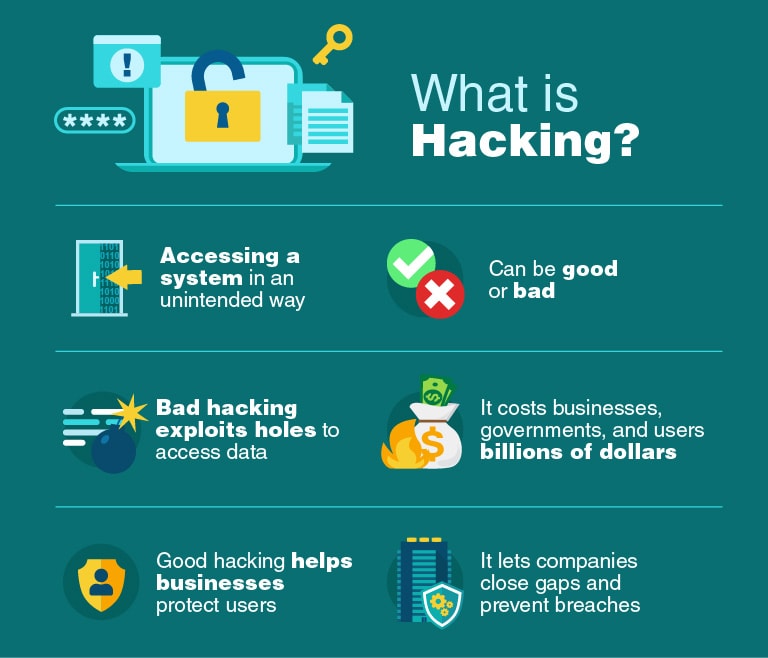
Hardware Requirements For Ethical Hacking . Ethical hacking is also known as “white hat” hacking or pentesting. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. It is the practice of using hacking techniques and tools to test the security of a computer system. What are the requirements for an ethical hacker’s laptop? This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. In general, a laptop for an ethical. There are a few requirements that a good laptop for pentesting should fulfill.
from scholarsark.com
What are the requirements for an ethical hacker’s laptop? It is the practice of using hacking techniques and tools to test the security of a computer system. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. Ethical hacking is also known as “white hat” hacking or pentesting. There are a few requirements that a good laptop for pentesting should fulfill. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. In general, a laptop for an ethical. This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring.
The Ultimate Guide to Ethical Hacking What You Need to Know in 2019
Hardware Requirements For Ethical Hacking What are the requirements for an ethical hacker’s laptop? Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. What are the requirements for an ethical hacker’s laptop? There are a few requirements that a good laptop for pentesting should fulfill. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. In general, a laptop for an ethical. This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. It is the practice of using hacking techniques and tools to test the security of a computer system. Ethical hacking is also known as “white hat” hacking or pentesting.
From www.slideserve.com
PPT ECCouncil’s Certified Ethical Hacker (CEH) PowerPoint Hardware Requirements For Ethical Hacking It is the practice of using hacking techniques and tools to test the security of a computer system. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. Ethical hacking is also known as “white hat” hacking or pentesting. What are the requirements for an ethical hacker’s laptop? Ethical hackers, on. Hardware Requirements For Ethical Hacking.
From www.infosectrain.com
Phases of Ethical Hacking InfosecTrain Hardware Requirements For Ethical Hacking Ethical hacking is also known as “white hat” hacking or pentesting. In general, a laptop for an ethical. There are a few requirements that a good laptop for pentesting should fulfill. What are the requirements for an ethical hacker’s laptop? It is the practice of using hacking techniques and tools to test the security of a computer system. To become. Hardware Requirements For Ethical Hacking.
From www.vrogue.co
Understanding Ethical Hacking Basics What Does An Eth vrogue.co Hardware Requirements For Ethical Hacking In general, a laptop for an ethical. What are the requirements for an ethical hacker’s laptop? It is the practice of using hacking techniques and tools to test the security of a computer system. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. There are a. Hardware Requirements For Ethical Hacking.
From scholarsark.com
The Ultimate Guide to Ethical Hacking What You Need to Know in 2019 Hardware Requirements For Ethical Hacking What are the requirements for an ethical hacker’s laptop? It is the practice of using hacking techniques and tools to test the security of a computer system. In general, a laptop for an ethical. This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and. Hardware Requirements For Ethical Hacking.
From www.educatorstechnology.com
What You Need to Know about Ethical Hacking Educational Technology Hardware Requirements For Ethical Hacking There are a few requirements that a good laptop for pentesting should fulfill. What are the requirements for an ethical hacker’s laptop? Ethical hacking is also known as “white hat” hacking or pentesting. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. In general, a laptop. Hardware Requirements For Ethical Hacking.
From www.slideshare.net
Skills Required for Ethical Hacking PDF Hardware Requirements For Ethical Hacking In general, a laptop for an ethical. This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. Ethical hacking is also known as “white hat” hacking or pentesting. It is the practice of using hacking techniques and tools to test the security of. Hardware Requirements For Ethical Hacking.
From www.eccouncil.org
Best Ethical Hacking Tools 100 Hacking Tools & Software Hardware Requirements For Ethical Hacking To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. It is the practice of using hacking techniques and tools to test the security. Hardware Requirements For Ethical Hacking.
From www.slideserve.com
PPT 5 Skills A Professional Ethical Hacker Required PowerPoint Hardware Requirements For Ethical Hacking It is the practice of using hacking techniques and tools to test the security of a computer system. In general, a laptop for an ethical. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. There are a few requirements that a good laptop for pentesting should fulfill. Ethical hacking is. Hardware Requirements For Ethical Hacking.
From www.techyv.com
Top 10 Ethical Hacking Tools Hardware Requirements For Ethical Hacking What are the requirements for an ethical hacker’s laptop? Ethical hacking is also known as “white hat” hacking or pentesting. It is the practice of using hacking techniques and tools to test the security of a computer system. In general, a laptop for an ethical. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify. Hardware Requirements For Ethical Hacking.
From hackr.io
How to an Ethical Hacker in 2023? [A Complete Guide] Hardware Requirements For Ethical Hacking This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. Ethical hacking is also known as “white hat” hacking or pentesting. What are the requirements for an ethical hacker’s laptop? There are a few requirements that a good laptop for pentesting should fulfill.. Hardware Requirements For Ethical Hacking.
From techjury.net
What Are The 5 Phases of Ethical Hacking? Hardware Requirements For Ethical Hacking There are a few requirements that a good laptop for pentesting should fulfill. In general, a laptop for an ethical. What are the requirements for an ethical hacker’s laptop? Ethical hacking is also known as “white hat” hacking or pentesting. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. It. Hardware Requirements For Ethical Hacking.
From www.youtube.com
Software and Hardware Requirements for Hacking Ethical Hacking System Hardware Requirements For Ethical Hacking To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. It is the practice of using hacking techniques and tools to test the security of a computer system. In general, a laptop for an ethical. This article guides readers on how to set up a home lab, covering considerations such as. Hardware Requirements For Ethical Hacking.
From rummageall.com
An Introduction To Ethical Hacking Types Of Hackers Hardware Requirements For Ethical Hacking This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. It is the practice of using hacking techniques and tools to test the security of a computer system. In general, a laptop for an ethical. What are the requirements for an ethical hacker’s. Hardware Requirements For Ethical Hacking.
From www.invensislearning.com
Phases of Ethical Hacking A Complete Guide to Ethical Hacking Process Hardware Requirements For Ethical Hacking Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. What are the requirements for an ethical hacker’s laptop? This article guides readers on how to set up. Hardware Requirements For Ethical Hacking.
From www.slideserve.com
PPT 5 Skills A Professional Ethical Hacker Required. PowerPoint Hardware Requirements For Ethical Hacking This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. There are a few requirements that a good laptop for pentesting should fulfill. In general, a laptop for an ethical. Ethical hackers, on the other hand, are security experts retained by organizations to. Hardware Requirements For Ethical Hacking.
From www.whizlabs.com
Certified Ethical Hacker Preparation Guide [2023] Hardware Requirements For Ethical Hacking It is the practice of using hacking techniques and tools to test the security of a computer system. Ethical hacking is also known as “white hat” hacking or pentesting. There are a few requirements that a good laptop for pentesting should fulfill. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh). Hardware Requirements For Ethical Hacking.
From matob.web.id
9 Best Laptops for Ethical Hacking in 2023 Complete Guide Matob Hardware Requirements For Ethical Hacking What are the requirements for an ethical hacker’s laptop? This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. There are a few requirements that a good laptop for pentesting should fulfill. Ethical hackers, on the other hand, are security experts retained by. Hardware Requirements For Ethical Hacking.
From www.youtube.com
Skills Required To an Ethical Hacker skills for ethical Hardware Requirements For Ethical Hacking There are a few requirements that a good laptop for pentesting should fulfill. Ethical hacking is also known as “white hat” hacking or pentesting. It is the practice of using hacking techniques and tools to test the security of a computer system. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh). Hardware Requirements For Ethical Hacking.
From www.slideserve.com
PPT 5 Skills A Professional Ethical Hacker Required. PowerPoint Hardware Requirements For Ethical Hacking To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. What are the requirements for an ethical hacker’s laptop? In general, a laptop for an ethical. It is the practice of using hacking techniques and tools to test the security of a computer system. Ethical hacking is also known as “white. Hardware Requirements For Ethical Hacking.
From www.youtube.com
System Requirements for Ethical Hacking [Hindi] CyberSec Geeks Hardware Requirements For Ethical Hacking Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. To become a certified ethical hacker, you must obtain a. Hardware Requirements For Ethical Hacking.
From www.youtube.com
Software and Hardware Requirements for Ethical Hacking YouTube Hardware Requirements For Ethical Hacking Ethical hacking is also known as “white hat” hacking or pentesting. It is the practice of using hacking techniques and tools to test the security of a computer system. What are the requirements for an ethical hacker’s laptop? In general, a laptop for an ethical. This article guides readers on how to set up a home lab, covering considerations such. Hardware Requirements For Ethical Hacking.
From www.slideshare.net
Ethical Hacking Hardware Requirements For Ethical Hacking To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. There are a few requirements that a good laptop for pentesting should fulfill. What are the requirements for. Hardware Requirements For Ethical Hacking.
From www.infosectrain.com
Phases of Ethical Hacking InfosecTrain Hardware Requirements For Ethical Hacking Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. In general, a laptop for an ethical. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. This article guides readers on how to set up a home. Hardware Requirements For Ethical Hacking.
From www.oneeducation.org.uk
Ethical Hacking One Education Hardware Requirements For Ethical Hacking In general, a laptop for an ethical. This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. Ethical hacking is also known as “white hat” hacking or pentesting. There are a few requirements that a good laptop for pentesting should fulfill. To become. Hardware Requirements For Ethical Hacking.
From www.cobalt.io
How Pentesting Differs from Ethical Hacking Cobalt Hardware Requirements For Ethical Hacking This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. It is the practice of using hacking techniques and tools. Hardware Requirements For Ethical Hacking.
From www.eccouncil.org
Ethical Hacking Basics Ethical Hacking Blogs & Articles ECCouncil Hardware Requirements For Ethical Hacking There are a few requirements that a good laptop for pentesting should fulfill. It is the practice of using hacking techniques and tools to test the security of a computer system. Ethical hacking is also known as “white hat” hacking or pentesting. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh). Hardware Requirements For Ethical Hacking.
From itexamsusa.blogspot.com
Ethical Hacking Career A Career Guideline For Ethical Hacker ♛ IT Hardware Requirements For Ethical Hacking Ethical hacking is also known as “white hat” hacking or pentesting. What are the requirements for an ethical hacker’s laptop? This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. It is the practice of using hacking techniques and tools to test the. Hardware Requirements For Ethical Hacking.
From techradix.in
Ethical Hacking Phases Techradix Technology Hardware Requirements For Ethical Hacking This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. It is the practice of using hacking techniques and tools to test the security. Hardware Requirements For Ethical Hacking.
From www.educba.com
Hardware Hacking Complete Guide to Hardware Hacking with Benifits Hardware Requirements For Ethical Hacking In general, a laptop for an ethical. This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines, selecting software tools, and ensuring. Ethical hacking is also known as “white hat” hacking or pentesting. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify. Hardware Requirements For Ethical Hacking.
From www.youtube.com
Introduction and Downloading Requirements Ethical Hacking 1 Hardware Requirements For Ethical Hacking Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. Ethical hacking is also known as “white hat” hacking or pentesting. In general, a laptop for an ethical. What are the requirements for an ethical hacker’s laptop? It is the practice of using hacking techniques and tools. Hardware Requirements For Ethical Hacking.
From www.youtube.com
Basic Requirements for Ethical Hacking. YouTube Hardware Requirements For Ethical Hacking To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. It is the practice of using hacking techniques and tools to test the security of a computer system. In general, a laptop for an ethical. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities. Hardware Requirements For Ethical Hacking.
From www.youtube.com
Ethical hacking demo session and system requirements. YouTube Hardware Requirements For Ethical Hacking Ethical hacking is also known as “white hat” hacking or pentesting. What are the requirements for an ethical hacker’s laptop? It is the practice of using hacking techniques and tools to test the security of a computer system. This article guides readers on how to set up a home lab, covering considerations such as choosing hardware, setting up virtual machines,. Hardware Requirements For Ethical Hacking.
From securitygladiators.com
The Ultimate Guide to the 21 Best Ethical Hacking Tools 2023 and Beyond Hardware Requirements For Ethical Hacking There are a few requirements that a good laptop for pentesting should fulfill. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. Ethical hacking is also known as “white hat” hacking or pentesting. This article guides readers on how to set up a home lab, covering. Hardware Requirements For Ethical Hacking.
From www.slideserve.com
PPT Everything you need to know about Ethical Hacking PowerPoint Hardware Requirements For Ethical Hacking What are the requirements for an ethical hacker’s laptop? To become a certified ethical hacker, you must obtain a certification such as the certified ethical hacker (ceh) credential. There are a few requirements that a good laptop for pentesting should fulfill. Ethical hacking is also known as “white hat” hacking or pentesting. This article guides readers on how to set. Hardware Requirements For Ethical Hacking.
From thecyphere.com
What Is Ethical Hacking? Working, Techniques And Jobs Cyphere Hardware Requirements For Ethical Hacking There are a few requirements that a good laptop for pentesting should fulfill. Ethical hackers, on the other hand, are security experts retained by organizations to proactively identify vulnerabilities before someone with ill intent discovers them. It is the practice of using hacking techniques and tools to test the security of a computer system. To become a certified ethical hacker,. Hardware Requirements For Ethical Hacking.