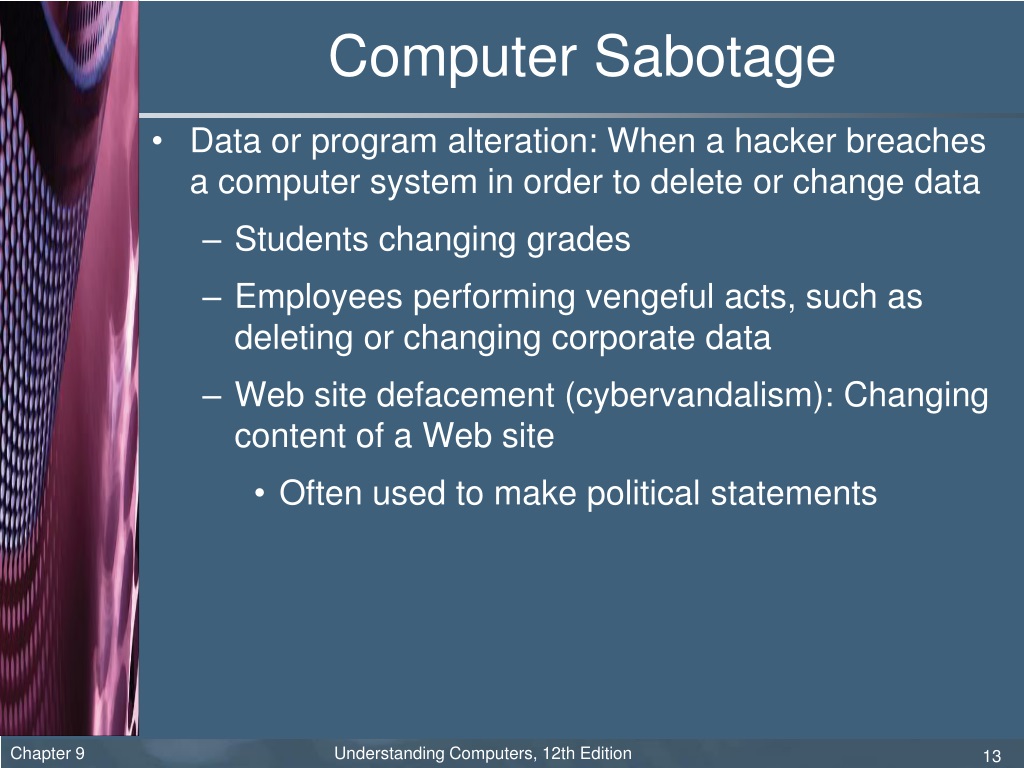
Computer Sabotages Example . With regard to computers, sabotage is the deliberate damage to equipment. Infecting a website with malware is an example of. They could involve the intentional destruction of systems or data. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. The risks to organizations go beyond data theft and leaks;
from www.slideserve.com
They could involve the intentional destruction of systems or data. Infecting a website with malware is an example of. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. The risks to organizations go beyond data theft and leaks; With regard to computers, sabotage is the deliberate damage to equipment. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some.
PPT Chapter 9 Network and Security PowerPoint Presentation
Computer Sabotages Example The risks to organizations go beyond data theft and leaks; With regard to computers, sabotage is the deliberate damage to equipment. The risks to organizations go beyond data theft and leaks; Infecting a website with malware is an example of. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. They could involve the intentional destruction of systems or data.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. They could involve the intentional destruction of systems or data. With regard to computers, sabotage is the deliberate damage to equipment. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation. Computer Sabotages Example.
From www.researchgate.net
(PDF) Insider Threat Study Computer System Sabotage in Critical Computer Sabotages Example Infecting a website with malware is an example of. They could involve the intentional destruction of systems or data. The risks to organizations go beyond data theft and leaks; With regard to computers, sabotage is the deliberate damage to equipment. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. Computer. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 4 Network and Security PowerPoint Presentation Computer Sabotages Example Infecting a website with malware is an example of. With regard to computers, sabotage is the deliberate damage to equipment. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. The risks to organizations go beyond data theft and leaks; They could involve the intentional destruction of systems. Computer Sabotages Example.
From slideplayer.com
Philip Nichilo Vincent Carestia ppt download Computer Sabotages Example This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. The risks to organizations go beyond data theft and leaks; Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. With regard to computers, sabotage is the deliberate damage. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example The risks to organizations go beyond data theft and leaks; Infecting a website with malware is an example of. They could involve the intentional destruction of systems or data. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. Computer sabotage involves deliberate attacks intended to disable computers or networks for. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. With regard to computers, sabotage is the deliberate damage to equipment. Infecting a website with malware is an example of. The risks to organizations go beyond data theft and leaks; They could involve the intentional destruction of systems or data. Computer. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example The risks to organizations go beyond data theft and leaks; They could involve the intentional destruction of systems or data. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. With regard to computers, sabotage is the deliberate damage to equipment. Computer sabotage involves deliberate attacks intended to disable computers or. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example Infecting a website with malware is an example of. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. With regard to computers, sabotage is the deliberate damage to equipment. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage. Computer Sabotages Example.
From www.insightsonindia.com
Meaning and Types of Cybersecurity Threats INSIGHTS IAS Simplifying Computer Sabotages Example Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. The risks to organizations go beyond data theft and leaks; They could involve the intentional destruction of systems or data. With regard to computers, sabotage is the deliberate damage to equipment. This report examines insider incidents across critical. Computer Sabotages Example.
From wirtschaftslexikon.gabler.de
Computersabotage • Definition Gabler Wirtschaftslexikon Computer Sabotages Example This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. The risks to organizations go beyond data theft and leaks; Infecting a website with malware is an example of. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal.. Computer Sabotages Example.
From www.slideserve.com
PPT Ethical Issues concerning CyberCrime PowerPoint Presentation Computer Sabotages Example Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. They could involve the intentional destruction of systems or data. The risks to organizations go beyond data theft and leaks; This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage. Computer Sabotages Example.
From www.quanswer.com
Provide several examples of computer sabotage? Quanswer Computer Sabotages Example They could involve the intentional destruction of systems or data. Infecting a website with malware is an example of. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some.. Computer Sabotages Example.
From slidetodoc.com
Cyber Security UNIT 1 UNIT 2 UNIT 3 Computer Sabotages Example With regard to computers, sabotage is the deliberate damage to equipment. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. Infecting a website with malware is an example of. They could involve the intentional destruction of systems or data. The risks to organizations go beyond data theft. Computer Sabotages Example.
From informationsecurityj.blogspot.com
Information Security Deliberate Act of Sabotage or Vandalism Computer Sabotages Example Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. With regard to computers, sabotage is the deliberate damage to equipment. The risks to organizations go beyond data theft and leaks; Infecting a website with malware is an example of. This report examines insider incidents across critical infrastructure. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example The risks to organizations go beyond data theft and leaks; Infecting a website with malware is an example of. They could involve the intentional destruction of systems or data. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. Computer sabotage involves deliberate attacks intended to disable computers or networks for. Computer Sabotages Example.
From www.itnews.com.au
Users sabotage work PCs to force upgrades Hardware Security iTnews Computer Sabotages Example With regard to computers, sabotage is the deliberate damage to equipment. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. They could involve the intentional destruction of systems or data. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example Infecting a website with malware is an example of. They could involve the intentional destruction of systems or data. With regard to computers, sabotage is the deliberate damage to equipment. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. This report examines insider incidents across critical infrastructure. Computer Sabotages Example.
From www.slideserve.com
PPT Network and Security PowerPoint Presentation, free Computer Sabotages Example Infecting a website with malware is an example of. They could involve the intentional destruction of systems or data. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. With regard to computers, sabotage is the deliberate damage to equipment. The risks to organizations go beyond data theft and leaks; Computer. Computer Sabotages Example.
From www.slideserve.com
PPT Network and Security PowerPoint Presentation, free Computer Sabotages Example The risks to organizations go beyond data theft and leaks; This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. With regard to computers, sabotage is the deliberate damage. Computer Sabotages Example.
From www.slideserve.com
PPT MORLEY Chapter 4 Network and Security PowerPoint Computer Sabotages Example Infecting a website with malware is an example of. With regard to computers, sabotage is the deliberate damage to equipment. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. The risks to organizations go beyond data theft and leaks; Computer sabotage involves deliberate attacks intended to disable computers or networks. Computer Sabotages Example.
From nordvpn.com
Software piracy types, examples, and risks NordVPN Computer Sabotages Example Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. With regard to computers, sabotage is the deliberate damage to equipment. Infecting a website with malware is an example. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example They could involve the intentional destruction of systems or data. With regard to computers, sabotage is the deliberate damage to equipment. Infecting a website with malware is an example of. The risks to organizations go beyond data theft and leaks; This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. Computer. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example The risks to organizations go beyond data theft and leaks; They could involve the intentional destruction of systems or data. Infecting a website with malware is an example of. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. Computer sabotage involves deliberate attacks intended to disable computers or networks for. Computer Sabotages Example.
From www.slideserve.com
PPT Definition of sabotage and how was it used in WWII PowerPoint Computer Sabotages Example This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. They could involve the intentional destruction of systems or data. With regard to computers, sabotage is the deliberate damage to equipment. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation. Computer Sabotages Example.
From www.youtube.com
Seven ways to sabotage a computer YouTube Computer Sabotages Example Infecting a website with malware is an example of. With regard to computers, sabotage is the deliberate damage to equipment. They could involve the intentional destruction of systems or data. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. The risks to organizations go beyond data theft. Computer Sabotages Example.
From www.dreamstime.com
Hackers Happy after Sabotaging Computers Stock Photo Image of malware Computer Sabotages Example Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. Infecting a website with malware is an example of. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. They could involve the intentional destruction of systems or data.. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example With regard to computers, sabotage is the deliberate damage to equipment. The risks to organizations go beyond data theft and leaks; Infecting a website with malware is an example of. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. They could involve the intentional destruction of systems or data. Computer. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example Infecting a website with malware is an example of. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. With regard to computers, sabotage is the deliberate damage to equipment. They could involve the intentional destruction of systems or data. Computer sabotage involves deliberate attacks intended to disable computers or networks. Computer Sabotages Example.
From www.goodlookgamer.com
Computer Sabotage Good Look Gamer Computer Sabotages Example The risks to organizations go beyond data theft and leaks; They could involve the intentional destruction of systems or data. Infecting a website with malware is an example of. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. This report examines insider incidents across critical infrastructure sectors. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example With regard to computers, sabotage is the deliberate damage to equipment. The risks to organizations go beyond data theft and leaks; This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation. Computer Sabotages Example.
From timlima-cyber.blogspot.com
Cyber Sabotage and Exortion Etika Profesi Teknologi Informasi Computer Sabotages Example Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. The risks to organizations go beyond data theft and leaks; With regard to computers, sabotage is the deliberate damage to equipment. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. With regard to computers, sabotage is the deliberate damage to equipment. This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. The risks to organizations go beyond data theft. Computer Sabotages Example.
From www.slideserve.com
PPT Introduction to Computer Security PowerPoint Presentation, free Computer Sabotages Example With regard to computers, sabotage is the deliberate damage to equipment. The risks to organizations go beyond data theft and leaks; Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. Infecting a website with malware is an example of. This report examines insider incidents across critical infrastructure. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example Infecting a website with malware is an example of. The risks to organizations go beyond data theft and leaks; They could involve the intentional destruction of systems or data. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. This report examines insider incidents across critical infrastructure sectors. Computer Sabotages Example.
From www.slideserve.com
PPT Chapter 9 Network and Security PowerPoint Presentation Computer Sabotages Example This report examines insider incidents across critical infrastructure sectors in which the insider’s primary goal was to sabotage some. They could involve the intentional destruction of systems or data. Computer sabotage involves deliberate attacks intended to disable computers or networks for the purpose of disrupting commerce, education and recreation for personal. With regard to computers, sabotage is the deliberate damage. Computer Sabotages Example.