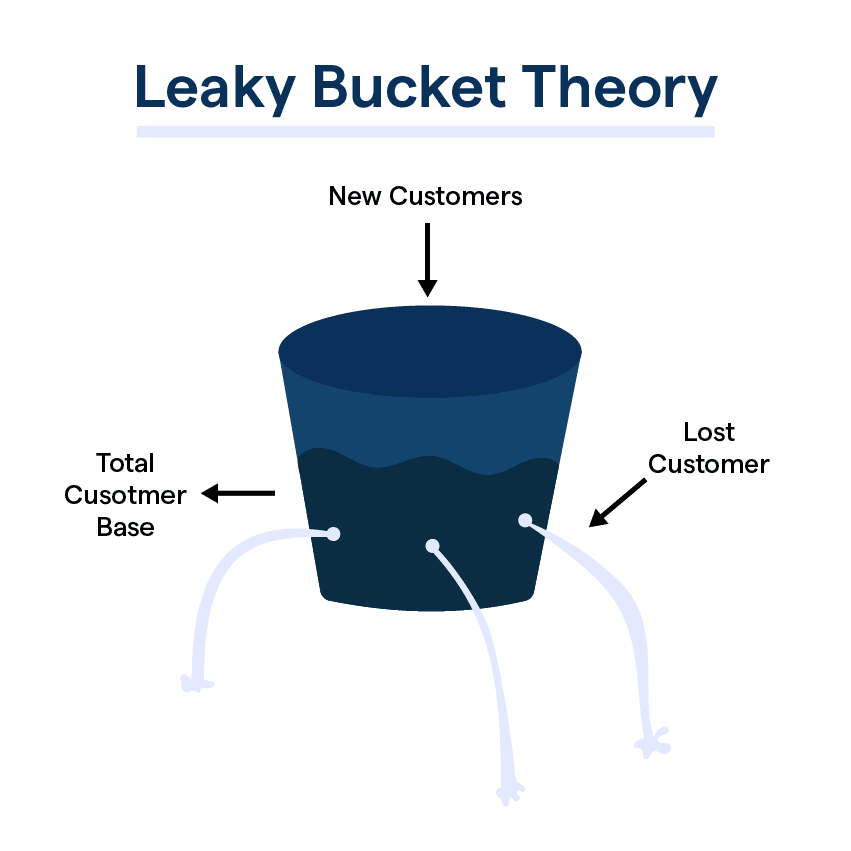
Leaky Bucket Algorithm Using C . The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. The other method is the leaky bucket algorithm. This is one of the algorithm used for congestion control in network layer. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Leaky bucket algorithm for congestion control. Picture a bucket with a. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. One can do very clever things using the leaky. If a packet arrives at. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. It is often used in scenarios where a constant.
from botpenguin.com
This is one of the algorithm used for congestion control in network layer. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Picture a bucket with a. Leaky bucket algorithm for congestion control. The other method is the leaky bucket algorithm. If a packet arrives at. One can do very clever things using the leaky. It is often used in scenarios where a constant.
What is Leaky Bucket Theory & its Applications?
Leaky Bucket Algorithm Using C It is often used in scenarios where a constant. The other method is the leaky bucket algorithm. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. This is one of the algorithm used for congestion control in network layer. It is often used in scenarios where a constant. Picture a bucket with a. Leaky bucket algorithm for congestion control. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. If a packet arrives at. One can do very clever things using the leaky. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. In class, we introduced the leaky bucket as a way to police the transmission rate of a session.
From www.semanticscholar.org
[PDF] Leaky Bucket Algorithm for Congestion Control Semantic Scholar Leaky Bucket Algorithm Using C The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. If a packet arrives at. Leaky bucket algorithm for congestion control. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. This is one of the algorithm. Leaky Bucket Algorithm Using C.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Algorithm Using C Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. Picture a bucket with a. The other method is the leaky bucket algorithm. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. The leaky bucket rate limiting algorithm utilizes. Leaky Bucket Algorithm Using C.
From www.youtube.com
12. Leaky Bucket Algorithm Program VTU 5th Sem Computer Network Lab Leaky Bucket Algorithm Using C The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. One can do very clever things using the leaky. This is one of the algorithm used for congestion control in network layer. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. The leaky bucket algorithm. Leaky Bucket Algorithm Using C.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Using C This is one of the algorithm used for congestion control in network layer. Picture a bucket with a. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. If a packet arrives at. Leaky bucket algorithm for congestion control. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate. Leaky Bucket Algorithm Using C.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Leaky Bucket Algorithm Using C In class, we introduced the leaky bucket as a way to police the transmission rate of a session. The other method is the leaky bucket algorithm. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. It is often used in scenarios where a constant. This is one of the. Leaky Bucket Algorithm Using C.
From dev.to
Rate Limiter in System Design. Part 2 Commonly Used Algorithms DEV Leaky Bucket Algorithm Using C Leaky bucket algorithm for congestion control. It is often used in scenarios where a constant. Picture a bucket with a. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. In class, we introduced the leaky. Leaky Bucket Algorithm Using C.
From www.youtube.com
Program 11 C/C++ Program for Congestion control using Leaky Bucket Leaky Bucket Algorithm Using C Leaky bucket algorithm for congestion control. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. The other method is the leaky bucket algorithm. One can do very clever things using the leaky. It is often. Leaky Bucket Algorithm Using C.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Algorithm Using C If a packet arrives at. This is one of the algorithm used for congestion control in network layer. It is often used in scenarios where a constant. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. The other method is the leaky bucket algorithm. The leaky bucket rate limiting algorithm utilizes. Leaky Bucket Algorithm Using C.
From github.com
GitHub ShreyaRao09/LeakyBucketAlgorithmImplementation A Computer Leaky Bucket Algorithm Using C Leaky bucket algorithm for congestion control. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. The other method is the leaky bucket algorithm. One can do very clever things using the leaky. If a packet arrives at. Picture a bucket. Leaky Bucket Algorithm Using C.
From www.transtutors.com
(Solved) Leaky Bucket Algorithm Complete The Following Table Using Leaky Bucket Algorithm Using C This is one of the algorithm used for congestion control in network layer. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite. Leaky Bucket Algorithm Using C.
From www.youtube.com
Congestion Control using Traffic Shaping in TCP, Leaky Bucket Algorithm Leaky Bucket Algorithm Using C One can do very clever things using the leaky. It is often used in scenarios where a constant. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. Picture a bucket with a. Leaky bucket algorithm for congestion control. This is one of the algorithm used for congestion control in network layer.. Leaky Bucket Algorithm Using C.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm Using C Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. This is one of the algorithm used for congestion control in network layer. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out). Leaky Bucket Algorithm Using C.
From www.scaler.com
Quality of Service in Computer Networks (QoS) Scaler Topics Leaky Bucket Algorithm Using C Picture a bucket with a. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. If a packet arrives at. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. It is often used in scenarios where a constant. Leaky bucket algorithm. Leaky Bucket Algorithm Using C.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Using C The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Picture a bucket with a. It is often used in scenarios where a constant. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. This is one of the algorithm used for congestion control in network. Leaky Bucket Algorithm Using C.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Using C Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. One can do very clever things using the leaky. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. This is one of the algorithm used for congestion control in network layer.. Leaky Bucket Algorithm Using C.
From www.code4it.dev
Davide's Code and Architecture Notes 4 algorithms to implement Rate Leaky Bucket Algorithm Using C Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. Leaky bucket algorithm for congestion control. If a packet arrives at. This is one of the algorithm used for congestion control in network layer. One can do very clever things using the leaky. The other method is the leaky bucket. Leaky Bucket Algorithm Using C.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID3009018 Leaky Bucket Algorithm Using C Picture a bucket with a. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. It is often used in scenarios where a constant. Leaky bucket algorithm for congestion control. This is. Leaky Bucket Algorithm Using C.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Using C The other method is the leaky bucket algorithm. This is one of the algorithm used for congestion control in network layer. Leaky bucket algorithm for congestion control. Picture a bucket with a. If a packet arrives at. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring. Leaky Bucket Algorithm Using C.
From www.scribd.com
Leaky Bucket algorithm PDF Leaky Bucket Algorithm Using C Picture a bucket with a. This is one of the algorithm used for congestion control in network layer. Leaky bucket algorithm for congestion control. The other method is the leaky bucket algorithm. It is often used in scenarios where a constant. If a packet arrives at. One can do very clever things using the leaky. In class, we introduced the. Leaky Bucket Algorithm Using C.
From www.youtube.com
Leaky bucket algorithm YouTube Leaky Bucket Algorithm Using C One can do very clever things using the leaky. Leaky bucket algorithm for congestion control. The other method is the leaky bucket algorithm. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. This is one of the algorithm used for. Leaky Bucket Algorithm Using C.
From vtucselabs.blogspot.com
VTU CSE LABS CN 12 LEAKY BUCKET ALGORITHM Leaky Bucket Algorithm Using C In class, we introduced the leaky bucket as a way to police the transmission rate of a session. Picture a bucket with a. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. This is one of the algorithm used for congestion control in network layer. It is often used. Leaky Bucket Algorithm Using C.
From www.slideserve.com
PPT Lecture 14 Distributed Multimedia Systems PowerPoint Leaky Bucket Algorithm Using C This is one of the algorithm used for congestion control in network layer. If a packet arrives at. Picture a bucket with a. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. One can do very clever. Leaky Bucket Algorithm Using C.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Leaky Bucket Algorithm Using C The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. This is one of the algorithm used for congestion control in network layer. One can do very clever things using the leaky. Leaky bucket algorithm for congestion control. In class, we introduced the leaky bucket as a way to police the transmission rate of a session.. Leaky Bucket Algorithm Using C.
From www.slideserve.com
PPT College of software,Zhejiang University of Technology PowerPoint Leaky Bucket Algorithm Using C In class, we introduced the leaky bucket as a way to police the transmission rate of a session. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. If a packet arrives at. Each host is connected to the network by an interface containing a leaky bucket, that is, a. Leaky Bucket Algorithm Using C.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Using C The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. One can do very clever things using the leaky. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. The other. Leaky Bucket Algorithm Using C.
From slideplayer.com
Introduction to Computer Networks ppt download Leaky Bucket Algorithm Using C One can do very clever things using the leaky. This is one of the algorithm used for congestion control in network layer. Leaky bucket algorithm for congestion control. Picture a bucket with a. It is often used in scenarios where a constant. In class, we introduced the leaky bucket as a way to police the transmission rate of a session.. Leaky Bucket Algorithm Using C.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Using C Picture a bucket with a. It is often used in scenarios where a constant. One can do very clever things using the leaky. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal. Leaky Bucket Algorithm Using C.
From www.scribd.com
Congestion Control Using Leaky Bucket Algorithm PDF Network Leaky Bucket Algorithm Using C The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Leaky bucket algorithm for congestion control. It is often used in scenarios where a constant. If a packet arrives at. The other method is the leaky bucket algorithm. This is one of the algorithm used for congestion control in network layer. The leaky bucket algorithm is. Leaky Bucket Algorithm Using C.
From www.slideserve.com
PPT Quality of Service Support PowerPoint Presentation, free download Leaky Bucket Algorithm Using C The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. This is one of the algorithm used for congestion control in network layer. It is often used in scenarios where a constant. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. The leaky bucket algorithm. Leaky Bucket Algorithm Using C.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID3009018 Leaky Bucket Algorithm Using C Leaky bucket algorithm for congestion control. Picture a bucket with a. The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. This is one of the algorithm used for congestion control in network layer. Each host is connected to the network. Leaky Bucket Algorithm Using C.
From www.youtube.com
6th network labPart Bprogram 6 congestion control using Leaky Bucket Algorithm Using C The leaky bucket rate limiting algorithm utilizes a fifo (first in, first out) queue with a fixed capacity to manage request rates, ensuring that requests are processed at a. This is one of the algorithm used for congestion control in network layer. Picture a bucket with a. If a packet arrives at. The leaky bucket algorithm is a simple yet. Leaky Bucket Algorithm Using C.
From www.slideserve.com
PPT Lecture 10 PowerPoint Presentation, free download ID4737649 Leaky Bucket Algorithm Using C The other method is the leaky bucket algorithm. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. Leaky bucket algorithm for congestion control. Picture a bucket with a. It is often used in scenarios where a constant. One can do very clever things using the leaky. The leaky bucket algorithm provides. Leaky Bucket Algorithm Using C.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID569119 Leaky Bucket Algorithm Using C The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. The other method is the leaky bucket algorithm. Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. Leaky bucket algorithm for congestion control. If a packet arrives at. The. Leaky Bucket Algorithm Using C.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Using C Picture a bucket with a. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. In class, we introduced the leaky bucket as a way to police the transmission rate of a session. One can do very clever things using the leaky. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the. Leaky Bucket Algorithm Using C.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Using C Each host is connected to the network by an interface containing a leaky bucket, that is, a finite internal queue. Leaky bucket algorithm for congestion control. This is one of the algorithm used for congestion control in network layer. One can do very clever things using the leaky. The leaky bucket algorithm is a simple yet effective algorithm designed to. Leaky Bucket Algorithm Using C.