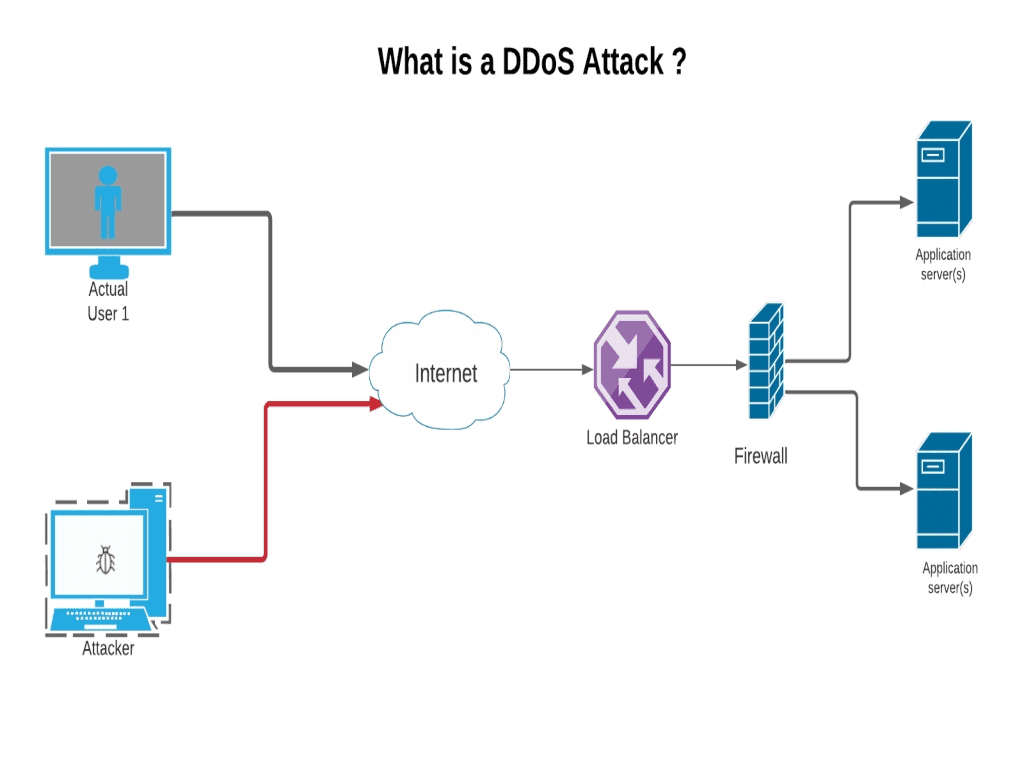
How To Block Ddos Attack In Fortigate . Learn the steps to ddos mitigation and what to look for in a mitigation. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. Configure the action to be taken when an attack is detected, such as. A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. Tcp port 80 for a web server) that cannot be. In this lab, we are going to set a ddos prevention on traffic from port1 to port2. In kali, we are going to install a. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc.
from www.loginradius.com
This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. Configure the action to be taken when an attack is detected, such as. Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. In kali, we are going to install a. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. In this lab, we are going to set a ddos prevention on traffic from port1 to port2. Learn the steps to ddos mitigation and what to look for in a mitigation. Tcp port 80 for a web server) that cannot be. A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks.
What is a DDoS Attack and How to Mitigate it
How To Block Ddos Attack In Fortigate Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. Learn the steps to ddos mitigation and what to look for in a mitigation. A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. In this lab, we are going to set a ddos prevention on traffic from port1 to port2. Tcp port 80 for a web server) that cannot be. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. Configure the action to be taken when an attack is detected, such as. Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. In kali, we are going to install a.
From www.sectigo.com
How A DDoS Attack Works And How To Prevent Them Sectigo® Official How To Block Ddos Attack In Fortigate Tcp port 80 for a web server) that cannot be. Learn the steps to ddos mitigation and what to look for in a mitigation. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g.. How To Block Ddos Attack In Fortigate.
From opentextbc.ca
7.1 DDoS Prevention FortiGate Firewall How To Block Ddos Attack In Fortigate Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network.. How To Block Ddos Attack In Fortigate.
From docs.fortinet.com
How to block the ongoing DDoS attack Forti Cloud 24.1.0 How To Block Ddos Attack In Fortigate This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. Tcp port 80 for a web server) that cannot be. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. Learn the steps to ddos mitigation and what to look for in a mitigation.. How To Block Ddos Attack In Fortigate.
From docs.fortinet.com
How to block the ongoing DDoS attack Forti Cloud 21.2.0 How To Block Ddos Attack In Fortigate In this lab, we are going to set a ddos prevention on traffic from port1 to port2. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. In a dos (denial of service) /. How To Block Ddos Attack In Fortigate.
From www.globalsign.com
What is DDoS Attack and How to Prevent It? How To Block Ddos Attack In Fortigate Configure the action to be taken when an attack is detected, such as. Tcp port 80 for a web server) that cannot be. In kali, we are going to install a. In this lab, we are going to set a ddos prevention on traffic from port1 to port2. In a dos (denial of service) / ddos (distributed denial of service). How To Block Ddos Attack In Fortigate.
From www.flowmon.com
How to Block an External Attack with FortiGate and Flowmon ADS Flowmon How To Block Ddos Attack In Fortigate This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. In this lab, we are going to set a ddos prevention on traffic from port1 to port2. A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. Tcp port 80 for a web server) that. How To Block Ddos Attack In Fortigate.
From www.youtube.com
How to protect against Denial of Service DoS & DDoS attacks using How To Block Ddos Attack In Fortigate In this lab, we are going to set a ddos prevention on traffic from port1 to port2. Configure the action to be taken when an attack is detected, such as. Tcp port 80 for a web server) that cannot be. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection. How To Block Ddos Attack In Fortigate.
From pressbooks.bccampus.ca
71 DDoS Prevention FortiGate Firewall Practical Guidance and Hands How To Block Ddos Attack In Fortigate Configure the action to be taken when an attack is detected, such as. A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. This article describes how to block a specific host permanently after an. How To Block Ddos Attack In Fortigate.
From www.youtube.com
How to block a website on Fortigate Firewall YouTube How To Block Ddos Attack In Fortigate Learn the steps to ddos mitigation and what to look for in a mitigation. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. Configure the action to be taken when an attack is detected, such as. This article describes how to block a specific host permanently after an. How To Block Ddos Attack In Fortigate.
From www.upguard.com
What is a DDoS Attack? How they Work + Protection Strategies UpGuard How To Block Ddos Attack In Fortigate A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. Configure the action to be taken when. How To Block Ddos Attack In Fortigate.
From greenclouddefense.com
FortiGate Enable IPS C&C Blocking Green Cloud Defense How To Block Ddos Attack In Fortigate In this lab, we are going to set a ddos prevention on traffic from port1 to port2. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. Learn the steps to ddos mitigation and what to look for in a mitigation. Tcp port 80 for a web server) that cannot be. In kali, we are. How To Block Ddos Attack In Fortigate.
From docs.fortinet.com
How to block the ongoing DDoS attack Forti Cloud 24.2.0 How To Block Ddos Attack In Fortigate Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. Tcp port 80 for a web server) that cannot be. Certain protocols can be blocked by firewalls, but most dos attacks. How To Block Ddos Attack In Fortigate.
From www.youtube.com
How to Block Application on FortiGate Firewall YouTube How To Block Ddos Attack In Fortigate A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. Tcp port 80 for a web server) that cannot be. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network.. How To Block Ddos Attack In Fortigate.
From clearvpn.com
How To Protect Yourself Against DDoS Attacks ClearVPN Blog How To Block Ddos Attack In Fortigate Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. Tcp port 80 for a web server) that cannot be. Learn the steps to ddos mitigation and what to look for in a mitigation. A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. Define the threshold values for various ddos. How To Block Ddos Attack In Fortigate.
From www.youtube.com
IPV4 DOS Policy Attack Protection in Fortigate Firewall(Education Only How To Block Ddos Attack In Fortigate Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. Configure the action to be taken when an attack is detected, such as. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. This article describes how to block a specific host permanently after. How To Block Ddos Attack In Fortigate.
From www.loginradius.com
What is a DDoS Attack and How to Mitigate it How To Block Ddos Attack In Fortigate A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. In this lab, we are going to set a ddos prevention on traffic from port1 to port2. Configure the action to be taken when an. How To Block Ddos Attack In Fortigate.
From securetriad.io
How to Stop a DDoS Attack and Protect Your Business? How To Block Ddos Attack In Fortigate A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. Learn the steps to. How To Block Ddos Attack In Fortigate.
From www.stormit.cloud
Cloud DDoS Protection How to Prevent and Mitigate DDoS How To Block Ddos Attack In Fortigate Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. Configure the action to be taken when an attack is detected, such as. Tcp port 80 for a web server) that cannot be. A. How To Block Ddos Attack In Fortigate.
From gcore.com
How to protect against DDoS attacks How To Block Ddos Attack In Fortigate In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. Tcp port 80 for a web server) that cannot be. In kali, we are going to install a. Configure the action. How To Block Ddos Attack In Fortigate.
From opentextbc.ca
7.1 DDoS Prevention FortiGate Firewall How To Block Ddos Attack In Fortigate Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. Learn the steps to ddos mitigation and what to look for in a mitigation. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. In a dos (denial of service) / ddos (distributed denial of service) attack,. How To Block Ddos Attack In Fortigate.
From www.flowmon.com
How to Block an External Attack with FortiGate and Flowmon ADS Flowmon How To Block Ddos Attack In Fortigate Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. Configure the action to be taken when an attack is detected, such as. Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. In a dos (denial of service) / ddos (distributed denial of service) attack, the. How To Block Ddos Attack In Fortigate.
From docs.fortinet.com
How to block the ongoing DDoS attack Forti Cloud 24.2.0 How To Block Ddos Attack In Fortigate Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. Learn the steps to ddos mitigation and what to look for in a mitigation. This article describes how to block a. How To Block Ddos Attack In Fortigate.
From blog.hostseo.com
A Beginner’s Guide To Understanding DDoS Attacks & How To Protect Your How To Block Ddos Attack In Fortigate Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. Configure the action to be taken when. How To Block Ddos Attack In Fortigate.
From greenclouddefense.com
FortiGate Enable IPS C&C Blocking Green Cloud Defense How To Block Ddos Attack In Fortigate In kali, we are going to install a. Tcp port 80 for a web server) that cannot be. In this lab, we are going to set a ddos prevention on traffic from port1 to port2. Configure the action to be taken when an attack is detected, such as. In a dos (denial of service) / ddos (distributed denial of service). How To Block Ddos Attack In Fortigate.
From www.indusface.com
What is a DDoS Attack and How Does it Work? Indusface How To Block Ddos Attack In Fortigate A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. In kali, we are going to install a. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. In a. How To Block Ddos Attack In Fortigate.
From www.youtube.com
Understanding FortiDDoS Attack Events DDoS Protection Solution YouTube How To Block Ddos Attack In Fortigate Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. Learn the steps to ddos mitigation and what to look for in a mitigation. In this lab, we are going to set a ddos prevention on traffic from port1 to port2. Define the threshold values for various ddos attack types, such as syn flood, udp. How To Block Ddos Attack In Fortigate.
From docs.fortinet.com
Using the DDoS attack log table FortiDDoSF 6.6.3 Document How To Block Ddos Attack In Fortigate Learn the steps to ddos mitigation and what to look for in a mitigation. In this lab, we are going to set a ddos prevention on traffic from port1 to port2. Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. Define the threshold values for various ddos attack types, such as syn flood, udp. How To Block Ddos Attack In Fortigate.
From www.esecurityplanet.com
How to Stop DDoS Attacks in Three Stages How To Block Ddos Attack In Fortigate Learn the steps to ddos mitigation and what to look for in a mitigation. Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. Configure the action to be taken when. How To Block Ddos Attack In Fortigate.
From techhorizonvn.com
FortiDDoS Giải Pháp bảo vệ DDoS của TECH HORIZON CORP. How To Block Ddos Attack In Fortigate Learn the steps to ddos mitigation and what to look for in a mitigation. In kali, we are going to install a. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. A ddos mitigation strategy is necessary to protect organizations from potentially devastating ddos attacks. Tcp port 80. How To Block Ddos Attack In Fortigate.
From www.youtube.com
How to Block sites in Fortigate Firewall Part 5 YouTube How To Block Ddos Attack In Fortigate In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. In kali, we are going to install a. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. Configure the action to be taken when an attack is. How To Block Ddos Attack In Fortigate.
From www.youtube.com
How to block DDOS attack in the MikroTik router? YouTube How To Block Ddos Attack In Fortigate Tcp port 80 for a web server) that cannot be. In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. In kali, we are going to install a. Learn the steps to ddos mitigation and what to look for in a mitigation. Define the threshold values for various ddos. How To Block Ddos Attack In Fortigate.
From www.dnsstuff.com
How to Stop and Prevent DDoS Attack DNSstuff How To Block Ddos Attack In Fortigate In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy.. How To Block Ddos Attack In Fortigate.
From sdncommunications.com
Managed DDoS Protection SDN Communications How To Block Ddos Attack In Fortigate Certain protocols can be blocked by firewalls, but most dos attacks utilize authorized ports (e.g. In kali, we are going to install a. Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. In this lab, we are going to set a ddos prevention on traffic from port1 to port2. In a. How To Block Ddos Attack In Fortigate.
From docs.fortinet.com
How to block the ongoing DDoS attack Forti Cloud 24.1.0 How To Block Ddos Attack In Fortigate Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. This article describes how to block a specific host permanently after an attack traffic is detected by the ddos protection policy. Configure the action to be taken when an attack is detected, such as. Certain protocols can be blocked by firewalls, but. How To Block Ddos Attack In Fortigate.
From www.youtube.com
How To Stop DDOS Attack Using FortiGate Firewall Policy شرح بالعربي How To Block Ddos Attack In Fortigate In a dos (denial of service) / ddos (distributed denial of service) attack, the attacker / bad actor overwhelms the network. Define the threshold values for various ddos attack types, such as syn flood, udp flood, icmp flood, etc. Learn the steps to ddos mitigation and what to look for in a mitigation. A ddos mitigation strategy is necessary to. How To Block Ddos Attack In Fortigate.