Windows Account Impersonation . Learn how to grant the impersonation role to a service account by using the exchange management shell. I need to grant it permission to impersonate another account within a group on another trusted domain, without. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. Impersonation enables a caller, such as a. The impersonation level field indicates the extent to which a process in the logon session can impersonate. Internally, active directory (ad) uses several naming schemes for a given object. I have a windows service account.
from documentation.decisions.com
Impersonation enables a caller, such as a. Learn how to grant the impersonation role to a service account by using the exchange management shell. Internally, active directory (ad) uses several naming schemes for a given object. I need to grant it permission to impersonate another account within a group on another trusted domain, without. I have a windows service account. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. The impersonation level field indicates the extent to which a process in the logon session can impersonate.
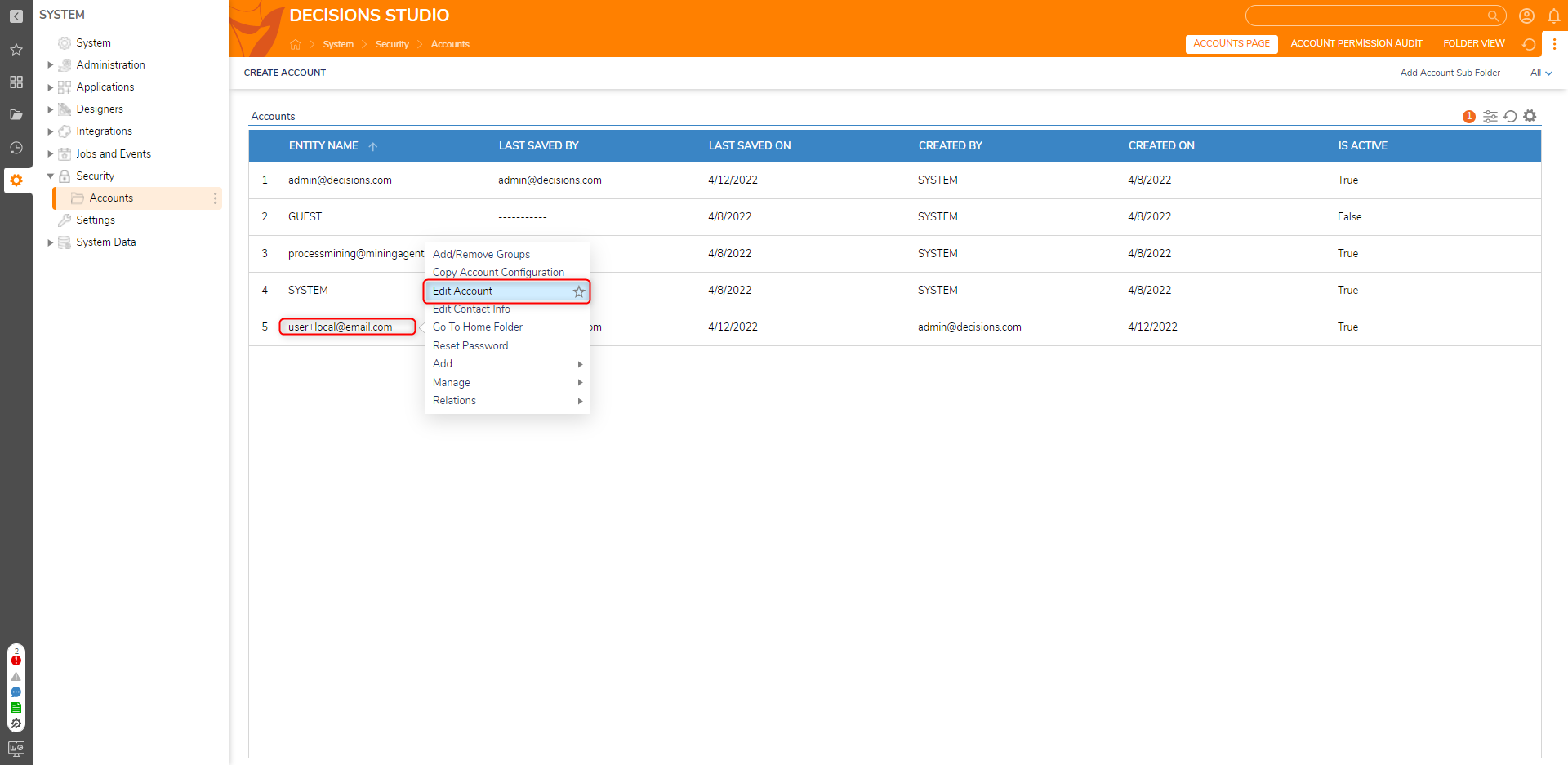
Account Impersonation Accounts & Groups
Windows Account Impersonation I need to grant it permission to impersonate another account within a group on another trusted domain, without. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. The impersonation level field indicates the extent to which a process in the logon session can impersonate. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. I need to grant it permission to impersonate another account within a group on another trusted domain, without. I have a windows service account. Impersonation enables a caller, such as a. Internally, active directory (ad) uses several naming schemes for a given object. Learn how to grant the impersonation role to a service account by using the exchange management shell.
From github.com
GitHub sensepost/impersonate A windows token impersonation tool Windows Account Impersonation Internally, active directory (ad) uses several naming schemes for a given object. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. I need to grant it permission to impersonate another account within a group on another trusted domain, without. Learn how to grant the. Windows Account Impersonation.
From github.com
Impersonate the security context of the Windows account · Issue 452 Windows Account Impersonation In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Learn how to grant the impersonation role to a service account by using the exchange management shell. The impersonation level field indicates the extent to which a process in the logon session can impersonate. Impersonation enables a caller,. Windows Account Impersonation.
From www.roelvanlisdonk.nl
Explaining SSRS datasource options “Use as Windows credentials when Windows Account Impersonation Internally, active directory (ad) uses several naming schemes for a given object. I have a windows service account. Learn how to grant the impersonation role to a service account by using the exchange management shell. I need to grant it permission to impersonate another account within a group on another trusted domain, without. Now, we’ll go over the two threat. Windows Account Impersonation.
From www.autodesk.com
Permissions for the Vault impersonation account are not consistent when Windows Account Impersonation Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. I have a windows service account. Internally, active directory (ad) uses several naming. Windows Account Impersonation.
From www.youtube.com
Databases Creating Linked Server Impersonation of Windows Windows Account Impersonation In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. I have a windows service account. The impersonation level field indicates the extent to which a process in the logon session can impersonate. Learn how to grant the impersonation role to a service account by using the exchange. Windows Account Impersonation.
From helpdesk.applicaa.com
How to impersonate an account? Windows Account Impersonation In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. I need to grant it permission to impersonate another account within a group on another trusted domain, without. I have a windows service account. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing. Windows Account Impersonation.
From www.autodesk.com
How to manage Vault impersonation account password Windows Account Impersonation In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Internally, active directory (ad) uses several naming schemes for a given object. Learn how to grant the impersonation role to a service account by using the exchange management shell. I need to grant it permission to impersonate another. Windows Account Impersonation.
From docs.revenuegrid.com
How to Create an Impersonating Email Account Revenue Grid Email Windows Account Impersonation I have a windows service account. I need to grant it permission to impersonate another account within a group on another trusted domain, without. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Impersonation enables a caller, such as a. The impersonation level field indicates the extent. Windows Account Impersonation.
From www.youtube.com
Token impersonation Active Directory Windows Privilege Escalation Windows Account Impersonation Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. Learn how to grant the impersonation role to a service account by using the exchange management shell. I need to grant it permission to impersonate another account within a group on another trusted domain, without.. Windows Account Impersonation.
From www.youtube.com
C Secure windows Impersonation? YouTube Windows Account Impersonation I need to grant it permission to impersonate another account within a group on another trusted domain, without. Learn how to grant the impersonation role to a service account by using the exchange management shell. Impersonation enables a caller, such as a. I have a windows service account. In situations where your application must impersonate a windows account that has. Windows Account Impersonation.
From documentation.decisions.com
Account Impersonation Accounts & Groups Windows Account Impersonation Internally, active directory (ad) uses several naming schemes for a given object. I have a windows service account. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Learn how to grant the impersonation role to a service account by using the exchange management shell. Impersonation enables a. Windows Account Impersonation.
From docs.oracle.com
Setting Up Microsoft Windows Impersonation Windows Account Impersonation I need to grant it permission to impersonate another account within a group on another trusted domain, without. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365. Windows Account Impersonation.
From help.synthesisplatform.net
SQL Server Logins or Using Windows Impersonation Windows Account Impersonation I have a windows service account. Internally, active directory (ad) uses several naming schemes for a given object. Learn how to grant the impersonation role to a service account by using the exchange management shell. The impersonation level field indicates the extent to which a process in the logon session can impersonate. Impersonation enables a caller, such as a. Now,. Windows Account Impersonation.
From help.synthesisplatform.net
SQL Server Logins or Using Windows Impersonation Windows Account Impersonation Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. I need to grant it permission to impersonate another account within a group. Windows Account Impersonation.
From documentation.decisions.com
Account Impersonation Accounts & Groups Windows Account Impersonation Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. I have a windows service account. I need to grant it permission to impersonate another account within a group on another trusted domain, without. In situations where your application must impersonate a windows account that. Windows Account Impersonation.
From docs.oracle.com
Setting Up Microsoft Windows Impersonation Windows Account Impersonation In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. I need to grant it permission to impersonate another account within a group on another trusted domain, without. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365. Windows Account Impersonation.
From help.synthesisplatform.net
SQL Server Logins or Using Windows Impersonation Windows Account Impersonation Impersonation enables a caller, such as a. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Internally, active directory (ad) uses several naming schemes for a given object. I need to grant it permission to impersonate another account within a group on another trusted domain, without. Now,. Windows Account Impersonation.
From 9to5answer.com
[Solved] Windows Impersonation from C 9to5Answer Windows Account Impersonation I need to grant it permission to impersonate another account within a group on another trusted domain, without. The impersonation level field indicates the extent to which a process in the logon session can impersonate. Learn how to grant the impersonation role to a service account by using the exchange management shell. Impersonation enables a caller, such as a. Now,. Windows Account Impersonation.
From www.youtube.com
Exposing Windows 7 JR/Windows Vista JR Impersonation, Hypocrisy Windows Account Impersonation Impersonation enables a caller, such as a. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. The impersonation level field indicates the extent to which a process in the logon session can impersonate. Learn how to grant the impersonation role to a service account by using the. Windows Account Impersonation.
From blog.nashtechglobal.com
Service Account IMPERSONAtion in GCP NashTech Insights Windows Account Impersonation Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. The impersonation level field indicates the extent to which a process in the. Windows Account Impersonation.
From help.clouduss.com
Configuring an Impersonation Account Help Unified Security Service Windows Account Impersonation Internally, active directory (ad) uses several naming schemes for a given object. I need to grant it permission to impersonate another account within a group on another trusted domain, without. Learn how to grant the impersonation role to a service account by using the exchange management shell. Now, we’ll go over the two threat vectors most commonly seen in phishing. Windows Account Impersonation.
From slideplayer.com
Passwordless Service Accounts ppt download Windows Account Impersonation Impersonation enables a caller, such as a. I have a windows service account. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. Internally, active directory (ad) uses several naming schemes for a given object. I need to grant it permission to impersonate another account. Windows Account Impersonation.
From serenity.is
Login (Impersonate) As User Serenity Guide Windows Account Impersonation Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. Internally, active directory (ad) uses several naming schemes for a given object. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. I. Windows Account Impersonation.
From docs.revenuegrid.com
Configure Impersonation for Office 365 Revenue Grid Knowledge Base Windows Account Impersonation I have a windows service account. Impersonation enables a caller, such as a. The impersonation level field indicates the extent to which a process in the logon session can impersonate. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. I need to grant it. Windows Account Impersonation.
From help.oneplacesolutions.com
Impersonation Account Windows Account Impersonation I have a windows service account. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Learn how to grant the impersonation role to a service account by using the exchange management shell. The impersonation level field indicates the extent to which a process in the logon session. Windows Account Impersonation.
From www.youtube.com
Windows How to impersonate a user from a service correctly? YouTube Windows Account Impersonation In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Impersonation enables a caller, such as a. Internally, active directory (ad) uses several naming schemes for a given object. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft. Windows Account Impersonation.
From www.youtube.com
Windows Temporarily impersonate the Windows authenticated user in ASP Windows Account Impersonation I have a windows service account. In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Impersonation enables a caller, such as a. Internally, active directory (ad) uses several naming schemes for a given object. The impersonation level field indicates the extent to which a process in the. Windows Account Impersonation.
From github.com
GitHub adxmax/windowsuserimpersonation win32api and win32con Windows Account Impersonation Impersonation enables a caller, such as a. I have a windows service account. Internally, active directory (ad) uses several naming schemes for a given object. Learn how to grant the impersonation role to a service account by using the exchange management shell. The impersonation level field indicates the extent to which a process in the logon session can impersonate. I. Windows Account Impersonation.
From helpdesk.applicaa.com
How to impersonate an account? Windows Account Impersonation In situations where your application must impersonate a windows account that has not been attached to the current thread by iis, you. Learn how to grant the impersonation role to a service account by using the exchange management shell. The impersonation level field indicates the extent to which a process in the logon session can impersonate. I have a windows. Windows Account Impersonation.
From www.youtube.com
Windows Using impersonation to launch processes (indirectly) in C Windows Account Impersonation Impersonation enables a caller, such as a. Internally, active directory (ad) uses several naming schemes for a given object. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them. In situations where your application must impersonate a windows account that has not been attached to. Windows Account Impersonation.
From help.reliasoft.com
SQL Server Logins or Using Windows Impersonation Windows Account Impersonation The impersonation level field indicates the extent to which a process in the logon session can impersonate. Impersonation enables a caller, such as a. I need to grant it permission to impersonate another account within a group on another trusted domain, without. Internally, active directory (ad) uses several naming schemes for a given object. I have a windows service account.. Windows Account Impersonation.
From documentation.decisions.com
Account Impersonation Accounts & Groups Windows Account Impersonation I have a windows service account. Learn how to grant the impersonation role to a service account by using the exchange management shell. The impersonation level field indicates the extent to which a process in the logon session can impersonate. In situations where your application must impersonate a windows account that has not been attached to the current thread by. Windows Account Impersonation.
From simplemedia.space
Windows 11 2022 Update security improvements Simple Media Windows Account Impersonation Internally, active directory (ad) uses several naming schemes for a given object. Impersonation enables a caller, such as a. The impersonation level field indicates the extent to which a process in the logon session can impersonate. I have a windows service account. Learn how to grant the impersonation role to a service account by using the exchange management shell. In. Windows Account Impersonation.
From documentation.decisions.com
Account Impersonation Accounts & Groups Windows Account Impersonation I need to grant it permission to impersonate another account within a group on another trusted domain, without. The impersonation level field indicates the extent to which a process in the logon session can impersonate. Now, we’ll go over the two threat vectors most commonly seen in phishing attacks—spoofing and impersonation, and how microsoft 365 protects your users against them.. Windows Account Impersonation.
From geekscripts.guru
PrintSpoofer Abusing Impersonation Privileges on Win10 and Server19 Windows Account Impersonation I need to grant it permission to impersonate another account within a group on another trusted domain, without. Impersonation enables a caller, such as a. Learn how to grant the impersonation role to a service account by using the exchange management shell. The impersonation level field indicates the extent to which a process in the logon session can impersonate. I. Windows Account Impersonation.