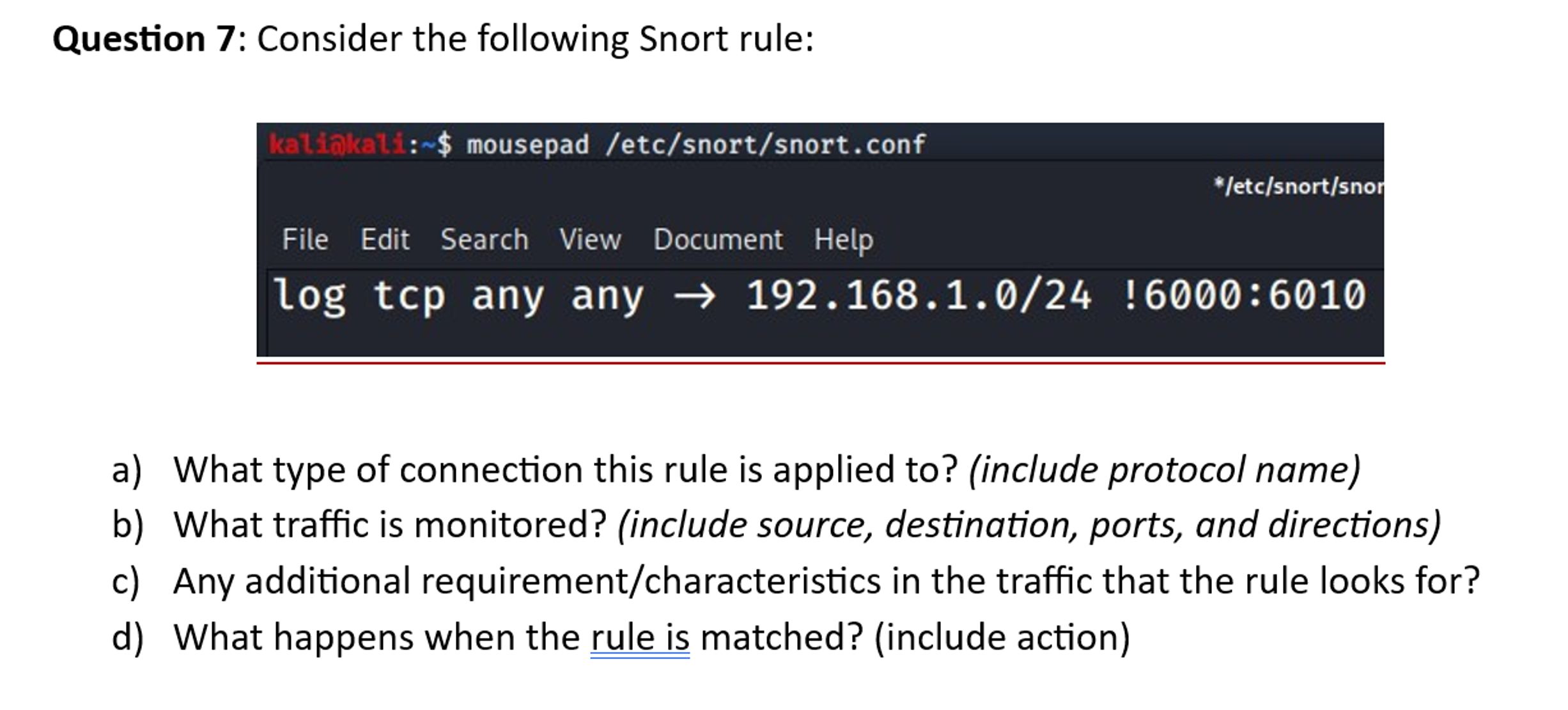
Snort Rule For Port Scanning . The syntax for a snort rule is: Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Common actions include alert, log,. Action proto source_ip source_port direction destination_ip destination_port (options) so you. Key components of a snort rule actions: Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. What should snort do when a rule is matched? Legitimate users on your network may employ similar port scanning techniques used by attackers. Learn various techniques for inspecting and analyzing network traffic using snort.
from www.chegg.com
Key components of a snort rule actions: The syntax for a snort rule is: What should snort do when a rule is matched? Action proto source_ip source_port direction destination_ip destination_port (options) so you. Legitimate users on your network may employ similar port scanning techniques used by attackers. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Common actions include alert, log,. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Learn various techniques for inspecting and analyzing network traffic using snort.
Solved Question 7 Consider the following Snort
Snort Rule For Port Scanning Learn various techniques for inspecting and analyzing network traffic using snort. Learn various techniques for inspecting and analyzing network traffic using snort. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Action proto source_ip source_port direction destination_ip destination_port (options) so you. Legitimate users on your network may employ similar port scanning techniques used by attackers. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Key components of a snort rule actions: Common actions include alert, log,. The syntax for a snort rule is: What should snort do when a rule is matched?
From www.slideserve.com
PPT Snort rules PowerPoint Presentation, free download ID4571858 Snort Rule For Port Scanning Learn various techniques for inspecting and analyzing network traffic using snort. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Key components of a snort rule actions: Legitimate users on your network may employ similar port scanning techniques used by attackers. What should snort do when a rule. Snort Rule For Port Scanning.
From www.securitybytes.in
Writing Snort rules with examples Snort Rule For Port Scanning Learn various techniques for inspecting and analyzing network traffic using snort. The syntax for a snort rule is: What should snort do when a rule is matched? Common actions include alert, log,. Legitimate users on your network may employ similar port scanning techniques used by attackers. Action proto source_ip source_port direction destination_ip destination_port (options) so you. Due to the flexibility. Snort Rule For Port Scanning.
From claroty.com
Blinding Snort IDS/IPS Breaking the Modbus OT Preprocessor Claroty Snort Rule For Port Scanning The syntax for a snort rule is: Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Learn various techniques for inspecting and analyzing network traffic using snort. Key components of a snort rule. Snort Rule For Port Scanning.
From www.youtube.com
Snort Rule Example YouTube Snort Rule For Port Scanning Action proto source_ip source_port direction destination_ip destination_port (options) so you. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. What should snort do when a rule is matched? Key components of a snort rule actions: Learn various techniques for inspecting and analyzing network traffic using snort. Legitimate users. Snort Rule For Port Scanning.
From stackoverflow.com
How to create a snort content rule Stack Overflow Snort Rule For Port Scanning Action proto source_ip source_port direction destination_ip destination_port (options) so you. Learn various techniques for inspecting and analyzing network traffic using snort. The syntax for a snort rule is: What should snort do when a rule is matched? Legitimate users on your network may employ similar port scanning techniques used by attackers. Key components of a snort rule actions: Identification of. Snort Rule For Port Scanning.
From cyvatar.ai
Writing snort rules Snort Rules Cheat Sheet and Examples CYVATAR.AI Snort Rule For Port Scanning Action proto source_ip source_port direction destination_ip destination_port (options) so you. Legitimate users on your network may employ similar port scanning techniques used by attackers. Learn various techniques for inspecting and analyzing network traffic using snort. Key components of a snort rule actions: Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of. Snort Rule For Port Scanning.
From www.slideserve.com
PPT Snort Rule PowerPoint Presentation, free download ID6369757 Snort Rule For Port Scanning Learn various techniques for inspecting and analyzing network traffic using snort. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Common actions include alert, log,. The syntax for a snort rule is: Action proto source_ip source_port direction destination_ip destination_port (options) so you. What should snort do when a rule is matched? Due to the. Snort Rule For Port Scanning.
From www.researchgate.net
Snort basic rule set [10, 11]. Download Scientific Diagram Snort Rule For Port Scanning Action proto source_ip source_port direction destination_ip destination_port (options) so you. What should snort do when a rule is matched? The syntax for a snort rule is: Legitimate users on your network may employ similar port scanning techniques used by attackers. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any. Snort Rule For Port Scanning.
From yourhelpershiv.blogspot.com
Why Port Scanning is considered "First line of cyber Attack"? Snort Rule For Port Scanning Common actions include alert, log,. What should snort do when a rule is matched? Legitimate users on your network may employ similar port scanning techniques used by attackers. The syntax for a snort rule is: Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Key components of a. Snort Rule For Port Scanning.
From www.comparitech.com
SNORT Cheat Sheet Downloadable JPG & PDF files Comparitech Snort Rule For Port Scanning Key components of a snort rule actions: Legitimate users on your network may employ similar port scanning techniques used by attackers. What should snort do when a rule is matched? Action proto source_ip source_port direction destination_ip destination_port (options) so you. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any. Snort Rule For Port Scanning.
From cyvatar.ai
Writing snort rules Snort Rules Cheat Sheet and Examples CYVATAR.AI Snort Rule For Port Scanning What should snort do when a rule is matched? Common actions include alert, log,. Legitimate users on your network may employ similar port scanning techniques used by attackers. Learn various techniques for inspecting and analyzing network traffic using snort. Action proto source_ip source_port direction destination_ip destination_port (options) so you. Identification of various port scanning techniques, including syn scans, fin scans,. Snort Rule For Port Scanning.
From security.stackexchange.com
Snort rule doesn't match the content in Meterpreter session packet Snort Rule For Port Scanning The syntax for a snort rule is: Legitimate users on your network may employ similar port scanning techniques used by attackers. Common actions include alert, log,. Key components of a snort rule actions: Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Due to the flexibility of the snort rule language and compatibility with. Snort Rule For Port Scanning.
From www.youtube.com
Snort detecting port scan YouTube Snort Rule For Port Scanning Key components of a snort rule actions: Action proto source_ip source_port direction destination_ip destination_port (options) so you. Legitimate users on your network may employ similar port scanning techniques used by attackers. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. What should snort do when a rule is matched? Learn various techniques for inspecting. Snort Rule For Port Scanning.
From www.slideserve.com
PPT SNORT PowerPoint Presentation, free download ID5482528 Snort Rule For Port Scanning Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Key components of a snort rule actions: Learn various techniques for inspecting and analyzing network traffic using snort. The syntax for a snort rule is: Common actions include alert, log,. What should snort do when a rule is matched? Due to the flexibility of the. Snort Rule For Port Scanning.
From slideplayer.com
Footprinting and Scanning ppt download Snort Rule For Port Scanning Legitimate users on your network may employ similar port scanning techniques used by attackers. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Key components of a snort rule actions: Action proto source_ip source_port direction destination_ip destination_port (options) so you. The syntax for a snort rule is: Common. Snort Rule For Port Scanning.
From www.semanticscholar.org
Figure 1 from RuleBased Network Intrusion Detection System for Port Snort Rule For Port Scanning The syntax for a snort rule is: Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Learn various techniques for inspecting and analyzing network traffic using snort. Legitimate users on your network may employ similar port scanning techniques used by attackers. Identification of various port scanning techniques, including. Snort Rule For Port Scanning.
From www.hackercoolmagazine.com
Port scanning techniques for beginners Hackercool Magazine Snort Rule For Port Scanning Legitimate users on your network may employ similar port scanning techniques used by attackers. Action proto source_ip source_port direction destination_ip destination_port (options) so you. Learn various techniques for inspecting and analyzing network traffic using snort. The syntax for a snort rule is: Common actions include alert, log,. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans,. Snort Rule For Port Scanning.
From www.slideserve.com
PPT SNORT PowerPoint Presentation, free download ID761514 Snort Rule For Port Scanning Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Learn various techniques for inspecting and analyzing network traffic using snort. Action proto source_ip source_port direction destination_ip destination_port (options) so you. The syntax for. Snort Rule For Port Scanning.
From www.youtube.com
Snort Rules ️ YouTube Snort Rule For Port Scanning Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Legitimate users on your network may employ similar port scanning techniques used by attackers. Common actions include alert, log,. What should snort do when. Snort Rule For Port Scanning.
From www.slideserve.com
PPT Snort rules PowerPoint Presentation, free download ID4571858 Snort Rule For Port Scanning What should snort do when a rule is matched? Key components of a snort rule actions: Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. The syntax for a snort rule is: Action proto source_ip source_port direction destination_ip destination_port (options) so you. Legitimate users on your network may employ similar port scanning techniques used. Snort Rule For Port Scanning.
From www.securitybytes.in
Writing Snort rules with examples Snort Rule For Port Scanning Legitimate users on your network may employ similar port scanning techniques used by attackers. Common actions include alert, log,. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Key components of a snort. Snort Rule For Port Scanning.
From www.securitybytes.in
Writing Snort rules with examples Snort Rule For Port Scanning Learn various techniques for inspecting and analyzing network traffic using snort. What should snort do when a rule is matched? Key components of a snort rule actions: Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Common actions include alert, log,. Identification of various port scanning techniques, including. Snort Rule For Port Scanning.
From www.slideserve.com
PPT Snort PowerPoint Presentation, free download ID519050 Snort Rule For Port Scanning Action proto source_ip source_port direction destination_ip destination_port (options) so you. The syntax for a snort rule is: Legitimate users on your network may employ similar port scanning techniques used by attackers. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. What should snort do when a rule is matched? Due to the flexibility of. Snort Rule For Port Scanning.
From ninocrudele.com
How to install Snort in Kali and any Linux container the quick way Snort Rule For Port Scanning Legitimate users on your network may employ similar port scanning techniques used by attackers. The syntax for a snort rule is: Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Action proto source_ip source_port direction destination_ip destination_port (options) so you. Common actions include alert, log,. Learn various techniques. Snort Rule For Port Scanning.
From www.thesecuritybuddy.com
A Guide To Port Scanning Using Nmap The Security Buddy Snort Rule For Port Scanning The syntax for a snort rule is: Common actions include alert, log,. Legitimate users on your network may employ similar port scanning techniques used by attackers. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. What should snort do when a rule is matched? Key components of a snort rule actions: Due to the. Snort Rule For Port Scanning.
From www.semanticscholar.org
Figure 4 from RuleBased Network Intrusion Detection System for Port Snort Rule For Port Scanning What should snort do when a rule is matched? Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Common actions include alert, log,. Learn various techniques for inspecting and analyzing network traffic using snort. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and. Snort Rule For Port Scanning.
From www.slideserve.com
PPT Intrusion Detection System (IDS) PowerPoint Presentation, free Snort Rule For Port Scanning The syntax for a snort rule is: Key components of a snort rule actions: What should snort do when a rule is matched? Action proto source_ip source_port direction destination_ip destination_port (options) so you. Common actions include alert, log,. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Learn various techniques for inspecting and analyzing. Snort Rule For Port Scanning.
From community.cisco.com
exempt specific Servers from a Snort Rule to avoid false positive Snort Rule For Port Scanning Action proto source_ip source_port direction destination_ip destination_port (options) so you. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Key components of a snort rule actions: Learn various techniques for inspecting and analyzing network traffic using snort. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable. Snort Rule For Port Scanning.
From www.researchgate.net
Port Scan Alerts generated by Snort are used as material for analysis Snort Rule For Port Scanning The syntax for a snort rule is: Action proto source_ip source_port direction destination_ip destination_port (options) so you. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Legitimate users on your network may employ similar port scanning techniques used by attackers. Key components of a snort rule actions: Learn various techniques for inspecting and analyzing. Snort Rule For Port Scanning.
From www.youtube.com
nids snort rules tutorial YouTube Snort Rule For Port Scanning Legitimate users on your network may employ similar port scanning techniques used by attackers. Key components of a snort rule actions: The syntax for a snort rule is: Common actions include alert, log,. What should snort do when a rule is matched? Action proto source_ip source_port direction destination_ip destination_port (options) so you. Due to the flexibility of the snort rule. Snort Rule For Port Scanning.
From www.slideshare.net
Introduction to Snort Rule Writing Snort Rule For Port Scanning Key components of a snort rule actions: Learn various techniques for inspecting and analyzing network traffic using snort. Action proto source_ip source_port direction destination_ip destination_port (options) so you. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. The syntax for a snort rule is: What should snort do when a rule is matched? Legitimate. Snort Rule For Port Scanning.
From www.slideserve.com
PPT An Introduction to Snort PowerPoint Presentation, free download Snort Rule For Port Scanning Common actions include alert, log,. Identification of various port scanning techniques, including syn scans, fin scans, xmas scans, and more. Action proto source_ip source_port direction destination_ip destination_port (options) so you. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Learn various techniques for inspecting and analyzing network traffic. Snort Rule For Port Scanning.
From www.chegg.com
Solved Question 7 Consider the following Snort Snort Rule For Port Scanning Key components of a snort rule actions: The syntax for a snort rule is: Legitimate users on your network may employ similar port scanning techniques used by attackers. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Identification of various port scanning techniques, including syn scans, fin scans,. Snort Rule For Port Scanning.
From cyvatar.ai
Writing snort rules Snort Rules Cheat Sheet and Examples CYVATAR.AI Snort Rule For Port Scanning The syntax for a snort rule is: Common actions include alert, log,. Legitimate users on your network may employ similar port scanning techniques used by attackers. Action proto source_ip source_port direction destination_ip destination_port (options) so you. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. Identification of various. Snort Rule For Port Scanning.
From www.slideserve.com
PPT An Introduction to Snort PowerPoint Presentation, free download Snort Rule For Port Scanning Action proto source_ip source_port direction destination_ip destination_port (options) so you. Due to the flexibility of the snort rule language and compatibility with all oses, snort is capable of detecting any network. What should snort do when a rule is matched? Common actions include alert, log,. Learn various techniques for inspecting and analyzing network traffic using snort. Identification of various port. Snort Rule For Port Scanning.