Splunk Where Exists . This would then allow for much. With the where command, you must use the like function. | stats sum (val) as vals by value |. Use the percent ( % ) symbol as a wildcard for matching multiple characters. I'm filtering a search to get a result for a specific values by checking it manually this way: I would use the fillnull command (docs) to add a generic value to all empty values in this field. If you are more used to splunk spl search syntax, you could do it like this:. You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. | eval status=if(searchmatch(*connected*), 1, 0) Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch.
from docs.splunk.com
This would then allow for much. I would use the fillnull command (docs) to add a generic value to all empty values in this field. If you are more used to splunk spl search syntax, you could do it like this:. You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. | eval status=if(searchmatch(*connected*), 1, 0) | stats sum (val) as vals by value |. Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. I'm filtering a search to get a result for a specific values by checking it manually this way: With the where command, you must use the like function. Use the percent ( % ) symbol as a wildcard for matching multiple characters.
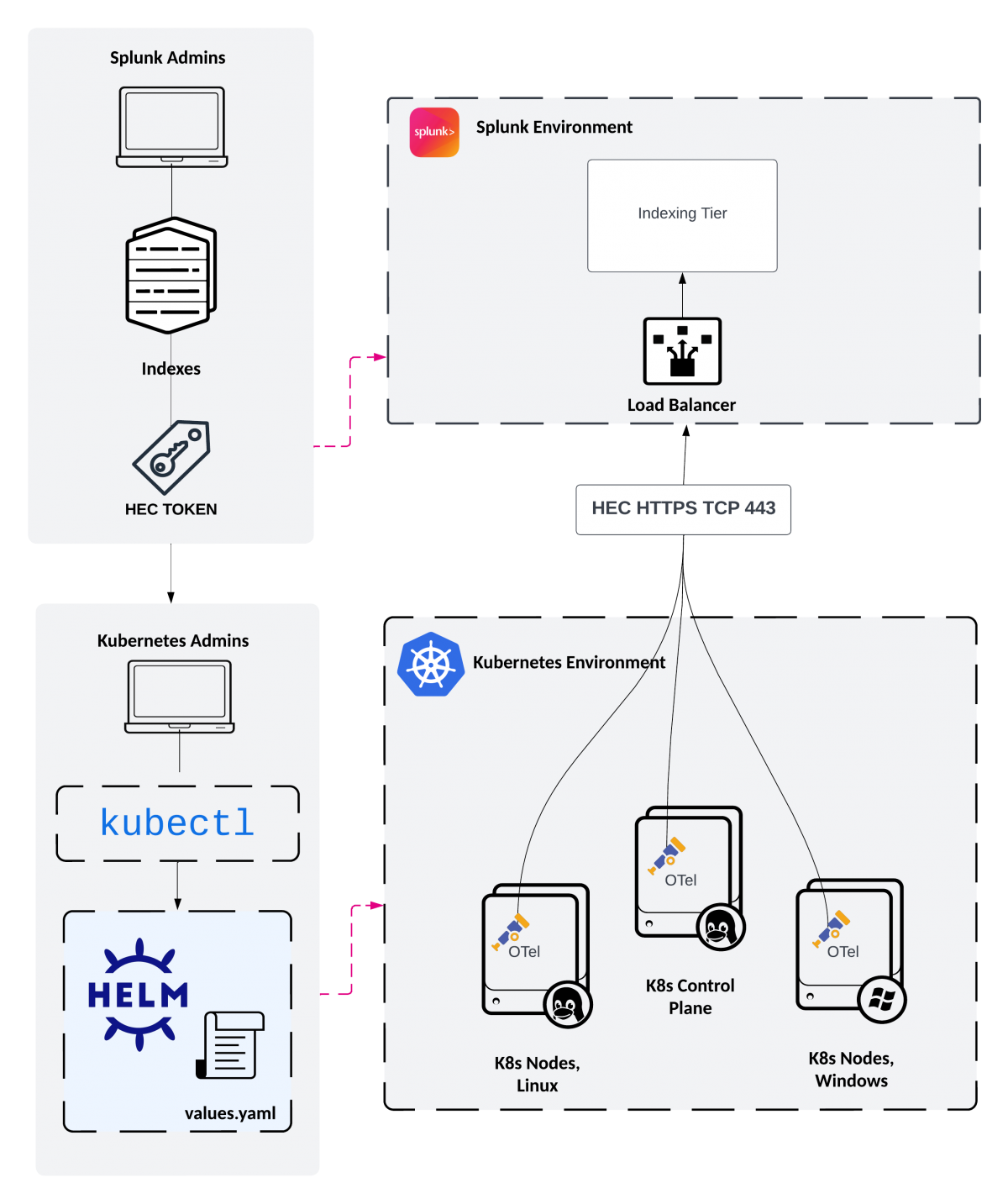
Splunk OpenTelemetry Collector for Splunk Documentation
Splunk Where Exists Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. I would use the fillnull command (docs) to add a generic value to all empty values in this field. With the where command, you must use the like function. If you are more used to splunk spl search syntax, you could do it like this:. I'm filtering a search to get a result for a specific values by checking it manually this way: | eval status=if(searchmatch(*connected*), 1, 0) Use the percent ( % ) symbol as a wildcard for matching multiple characters. Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. This would then allow for much. You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. | stats sum (val) as vals by value |.
From www.codecnetworks.com
What is Splunk Introduction, Architecture and Stages in Splunk Splunk Where Exists This would then allow for much. Use the percent ( % ) symbol as a wildcard for matching multiple characters. I'm filtering a search to get a result for a specific values by checking it manually this way: With the where command, you must use the like function. If you are more used to splunk spl search syntax, you could. Splunk Where Exists.
From docs.splunk.com
Splunk OpenTelemetry Collector for Splunk Documentation Splunk Where Exists This would then allow for much. I would use the fillnull command (docs) to add a generic value to all empty values in this field. I'm filtering a search to get a result for a specific values by checking it manually this way: | stats sum (val) as vals by value |. You can probably do this using a where. Splunk Where Exists.
From kinneygroup.com
Everything You Need To Know About Splunk Search Modes Kinney Group Splunk Where Exists Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. I would use the fillnull command (docs) to add a generic value to all empty values in this field. | stats sum (val) as vals by value |. Use the percent ( % ) symbol as a. Splunk Where Exists.
From devops.com
Splunk Unveils Unified Observability Platform Splunk Where Exists I would use the fillnull command (docs) to add a generic value to all empty values in this field. Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. Use the percent ( % ) symbol as a wildcard for matching multiple characters. This would then allow. Splunk Where Exists.
From docs.splunk.com
Basic searches and search results Splunk Documentation Splunk Where Exists I'm filtering a search to get a result for a specific values by checking it manually this way: Use the percent ( % ) symbol as a wildcard for matching multiple characters. If you are more used to splunk spl search syntax, you could do it like this:. With the where command, you must use the like function. | eval. Splunk Where Exists.
From daillyresource.blogspot.com
How to use Splunk SPL commands to write better queries Part I Splunk Where Exists I would use the fillnull command (docs) to add a generic value to all empty values in this field. This would then allow for much. Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. With the where command, you must use the like function. Use the. Splunk Where Exists.
From www.knowledgehut.com
What is Splunk? Features, Architecture, Pros and Cons Splunk Where Exists If you are more used to splunk spl search syntax, you could do it like this:. This would then allow for much. With the where command, you must use the like function. Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. Use the percent ( %. Splunk Where Exists.
From www.devopsschool.com
Analyzing Machine Data with Splunk Splunk Where Exists With the where command, you must use the like function. | eval status=if(searchmatch(*connected*), 1, 0) Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. | stats sum (val) as vals by value |. I would use the fillnull command (docs) to add a generic value to. Splunk Where Exists.
From innovation.co.id
Pengertian Splunk dan Segala Kegunannya Splunk Where Exists You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. If you are more used to splunk spl search syntax, you could do it like this:. I'm filtering a search to get a result for a specific values by checking it manually this way:. Splunk Where Exists.
From techbusinessintelligence.blogspot.com
techBI What is Splunk? Splunk Where Exists | stats sum (val) as vals by value |. You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. I'm filtering. Splunk Where Exists.
From www.edureka.co
Splunk Tutorial For Beginners Explore Machine Data Edureka Splunk Where Exists With the where command, you must use the like function. | stats sum (val) as vals by value |. I would use the fillnull command (docs) to add a generic value to all empty values in this field. Use the percent ( % ) symbol as a wildcard for matching multiple characters. | eval status=if(searchmatch(*connected*), 1, 0) You can probably. Splunk Where Exists.
From www.programmingcube.com
What is Splunk and What it is used for Programming Cube Splunk Where Exists With the where command, you must use the like function. If you are more used to splunk spl search syntax, you could do it like this:. | eval status=if(searchmatch(*connected*), 1, 0) Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. | stats sum (val) as vals. Splunk Where Exists.
From hurricanelabs.com
Understanding Splunk ES and Its Role in Cybersecurity Hurricane Labs Splunk Where Exists | eval status=if(searchmatch(*connected*), 1, 0) | stats sum (val) as vals by value |. I would use the fillnull command (docs) to add a generic value to all empty values in this field. You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. Use. Splunk Where Exists.
From docs.splunk.com
Basic searches and search results Splunk Documentation Splunk Where Exists With the where command, you must use the like function. This would then allow for much. Use the percent ( % ) symbol as a wildcard for matching multiple characters. You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. I'm filtering a search. Splunk Where Exists.
From kinneygroup.com
A Beginner's Guide to Splunk Logs Kinney Group Splunk Where Exists This would then allow for much. | eval status=if(searchmatch(*connected*), 1, 0) I would use the fillnull command (docs) to add a generic value to all empty values in this field. If you are more used to splunk spl search syntax, you could do it like this:. Use the percent ( % ) symbol as a wildcard for matching multiple characters.. Splunk Where Exists.
From velog.io
[splunk] Introducing Splunk and Splunk's Components Splunk Where Exists I'm filtering a search to get a result for a specific values by checking it manually this way: With the where command, you must use the like function. | eval status=if(searchmatch(*connected*), 1, 0) You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. Use. Splunk Where Exists.
From daillyresource.blogspot.com
How to use Splunk SPL commands to write better queries Part I Splunk Where Exists I would use the fillnull command (docs) to add a generic value to all empty values in this field. I'm filtering a search to get a result for a specific values by checking it manually this way: | eval status=if(searchmatch(*connected*), 1, 0) You can probably do this using a where clause after the search, as it's not possible to know. Splunk Where Exists.
From www.splunk.com
Top 5 Reasons Why Splunk Is the Ideal Platform for Unified Security and Splunk Where Exists With the where command, you must use the like function. | stats sum (val) as vals by value |. | eval status=if(searchmatch(*connected*), 1, 0) I'm filtering a search to get a result for a specific values by checking it manually this way: I would use the fillnull command (docs) to add a generic value to all empty values in this. Splunk Where Exists.
From securityboulevard.com
Code42 + Splunk A Panoramic View of the Insider Threat Landscape Splunk Where Exists With the where command, you must use the like function. You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. I'm filtering a search to get a result for a specific values by checking it manually this way: This would then allow for much.. Splunk Where Exists.
From www.socinvestigation.com
Splunk Architecture Forwarder, Indexer, And Search Head Security Splunk Where Exists Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. This would then allow for much. With the where command, you must use the like function. | eval status=if(searchmatch(*connected*), 1, 0) Use the percent ( % ) symbol as a wildcard for matching multiple characters. | stats. Splunk Where Exists.
From www.somerfordassociates.com
What is Splunk's Universal Forwarder? Somerford Associates Blog Splunk Where Exists Use the percent ( % ) symbol as a wildcard for matching multiple characters. If you are more used to splunk spl search syntax, you could do it like this:. I would use the fillnull command (docs) to add a generic value to all empty values in this field. This would then allow for much. You can probably do this. Splunk Where Exists.
From www.stratosphereips.org
Getting Started With Splunk Basic Searching & Data Viz — Stratosphere IPS Splunk Where Exists | eval status=if(searchmatch(*connected*), 1, 0) With the where command, you must use the like function. This would then allow for much. Use the percent ( % ) symbol as a wildcard for matching multiple characters. I'm filtering a search to get a result for a specific values by checking it manually this way: Use the exists operator to test if. Splunk Where Exists.
From queirozf.com
Splunk Examples Manipulating Text and Strings Splunk Where Exists With the where command, you must use the like function. Use the percent ( % ) symbol as a wildcard for matching multiple characters. Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. I'm filtering a search to get a result for a specific values by. Splunk Where Exists.
From hurricanelabs.com
Splunk SOAR Cyber Security A Comprehensive Overview Hurricane Labs Splunk Where Exists You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. This would then allow for much. I'm filtering a search to get a result for a specific values by checking it manually this way: | stats sum (val) as vals by value |. With. Splunk Where Exists.
From sematext.com
Datadog vs Splunk Comparison, key features, and overview Sematext Splunk Where Exists This would then allow for much. If you are more used to splunk spl search syntax, you could do it like this:. Use the percent ( % ) symbol as a wildcard for matching multiple characters. You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data,. Splunk Where Exists.
From logos-world.net
Splunk Logo, symbol, meaning, history, PNG, brand Splunk Where Exists This would then allow for much. I would use the fillnull command (docs) to add a generic value to all empty values in this field. | eval status=if(searchmatch(*connected*), 1, 0) With the where command, you must use the like function. Use the exists operator to test if an event in the main search dataset correlates with at least one event. Splunk Where Exists.
From intotheone.blogspot.com
Cyber Security Awareness Splunk Custom Search Command Searching for Splunk Where Exists | stats sum (val) as vals by value |. I would use the fillnull command (docs) to add a generic value to all empty values in this field. I'm filtering a search to get a result for a specific values by checking it manually this way: Use the exists operator to test if an event in the main search dataset. Splunk Where Exists.
From queirozf.com
Splunk Examples Manipulating Text and Strings Splunk Where Exists With the where command, you must use the like function. Use the percent ( % ) symbol as a wildcard for matching multiple characters. If you are more used to splunk spl search syntax, you could do it like this:. | eval status=if(searchmatch(*connected*), 1, 0) | stats sum (val) as vals by value |. I'm filtering a search to get. Splunk Where Exists.
From subscription.packtpub.com
What is Splunk? Splunk 7.x Quick Start Guide Splunk Where Exists I'm filtering a search to get a result for a specific values by checking it manually this way: With the where command, you must use the like function. | stats sum (val) as vals by value |. | eval status=if(searchmatch(*connected*), 1, 0) Use the exists operator to test if an event in the main search dataset correlates with at least. Splunk Where Exists.
From www.stationx.net
What Is Splunk Used For? (2024 Guide) Splunk Where Exists | stats sum (val) as vals by value |. Use the percent ( % ) symbol as a wildcard for matching multiple characters. This would then allow for much. I'm filtering a search to get a result for a specific values by checking it manually this way: You can probably do this using a where clause after the search, as. Splunk Where Exists.
From infohub.delltechnologies.com
What is Splunk? White Paper—Cloud Native Splunk Enterprise with Splunk Where Exists If you are more used to splunk spl search syntax, you could do it like this:. You can probably do this using a where clause after the search, as it's not possible to know in advance of seeing the data, if the. I would use the fillnull command (docs) to add a generic value to all empty values in this. Splunk Where Exists.
From www.stratosphereips.org
Getting Started With Splunk Basic Searching & Data Viz — Stratosphere IPS Splunk Where Exists Use the percent ( % ) symbol as a wildcard for matching multiple characters. Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. | stats sum (val) as vals by value |. You can probably do this using a where clause after the search, as it's. Splunk Where Exists.
From www.educba.com
What is Splunk? Basic Guide to Splunk Concept And Commands Splunk Where Exists Use the percent ( % ) symbol as a wildcard for matching multiple characters. This would then allow for much. I would use the fillnull command (docs) to add a generic value to all empty values in this field. | stats sum (val) as vals by value |. | eval status=if(searchmatch(*connected*), 1, 0) Use the exists operator to test if. Splunk Where Exists.
From docs.bugsnag.com
BugSnag docs › Product › Integrations › Data forwarding › Splunk Splunk Where Exists If you are more used to splunk spl search syntax, you could do it like this:. | stats sum (val) as vals by value |. With the where command, you must use the like function. This would then allow for much. | eval status=if(searchmatch(*connected*), 1, 0) Use the exists operator to test if an event in the main search dataset. Splunk Where Exists.
From www.youtube.com
Splunk Stats Command Tutorial YouTube Splunk Where Exists With the where command, you must use the like function. Use the exists operator to test if an event in the main search dataset correlates with at least one event in the subsearch. I'm filtering a search to get a result for a specific values by checking it manually this way: | eval status=if(searchmatch(*connected*), 1, 0) This would then allow. Splunk Where Exists.