How To Use Traffic Light Protocol . The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. Tlp is a set of designations used to ensure that. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for.
from insightforfuture.blogspot.com
The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. Tlp is a set of designations used to ensure that. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information.
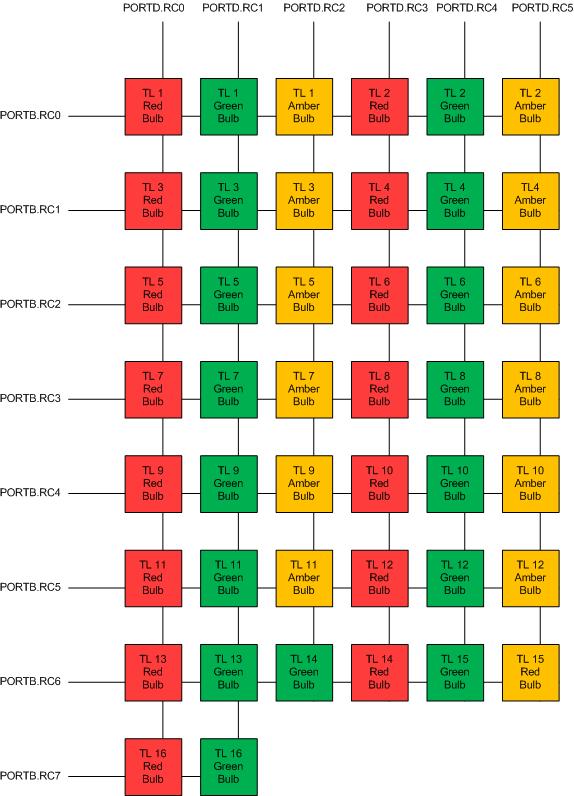
Insight 8*6 LED Matrix for Intelligent Traffic Light System
How To Use Traffic Light Protocol Tlp is a set of designations used to ensure that. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. Tlp is a set of designations used to ensure that. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information.
From blog.apnic.net
Enhancing Traffic Light Protocol with IEP APNIC Blog How To Use Traffic Light Protocol The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. At the 28th annual conference and agm. How To Use Traffic Light Protocol.
From www.vrogue.co
The New And Improved Traffic Light Protocol 2 0 In Cy vrogue.co How To Use Traffic Light Protocol The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. At the 28th annual conference and agm. How To Use Traffic Light Protocol.
From www.connecthealth.co.uk
The Connect Health approach to Clinical Support Tools Connect Health How To Use Traffic Light Protocol At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to. How To Use Traffic Light Protocol.
From gallery.zetalliance.org
Zeta Alliance Traffic Light Protocol TLP Zimlet How To Use Traffic Light Protocol The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. Tlp is a set of designations used to ensure that. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. Traffic light protocol (tlp) is a system of markings. How To Use Traffic Light Protocol.
From www.researchgate.net
The Traffic Light Protocol (TLP). Download Scientific Diagram How To Use Traffic Light Protocol The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. Tlp is a set of designations used to ensure that. At the 28th annual conference and agm in seoul, june. How To Use Traffic Light Protocol.
From gallery.zetalliance.org
Zeta Alliance Traffic Light Protocol TLP Confidential Header Zimlet How To Use Traffic Light Protocol The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. At the 28th annual conference and agm. How To Use Traffic Light Protocol.
From www.youtube.com
Updated Traffic Light Protocol (TLP) AT&T ThreatTraq YouTube How To Use Traffic Light Protocol The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The traffic. How To Use Traffic Light Protocol.
From www.scribd.com
Traffic lights Communications Protocols Technology How To Use Traffic Light Protocol Tlp is a set of designations used to ensure that. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. The traffic light protocol. How To Use Traffic Light Protocol.
From blog.zimbra.com
Traffic Light Protocol (TLP) Zimlet Zimbra Blog How To Use Traffic Light Protocol The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The traffic light protocol (tlp) is a. How To Use Traffic Light Protocol.
From reminthink.com
How to protect the confidentiality of information with Traffic Light How To Use Traffic Light Protocol Tlp is a set of designations used to ensure that. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The traffic light protocol (tlp) is a fundamental designation. How To Use Traffic Light Protocol.
From www.researchgate.net
11 The traffic light protocol. Download Scientific Diagram How To Use Traffic Light Protocol The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions. How To Use Traffic Light Protocol.
From docslib.org
TRAFFIC LIGHT PROTOCOL (TLP) FIRST Standards Definitions and Usage How To Use Traffic Light Protocol Tlp is a set of designations used to ensure that. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat. How To Use Traffic Light Protocol.
From elemendar.com
Traffic Light Protocol is Green for Go! Elemendar How To Use Traffic Light Protocol The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. Tlp is a set of designations used to ensure that. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. At the 28th annual conference and agm in seoul, june 2016, the. How To Use Traffic Light Protocol.
From www.cert.govt.nz
Traffic light protocol CERT NZ How To Use Traffic Light Protocol Tlp is a set of designations used to ensure that. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat. How To Use Traffic Light Protocol.
From www.behance.net
Infografía Traffic Light Protocol on Behance How To Use Traffic Light Protocol The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. Tlp is a set of designations used to ensure that. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. Traffic light protocol (tlp). How To Use Traffic Light Protocol.
From insightforfuture.blogspot.com
Insight 8*6 LED Matrix for Intelligent Traffic Light System How To Use Traffic Light Protocol The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. Traffic light protocol (tlp) is a system. How To Use Traffic Light Protocol.
From cyberhoot.com
Traffic Light Protocol (TLP) CyberHoot How To Use Traffic Light Protocol Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a. How To Use Traffic Light Protocol.
From www.sentinelone.com
What is Traffic Light Protocol (TLP) in Cybersecurity? How To Use Traffic Light Protocol The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a. How To Use Traffic Light Protocol.
From pshumanresources.co.uk
Navigating the travel traffic light system this summer PS Human Resources How To Use Traffic Light Protocol The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. Tlp is a set of designations used. How To Use Traffic Light Protocol.
From logixconsulting.com
What Is the Traffic Light Protocol (TLP) and How Does It Work? Logix How To Use Traffic Light Protocol At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. Tlp is a set of designations used to ensure that. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. The traffic light protocol (tlp) was. How To Use Traffic Light Protocol.
From thinkingpathwayz.weebly.com
Traffic Light Reflection THINKING PATHWAYS How To Use Traffic Light Protocol Tlp is a set of designations used to ensure that. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat. How To Use Traffic Light Protocol.
From www.youtube.com
What is Traffic Light Protocol? YouTube How To Use Traffic Light Protocol Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Tlp is. How To Use Traffic Light Protocol.
From www.wbbjtv.com
Officials talks power outage priority, traffic light protocol WBBJ TV How To Use Traffic Light Protocol Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. The traffic light protocol (tlp) is a. How To Use Traffic Light Protocol.
From www.carparts.com
All About Traffic Lights Traffic Light Size, Weight, and More In The How To Use Traffic Light Protocol At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. Tlp is a set of designations used to ensure that. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Traffic light protocol (tlp) is a. How To Use Traffic Light Protocol.
From gallery.zetalliance.org
Zeta Alliance Traffic Light Protocol TLP Confidential Header Zimlet How To Use Traffic Light Protocol The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. At the. How To Use Traffic Light Protocol.
From warnerchad.medium.com
Traffic Light Protocol (TLP) 2.0 in Cyber Threat Intelligence by Chad How To Use Traffic Light Protocol The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Tlp is a set of designations used to ensure that. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. Traffic light protocol (tlp) is a system of markings that designates the. How To Use Traffic Light Protocol.
From gallery.zetalliance.org
Zeta Alliance Traffic Light Protocol TLP Zimlet How To Use Traffic Light Protocol The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Tlp is a set of designations used to ensure that. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may. How To Use Traffic Light Protocol.
From www.pinterest.co.uk
Traffic Light List for PowerPoint Traffic light How To Use Traffic Light Protocol Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. The traffic. How To Use Traffic Light Protocol.
From www.csoonline.com
What is Traffic Light Protocol? Here’s how it supports CISOs in sharing How To Use Traffic Light Protocol At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients. How To Use Traffic Light Protocol.
From blog.zimbra.com
Traffic Light Protocol (TLP) Zimlet Zimbra Blog How To Use Traffic Light Protocol Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions. How To Use Traffic Light Protocol.
From cyberhoot.com
Traffic Light Protocol CyberHoot How To Use Traffic Light Protocol The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. The tlp or traffic light protocol is a set of designations designed to help sharing of sensitive information. Tlp is a set of designations used. How To Use Traffic Light Protocol.
From cyware.com
Traffic Light Protocol (TLP) 2.0 Threat Intel Sharing Standard Now How To Use Traffic Light Protocol The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions. How To Use Traffic Light Protocol.
From www.bleepingcomputer.com
New Traffic Light Protocol standard released after five years How To Use Traffic Light Protocol The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. The traffic light protocol (tlp) was created in order to facilitate greater sharing of information. Traffic light protocol (tlp) is a system of markings that designates the extent to which recipients may share potentially sensitive. Tlp is a set of. How To Use Traffic Light Protocol.
From pitterpatterdance.co.nz
Traffic Light System Pitter Patter Dance How To Use Traffic Light Protocol The traffic light protocol (tlp) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify. At the 28th annual conference and agm in seoul, june 2016, the tlp sig produced the initial draft of a common, standardized set of definitions for. The tlp or traffic light protocol is a set of designations designed to help. How To Use Traffic Light Protocol.