What Is Access Control Rule Configuration . This tutorial explains how to configure cisco access control lists. A network router uses the rules in its acl to determine how — or whether — to route each incoming packet. What are access control lists (acls)? An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. An access control list (acl) is a tool used to enforce it security policies. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. This tutorial explains how to configure, view, edit, update and delete a standard named access control. Learn cisco acls configuration commands with their arguments, options, and parameters. The primary purpose of access control lists is to secure. Learn how to create and manage a. An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system.
from www.cisco.com
Learn how to create and manage a. Learn cisco acls configuration commands with their arguments, options, and parameters. The primary purpose of access control lists is to secure. This tutorial explains how to configure, view, edit, update and delete a standard named access control. A network router uses the rules in its acl to determine how — or whether — to route each incoming packet. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. This tutorial explains how to configure cisco access control lists. An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. What are access control lists (acls)?
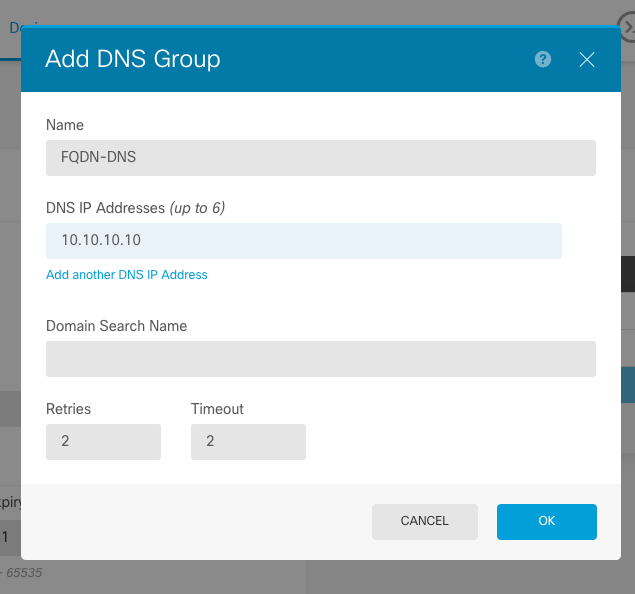
Configure FQDN Based Object for Access Control Rule Cisco
What Is Access Control Rule Configuration The primary purpose of access control lists is to secure. The primary purpose of access control lists is to secure. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Learn cisco acls configuration commands with their arguments, options, and parameters. An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. Learn how to create and manage a. An access control list (acl) is a tool used to enforce it security policies. This tutorial explains how to configure, view, edit, update and delete a standard named access control. What are access control lists (acls)? A network router uses the rules in its acl to determine how — or whether — to route each incoming packet. An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. This tutorial explains how to configure cisco access control lists.
From www.slideserve.com
PPT WLCGRUS PowerPoint Presentation, free download ID6457178 What Is Access Control Rule Configuration An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. Learn cisco acls configuration commands with their arguments,. What Is Access Control Rule Configuration.
From www.cisco.com
Configure FQDN Based Object for Access Control Rule Cisco What Is Access Control Rule Configuration An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. This tutorial explains how to configure cisco. What Is Access Control Rule Configuration.
From thecyphere.com
Access Control Security Types Of Access Control What Is Access Control Rule Configuration The primary purpose of access control lists is to secure. Learn cisco acls configuration commands with their arguments, options, and parameters. An access control list (acl) is a tool used to enforce it security policies. This tutorial explains how to configure, view, edit, update and delete a standard named access control. An access control list (acl) is a list of. What Is Access Control Rule Configuration.
From www.cisco.com
Configure FQDN Based Object for Access Control Rule Cisco What Is Access Control Rule Configuration This tutorial explains how to configure, view, edit, update and delete a standard named access control. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. An access control list (acl) is a tool used to enforce it security policies. Learn how to create. What Is Access Control Rule Configuration.
From getsafeandsound.com
Access Control Systems The Complete Guide for 2023 What Is Access Control Rule Configuration The primary purpose of access control lists is to secure. An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. An access control list is a set of rules that govern the flow of traffic through a network device, such as a router,. What Is Access Control Rule Configuration.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator What Is Access Control Rule Configuration Learn how to create and manage a. What are access control lists (acls)? Learn cisco acls configuration commands with their arguments, options, and parameters. This tutorial explains how to configure cisco access control lists. A network router uses the rules in its acl to determine how — or whether — to route each incoming packet. The primary purpose of access. What Is Access Control Rule Configuration.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free What Is Access Control Rule Configuration What are access control lists (acls)? Learn cisco acls configuration commands with their arguments, options, and parameters. An access control list (acl) is a tool used to enforce it security policies. An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. Learn how to. What Is Access Control Rule Configuration.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free What Is Access Control Rule Configuration The primary purpose of access control lists is to secure. An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. An access control list (acl) is a tool used to enforce it security policies. This tutorial explains how to configure cisco access control lists.. What Is Access Control Rule Configuration.
From pegaks.com
How To Configuring Attribute Based Access Control Pega 8 Pega KS What Is Access Control Rule Configuration A network router uses the rules in its acl to determine how — or whether — to route each incoming packet. An access control list (acl) is a tool used to enforce it security policies. Learn how to create and manage a. What are access control lists (acls)? Access control lists are made up of a set of rules used. What Is Access Control Rule Configuration.
From liquidvideotechnologies.com
What is Access Control Liquid Video Technologies What Is Access Control Rule Configuration What are access control lists (acls)? It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. An access control list (acl) is a tool used to enforce it security policies. An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. What Is Access Control Rule Configuration.
From www.pynetlabs.com
What is Network Access Control List (ACL)? Labs What Is Access Control Rule Configuration An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. What are access control lists (acls)? An access control list (acl) is a tool used to enforce it security policies. An access control list (acl) is a list of rules that specifies which users. What Is Access Control Rule Configuration.
From docs.terminalfour.com
Access Control Configuration Terminalfour Knowledge Base What Is Access Control Rule Configuration An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. Learn how to create and manage a. This. What Is Access Control Rule Configuration.
From hackersparadise01.com
What is Access Control? Important Networking Basics Part 25 What Is Access Control Rule Configuration Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. What are access control lists (acls)? This tutorial explains how to configure cisco access control lists. The. What Is Access Control Rule Configuration.
From www.comparitech.com
How to create & configure an access control list (ACL) stepbystep What Is Access Control Rule Configuration Learn cisco acls configuration commands with their arguments, options, and parameters. An access control list (acl) is a tool used to enforce it security policies. This tutorial explains how to configure cisco access control lists. An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or. What Is Access Control Rule Configuration.
From www.shineacs.com
How to configure an access control system? ShineACS Security What Is Access Control Rule Configuration An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. Learn how to create and manage a. An access control list (acl) is a tool used to enforce it security policies. Learn cisco acls configuration commands with their arguments, options, and parameters. This tutorial. What Is Access Control Rule Configuration.
From www.slideserve.com
PPT 7Access Control Fundamentals PowerPoint Presentation, free What Is Access Control Rule Configuration An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. Learn cisco acls configuration commands with their arguments, options, and parameters. An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a. What Is Access Control Rule Configuration.
From www.sunnyvalley.io
What are Best Practices for Firewall Rules Configuration? sunnyvalley.io What Is Access Control Rule Configuration This tutorial explains how to configure cisco access control lists. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Learn cisco acls configuration commands with their. What Is Access Control Rule Configuration.
From www.cdvi.co.uk
What is access control? Access control explained CDVI UK What Is Access Control Rule Configuration An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. This tutorial explains how to configure cisco access control lists. This tutorial explains how to configure,. What Is Access Control Rule Configuration.
From blog.nortechcontrol.com
What Is Access Control? (Simple Guide) What Is Access Control Rule Configuration It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. Learn cisco acls configuration commands with their arguments, options, and parameters. An access control list (acl) is. What Is Access Control Rule Configuration.
From jaycemeowcunningham.blogspot.com
What Function Describe the Uses of an Access Control List What Is Access Control Rule Configuration An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. What are access control lists (acls)? Learn cisco acls configuration commands with their arguments, options, and parameters. This tutorial explains how to configure, view, edit, update and delete a standard named access control. It. What Is Access Control Rule Configuration.
From www.researchgate.net
Example of access control rule placement Download Scientific Diagram What Is Access Control Rule Configuration Learn how to create and manage a. A network router uses the rules in its acl to determine how — or whether — to route each incoming packet. An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. Learn cisco acls configuration commands. What Is Access Control Rule Configuration.
From sath.com
RuleBased Access Control Understanding The Basics What Is Access Control Rule Configuration This tutorial explains how to configure, view, edit, update and delete a standard named access control. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. An access control list (acl) is a tool used to enforce it security policies. A network router uses. What Is Access Control Rule Configuration.
From www.slideserve.com
PPT Module 11 PowerPoint Presentation, free download ID1591973 What Is Access Control Rule Configuration It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. This tutorial explains how to configure, view, edit, update and delete a standard named access control. This tutorial explains how to configure cisco access control lists. An access control list is a set of rules that govern the flow of traffic through a. What Is Access Control Rule Configuration.
From www.cisco.com
Configure FQDN Based Object for Access Control Rule Cisco What Is Access Control Rule Configuration Learn cisco acls configuration commands with their arguments, options, and parameters. This tutorial explains how to configure cisco access control lists. This tutorial explains how to configure, view, edit, update and delete a standard named access control. Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories,. What Is Access Control Rule Configuration.
From content-1606--budibase.netlify.app
RoleBased Access Control Ultimate Guide What Is Access Control Rule Configuration What are access control lists (acls)? Learn cisco acls configuration commands with their arguments, options, and parameters. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch.. What Is Access Control Rule Configuration.
From cyberhoot.com
Access Control Mechanism CyberHoot What Is Access Control Rule Configuration It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. What are access control lists (acls)? A network router uses the rules in its acl to determine how — or whether — to route each incoming packet. This tutorial explains how to configure cisco access control lists. This tutorial explains how to configure,. What Is Access Control Rule Configuration.
From www.getgenea.com
Types of Access Control RuleBased vs RoleBased & More 2024 Guide What Is Access Control Rule Configuration An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. What are access control lists (acls)? This tutorial explains how to configure, view, edit, update and delete a standard named access control. An access control list is a set of rules that govern. What Is Access Control Rule Configuration.
From www.youtube.com
Configuring cisco extended acl / extended named access control list What Is Access Control Rule Configuration An access control list (acl) is a tool used to enforce it security policies. An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. The primary purpose of access control lists is to secure. Learn how to create and manage a. This tutorial. What Is Access Control Rule Configuration.
From pynetlabsnetwork.blogspot.com
What is Access Control List (ACL)? What Is Access Control Rule Configuration An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. What are access control lists (acls)? This. What Is Access Control Rule Configuration.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download What Is Access Control Rule Configuration Learn how to create and manage a. An access control list (acl) is a tool used to enforce it security policies. What are access control lists (acls)? Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. The primary purpose of access control lists. What Is Access Control Rule Configuration.
From www.slideserve.com
PPT Chapter 9 Access Control and Authorization PowerPoint What Is Access Control Rule Configuration Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. An access control list is a set of rules that govern the flow of traffic through a network device, such as a router, firewall, or switch. Learn cisco acls configuration commands with their arguments,. What Is Access Control Rule Configuration.
From www.slideserve.com
PPT Access Control Matrix PowerPoint Presentation, free download ID What Is Access Control Rule Configuration An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. Learn cisco acls configuration commands with their arguments, options, and parameters. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. This tutorial explains how to. What Is Access Control Rule Configuration.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 What Is Access Control Rule Configuration An access control list (acl) is a tool used to enforce it security policies. Learn how to create and manage a. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Learn cisco acls configuration commands with their arguments, options, and parameters. This tutorial explains how to configure, view, edit, update and delete. What Is Access Control Rule Configuration.
From www.slideserve.com
PPT Access Control Lists PowerPoint Presentation, free download ID What Is Access Control Rule Configuration Learn how to create and manage a. What are access control lists (acls)? This tutorial explains how to configure, view, edit, update and delete a standard named access control. An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. This tutorial explains how. What Is Access Control Rule Configuration.
From budibase.com
RuleBased vs RoleBased Access Control What Is Access Control Rule Configuration An access control list (acl) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system. A network router uses the rules in its acl to determine how — or whether — to route each incoming packet. This tutorial explains how to configure cisco access control lists. An access. What Is Access Control Rule Configuration.