Search Box Xss . The actors involved in an xss. This cheat sheet helps developers prevent xss vulnerabilities. You can select vectors by the event, tag or browser and a proof of concept. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. I have a textbox which is used for searching the data within the site. What my client wants that, 1)enter any text in the search field. Originally this term was derived. I decided to try a bunch of special character — !@#$%^&* ()_+. Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. I quickly noticed that anything after & and # was acting differently. I then decided to see how each symbol works. This code is privileged in. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results.
from www.exceldemy.com
The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. I then decided to see how each symbol works. I decided to try a bunch of special character — !@#$%^&* ()_+. Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. I have a textbox which is used for searching the data within the site. You can select vectors by the event, tag or browser and a proof of concept. The actors involved in an xss. This code is privileged in. Originally this term was derived. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results.
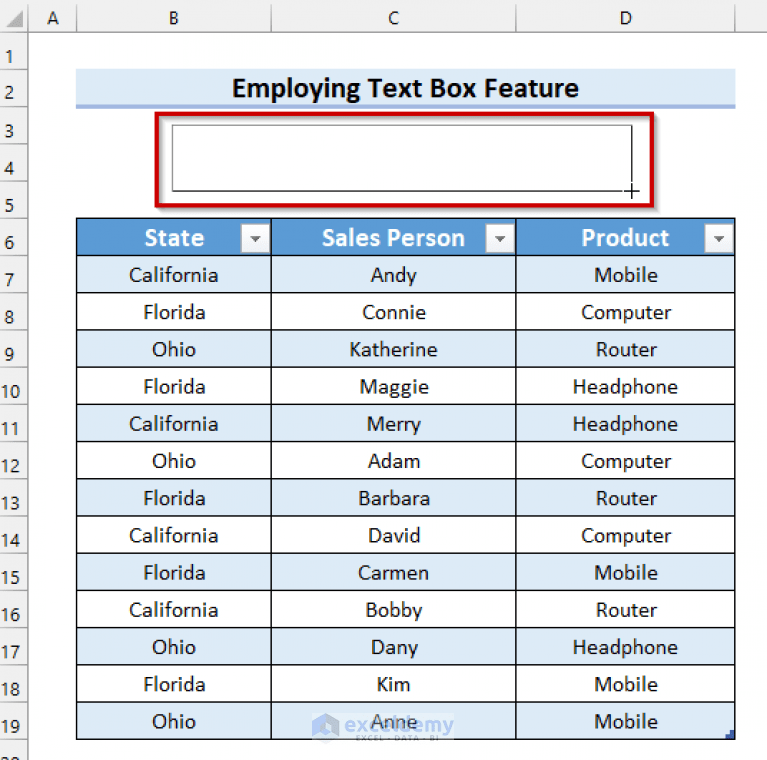
Create a Search Box in Excel with VBA (5 Suitable Examples)
Search Box Xss I quickly noticed that anything after & and # was acting differently. This code is privileged in. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. I quickly noticed that anything after & and # was acting differently. You can select vectors by the event, tag or browser and a proof of concept. Originally this term was derived. This cheat sheet helps developers prevent xss vulnerabilities. I then decided to see how each symbol works. I have a textbox which is used for searching the data within the site. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. The actors involved in an xss. I decided to try a bunch of special character — !@#$%^&* ()_+. What my client wants that, 1)enter any text in the search field.
From www.vecteezy.com
Search box with copy space, search bar icon. vector. 21868694 Vector Search Box Xss This cheat sheet helps developers prevent xss vulnerabilities. I decided to try a bunch of special character — !@#$%^&* ()_+. Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. The actors involved in an xss. You can select vectors by the event, tag or browser. Search Box Xss.
From aspsecuritykit.net
Understand CrossSite Scripting (XSS) by examples in the Zero Search Box Xss You can select vectors by the event, tag or browser and a proof of concept. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. I then decided to see how each symbol works. What my client wants that, 1)enter any text in the. Search Box Xss.
From detectify.com
XSS Vulnerability Scanner Detectify Search Box Xss You can select vectors by the event, tag or browser and a proof of concept. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. I then decided to see how each symbol works. What my client wants that, 1)enter any text in the search field. Xss. Search Box Xss.
From mygeektricks.blogspot.com
how to find xss cross site scripting vulnerability in website My Geek Search Box Xss In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. I quickly noticed that anything after & and # was acting differently. This cheat sheet helps developers prevent xss vulnerabilities. What my client wants that, 1)enter any text in the search field. I decided. Search Box Xss.
From www.iconpacks.net
Free XSS Attack And Browser SVG, PNG Icon, Symbol. Download Image. Search Box Xss I quickly noticed that anything after & and # was acting differently. This cheat sheet helps developers prevent xss vulnerabilities. You can select vectors by the event, tag or browser and a proof of concept. Originally this term was derived. In this challenge, we have a simple search website, it has a search box, and when we search for something,. Search Box Xss.
From sheetsformarketers.com
How to Create a Search Box in Google Sheets Sheets for Marketers Search Box Xss I quickly noticed that anything after & and # was acting differently. I decided to try a bunch of special character — !@#$%^&* ()_+. Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. The actors involved in an xss. You can select vectors by the. Search Box Xss.
From auth0.com
Defend Your Apps from CrossSite Scripting (XSS) Search Box Xss This cheat sheet helps developers prevent xss vulnerabilities. The actors involved in an xss. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. I decided to try a bunch of special character — !@#$%^&* ()_+. I have a textbox which is used for. Search Box Xss.
From www.youtube.com
XSS on Google Search Sanitizing HTML in The Client? YouTube Search Box Xss Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. I quickly noticed that anything after & and # was acting differently. What. Search Box Xss.
From www.exceldemy.com
How to Create a Search Box in Excel for Multiple Sheets (2 Ways) Search Box Xss The actors involved in an xss. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. You can select vectors by. Search Box Xss.
From www.youtube.com
Search Box, Html & Css only YouTube Search Box Xss In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. Originally this term was derived. I then decided to see how each symbol works. This code is privileged in. This cheat sheet helps developers prevent xss vulnerabilities. You can select vectors by the event,. Search Box Xss.
From www.codingnepalweb.com
Image Gallery with Search Box in HTML CSS & JavaScript Search Box Xss You can select vectors by the event, tag or browser and a proof of concept. This code is privileged in. This cheat sheet helps developers prevent xss vulnerabilities. Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. Originally this term was derived. The actors involved. Search Box Xss.
From www.softwaretestinghelp.com
Cross Site Scripting (XSS) Attack Tutorials with Examples, Types Search Box Xss The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. This cheat sheet helps developers prevent xss vulnerabilities. What my client wants that, 1)enter any text in the search field. Originally this term was derived. I decided to try a bunch of special character — !@#$%^&* ()_+.. Search Box Xss.
From www.kitploit.com
ExtendedXSSSearch Scans For Different Types Of XSS On A List Of URLs Search Box Xss Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. In this challenge, we have a simple search website, it has a search. Search Box Xss.
From www.youtube.com
How to Enable New Search Box on the Left Side of the Taskbar in Windows Search Box Xss What my client wants that, 1)enter any text in the search field. I then decided to see how each symbol works. This cheat sheet helps developers prevent xss vulnerabilities. I have a textbox which is used for searching the data within the site. I decided to try a bunch of special character — !@#$%^&* ()_+. You can select vectors by. Search Box Xss.
From www.youtube.com
How to do xss attack on a website YouTube Search Box Xss You can select vectors by the event, tag or browser and a proof of concept. Originally this term was derived. I quickly noticed that anything after & and # was acting differently. I have a textbox which is used for searching the data within the site. I then decided to see how each symbol works. I decided to try a. Search Box Xss.
From www.youtube.com
How to design search box YouTube Search Box Xss What my client wants that, 1)enter any text in the search field. Originally this term was derived. This cheat sheet helps developers prevent xss vulnerabilities. You can select vectors by the event, tag or browser and a proof of concept. This code is privileged in. The goal of an xss attack is for an attacker to somehow inject code into. Search Box Xss.
From www.youtube.com
How To Create Search Box In Excel How to Search in Excel YouTube Search Box Xss This code is privileged in. What my client wants that, 1)enter any text in the search field. I then decided to see how each symbol works. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. I decided to try a bunch of special character — !@#$%^&*. Search Box Xss.
From www.exceldemy.com
Create a Search Box in Excel with VBA (5 Suitable Examples) Search Box Xss This code is privileged in. I quickly noticed that anything after & and # was acting differently. Originally this term was derived. You can select vectors by the event, tag or browser and a proof of concept. This cheat sheet helps developers prevent xss vulnerabilities. In this challenge, we have a simple search website, it has a search box, and. Search Box Xss.
From www.anoopcnair.com
Custom Search Box On The Taskbar Of Windows 11 HTMD Blog Search Box Xss Originally this term was derived. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. What my client wants that, 1)enter any text in the search field. The actors involved in an xss. I have a textbox which is used for searching the data. Search Box Xss.
From www.g2.com
What Is CrossSite Scripting? How To Prevent XSS Attacks Search Box Xss I have a textbox which is used for searching the data within the site. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web. Search Box Xss.
From payatu.com
How DOMbased CrossSite Scripting (XSS) Attack Works Search Box Xss I then decided to see how each symbol works. I quickly noticed that anything after & and # was acting differently. What my client wants that, 1)enter any text in the search field. Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. Originally this term. Search Box Xss.
From securityonline.info
toxssin POSTXSS exploitation tool Search Box Xss I quickly noticed that anything after & and # was acting differently. This code is privileged in. I have a textbox which is used for searching the data within the site. The actors involved in an xss. You can select vectors by the event, tag or browser and a proof of concept. Xss or cross site scripting is a web. Search Box Xss.
From meterpreter.org
Microsoft adds more ads to Windows 11 search box Search Box Xss What my client wants that, 1)enter any text in the search field. The actors involved in an xss. Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. I then decided to see how each symbol works. You can select vectors by the event, tag or. Search Box Xss.
From www.indusface.com
What is XSS and How to Prevent It? Indusface Blog Search Box Xss Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. What my client wants that, 1)enter any text in the search field. I decided to try a bunch of special character — !@#$%^&* ()_+. I quickly noticed that anything after & and # was acting differently.. Search Box Xss.
From jlajara.gitlab.io
XSS 101 Solving Google's XSS Challenge · Lajara site Search Box Xss I have a textbox which is used for searching the data within the site. This code is privileged in. I then decided to see how each symbol works. I quickly noticed that anything after & and # was acting differently. In this challenge, we have a simple search website, it has a search box, and when we search for something,. Search Box Xss.
From www.trustedsec.com
TrustedSec Scraping Login Credentials With XSS Search Box Xss I decided to try a bunch of special character — !@#$%^&* ()_+. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. This cheat sheet helps developers prevent xss vulnerabilities. I have a textbox which is used for searching the data within the site.. Search Box Xss.
From blog.csdn.net
XSS Cheat SheetCSDN博客 Search Box Xss In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. I quickly noticed that anything after & and # was acting differently. I have a textbox which is used for searching the data within the site. I decided to try a bunch of special. Search Box Xss.
From www.hacking.reviews
ExtendedXSSSearch Scans For Different Types Of XSS On A List Of Search Box Xss I have a textbox which is used for searching the data within the site. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served. Search Box Xss.
From www.exceldemy.com
How to Create a Search Box in Excel (4 Easy Methods) Search Box Xss The actors involved in an xss. I decided to try a bunch of special character — !@#$%^&* ()_+. This cheat sheet helps developers prevent xss vulnerabilities. This code is privileged in. I then decided to see how each symbol works. What my client wants that, 1)enter any text in the search field. In this challenge, we have a simple search. Search Box Xss.
From payatu.com
How DOMbased CrossSite Scripting (XSS) Attack Works Search Box Xss I have a textbox which is used for searching the data within the site. I decided to try a bunch of special character — !@#$%^&* ()_+. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the search results. The actors involved in an xss. I quickly. Search Box Xss.
From www.vecteezy.com
A search box with a wide search field and a magnifying glass search Search Box Xss I then decided to see how each symbol works. You can select vectors by the event, tag or browser and a proof of concept. I decided to try a bunch of special character — !@#$%^&* ()_+. In this challenge, we have a simple search website, it has a search box, and when we search for something, it will return the. Search Box Xss.
From www.tutorjoes.in
Different Style of Search Box Design in CSS Search Box Xss I have a textbox which is used for searching the data within the site. This cheat sheet helps developers prevent xss vulnerabilities. I then decided to see how each symbol works. The actors involved in an xss. You can select vectors by the event, tag or browser and a proof of concept. In this challenge, we have a simple search. Search Box Xss.
From www.exceldemy.com
How to Create a Search Box in Excel (4 Easy Methods) Search Box Xss I then decided to see how each symbol works. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. Xss or cross site scripting is a web application vulnerability that occurs when untrusted data from the user is processed by the web application. This code is privileged. Search Box Xss.
From www.youtube.com
XSSPLOIT Auto Search XSS Tutorial YouTube Search Box Xss You can select vectors by the event, tag or browser and a proof of concept. This cheat sheet helps developers prevent xss vulnerabilities. I decided to try a bunch of special character — !@#$%^&* ()_+. The goal of an xss attack is for an attacker to somehow inject code into a webpage that is served from your site. I then. Search Box Xss.
From www.youtube.com
hard xss in search box YouTube Search Box Xss What my client wants that, 1)enter any text in the search field. I have a textbox which is used for searching the data within the site. Originally this term was derived. The actors involved in an xss. I then decided to see how each symbol works. Xss or cross site scripting is a web application vulnerability that occurs when untrusted. Search Box Xss.