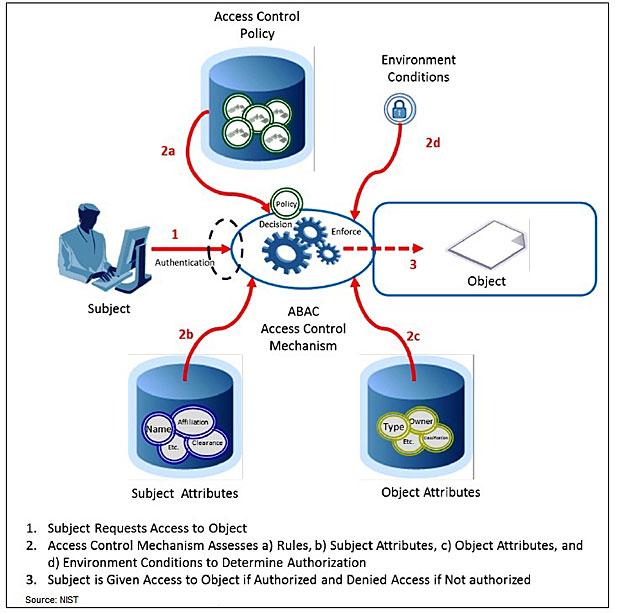
Access Control Policy Nist . organizations planning to implement an access control system should consider three abstractions: organizations planning to implement an access control system should consider three abstractions: To solve the interoperability and policy enforcement. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. section 1 states the purpose and scope of attributes used for access control systems. 4 (updated 1/07/22) describes the changes to each control and. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). policy machine and next generation access control.
from www.bankinfosecurity.com
section 1 states the purpose and scope of attributes used for access control systems. 4 (updated 1/07/22) describes the changes to each control and. organizations planning to implement an access control system should consider three abstractions: policy machine and next generation access control. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. To solve the interoperability and policy enforcement. organizations planning to implement an access control system should consider three abstractions:
NIST Guide Aims to Ease Access Control BankInfoSecurity
Access Control Policy Nist policy machine and next generation access control. policy machine and next generation access control. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). section 1 states the purpose and scope of attributes used for access control systems. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. organizations planning to implement an access control system should consider three abstractions: To solve the interoperability and policy enforcement. organizations planning to implement an access control system should consider three abstractions: 4 (updated 1/07/22) describes the changes to each control and.
From de.tenable.com
NIST 80053 Authentication and Access Control SC Dashboard Tenable® Access Control Policy Nist 4 (updated 1/07/22) describes the changes to each control and. section 1 states the purpose and scope of attributes used for access control systems. policy machine and next generation access control. organizations planning to implement an access control system should consider three abstractions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination.. Access Control Policy Nist.
From giociqrrr.blob.core.windows.net
Nist Access Control Policy at Nathan blog Access Control Policy Nist policy machine and next generation access control. section 1 states the purpose and scope of attributes used for access control systems. To solve the interoperability and policy enforcement. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). 4 (updated 1/07/22) describes the changes to each control and. organizations planning to implement. Access Control Policy Nist.
From templates.esad.edu.br
Nist 800171 Access Control Policy Template Access Control Policy Nist (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). organizations planning to implement an access control system should consider three abstractions: section 1 states the purpose and scope of attributes used for access control systems. To solve the interoperability and policy enforcement. 4 (updated 1/07/22) describes the changes to each control and.. Access Control Policy Nist.
From cashier.mijndomein.nl
Access Control Policy Template Nist Access Control Policy Nist section 1 states the purpose and scope of attributes used for access control systems. policy machine and next generation access control. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. organizations planning to implement an access control. Access Control Policy Nist.
From giociqrrr.blob.core.windows.net
Nist Access Control Policy at Nathan blog Access Control Policy Nist To solve the interoperability and policy enforcement. policy machine and next generation access control. organizations planning to implement an access control system should consider three abstractions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. 4 (updated 1/07/22) describes the changes to each control and. section 1 states the purpose and scope. Access Control Policy Nist.
From exyedhsog.blob.core.windows.net
Nist 800171 Access Control Policy at Lydia Valdez blog Access Control Policy Nist To solve the interoperability and policy enforcement. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). policy machine and next generation access control. organizations planning to implement an access control system should consider three abstractions: section 1 states the purpose and scope of attributes used for access control systems. an. Access Control Policy Nist.
From complianceforge.com
NIST 80053 R5 (moderate) Policy Template Access Control Policy Nist section 1 states the purpose and scope of attributes used for access control systems. To solve the interoperability and policy enforcement. organizations planning to implement an access control system should consider three abstractions: 4 (updated 1/07/22) describes the changes to each control and. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4).. Access Control Policy Nist.
From giociqrrr.blob.core.windows.net
Nist Access Control Policy at Nathan blog Access Control Policy Nist To solve the interoperability and policy enforcement. section 1 states the purpose and scope of attributes used for access control systems. organizations planning to implement an access control system should consider three abstractions: 4 (updated 1/07/22) describes the changes to each control and. policy machine and next generation access control. (1) restricted access to privileged funcons. Access Control Policy Nist.
From issecuritysolutions.com
Identity Access Control Policies NIST AC1 and IA1 Access Control Policy Nist 4 (updated 1/07/22) describes the changes to each control and. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). organizations planning to implement an access control system should consider three abstractions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. section 1 states the purpose and scope. Access Control Policy Nist.
From testsumus.oxfam.org
Nist 800 53 Access Control Policy Template Each Control Is Mapped To Access Control Policy Nist To solve the interoperability and policy enforcement. organizations planning to implement an access control system should consider three abstractions: policy machine and next generation access control. section 1 states the purpose and scope of attributes used for access control systems. 4 (updated 1/07/22) describes the changes to each control and. (1) restricted access to privileged funcons. Access Control Policy Nist.
From cashier.mijndomein.nl
Access Control Policy Template Nist Access Control Policy Nist 4 (updated 1/07/22) describes the changes to each control and. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). To solve the interoperability and policy enforcement. section 1 states the purpose and scope of attributes used for access control systems. organizations planning to implement an access control system should consider three abstractions:. Access Control Policy Nist.
From issecuritysolutions.com
Identity Access Control Policies NIST AC1 and IA1 Access Control Policy Nist 4 (updated 1/07/22) describes the changes to each control and. To solve the interoperability and policy enforcement. organizations planning to implement an access control system should consider three abstractions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). . Access Control Policy Nist.
From templates.rjuuc.edu.np
Nist Configuration Management Policy Template Access Control Policy Nist organizations planning to implement an access control system should consider three abstractions: policy machine and next generation access control. 4 (updated 1/07/22) describes the changes to each control and. organizations planning to implement an access control system should consider three abstractions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. (1). Access Control Policy Nist.
From ipkeys.com
Access Control Policy & Procedures Template [w/ Examples] Access Control Policy Nist an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. policy machine and next generation access control. section 1 states the purpose and scope of attributes used for access control systems. organizations planning to implement an access control system should consider three abstractions: organizations planning to implement an access control system should. Access Control Policy Nist.
From sprinto.com
An Ultimate Guide to NIST Access Controls Requirements Sprinto Access Control Policy Nist organizations planning to implement an access control system should consider three abstractions: (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). To solve the interoperability and policy enforcement. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. policy machine and next generation access control. organizations planning. Access Control Policy Nist.
From cashier.mijndomein.nl
Access Control Policy Template Nist Access Control Policy Nist 4 (updated 1/07/22) describes the changes to each control and. organizations planning to implement an access control system should consider three abstractions: (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). To solve the interoperability and policy enforcement. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. . Access Control Policy Nist.
From old.sermitsiaq.ag
Nist 800 53 Access Control Policy Template Access Control Policy Nist organizations planning to implement an access control system should consider three abstractions: section 1 states the purpose and scope of attributes used for access control systems. To solve the interoperability and policy enforcement. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). organizations planning to implement an access control system should. Access Control Policy Nist.
From www.bankinfosecurity.com
NIST Guide Aims to Ease Access Control BankInfoSecurity Access Control Policy Nist an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. policy machine and next generation access control. To solve the interoperability and policy enforcement. organizations planning to implement an access control system should consider three abstractions: section 1 states the purpose and scope of attributes used for access control systems. 4 (updated 1/07/22). Access Control Policy Nist.
From www.slideserve.com
PPT Automatic Construction and Validation of Access Control Policies Access Control Policy Nist an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. 4 (updated 1/07/22) describes the changes to each control and. organizations planning to implement an access control system should consider three abstractions: To solve the interoperability and policy enforcement. section 1 states the purpose and scope of attributes used for access control systems. . Access Control Policy Nist.
From stealthlabs.demolobby.com
What is NIST Compliance? Key Steps to NIST Compliant Access Control Policy Nist (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). organizations planning to implement an access control system should consider three abstractions: 4 (updated 1/07/22) describes the changes to each control and. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. section 1 states the purpose and scope. Access Control Policy Nist.
From www.goodreads.com
Verification and Test Methods for Access Control Policies/Models NIST Access Control Policy Nist section 1 states the purpose and scope of attributes used for access control systems. organizations planning to implement an access control system should consider three abstractions: 4 (updated 1/07/22) describes the changes to each control and. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). an access control policy that addresses. Access Control Policy Nist.
From www.nist.gov
Access Control System and Process for Managing and Enforcing an Access Control Policy Nist organizations planning to implement an access control system should consider three abstractions: 4 (updated 1/07/22) describes the changes to each control and. organizations planning to implement an access control system should consider three abstractions: policy machine and next generation access control. To solve the interoperability and policy enforcement. (1) restricted access to privileged funcons (2) dual. Access Control Policy Nist.
From cemle.com
Top 6 nist 80053 rev 4 control families 2022 Access Control Policy Nist organizations planning to implement an access control system should consider three abstractions: organizations planning to implement an access control system should consider three abstractions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). 4 (updated 1/07/22) describes the. Access Control Policy Nist.
From mavink.com
Nist Framework Overview Access Control Policy Nist organizations planning to implement an access control system should consider three abstractions: organizations planning to implement an access control system should consider three abstractions: 4 (updated 1/07/22) describes the changes to each control and. section 1 states the purpose and scope of attributes used for access control systems. (1) restricted access to privileged funcons (2) dual. Access Control Policy Nist.
From templates.rjuuc.edu.np
Nist 800 53 Ssp Template Access Control Policy Nist policy machine and next generation access control. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. section 1 states the purpose and scope of attributes used for access control systems. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). To solve the interoperability and policy enforcement. . Access Control Policy Nist.
From template.mapadapalavra.ba.gov.br
Nist 800171 Access Control Policy Template Access Control Policy Nist To solve the interoperability and policy enforcement. 4 (updated 1/07/22) describes the changes to each control and. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. section 1 states the purpose and scope of attributes used for access control systems. organizations planning to implement an access control system should consider three abstractions: . Access Control Policy Nist.
From tutore.org
Nist Sp 800 171 Compliance Template Access Control Policy Nist policy machine and next generation access control. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. 4 (updated 1/07/22) describes the changes to each control and. To solve the interoperability and policy enforcement. section 1 states the purpose and scope of attributes used for access control systems. organizations planning to implement an. Access Control Policy Nist.
From www.contrapositionmagazine.com
Nist 800 171 Access Control Policy Template Template 1 Resume Access Control Policy Nist section 1 states the purpose and scope of attributes used for access control systems. organizations planning to implement an access control system should consider three abstractions: 4 (updated 1/07/22) describes the changes to each control and. policy machine and next generation access control. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination.. Access Control Policy Nist.
From www.contrapositionmagazine.com
Nist 800 171 Access Control Policy Template Template 1 Resume Access Control Policy Nist (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). To solve the interoperability and policy enforcement. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. 4 (updated 1/07/22) describes the changes to each control and. section 1 states the purpose and scope of attributes used for access control. Access Control Policy Nist.
From www.nccoe.nist.gov
Identity and Access Management NIST SP 18002 Access Control Policy Nist (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). 4 (updated 1/07/22) describes the changes to each control and. organizations planning to implement an access control system should consider three abstractions: organizations planning to implement an access control system should consider three abstractions: section 1 states the purpose and scope of. Access Control Policy Nist.
From www.pinterest.co.uk
Explore Our Sample of Data Retention Policy Template Nist for Free Access Control Policy Nist To solve the interoperability and policy enforcement. 4 (updated 1/07/22) describes the changes to each control and. organizations planning to implement an access control system should consider three abstractions: organizations planning to implement an access control system should consider three abstractions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. (1) restricted. Access Control Policy Nist.
From www.youtube.com
AuditTrails NIST 80053 Series AC Control Family, AC1 ACCESS CONTROL Access Control Policy Nist (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. To solve the interoperability and policy enforcement. organizations planning to implement an access control system should consider three abstractions: policy machine and next generation access control. organizations planning. Access Control Policy Nist.
From templates.hilarious.edu.np
Nist 800171 Access Control Policy Template Access Control Policy Nist policy machine and next generation access control. 4 (updated 1/07/22) describes the changes to each control and. organizations planning to implement an access control system should consider three abstractions: an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4).. Access Control Policy Nist.
From www.enzoic.com
Surprising Password Guidelines from NIST Enzoic Access Control Policy Nist organizations planning to implement an access control system should consider three abstractions: policy machine and next generation access control. section 1 states the purpose and scope of attributes used for access control systems. 4 (updated 1/07/22) describes the changes to each control and. an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination.. Access Control Policy Nist.
From templates.rjuuc.edu.np
Nist 800 53 Access Control Policy Template Access Control Policy Nist organizations planning to implement an access control system should consider three abstractions: 4 (updated 1/07/22) describes the changes to each control and. policy machine and next generation access control. (1) restricted access to privileged funcons (2) dual authorizaon (3) mandatory access control (4). section 1 states the purpose and scope of attributes used for access control. Access Control Policy Nist.