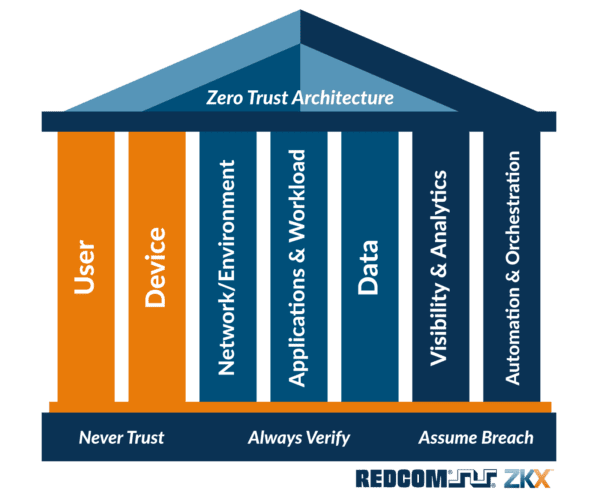
Pillars Of Zta . A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. How to implement zero trust architecture. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. Learn how forrester's zero trust extended framework can help it leaders identify, organize and. What are the seven core pillars of zero trust architecture? The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. Key feature of the model is that it focuses attention on five pillars: Zta involves presuming that every entity trying to connect to a network or application is a threat. Identity (“an attribute or set of attributes that uniquely. In the context of cybersecurity in 2024, zta.
from www.redcom.com
6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. Zta involves presuming that every entity trying to connect to a network or application is a threat. A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. Key feature of the model is that it focuses attention on five pillars: What are the seven core pillars of zero trust architecture? Identity (“an attribute or set of attributes that uniquely. In the context of cybersecurity in 2024, zta. How to implement zero trust architecture. Learn how forrester's zero trust extended framework can help it leaders identify, organize and. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be.
Identity and Authentication the most important pillars in a Zero Trust
Pillars Of Zta The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. Zta involves presuming that every entity trying to connect to a network or application is a threat. Learn how forrester's zero trust extended framework can help it leaders identify, organize and. In the context of cybersecurity in 2024, zta. Key feature of the model is that it focuses attention on five pillars: Identity (“an attribute or set of attributes that uniquely. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. What are the seven core pillars of zero trust architecture? How to implement zero trust architecture.
From www.zeta.tech
Revolutionizing Banking Security With Zero Trust Architecture Zeta US Pillars Of Zta Learn how forrester's zero trust extended framework can help it leaders identify, organize and. Zta involves presuming that every entity trying to connect to a network or application is a threat. What are the seven core pillars of zero trust architecture? Key feature of the model is that it focuses attention on five pillars: The ztmm represents a gradient of. Pillars Of Zta.
From pixelplex.io
How to Implement Zero Trust Architecture in 5 Steps [Checklist] Pillars Of Zta 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. Zta involves presuming that every entity trying to connect to a network or application is a threat. Identity (“an attribute or set. Pillars Of Zta.
From www.vrogue.co
What Is Zero Trust Architecture Zta F5 Labs vrogue.co Pillars Of Zta In the context of cybersecurity in 2024, zta. How to implement zero trust architecture. Key feature of the model is that it focuses attention on five pillars: Learn how forrester's zero trust extended framework can help it leaders identify, organize and. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications. Pillars Of Zta.
From dzone.com
Implementing Zero Trust Architecture on Azure Hybrid Cloud DZone Pillars Of Zta A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. What are the seven core pillars of zero trust architecture? Learn how forrester's zero trust extended framework can help it leaders identify, organize and. Identity (“an. Pillars Of Zta.
From wilderbaqueconsuegra.blogspot.com
Organismos de organización internacionales y nacionales de Pillars Of Zta Learn how forrester's zero trust extended framework can help it leaders identify, organize and. Identity (“an attribute or set of attributes that uniquely. Zta involves presuming that every entity trying to connect to a network or application is a threat. What are the seven core pillars of zero trust architecture? A zero trust architecture (zta) uses zero trust principles to. Pillars Of Zta.
From resilientcyber.substack.com
A look at the DoD's Zero Trust Strategy by Chris Hughes Pillars Of Zta Identity (“an attribute or set of attributes that uniquely. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. What are the seven core pillars of zero trust architecture? Key feature of the model is that it focuses attention on five pillars: Zta involves presuming that every entity trying. Pillars Of Zta.
From www.linkedin.com
Enhancing Zero Trust Security ZTAThe Device Pillar. Pillars Of Zta Key feature of the model is that it focuses attention on five pillars: How to implement zero trust architecture. Identity (“an attribute or set of attributes that uniquely. Learn how forrester's zero trust extended framework can help it leaders identify, organize and. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks,. Pillars Of Zta.
From zkxsolutions.com
The user and the device the two most critical pillars of a Zero Trust Pillars Of Zta 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. Key feature of the model is that it focuses attention on five pillars: Identity (“an attribute or set of attributes that uniquely. What are the seven core pillars of zero trust architecture? A zero trust architecture (zta) uses zero. Pillars Of Zta.
From www.researchgate.net
The fracture mechanism of a ZTA and b GOZTA Download Scientific Diagram Pillars Of Zta Key feature of the model is that it focuses attention on five pillars: Learn how forrester's zero trust extended framework can help it leaders identify, organize and. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. How to implement zero trust architecture. What are the seven core pillars of zero trust architecture?. Pillars Of Zta.
From emergewomanmagazine.com
Exploring the Five Pillars of ZTA Sisterhood A Comprehensive Guide Pillars Of Zta Learn how forrester's zero trust extended framework can help it leaders identify, organize and. Zta involves presuming that every entity trying to connect to a network or application is a threat. Identity (“an attribute or set of attributes that uniquely. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and. Pillars Of Zta.
From blog.securesky.com
Zero Trust Maturity Model (ZTMM 2.0) A Transition to ZTA Pillars Of Zta How to implement zero trust architecture. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. Identity (“an attribute or set of attributes that uniquely. What are the seven core pillars of. Pillars Of Zta.
From www.redcom.com
Identity and Authentication the most important pillars in a Zero Trust Pillars Of Zta The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. Learn how forrester's zero trust extended framework can help it leaders identify, organize and. In the context of cybersecurity in 2024, zta. Identity (“an attribute or. Pillars Of Zta.
From www.vrogue.co
Zero Trust Architecture Zta vrogue.co Pillars Of Zta Learn how forrester's zero trust extended framework can help it leaders identify, organize and. How to implement zero trust architecture. A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. In the context of cybersecurity in 2024, zta. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements. Pillars Of Zta.
From www.nextlabs.com
Zero Trust Architecture (ZTA) NextLabs Pillars Of Zta 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. Zta involves presuming that every entity trying to connect to a network or application is a threat. How to implement zero trust architecture. Key feature of the model is that it focuses attention on five pillars: The ztmm represents. Pillars Of Zta.
From www.f5.com
What Is Zero Trust Architecture (ZTA)? F5 Labs Pillars Of Zta What are the seven core pillars of zero trust architecture? A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. Learn how forrester's zero trust extended framework can help it leaders identify,. Pillars Of Zta.
From dribbble.com
7 Pillars of ZeroTrust Architecture (ZTA) by CloudStakes Technology Pillars Of Zta Key feature of the model is that it focuses attention on five pillars: 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. In the context of cybersecurity in 2024, zta. What are the seven core pillars of zero trust architecture? A zero trust architecture (zta) uses zero trust. Pillars Of Zta.
From www.mdpi.com
Electronics Free FullText Metaverse Security Issues, Challenges Pillars Of Zta The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. Key feature of the model is that it focuses attention on five pillars: Identity (“an attribute or set of attributes that uniquely. Zta involves presuming that every entity trying to connect to a network or application is a threat. How to implement zero. Pillars Of Zta.
From blog.barracuda.com
The Zero Trust Maturity Model Pillars Of Zta Identity (“an attribute or set of attributes that uniquely. How to implement zero trust architecture. In the context of cybersecurity in 2024, zta. What are the seven core pillars of zero trust architecture? Zta involves presuming that every entity trying to connect to a network or application is a threat. 6.2 pillars of zta the five (5) pillars of the. Pillars Of Zta.
From resilientcyber.substack.com
A look at the DoD's Zero Trust Strategy by Chris Hughes Pillars Of Zta What are the seven core pillars of zero trust architecture? The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. In the context of cybersecurity in 2024, zta. Learn how forrester's zero trust extended framework can help it leaders identify, organize and. Identity (“an attribute or set of attributes that uniquely. Zta involves. Pillars Of Zta.
From www.reddit.com
This particular shot of Zeta Halo reminded of Asgard in the Marvel Pillars Of Zta Zta involves presuming that every entity trying to connect to a network or application is a threat. A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. What are the seven core pillars of zero trust. Pillars Of Zta.
From www.collidu.com
HR (Human Resources) Pillars PowerPoint and Google Slides Template Pillars Of Zta Learn how forrester's zero trust extended framework can help it leaders identify, organize and. What are the seven core pillars of zero trust architecture? Key feature of the model is that it focuses attention on five pillars: Zta involves presuming that every entity trying to connect to a network or application is a threat. 6.2 pillars of zta the five. Pillars Of Zta.
From shorepointinc.com
ShorePoint’s Innovative ZTA Framework and Agile Implementation Pillars Of Zta The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. Zta involves presuming that every entity trying to connect to a network or application is a threat. A zero trust architecture (zta). Pillars Of Zta.
From www.gcst.ae
Defining Zero Trust in the Wake of the Biden Administration’s Pillars Of Zta What are the seven core pillars of zero trust architecture? In the context of cybersecurity in 2024, zta. How to implement zero trust architecture. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. Learn how forrester's zero trust extended framework can help it leaders identify, organize and. A. Pillars Of Zta.
From www.nextlabs.com
Zero Trust Architecture (ZTA) NextLabs Pillars Of Zta In the context of cybersecurity in 2024, zta. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. Identity (“an attribute or set of attributes that uniquely. Learn how forrester's zero trust extended framework can help it leaders identify, organize and. Key feature of the model is that it focuses attention on five. Pillars Of Zta.
From www.researchgate.net
The fracture surface of a ZTA and b GOZTA parts Download Scientific Pillars Of Zta What are the seven core pillars of zero trust architecture? In the context of cybersecurity in 2024, zta. A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. The ztmm represents a. Pillars Of Zta.
From humanize.security
7 Pillars of ZeroTrust Architecture Blog Humanize Pillars Of Zta Zta involves presuming that every entity trying to connect to a network or application is a threat. Key feature of the model is that it focuses attention on five pillars: The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. What are the seven core pillars of zero trust architecture? Learn how forrester's. Pillars Of Zta.
From tamikaamayneso.blob.core.windows.net
Pillars Of Zero Trust at tamikaamayneso blog Pillars Of Zta In the context of cybersecurity in 2024, zta. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. Zta involves presuming that every entity trying to connect to a network or application. Pillars Of Zta.
From stratuscyber.com
Zero Trust is not a destination; it’s a complex journey Stratus Cyber Pillars Of Zta Zta involves presuming that every entity trying to connect to a network or application is a threat. Key feature of the model is that it focuses attention on five pillars: 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. The ztmm represents a gradient of implementation across five. Pillars Of Zta.
From www.ivoxy.com
Five Pillars of Zero Trust IVOXY Consulting Pillars Of Zta Zta involves presuming that every entity trying to connect to a network or application is a threat. Learn how forrester's zero trust extended framework can help it leaders identify, organize and. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. How to implement zero trust architecture. A zero trust architecture (zta) uses. Pillars Of Zta.
From er.educause.edu
Zero Trust Architecture Rethinking Cybersecurity for Changing Pillars Of Zta The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. What are the seven core pillars of zero trust architecture? Identity (“an attribute or set of attributes that uniquely. Zta involves presuming that every entity trying to connect to a network or application is a threat. Key feature of the model is that. Pillars Of Zta.
From www.linkedin.com
Zero Trust Security Understanding the Network Pillar of ZTA Pillars Of Zta In the context of cybersecurity in 2024, zta. How to implement zero trust architecture. Zta involves presuming that every entity trying to connect to a network or application is a threat. Identity (“an attribute or set of attributes that uniquely. Key feature of the model is that it focuses attention on five pillars: What are the seven core pillars of. Pillars Of Zta.
From www.csis.org
“Never Trust, Always Verify” Federal Migration to ZTA and Endpoint Pillars Of Zta How to implement zero trust architecture. The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. Identity (“an attribute or set of attributes that uniquely. In the context of cybersecurity in 2024, zta. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and. Pillars Of Zta.
From questsys.com
Why You Need 6 Layers of ZeroTrust Control Pillars Of Zta A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. 6.2 pillars of zta the five (5) pillars of the zero trust maturity model are identity, devices, networks, applications and workloads,. Learn how forrester's zero trust extended framework can help it leaders identify, organize and. The ztmm represents a gradient of implementation across. Pillars Of Zta.
From dribbble.com
7 Pillars of ZeroTrust Architecture (ZTA) by CloudStakes Technology Pillars Of Zta The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. Zta involves presuming that every entity trying to connect to a network or application is a threat. How to implement zero trust architecture. What are the. Pillars Of Zta.
From www.cimcor.com
The Comprehensive Guide to Zero Trust Architecture Pillars Of Zta The ztmm represents a gradient of implementation across five distinct pillars, in which minor advancements can be. A zero trust architecture (zta) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. How to implement zero trust architecture. What are the seven core pillars of zero trust architecture? Key feature of the model is that it focuses attention. Pillars Of Zta.