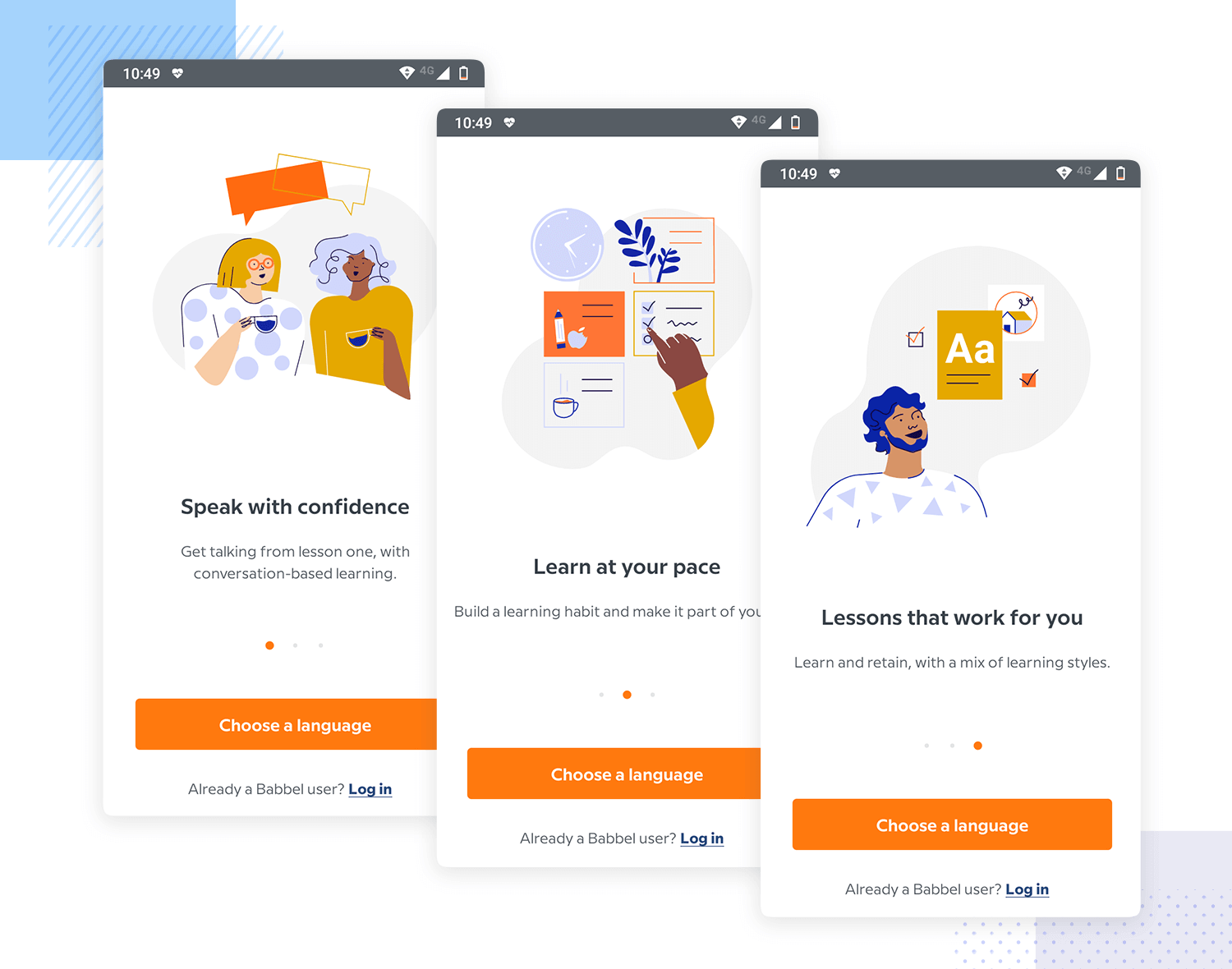
User Login Best Practices . This is usually a username and. Then, we’ll share a login screen example for each to help you get a better understanding of what. This is where it all begins. Share how and why you use and collect data. One tip to get users to embrace extra steps in protecting their identities is to. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. Users must first provide their login credentials for the information they want to access. Learn essential authentication best practices, including securing login processes, password. Protect your web application and authentication server with expert guidance. In this guide, we’ll share ten practices to make any login screens you create shine.
from www.justinmind.com
One tip to get users to embrace extra steps in protecting their identities is to. Protect your web application and authentication server with expert guidance. Then, we’ll share a login screen example for each to help you get a better understanding of what. This is where it all begins. Share how and why you use and collect data. In this guide, we’ll share ten practices to make any login screens you create shine. This is usually a username and. Learn essential authentication best practices, including securing login processes, password. Users must first provide their login credentials for the information they want to access. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with.
User onboarding 11 best practices and 15 examples Justinmind
User Login Best Practices Then, we’ll share a login screen example for each to help you get a better understanding of what. Then, we’ll share a login screen example for each to help you get a better understanding of what. Share how and why you use and collect data. Learn essential authentication best practices, including securing login processes, password. This is where it all begins. Protect your web application and authentication server with expert guidance. This is usually a username and. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. In this guide, we’ll share ten practices to make any login screens you create shine. One tip to get users to embrace extra steps in protecting their identities is to. Users must first provide their login credentials for the information they want to access.
From www.mockplus.com
16 Simplistic Signup/Login Best Practices Every App Developer Need to Know User Login Best Practices Share how and why you use and collect data. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. Learn essential authentication best practices, including securing login processes, password. Users must first provide their login credentials for the information they want to access. This is usually a. User Login Best Practices.
From www.vrogue.co
Beautiful Html Css Login Form Tutorial Login Form In vrogue.co User Login Best Practices This is where it all begins. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. Then, we’ll share a login screen example for each to help you get a better understanding of what. Share how and why you use and collect data. This is usually a. User Login Best Practices.
From www.vrogue.co
17 Best Login Page Design Examples And Best Practices vrogue.co User Login Best Practices This is usually a username and. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. This is where it all begins. One tip to get users to embrace extra steps in protecting their identities is to. Learn essential authentication best practices, including securing login processes, password.. User Login Best Practices.
From www.mockplus.com
16 Simplistic Signup/Login Best Practices Every App Developer Need to Know User Login Best Practices This is where it all begins. One tip to get users to embrace extra steps in protecting their identities is to. Learn essential authentication best practices, including securing login processes, password. This is usually a username and. Users must first provide their login credentials for the information they want to access. Protect your web application and authentication server with expert. User Login Best Practices.
From kanzaakhwand.com
Simplistic Signup/Login Best Practices Every App Team Needs To Know User Login Best Practices Learn essential authentication best practices, including securing login processes, password. One tip to get users to embrace extra steps in protecting their identities is to. Share how and why you use and collect data. Then, we’ll share a login screen example for each to help you get a better understanding of what. Whether you're responsible for a website hosted in. User Login Best Practices.
From gopius.com
Hawkit Login Best Practices For User Experience User Login Best Practices One tip to get users to embrace extra steps in protecting their identities is to. Users must first provide their login credentials for the information they want to access. In this guide, we’ll share ten practices to make any login screens you create shine. Protect your web application and authentication server with expert guidance. Share how and why you use. User Login Best Practices.
From www.mockplus.com
16 Simplistic Signup/Login Best Practices Every App Developer Need to Know User Login Best Practices This is usually a username and. In this guide, we’ll share ten practices to make any login screens you create shine. Share how and why you use and collect data. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. Then, we’ll share a login screen example. User Login Best Practices.
From www.briefcasecoach.com
LinkedIn Best Practices Briefcase Coach User Login Best Practices Users must first provide their login credentials for the information they want to access. This is where it all begins. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. This is usually a username and. One tip to get users to embrace extra steps in protecting. User Login Best Practices.
From playsquare.tv
ux login best practice playsquare.tv User Login Best Practices In this guide, we’ll share ten practices to make any login screens you create shine. This is usually a username and. This is where it all begins. Users must first provide their login credentials for the information they want to access. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase,. User Login Best Practices.
From www.slideserve.com
PPT Intuitpayrolllogin PowerPoint Presentation, free download ID User Login Best Practices In this guide, we’ll share ten practices to make any login screens you create shine. Users must first provide their login credentials for the information they want to access. This is usually a username and. One tip to get users to embrace extra steps in protecting their identities is to. Whether you're responsible for a website hosted in google kubernetes. User Login Best Practices.
From developer.taptap.cn
Best TapTap Login Practices TapTap 开发者文档 User Login Best Practices Protect your web application and authentication server with expert guidance. Users must first provide their login credentials for the information they want to access. This is where it all begins. This is usually a username and. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. Share. User Login Best Practices.
From institute.careerguide.com
EEDS Login StepbyGuide, Troubleshooting, Optimizing Security User Login Best Practices Learn essential authentication best practices, including securing login processes, password. In this guide, we’ll share ten practices to make any login screens you create shine. Protect your web application and authentication server with expert guidance. Then, we’ll share a login screen example for each to help you get a better understanding of what. One tip to get users to embrace. User Login Best Practices.
From userpilot.com
12 Client Onboarding Best Practices to Increase User Activation User Login Best Practices This is usually a username and. Learn essential authentication best practices, including securing login processes, password. Share how and why you use and collect data. One tip to get users to embrace extra steps in protecting their identities is to. This is where it all begins. Whether you're responsible for a website hosted in google kubernetes engine, an api on. User Login Best Practices.
From www.growthmachine.com
5 Design Best Practices for Better User Experience User Login Best Practices In this guide, we’ll share ten practices to make any login screens you create shine. Learn essential authentication best practices, including securing login processes, password. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. Then, we’ll share a login screen example for each to help you. User Login Best Practices.
From www.voiceandcode.com
UX Best Practices Form Design — Voice+Code User Login Best Practices Users must first provide their login credentials for the information they want to access. This is where it all begins. Share how and why you use and collect data. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. In this guide, we’ll share ten practices to. User Login Best Practices.
From www.mockplus.com
16 Simplistic Signup/Login Best Practices Every App Developer Need to Know User Login Best Practices Protect your web application and authentication server with expert guidance. In this guide, we’ll share ten practices to make any login screens you create shine. This is where it all begins. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. Then, we’ll share a login screen. User Login Best Practices.
From support.absorblms.com
User Management Absorb Help Center User Login Best Practices This is where it all begins. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. Users must first provide their login credentials for the information they want to access. Then, we’ll share a login screen example for each to help you get a better understanding of. User Login Best Practices.
From webtips.dev
Best Practices for Responsive User Interfaces Using CSS tips User Login Best Practices This is where it all begins. Learn essential authentication best practices, including securing login processes, password. In this guide, we’ll share ten practices to make any login screens you create shine. Protect your web application and authentication server with expert guidance. Share how and why you use and collect data. Whether you're responsible for a website hosted in google kubernetes. User Login Best Practices.
From www.mockplus.com
16 Simplistic Signup/Login Best Practices Every App Developer Need to Know User Login Best Practices In this guide, we’ll share ten practices to make any login screens you create shine. Share how and why you use and collect data. Protect your web application and authentication server with expert guidance. Learn essential authentication best practices, including securing login processes, password. Users must first provide their login credentials for the information they want to access. Then, we’ll. User Login Best Practices.
From www.freepik.com
Login ui Vectors & Illustrations for Free Download Freepik User Login Best Practices Learn essential authentication best practices, including securing login processes, password. Share how and why you use and collect data. Protect your web application and authentication server with expert guidance. Then, we’ll share a login screen example for each to help you get a better understanding of what. This is usually a username and. One tip to get users to embrace. User Login Best Practices.
From www.mockplus.com
16 Simplistic Signup/Login Best Practices Every App Developer Need to Know User Login Best Practices This is usually a username and. Then, we’ll share a login screen example for each to help you get a better understanding of what. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. This is where it all begins. In this guide, we’ll share ten practices. User Login Best Practices.
From reactnativetips.com
Master React Native Login Screens Security & UX Best Practices User Login Best Practices This is usually a username and. One tip to get users to embrace extra steps in protecting their identities is to. This is where it all begins. Learn essential authentication best practices, including securing login processes, password. In this guide, we’ll share ten practices to make any login screens you create shine. Whether you're responsible for a website hosted in. User Login Best Practices.
From medium.com
Best Practices while designing User Interface with images. Tips to help User Login Best Practices This is usually a username and. Users must first provide their login credentials for the information they want to access. Share how and why you use and collect data. Protect your web application and authentication server with expert guidance. This is where it all begins. Learn essential authentication best practices, including securing login processes, password. Whether you're responsible for a. User Login Best Practices.
From hype4.academy
Minimal Login Form UI Design Guide Hype4Academy User Login Best Practices Users must first provide their login credentials for the information they want to access. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. Learn essential authentication best practices, including securing login processes, password. Share how and why you use and collect data. Then, we’ll share a. User Login Best Practices.
From store.magenest.com
Top 6 Social Login best practices for in 2024 User Login Best Practices Then, we’ll share a login screen example for each to help you get a better understanding of what. This is usually a username and. Protect your web application and authentication server with expert guidance. Users must first provide their login credentials for the information they want to access. Share how and why you use and collect data. This is where. User Login Best Practices.
From www.mockplus.com
16 Simplistic Signup/Login Best Practices Every App Developer Need to Know User Login Best Practices Then, we’ll share a login screen example for each to help you get a better understanding of what. In this guide, we’ll share ten practices to make any login screens you create shine. This is where it all begins. This is usually a username and. Learn essential authentication best practices, including securing login processes, password. Protect your web application and. User Login Best Practices.
From emergetech.com
NetSuite Login 6 MustHave Login Best Practices in 2020 User Login Best Practices One tip to get users to embrace extra steps in protecting their identities is to. Then, we’ll share a login screen example for each to help you get a better understanding of what. Users must first provide their login credentials for the information they want to access. In this guide, we’ll share ten practices to make any login screens you. User Login Best Practices.
From www.mockplus.com
16 Simplistic Signup/Login Best Practices Every App Developer Need to Know User Login Best Practices Protect your web application and authentication server with expert guidance. Learn essential authentication best practices, including securing login processes, password. This is usually a username and. Then, we’ll share a login screen example for each to help you get a better understanding of what. This is where it all begins. Share how and why you use and collect data. Users. User Login Best Practices.
From www.mockplus.com
16 Simplistic Signup/Login Best Practices Every App Developer Need to Know User Login Best Practices Learn essential authentication best practices, including securing login processes, password. This is usually a username and. Users must first provide their login credentials for the information they want to access. Protect your web application and authentication server with expert guidance. Then, we’ll share a login screen example for each to help you get a better understanding of what. Share how. User Login Best Practices.
From www.justinmind.com
User onboarding 11 best practices and 15 examples Justinmind User Login Best Practices Learn essential authentication best practices, including securing login processes, password. Share how and why you use and collect data. In this guide, we’ll share ten practices to make any login screens you create shine. Protect your web application and authentication server with expert guidance. Then, we’ll share a login screen example for each to help you get a better understanding. User Login Best Practices.
From forums.ivanti.com
Administrator Login Best Practices User Login Best Practices This is usually a username and. Learn essential authentication best practices, including securing login processes, password. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. Share how and why you use and collect data. In this guide, we’ll share ten practices to make any login screens. User Login Best Practices.
From www.paidmembershipspro.com
Login Best Practices Improve Membership Site Log In and Log Out User Login Best Practices Share how and why you use and collect data. This is where it all begins. One tip to get users to embrace extra steps in protecting their identities is to. This is usually a username and. In this guide, we’ll share ten practices to make any login screens you create shine. Learn essential authentication best practices, including securing login processes,. User Login Best Practices.
From digitaltemplatemarket.com
15 Best Free HTML5 Login Form Templates 2024 DigitalTemplateMarket User Login Best Practices Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. In this guide, we’ll share ten practices to make any login screens you create shine. This is usually a username and. Users must first provide their login credentials for the information they want to access. Protect your. User Login Best Practices.
From www.mockplus.com
16 Simplistic Signup/Login Best Practices Every App Developer Need to Know User Login Best Practices Then, we’ll share a login screen example for each to help you get a better understanding of what. Whether you're responsible for a website hosted in google kubernetes engine, an api on apigee, an app using firebase, or other service with. In this guide, we’ll share ten practices to make any login screens you create shine. Learn essential authentication best. User Login Best Practices.
From pixelsweb.design
Mastering The Art Of WordPress LoginBest Practices And Tips User Login Best Practices Share how and why you use and collect data. This is usually a username and. In this guide, we’ll share ten practices to make any login screens you create shine. One tip to get users to embrace extra steps in protecting their identities is to. Users must first provide their login credentials for the information they want to access. This. User Login Best Practices.