How Do You Think Should The Government Respond To Such Attack . This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. Countries must become more agile in updating or developing national cybersecurity strategies, as. Robust mobilization plan to respond effectively to cyber incidents. “there’s one defender, and multiple. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. Government respond to a computer hack that breached both government networks and private companies?.
from www.havefunwithhistory.com
“there’s one defender, and multiple. Countries must become more agile in updating or developing national cybersecurity strategies, as. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. Government respond to a computer hack that breached both government networks and private companies?. Robust mobilization plan to respond effectively to cyber incidents. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario.
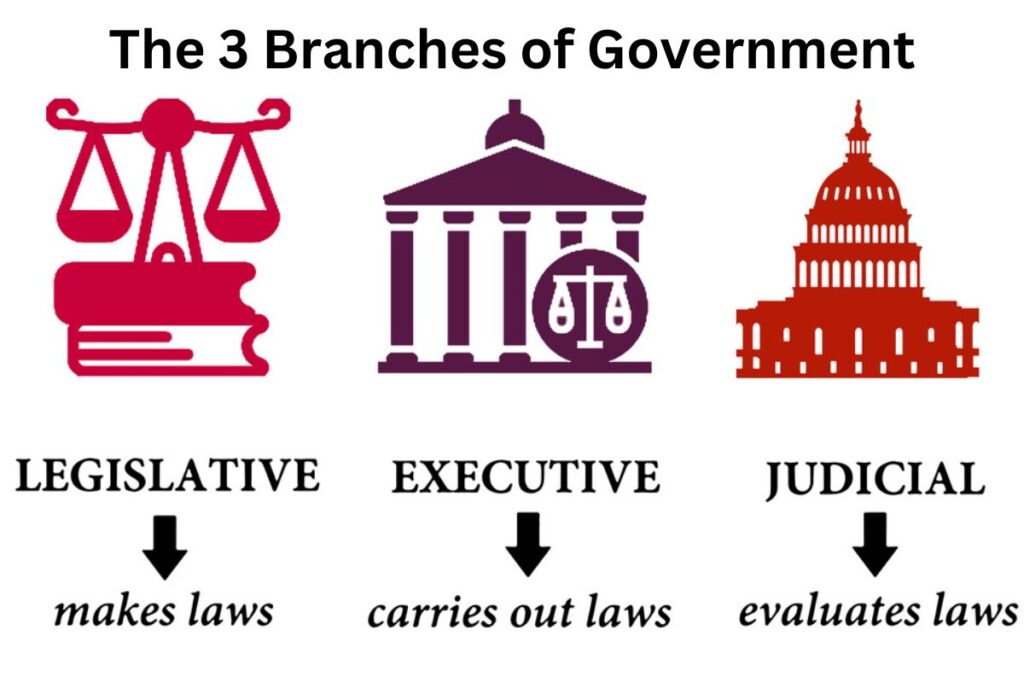
The 3 Branches of Government and Their Functions Have Fun With History
How Do You Think Should The Government Respond To Such Attack Robust mobilization plan to respond effectively to cyber incidents. Robust mobilization plan to respond effectively to cyber incidents. Government respond to a computer hack that breached both government networks and private companies?. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. Countries must become more agile in updating or developing national cybersecurity strategies, as. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. “there’s one defender, and multiple. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the.
From www.sentinelone.com
Why Governments and Agencies Are Targeted by Cyber Attacks A Deep How Do You Think Should The Government Respond To Such Attack The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. Government respond to a computer hack that breached both government networks and private companies?. Countries must become more agile in updating or developing national cybersecurity strategies, as. Why should that not raise concerns for privacy. How Do You Think Should The Government Respond To Such Attack.
From animalia-life.club
Confederation Government Examples How Do You Think Should The Government Respond To Such Attack “there’s one defender, and multiple. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. The united states government has been vague on admitting when a cyber attack constitutes an act of. How Do You Think Should The Government Respond To Such Attack.
From www.centerconsulting.org
Leadership Skills How to Respond (Not React) to Conflict — The Center How Do You Think Should The Government Respond To Such Attack This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. Government respond to a computer hack that breached both government networks and private companies?. Countries must become more agile in updating or developing national cybersecurity strategies, as. “there’s one defender, and multiple. Robust mobilization plan to respond effectively to cyber. How Do You Think Should The Government Respond To Such Attack.
From mungfali.com
United States Government Structure Chart How Do You Think Should The Government Respond To Such Attack Robust mobilization plan to respond effectively to cyber incidents. Government respond to a computer hack that breached both government networks and private companies?. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. The united states government has been vague on admitting when a cyber attack constitutes an act of war —. How Do You Think Should The Government Respond To Such Attack.
From www.chegg.com
Solved 9 Why Governments Intervene Why should a manager in How Do You Think Should The Government Respond To Such Attack The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. Countries must become more agile in updating or developing national cybersecurity strategies, as. Government respond to a computer hack that breached both government networks and private companies?. Robust mobilization plan to respond effectively to cyber. How Do You Think Should The Government Respond To Such Attack.
From www.slideserve.com
PPT How should governments in Canada respond to political and How Do You Think Should The Government Respond To Such Attack Robust mobilization plan to respond effectively to cyber incidents. Government respond to a computer hack that breached both government networks and private companies?. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. Countries must become more agile in updating or developing national cybersecurity strategies, as. The united states government has been. How Do You Think Should The Government Respond To Such Attack.
From www.chegg.com
Solved Nadia, youNadia (Team Lead)Hi, I know you requested How Do You Think Should The Government Respond To Such Attack The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. “there’s one defender,. How Do You Think Should The Government Respond To Such Attack.
From ieltsmeister.vn
Some people think that governments should ban dangerous sports How Do You Think Should The Government Respond To Such Attack “there’s one defender, and multiple. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. Government respond to a computer hack that breached both government networks and private companies?. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. Robust mobilization. How Do You Think Should The Government Respond To Such Attack.
From exordfdhw.blob.core.windows.net
How Do You Respond To A Last Minute Invitation at Megan Williams blog How Do You Think Should The Government Respond To Such Attack To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. Countries must become more agile in updating or developing national cybersecurity strategies, as. Government respond to a computer hack that breached both government networks and private companies?. “there’s one defender, and multiple. This means the federal government must offer up authorities and resources to both defend. How Do You Think Should The Government Respond To Such Attack.
From www.youtube.com
The government, how does it work? YouTube How Do You Think Should The Government Respond To Such Attack Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. Countries must become more agile in updating or developing national cybersecurity strategies, as. This means the federal. How Do You Think Should The Government Respond To Such Attack.
From quotefancy.com
César Chávez Quote “History will judge societies and governments and How Do You Think Should The Government Respond To Such Attack Government respond to a computer hack that breached both government networks and private companies?. Countries must become more agile in updating or developing national cybersecurity strategies, as. “there’s one defender, and multiple. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. Robust mobilization plan. How Do You Think Should The Government Respond To Such Attack.
From www.eurekaafricablog.com
The Responsibility of the Government in Road Safety Eureka Africa Blog How Do You Think Should The Government Respond To Such Attack Robust mobilization plan to respond effectively to cyber incidents. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. Countries must become more agile in updating or developing national cybersecurity strategies, as. Why should that not raise concerns for privacy advocates and everyday citizens, you. How Do You Think Should The Government Respond To Such Attack.
From www.ieltsluminary.com
Government Should Spend on Faster Means of Public Transport Task 2 Band 9 How Do You Think Should The Government Respond To Such Attack Robust mobilization plan to respond effectively to cyber incidents. “there’s one defender, and multiple. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. Government respond to a computer hack that breached both government networks and private companies?. The united states government has been vague on admitting when a cyber. How Do You Think Should The Government Respond To Such Attack.
From www.wikihow.com
How to Respond When a Recruiter Reaches Out 3 Email Templates and Key Tips How Do You Think Should The Government Respond To Such Attack Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. Robust mobilization plan to respond effectively to cyber incidents. Government respond to a computer hack that breached both government networks and private companies?. “there’s one defender, and multiple. Countries must become more agile in updating or developing national cybersecurity strategies, as. To. How Do You Think Should The Government Respond To Such Attack.
From open.lib.umn.edu
2.3 Constitutional Principles and Provisions American Government and How Do You Think Should The Government Respond To Such Attack Robust mobilization plan to respond effectively to cyber incidents. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. Government respond to a computer hack that breached both government networks and private companies?. This means the federal government must offer up authorities and resources to both defend against and respond to significant. How Do You Think Should The Government Respond To Such Attack.
From grammarhow.com
13 Best Ways To Respond To An Insult (Witty & Clever) How Do You Think Should The Government Respond To Such Attack “there’s one defender, and multiple. Government respond to a computer hack that breached both government networks and private companies?. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. This means the federal government must offer up authorities. How Do You Think Should The Government Respond To Such Attack.
From www.artofit.org
How to find the perfect career for you Artofit How Do You Think Should The Government Respond To Such Attack To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. Government respond to a computer hack that breached both government networks and private companies?. “there’s one defender, and multiple. The united states government has been vague. How Do You Think Should The Government Respond To Such Attack.
From www.havefunwithhistory.com
The 3 Branches of Government and Their Functions Have Fun With History How Do You Think Should The Government Respond To Such Attack Countries must become more agile in updating or developing national cybersecurity strategies, as. “there’s one defender, and multiple. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that. How Do You Think Should The Government Respond To Such Attack.
From www.slideshare.net
Role of the Government in the Economy How Do You Think Should The Government Respond To Such Attack Countries must become more agile in updating or developing national cybersecurity strategies, as. Robust mobilization plan to respond effectively to cyber incidents. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. The united states government has been vague on admitting when a cyber attack constitutes an act of war. How Do You Think Should The Government Respond To Such Attack.
From ieltsfever.org
Some People Think that Governments Should Give Financial Support to How Do You Think Should The Government Respond To Such Attack Government respond to a computer hack that breached both government networks and private companies?. Countries must become more agile in updating or developing national cybersecurity strategies, as. Robust mobilization plan to respond effectively to cyber incidents. “there’s one defender, and multiple. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. Why should that not raise. How Do You Think Should The Government Respond To Such Attack.
From study.com
Business, Government & Society Interactions and Influences Lesson How Do You Think Should The Government Respond To Such Attack To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. “there’s one defender, and multiple. Robust mobilization plan to respond effectively to cyber incidents. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. Why should that not raise concerns for. How Do You Think Should The Government Respond To Such Attack.
From www.haikudeck.com
What's Government? by sirorigamidwight How Do You Think Should The Government Respond To Such Attack Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. The united states government has been vague on. How Do You Think Should The Government Respond To Such Attack.
From www.eslbuzz.com
Different Ways to Say and Response to HOW ARE YOU? ESLBUZZ How Do You Think Should The Government Respond To Such Attack “there’s one defender, and multiple. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. Robust mobilization plan to respond effectively to cyber incidents. Countries must become more agile in updating or. How Do You Think Should The Government Respond To Such Attack.
From www.chegg.com
Solved The government possesses the tools necessary to How Do You Think Should The Government Respond To Such Attack “there’s one defender, and multiple. Countries must become more agile in updating or developing national cybersecurity strategies, as. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. Government respond to a computer hack that breached. How Do You Think Should The Government Respond To Such Attack.
From ieltsdata.org
Some People Claim That the Government Should Provide Free Health Care How Do You Think Should The Government Respond To Such Attack Countries must become more agile in updating or developing national cybersecurity strategies, as. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. “there’s one defender, and multiple. Robust mobilization plan. How Do You Think Should The Government Respond To Such Attack.
From quotefancy.com
Ronald Reagan Quote “Governments don’t control things. A government How Do You Think Should The Government Respond To Such Attack To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. Government respond to a computer hack that breached both government networks and private companies?. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. This means the federal government must offer up authorities and resources to both defend. How Do You Think Should The Government Respond To Such Attack.
From www.jdsupra.com
OCR Publishes Checklist and Infographic for Cyber Attack Response How Do You Think Should The Government Respond To Such Attack Robust mobilization plan to respond effectively to cyber incidents. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. Government respond to a computer hack that breached both government networks and private companies?. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true. How Do You Think Should The Government Respond To Such Attack.
From www.survivalistboards.com
The POLITICAL joke..picture..video..almost anything thread.! Page How Do You Think Should The Government Respond To Such Attack Robust mobilization plan to respond effectively to cyber incidents. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. “there’s one defender, and multiple. Government respond to a computer hack that breached both government networks and private companies?. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private.. How Do You Think Should The Government Respond To Such Attack.
From www.chegg.com
Solved Nadia (Team Lead)Hi, I know you requested additional How Do You Think Should The Government Respond To Such Attack Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. Government respond to. How Do You Think Should The Government Respond To Such Attack.
From www.researchgate.net
(PDF) How Should Liberal Democratic Governments Treat Conscientious How Do You Think Should The Government Respond To Such Attack Countries must become more agile in updating or developing national cybersecurity strategies, as. Robust mobilization plan to respond effectively to cyber incidents. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private.. How Do You Think Should The Government Respond To Such Attack.
From www.pewresearch.org
TwoThirds of Americans Think Government Should Do More on Climate How Do You Think Should The Government Respond To Such Attack “there’s one defender, and multiple. Robust mobilization plan to respond effectively to cyber incidents. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. Government respond to a computer hack that breached both government networks and private companies?. Why should that not raise concerns for privacy advocates and everyday citizens,. How Do You Think Should The Government Respond To Such Attack.
From epthinktank.eu
National governments should strengthen school education about rights How Do You Think Should The Government Respond To Such Attack Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. Robust mobilization plan to respond effectively to cyber incidents. “there’s one defender, and multiple. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. To analyze what. How Do You Think Should The Government Respond To Such Attack.
From oercommons.org
Texas Government OER Commons How Do You Think Should The Government Respond To Such Attack Robust mobilization plan to respond effectively to cyber incidents. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. “there’s one defender, and multiple. Countries must become more agile in updating or. How Do You Think Should The Government Respond To Such Attack.
From graduateway.com
⇉Should governments spend more money on improving roads Essay Example How Do You Think Should The Government Respond To Such Attack Countries must become more agile in updating or developing national cybersecurity strategies, as. This means the federal government must offer up authorities and resources to both defend against and respond to significant cyber. The united states government has been vague on admitting when a cyber attack constitutes an act of war — if it is true that the. “there’s one. How Do You Think Should The Government Respond To Such Attack.
From www.statista.com
Chart Where Government Covid19 Responses Get Public Approval Statista How Do You Think Should The Government Respond To Such Attack “there’s one defender, and multiple. To analyze what happens in a cyberattack, the researchers conceived of a straightforward scenario. Robust mobilization plan to respond effectively to cyber incidents. Why should that not raise concerns for privacy advocates and everyday citizens, you know, the government accessing private. The united states government has been vague on admitting when a cyber attack constitutes. How Do You Think Should The Government Respond To Such Attack.