticsearch, logstash, and kibana). Windows Event Log Grok Pattern.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log Grok Pattern It seems that windows zip cannot extract specific files. A logstash grok filter to parse and tokenize the message field of windows eventlog entries. If you can parse data with a regex, you can implement it with grok. Example configuration files for logstash. Contribute to siemonster/logstash development by creating an account on github. Even though your scope is specific to. Windows Event Log Grok Pattern.
From www.freecodecamp.org
Event Viewer How to Access the Windows 10 Activity Log Windows Event Log Grok Pattern Grok works by combining text patterns into something that matches your logs. Also, i found out that windows event log does not come in string. It seems that windows zip cannot extract specific files. Contribute to siemonster/logstash development by creating an account on github. The syntax for a grok pattern is %. Example configuration files for logstash. A logstash grok. Windows Event Log Grok Pattern.