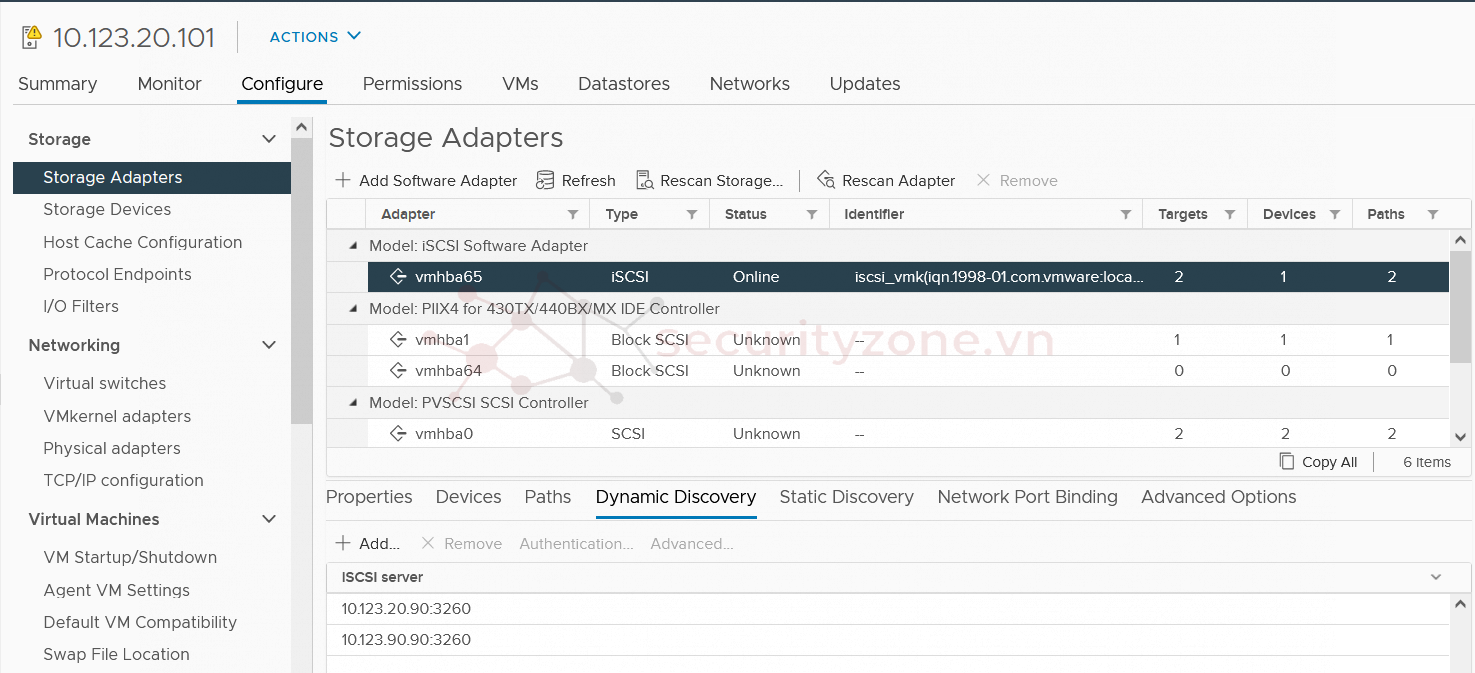
Which Security Technology Does Vmware Iscsi Use . Iscsi initiators on esxi hosts can use chap for authentication purposes. You can also take advantage of chap. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Follow best practices for storage security, as outlined by your storage security provider. Two chap authentication methods are available:
from securityzone.vn
You can also take advantage of chap. Follow best practices for storage security, as outlined by your storage security provider. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi initiators on esxi hosts can use chap for authentication purposes. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Two chap authentication methods are available:
Microsoft Cấu hình iSCSI Targets trên VMware ESXi Server với tính
Which Security Technology Does Vmware Iscsi Use Iscsi initiators on esxi hosts can use chap for authentication purposes. Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Follow best practices for storage security, as outlined by your storage security provider. Two chap authentication methods are available: You can also take advantage of chap.
From kb.synology.com
How to Use iSCSI Targets on VMware ESXi Server with Multipath Support Which Security Technology Does Vmware Iscsi Use Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Follow best practices for storage security, as outlined by your storage security provider. Two chap authentication methods are available: You can also take advantage of chap. Iscsi supports accessing scsi. Which Security Technology Does Vmware Iscsi Use.
From core.vmware.com
Best Practices For Running VMware vSphere On iSCSI VMware Which Security Technology Does Vmware Iscsi Use You can also take advantage of chap. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi initiators on esxi hosts can use chap for authentication purposes. Two chap authentication. Which Security Technology Does Vmware Iscsi Use.
From core.vmware.com
Introduction to Storage Virtualization VMware Which Security Technology Does Vmware Iscsi Use You can also take advantage of chap. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Follow best practices for storage security, as outlined by your storage security provider. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Two. Which Security Technology Does Vmware Iscsi Use.
From securityzone.vn
Microsoft Cấu hình iSCSI Targets trên VMware ESXi Server với tính Which Security Technology Does Vmware Iscsi Use Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Follow best practices for storage security, as outlined by your storage security provider. Two chap authentication methods are available: Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or. Which Security Technology Does Vmware Iscsi Use.
From kb.synology.com
How to Use iSCSI Targets on VMware ESXi Server with Multipath Support Which Security Technology Does Vmware Iscsi Use Two chap authentication methods are available: Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi initiators on esxi hosts can use chap for authentication purposes. You can also take. Which Security Technology Does Vmware Iscsi Use.
From www.cloud13.ch
A Closer Look at VMware NSX Security cloud13.ch Which Security Technology Does Vmware Iscsi Use To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Follow best practices for storage security, as outlined by your storage security provider. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Iscsi initiators on esxi hosts can use chap. Which Security Technology Does Vmware Iscsi Use.
From www.techtarget.com
What is iSCSI and How Does it Work? Which Security Technology Does Vmware Iscsi Use Iscsi initiators on esxi hosts can use chap for authentication purposes. Two chap authentication methods are available: To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. You can also take advantage of chap. Follow best practices for storage security, as outlined by your storage security provider. Iscsi supports accessing scsi. Which Security Technology Does Vmware Iscsi Use.
From www.youtube.com
Configuring iSCSI storage Add the iSCSI software adapter to an ESXi Which Security Technology Does Vmware Iscsi Use Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Two chap authentication methods are available: Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. You can also take. Which Security Technology Does Vmware Iscsi Use.
From cryptomonkeys.org
vSphere 5, iSCSI, and FreeNAS Cryptomonkeys UNIX/Security Consulting Which Security Technology Does Vmware Iscsi Use You can also take advantage of chap. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Follow best practices. Which Security Technology Does Vmware Iscsi Use.
From geek-university.com
iSCSI SAN components VMware ESXi Which Security Technology Does Vmware Iscsi Use To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. You can also take advantage of chap. Iscsi initiators on esxi hosts can use chap for authentication purposes. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Two chap authentication. Which Security Technology Does Vmware Iscsi Use.
From www.parkplacetechnologies.com
VMware vSphere vs. vCenter vs. ESXi Differences, Benefits & More Which Security Technology Does Vmware Iscsi Use Two chap authentication methods are available: You can also take advantage of chap. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Iscsi initiators on esxi hosts can use chap. Which Security Technology Does Vmware Iscsi Use.
From core.vmware.com
iSCSI Best Practice Resources VMware Which Security Technology Does Vmware Iscsi Use You can also take advantage of chap. Two chap authentication methods are available: Follow best practices for storage security, as outlined by your storage security provider. Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi supports accessing scsi. Which Security Technology Does Vmware Iscsi Use.
From geek-university.com
iSCSI initiators VMware ESXi Which Security Technology Does Vmware Iscsi Use You can also take advantage of chap. Iscsi initiators on esxi hosts can use chap for authentication purposes. Two chap authentication methods are available: To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than. Which Security Technology Does Vmware Iscsi Use.
From kb.synology.com
How to Use iSCSI Targets on VMware ESXi Server with Multipath Support Which Security Technology Does Vmware Iscsi Use Iscsi initiators on esxi hosts can use chap for authentication purposes. Two chap authentication methods are available: To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. You can also take advantage of chap. Follow best practices for storage security, as outlined by your storage security provider. Iscsi supports accessing scsi. Which Security Technology Does Vmware Iscsi Use.
From cryptomonkeys.org
vSphere 5, iSCSI, and FreeNAS Cryptomonkeys UNIX/Security Consulting Which Security Technology Does Vmware Iscsi Use To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi initiators on esxi hosts can use chap for authentication purposes. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Follow best practices for storage security, as outlined by your. Which Security Technology Does Vmware Iscsi Use.
From blogs.vmware.com
VMware NSX and Check Point vSEC Network and Security Virtualization Which Security Technology Does Vmware Iscsi Use To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Two chap authentication methods are available: Follow best practices for storage security, as outlined by your storage security provider. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. You can. Which Security Technology Does Vmware Iscsi Use.
From www.kernsafe.com
KernSafe iSCSI SAN for VMware ESX Storage Which Security Technology Does Vmware Iscsi Use Follow best practices for storage security, as outlined by your storage security provider. Iscsi initiators on esxi hosts can use chap for authentication purposes. You can also take advantage of chap. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. To secure iscsi devices, require that the esxi host,. Which Security Technology Does Vmware Iscsi Use.
From supertechman.com.au
VMware Security Best Practices Which Security Technology Does Vmware Iscsi Use Two chap authentication methods are available: Follow best practices for storage security, as outlined by your storage security provider. You can also take advantage of chap. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to. Which Security Technology Does Vmware Iscsi Use.
From aws.amazon.com
Integrating iSCSI Storage with VMware Cloud on AWS Virtual Machines Which Security Technology Does Vmware Iscsi Use Follow best practices for storage security, as outlined by your storage security provider. You can also take advantage of chap. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi. Which Security Technology Does Vmware Iscsi Use.
From alt64.se
VMware vSAN iSCSI use case? Virtual thoughts Which Security Technology Does Vmware Iscsi Use Iscsi initiators on esxi hosts can use chap for authentication purposes. Follow best practices for storage security, as outlined by your storage security provider. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Two chap authentication methods are available: You can also take advantage of chap. To secure iscsi. Which Security Technology Does Vmware Iscsi Use.
From www.itechguides.com
Configure VMware ESXi Servers to Share an iSCSI Storage Itechguides Which Security Technology Does Vmware Iscsi Use To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Follow best practices for storage security, as outlined by your storage security provider. Iscsi initiators on esxi hosts can use chap for authentication purposes. Two chap authentication methods are available: Iscsi supports accessing scsi devices and exchanging data by using tcp/ip. Which Security Technology Does Vmware Iscsi Use.
From geek-university.com
iSCSI target discovery VMware ESXi Which Security Technology Does Vmware Iscsi Use To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. You can also take advantage of chap. Two chap authentication methods are available: Iscsi initiators on esxi hosts can use chap. Which Security Technology Does Vmware Iscsi Use.
From kb.synology.com
How to Use iSCSI Targets on VMware ESXi Server with Multipath Support Which Security Technology Does Vmware Iscsi Use Follow best practices for storage security, as outlined by your storage security provider. Two chap authentication methods are available: To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. You can also take advantage of chap. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port. Which Security Technology Does Vmware Iscsi Use.
From www.server-world.info
VMware ESXi 8 Use iSCSI Storage Server World Which Security Technology Does Vmware Iscsi Use Follow best practices for storage security, as outlined by your storage security provider. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi. Which Security Technology Does Vmware Iscsi Use.
From dandkmotorsports.com
Iscsi Storage Vmware Workstation Dandk Organizer Which Security Technology Does Vmware Iscsi Use To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. You can also take advantage of chap. Two chap authentication methods are available: Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Follow best practices for storage security, as outlined. Which Security Technology Does Vmware Iscsi Use.
From cryptomonkeys.org
vSphere 5, iSCSI, and FreeNAS Cryptomonkeys UNIX/Security Consulting Which Security Technology Does Vmware Iscsi Use You can also take advantage of chap. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Two chap authentication methods are available: Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi. Which Security Technology Does Vmware Iscsi Use.
From www.oracle.com
Oracle ZFS Storage Appliance Settings iSCSI Protocol Which Security Technology Does Vmware Iscsi Use Follow best practices for storage security, as outlined by your storage security provider. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi initiators on esxi hosts can use chap. Which Security Technology Does Vmware Iscsi Use.
From www.techwrix.com
iSCSI Techwrix Which Security Technology Does Vmware Iscsi Use Follow best practices for storage security, as outlined by your storage security provider. Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Two chap authentication methods are available: Iscsi supports accessing scsi devices and exchanging data by using tcp/ip. Which Security Technology Does Vmware Iscsi Use.
From securityzone.vn
Microsoft Cấu hình iSCSI Targets trên VMware ESXi Server với tính Which Security Technology Does Vmware Iscsi Use Two chap authentication methods are available: Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Follow best practices for. Which Security Technology Does Vmware Iscsi Use.
From www.starwindsoftware.com
What is iSCSI and How Does it Work? Components and Benefits Which Security Technology Does Vmware Iscsi Use Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Follow best practices for storage security, as outlined by your storage security provider. You can also take advantage of chap. Two chap authentication methods are available: To secure iscsi devices, require that the esxi host, or initiator, can authenticate to. Which Security Technology Does Vmware Iscsi Use.
From blogs.vmware.com
What’s New with VMware vSAN 6.7 Virtual Blocks Blog Which Security Technology Does Vmware Iscsi Use Two chap authentication methods are available: Iscsi initiators on esxi hosts can use chap for authentication purposes. Follow best practices for storage security, as outlined by your storage security provider. You can also take advantage of chap. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. To secure iscsi. Which Security Technology Does Vmware Iscsi Use.
From kb.synology.com
How to Use iSCSI Targets on VMware ESXi Server with Multipath Support Which Security Technology Does Vmware Iscsi Use Follow best practices for storage security, as outlined by your storage security provider. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. You can also take advantage of chap. Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host,. Which Security Technology Does Vmware Iscsi Use.
From aws.amazon.com
Integrating iSCSI Storage with VMware Cloud on AWS Virtual Machines Which Security Technology Does Vmware Iscsi Use Follow best practices for storage security, as outlined by your storage security provider. You can also take advantage of chap. Iscsi initiators on esxi hosts can use chap for authentication purposes. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Two chap authentication methods are available: Iscsi supports accessing scsi. Which Security Technology Does Vmware Iscsi Use.
From www.techtarget.com
Use iSCSI storage for VMware to create a data store Which Security Technology Does Vmware Iscsi Use Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. You can also take advantage of chap. To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Two chap authentication methods are available: Iscsi initiators on esxi hosts can use chap. Which Security Technology Does Vmware Iscsi Use.
From www.techtarget.com
Use iSCSI storage for VMware to create a data store Which Security Technology Does Vmware Iscsi Use To secure iscsi devices, require that the esxi host, or initiator, can authenticate to the iscsi device, or target,. Iscsi supports accessing scsi devices and exchanging data by using tcp/ip over a network port rather than through a direct. Two chap authentication methods are available: Follow best practices for storage security, as outlined by your storage security provider. Iscsi initiators. Which Security Technology Does Vmware Iscsi Use.