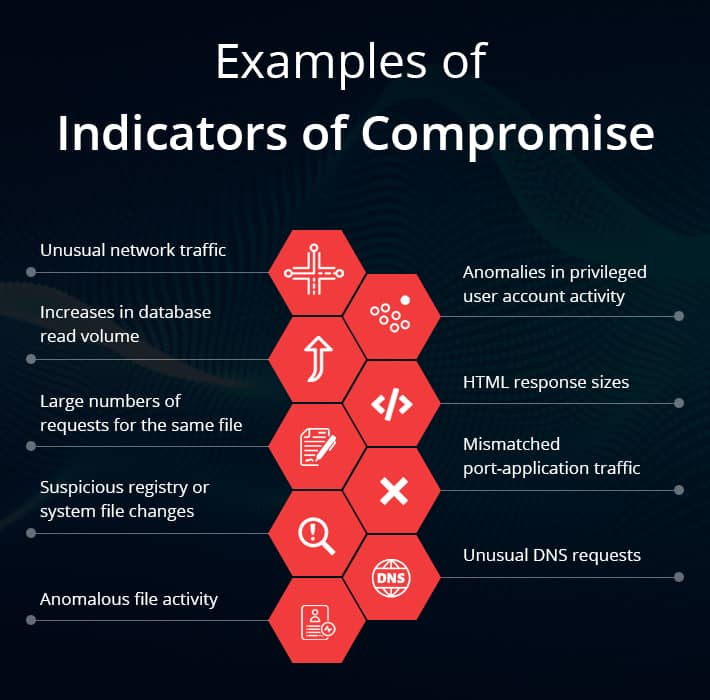
Indicators Of Compromise Applications . — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. They are types of forensic evidence that point to the. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked.
from www.lepide.com
— indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. This guide explores the types of. They are types of forensic evidence that point to the. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked.
What are Indicators of Compromise?
Indicators Of Compromise Applications — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. This guide explores the types of. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. They are types of forensic evidence that point to the. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a.
From www.youtube.com
What are the Indicators of compromise YouTube Indicators Of Compromise Applications This guide explores the types of. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. They are types of forensic evidence that point to the. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that. Indicators Of Compromise Applications.
From www.wallarm.com
What are Indicators of Compromise (IOC)? Indicators Of Compromise Applications an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. They are types of forensic evidence that point to the. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. — indicators of compromise are behaviors or data which show that. Indicators Of Compromise Applications.
From www.linkedin.com
The Importance and Difference Between Indicators of Attack and Indicators Of Compromise Applications indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. This guide explores the types of. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. Indicators Of Compromise Applications.
From arcticwolf.com
Understanding Indicators of Compromise I Arctic Wolf Indicators Of Compromise Applications indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of. They are types of forensic evidence that point to the. indicators of compromise (iocs) refer to. Indicators Of Compromise Applications.
From www.sekoia.io
What is an Indicator of Compromise (IoC)? SEKOIA.IO Indicators Of Compromise Applications indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. They are types of forensic evidence that point to the. This guide explores the types of. — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on. Indicators Of Compromise Applications.
From www.xcitium.com
What are Indicators of Compromise Security? IOC Meaning Indicators Of Compromise Applications indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. They are types of forensic evidence that point to the. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software. Indicators Of Compromise Applications.
From www.onlinesolutionsgroup.de
Indicators of Compromise (IoCs) ⏩ Online Marketing Glossar der OSG Indicators Of Compromise Applications This guide explores the types of. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or. Indicators Of Compromise Applications.
From www.trendmicro.com
Empowering the Analyst Indicators of Compromise Trend Micro (US) Indicators Of Compromise Applications indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. They are types of forensic evidence that point to the. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. indicators of compromise (iocs) are key to an organization’s. Indicators Of Compromise Applications.
From cyberhoot.com
Indicators of Compromise (IoC) CyberHoot Indicators Of Compromise Applications indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. — indicators of compromise. Indicators Of Compromise Applications.
From www.lepide.com
What are Indicators of Compromise? Indicators Of Compromise Applications — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. This guide explores the types of. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of. Indicators Of Compromise Applications.
From blog.threat.zone
Glossary Indicator of Compromise VS Indicator of Attack Indicators Of Compromise Applications indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. This guide explores the types of. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. They are. Indicators Of Compromise Applications.
From www.domaintools.com
Tools To Quickly Extract Indicators of Compromise DomainTools Start Indicators Of Compromise Applications indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. an. Indicators Of Compromise Applications.
From flare.io
What are Indicators of Compromise in Threat Intelligence? Flare Indicators Of Compromise Applications indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. This guide explores the types of. — indicators of compromise (iocs) are artifacts that indicate a. Indicators Of Compromise Applications.
From www.cyberwiki.in
Indicators of Compromise (IoCs) CyberWiki Encyclopedia of Cybersecurity Indicators Of Compromise Applications indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or. Indicators Of Compromise Applications.
From www.thesslstore.com
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed Indicators Of Compromise Applications indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. They are types of forensic evidence that point to the. — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. —. Indicators Of Compromise Applications.
From www.rstcloud.com
Public Database of 10M Indicators of Compromise RST Cloud Indicators Of Compromise Applications indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. They are types of forensic evidence that point to the. indicators of compromise (iocs) are key to an organization’s ability to. Indicators Of Compromise Applications.
From exobbptro.blob.core.windows.net
Indicator Of Compromise Sample at Arthur Carnes blog Indicators Of Compromise Applications indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. This guide explores the types of. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. They are types of forensic evidence that point to. Indicators Of Compromise Applications.
From www.lepide.com
What are Indicators of Compromise? Indicators Of Compromise Applications indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked.. Indicators Of Compromise Applications.
From www.packetlabs.net
What are Indicators of Compromise (IoCs)? Indicators Of Compromise Applications This guide explores the types of. indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. . Indicators Of Compromise Applications.
From www.sentinelone.com
What are Indicators of Compromise (IoCs)? An Easy Guide Indicators Of Compromise Applications — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. indicators of compromise (iocs) refer to. Indicators Of Compromise Applications.
From defensys.com
Indicators of compromise Lifecycle management Defensys Indicators Of Compromise Applications They are types of forensic evidence that point to the. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise (ioc) help organizations locate and confirm. Indicators Of Compromise Applications.
From www.semanticscholar.org
Table 1 from Digital Forensic Indicators of Compromise Format(DFIOC Indicators Of Compromise Applications indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. This guide explores the types of. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise (ioc) help organizations locate and confirm the. Indicators Of Compromise Applications.
From www.mdpi.com
Electronics Free FullText Key Requirements for the Detection and Indicators Of Compromise Applications indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. an indicator of. Indicators Of Compromise Applications.
From www.semanticscholar.org
Indicator of compromise Semantic Scholar Indicators Of Compromise Applications — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. This guide explores the types of. — indicators. Indicators Of Compromise Applications.
From www.linkedin.com
Indicators of Compromise (IOCs) Explained Indicators Of Compromise Applications indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of. They are types of forensic evidence that point to the. . Indicators Of Compromise Applications.
From exobbptro.blob.core.windows.net
Indicator Of Compromise Sample at Arthur Carnes blog Indicators Of Compromise Applications indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber. Indicators Of Compromise Applications.
From www.elastic.co
Indicators of compromise Elastic Security Solution [8.15] Elastic Indicators Of Compromise Applications an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. —. Indicators Of Compromise Applications.
From www.makeuseof.com
What Do the Indicators of Compromise Mean? The Best Tools to Help Indicators Of Compromise Applications an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. indicators of compromise (ioc) help organizations. Indicators Of Compromise Applications.
From www.teramind.co
10 Indicators of Compromise (IOC) Examples To Look Out For Indicators Of Compromise Applications — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (ioc) help organizations. Indicators Of Compromise Applications.
From www.linkedin.com
What are IT Security Indicators of Compromise? Indicators Of Compromise Applications They are types of forensic evidence that point to the. — indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) refer. Indicators Of Compromise Applications.
From www.semanticscholar.org
Table 1 from Understanding Indicators of Compromise against Cyber Indicators Of Compromise Applications They are types of forensic evidence that point to the. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. indicators of compromise (ioc) help organizations locate and. Indicators Of Compromise Applications.
From www.upguard.com
What are Indicators of Compromise (IOCs)? UpGuard Indicators Of Compromise Applications indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a.. Indicators Of Compromise Applications.
From attacksimulator.com
8 types of Indicators of Compromise (IoCs) and how to recognize them Indicators Of Compromise Applications This guide explores the types of. They are types of forensic evidence that point to the. indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. Indicators Of Compromise Applications.
From exchange.xforce.ibmcloud.com
IBM XForce Exchange Indicators Of Compromise Applications an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. They are types of forensic evidence that point to the. — indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber. Indicators Of Compromise Applications.
From dokumen.tips
(PDF) Automatic Extraction of Indicators of Compromise … Automatic Indicators Of Compromise Applications an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) are key to an organization’s ability to detect a cyberattack. indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a. — indicators of compromise (iocs) are artifacts that indicate. Indicators Of Compromise Applications.