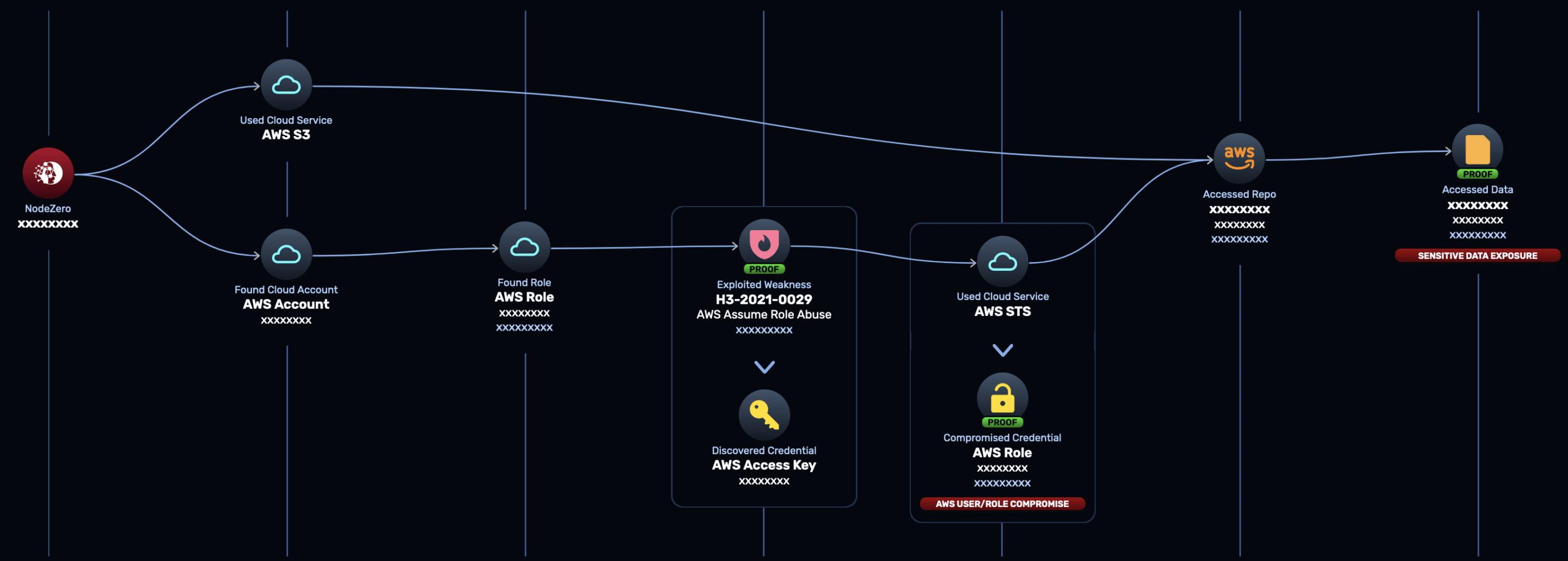
Aws Bucket Misconfiguration . If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. Step by step guide to takeover misconfigured s3 bucket; Download our aws security misconfigurations cheat sheet to learn more. Here are a few pro tips you can implement relatively. Dangling dns with a public deleted aws s3 bucket. If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. Here are the top aws s3 buckets misconfigurations that you need to. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: S3 buckets are considered vulnerable to data exposure. These policies help ensure secure settings for. How to find s3 buckets; Once on the lab url,.
from www.horizon3.ai
Download our aws security misconfigurations cheat sheet to learn more. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: How to find s3 buckets; Step by step guide to takeover misconfigured s3 bucket; Dangling dns with a public deleted aws s3 bucket. If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. Once on the lab url,. S3 buckets are considered vulnerable to data exposure. These policies help ensure secure settings for. Here are a few pro tips you can implement relatively.
AWS Misconfiguration Leads to Buckets of Data Horizon3.ai
Aws Bucket Misconfiguration Here are a few pro tips you can implement relatively. Download our aws security misconfigurations cheat sheet to learn more. Dangling dns with a public deleted aws s3 bucket. Once on the lab url,. S3 buckets are considered vulnerable to data exposure. Step by step guide to takeover misconfigured s3 bucket; Here are the top aws s3 buckets misconfigurations that you need to. These policies help ensure secure settings for. If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. Here are a few pro tips you can implement relatively. If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. How to find s3 buckets; Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention:
From www.youtube.com
AWS S3 Bucket Misconfiguration POC Bug Bounty 2020 YouTube Aws Bucket Misconfiguration S3 buckets are considered vulnerable to data exposure. Here are the top aws s3 buckets misconfigurations that you need to. If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. Step by step guide to takeover misconfigured s3 bucket; These policies help ensure secure settings for. Once on the. Aws Bucket Misconfiguration.
From security.packt.com
Detect AWS S3 Bucket Misconfiguration using OpenSource tools Packt Aws Bucket Misconfiguration Once on the lab url,. How to find s3 buckets; Step by step guide to takeover misconfigured s3 bucket; If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. These policies help ensure secure settings for. If you’re using aws, keeping an eye out for warning signs that a. Aws Bucket Misconfiguration.
From cycode.com
How To Prevent AWS S3 Bucket Misconfigurations Aws Bucket Misconfiguration Once on the lab url,. Here are the top aws s3 buckets misconfigurations that you need to. If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. How to find s3 buckets; Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and. Aws Bucket Misconfiguration.
From exojzwiho.blob.core.windows.net
Aws S3 Bucket Java Api at Carol Hargett blog Aws Bucket Misconfiguration If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. Download our aws security misconfigurations cheat sheet to learn more. S3 buckets are considered vulnerable to data exposure. Dangling dns with a public deleted aws s3 bucket. Here are a few pro tips you can implement relatively. These policies. Aws Bucket Misconfiguration.
From medium.com
AWS S3 Bucket Misconfiguration. Hello I am Sudharshan (just a noob who Aws Bucket Misconfiguration Here are a few pro tips you can implement relatively. Dangling dns with a public deleted aws s3 bucket. S3 buckets are considered vulnerable to data exposure. Step by step guide to takeover misconfigured s3 bucket; If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. Cycode. Aws Bucket Misconfiguration.
From www.securin.io
AWS S3 Bucket Misconfiguration Lessons Learned from SEGA Europe’s Aws Bucket Misconfiguration Dangling dns with a public deleted aws s3 bucket. Here are the top aws s3 buckets misconfigurations that you need to. Here are a few pro tips you can implement relatively. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: If you’re using aws, keeping an eye out for warning signs that. Aws Bucket Misconfiguration.
From u3nerd.hatenablog.com
AWS S3 Bucket Misconfiguration Exposes PII and Documents of Job Seekers Aws Bucket Misconfiguration If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. Once on the lab url,. If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. S3 buckets are considered vulnerable to data exposure. Dangling dns with. Aws Bucket Misconfiguration.
From u3nerd.hatenablog.com
AWS S3 Bucket Misconfiguration Exposes PII and Documents of Job Seekers Aws Bucket Misconfiguration Here are the top aws s3 buckets misconfigurations that you need to. Here are a few pro tips you can implement relatively. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: These policies help ensure secure settings for. How to find s3 buckets; Dangling dns with a public deleted aws s3 bucket.. Aws Bucket Misconfiguration.
From www.techzine.eu
'Lots of leaking AWS S3 storage buckets due to misconfiguration Aws Bucket Misconfiguration These policies help ensure secure settings for. S3 buckets are considered vulnerable to data exposure. Once on the lab url,. Dangling dns with a public deleted aws s3 bucket. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: Here are the top aws s3 buckets misconfigurations that you need to. Step by. Aws Bucket Misconfiguration.
From www.defenxor.com
Cara Identifikasi Misconfiguration AWS S3 Bucket, Lakukan Segera untuk Aws Bucket Misconfiguration If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. Here are a few pro tips you can implement relatively. Download our aws security misconfigurations cheat sheet to learn more. How to find s3 buckets; S3 buckets are considered vulnerable to data exposure. Dangling dns with a. Aws Bucket Misconfiguration.
From security.packt.com
Detect AWS S3 Bucket Misconfiguration using OpenSource tools Packt Aws Bucket Misconfiguration Once on the lab url,. Step by step guide to takeover misconfigured s3 bucket; Here are a few pro tips you can implement relatively. These policies help ensure secure settings for. Here are the top aws s3 buckets misconfigurations that you need to. Download our aws security misconfigurations cheat sheet to learn more. Dangling dns with a public deleted aws. Aws Bucket Misconfiguration.
From security.packt.com
Detect AWS S3 Bucket Misconfiguration using OpenSource tools Packt Aws Bucket Misconfiguration Step by step guide to takeover misconfigured s3 bucket; S3 buckets are considered vulnerable to data exposure. If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. How to find s3 buckets; Download our aws security misconfigurations cheat sheet to learn more. Cycode currently offers over 30. Aws Bucket Misconfiguration.
From www.webhat.in
AWS > Create bucket > General configuration Hat Aws Bucket Misconfiguration If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. These policies help ensure secure settings for. S3 buckets are considered vulnerable to data exposure. Download our aws security misconfigurations cheat sheet to learn more. How to find s3 buckets; Once on the lab url,. Cycode currently offers over. Aws Bucket Misconfiguration.
From exyydqkjo.blob.core.windows.net
Amazon S3 Bucket Misconfiguration at Elton Perez blog Aws Bucket Misconfiguration Once on the lab url,. Dangling dns with a public deleted aws s3 bucket. How to find s3 buckets; Download our aws security misconfigurations cheat sheet to learn more. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: Here are a few pro tips you can implement relatively. S3 buckets are considered. Aws Bucket Misconfiguration.
From www.securin.io
AWS S3 Bucket Misconfiguration Lessons Learned from SEGA Europe’s Aws Bucket Misconfiguration Dangling dns with a public deleted aws s3 bucket. Once on the lab url,. Here are a few pro tips you can implement relatively. If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. How to find s3 buckets; Step by step guide to takeover misconfigured s3 bucket; Cycode. Aws Bucket Misconfiguration.
From www.armorcode.com
AWS S3 Bucket Security The Top CSPM Practices ArmorCode Aws Bucket Misconfiguration Step by step guide to takeover misconfigured s3 bucket; Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. These policies help ensure secure settings for. If you are vulnerable,. Aws Bucket Misconfiguration.
From teguh.co
SSRF Vulnerability dan AWS S3 Bucket Misconfiguration di Placeit Aws Bucket Misconfiguration These policies help ensure secure settings for. S3 buckets are considered vulnerable to data exposure. Here are the top aws s3 buckets misconfigurations that you need to. Step by step guide to takeover misconfigured s3 bucket; Once on the lab url,. If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and. Aws Bucket Misconfiguration.
From www.horizon3.ai
AWS Misconfiguration Leads to Buckets of Data Horizon3.ai Aws Bucket Misconfiguration Here are the top aws s3 buckets misconfigurations that you need to. These policies help ensure secure settings for. Once on the lab url,. If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. How to find s3 buckets; Here are a few pro tips you can. Aws Bucket Misconfiguration.
From sumeru.gitbook.io
AWS S3 Bucket Misconfiguration Sumeru Cyber Security Aws Bucket Misconfiguration S3 buckets are considered vulnerable to data exposure. Download our aws security misconfigurations cheat sheet to learn more. If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. Dangling dns with a public deleted aws s3 bucket. Here are the top aws s3 buckets misconfigurations that you need to.. Aws Bucket Misconfiguration.
From www.youtube.com
AWS S3 Bucket Misconfiguration EXPLAINED YouTube Aws Bucket Misconfiguration How to find s3 buckets; Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: Once on the lab url,. These policies help ensure secure settings for. If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. Here are the. Aws Bucket Misconfiguration.
From securityboulevard.com
AWS Misconfiguration Leads to Buckets of Data Security Boulevard Aws Bucket Misconfiguration S3 buckets are considered vulnerable to data exposure. Once on the lab url,. How to find s3 buckets; If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. Dangling dns with a public deleted aws s3 bucket. If you are vulnerable, attackers could get full access to. Aws Bucket Misconfiguration.
From www.defenxor.com
Cara Identifikasi Misconfiguration AWS S3 Bucket, Lakukan Segera untuk Aws Bucket Misconfiguration Once on the lab url,. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: Here are a few pro tips you can implement relatively. S3 buckets are considered vulnerable to data exposure. These policies help ensure secure settings for. Here are the top aws s3 buckets misconfigurations that you need to. Download. Aws Bucket Misconfiguration.
From www.securin.io
AWS S3 Bucket Misconfiguration Lessons Learned from SEGA Europe’s Aws Bucket Misconfiguration Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. Here are a few pro tips you can implement relatively. If you’re using aws, keeping an eye out for warning signs that. Aws Bucket Misconfiguration.
From infosecwriteups.com
AWS S3 Bucket Misconfiguration Exposes PII and Documents of Job Seekers Aws Bucket Misconfiguration Step by step guide to takeover misconfigured s3 bucket; Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: How to find s3 buckets; Here are a few pro tips you can implement relatively. Dangling dns with a public deleted aws s3 bucket. If you are vulnerable, attackers could get full access to. Aws Bucket Misconfiguration.
From aws.amazon.com
Synchronizing Amazon S3 Buckets Using AWS Step Functions AWS Compute Blog Aws Bucket Misconfiguration Once on the lab url,. If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. S3 buckets are considered vulnerable to data exposure. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: Step by step guide to takeover misconfigured s3 bucket;. Aws Bucket Misconfiguration.
From secops.group
The Anatomy of AWS Misconfigurations How to Stay Safe • The SecOps Group Aws Bucket Misconfiguration If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. Dangling dns with a public deleted aws s3 bucket. Here are a few pro tips you can implement relatively. Here are the top aws s3 buckets misconfigurations that you need to. These policies help ensure secure settings for. Step. Aws Bucket Misconfiguration.
From www.youtube.com
AWS S3 BUCKET MISCONFIGURATION HOW TO FIND S3 BUCKETS CLOUD Aws Bucket Misconfiguration Step by step guide to takeover misconfigured s3 bucket; If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. S3 buckets are considered vulnerable to data. Aws Bucket Misconfiguration.
From secops.group
The Anatomy of AWS Misconfigurations How to Stay Safe • The SecOps Group Aws Bucket Misconfiguration Download our aws security misconfigurations cheat sheet to learn more. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: Here are the top aws s3 buckets misconfigurations that you need to. Here are a few pro tips you can implement relatively. How to find s3 buckets; If you are vulnerable, attackers could. Aws Bucket Misconfiguration.
From www.youtube.com
HOW TO FIND AWS S3 BUCKET MISCONFIGURATION VULNERABILITIES CLOUD Aws Bucket Misconfiguration Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: Once on the lab url,. How to find s3 buckets; Dangling dns with a public deleted aws s3 bucket. Here are a few pro tips you can implement relatively. Download our aws security misconfigurations cheat sheet to learn more. S3 buckets are considered. Aws Bucket Misconfiguration.
From home.bigid.com
Solution Brief Bucket Configuration Management Aws Bucket Misconfiguration Download our aws security misconfigurations cheat sheet to learn more. These policies help ensure secure settings for. Here are the top aws s3 buckets misconfigurations that you need to. Once on the lab url,. If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. Here are a few pro. Aws Bucket Misconfiguration.
From www.securin.io
AWS S3 Bucket Misconfiguration Lessons Learned from SEGA Europe’s Aws Bucket Misconfiguration Download our aws security misconfigurations cheat sheet to learn more. Once on the lab url,. Here are the top aws s3 buckets misconfigurations that you need to. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: These policies help ensure secure settings for. How to find s3 buckets; Dangling dns with a. Aws Bucket Misconfiguration.
From mostafa-mano.medium.com
S3 Bucket Misconfiguration Lead To Access Sensitive Files by Mostafa Aws Bucket Misconfiguration Here are a few pro tips you can implement relatively. If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: Here are the top aws s3 buckets misconfigurations that you. Aws Bucket Misconfiguration.
From www.horizon3.ai
AWS Misconfiguration Leads to Buckets of Data Horizon3.ai Aws Bucket Misconfiguration Here are the top aws s3 buckets misconfigurations that you need to. Cycode currently offers over 30 cloud and iac policies related to aws s3 governance and misconfiguration prevention: Dangling dns with a public deleted aws s3 bucket. If you are vulnerable, attackers could get full access to your s3 bucket, allowing them to download, upload and overwrite files. Download. Aws Bucket Misconfiguration.
From www.techzine.eu
'Lots of leaking AWS S3 storage buckets due to misconfiguration Aws Bucket Misconfiguration Dangling dns with a public deleted aws s3 bucket. How to find s3 buckets; If you’re using aws, keeping an eye out for warning signs that a bucket may have “gone public” should be top of mind. Step by step guide to takeover misconfigured s3 bucket; Here are the top aws s3 buckets misconfigurations that you need to. If you. Aws Bucket Misconfiguration.
From cycode.com
How To Prevent AWS S3 Bucket Misconfigurations Aws Bucket Misconfiguration Step by step guide to takeover misconfigured s3 bucket; Download our aws security misconfigurations cheat sheet to learn more. Here are the top aws s3 buckets misconfigurations that you need to. How to find s3 buckets; Here are a few pro tips you can implement relatively. These policies help ensure secure settings for. If you’re using aws, keeping an eye. Aws Bucket Misconfiguration.