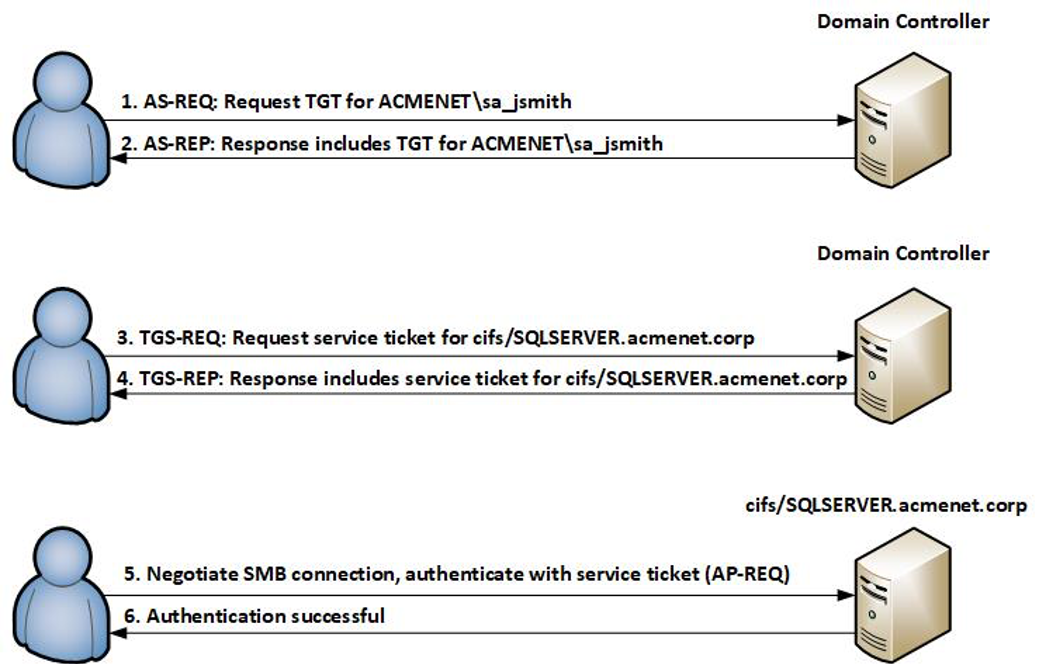
Kerberos Client Server Example . All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. Example of the kerberos process keep the learning going. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. It’s been used since windows 2000 and is a critical part of windows active. We’ll see an example of the client/server exchange a little later in this series. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Kerberos process breakdown (16 steps) 1. Client/server exchange (or lack thereof) For configuration examples using the commands in this chapter, refer to the section “kerberos configuration examples” located at the end of.
from www.mandiant.com
Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. We’ll see an example of the client/server exchange a little later in this series. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. It’s been used since windows 2000 and is a critical part of windows active. Kerberos process breakdown (16 steps) 1. For configuration examples using the commands in this chapter, refer to the section “kerberos configuration examples” located at the end of. Client/server exchange (or lack thereof) Kerberos is the default protocol for authenticating service requests between trusted devices on a network. Example of the kerberos process keep the learning going. All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file.
Kerberos Tickets on Linux Red Teams Mandiant
Kerberos Client Server Example Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. Client/server exchange (or lack thereof) It’s been used since windows 2000 and is a critical part of windows active. Example of the kerberos process keep the learning going. Kerberos process breakdown (16 steps) 1. We’ll see an example of the client/server exchange a little later in this series. For configuration examples using the commands in this chapter, refer to the section “kerberos configuration examples” located at the end of.
From redsiege.com
Kerberos Authentication Process Kerberos Client Server Example Kerberos is the default protocol for authenticating service requests between trusted devices on a network. Kerberos process breakdown (16 steps) 1. Example of the kerberos process keep the learning going. Client/server exchange (or lack thereof) It’s been used since windows 2000 and is a critical part of windows active. Before kerberos, ntlm authentication could be used, which requires an application. Kerberos Client Server Example.
From lasopagamer793.weebly.com
Kerberos client windows lasopagamer Kerberos Client Server Example Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Client/server exchange (or lack thereof) Example of the kerberos process keep the learning going. It’s been used since windows 2000 and is a critical part of windows active. We’ll see an example of the client/server. Kerberos Client Server Example.
From www.freecodecamp.org
How Does Kerberos Work? The Authentication Protocol Explained Kerberos Client Server Example Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. For. Kerberos Client Server Example.
From docs.getskyvault.net
Kerberos client configuration SkyVault Documentation Kerberos Client Server Example We’ll see an example of the client/server exchange a little later in this series. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. For configuration examples using the commands in this chapter, refer to the section “kerberos configuration examples” located at the end of.. Kerberos Client Server Example.
From www.beyondtrust.com
Setup Example 2 Kerberos KDC and LDAP Server on the Same Network Kerberos Client Server Example All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. We’ll see an example of the client/server exchange a little later in this series. Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. Kerberos process. Kerberos Client Server Example.
From www.slideserve.com
PPT Active Directory and NT Kerberos PowerPoint Presentation, free Kerberos Client Server Example Kerberos process breakdown (16 steps) 1. Example of the kerberos process keep the learning going. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. We’ll see an example of. Kerberos Client Server Example.
From samonsatrom1955.blogspot.com
When Using Kerberos, What Is The Purpose Of A Ticket? Samons Atrom1955 Kerberos Client Server Example Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Example of the kerberos process keep the learning going. Kerberos process breakdown (16 steps) 1. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. For configuration examples using the. Kerberos Client Server Example.
From learn.microsoft.com
Kerberos authentication troubleshooting guidance Windows Server Kerberos Client Server Example Example of the kerberos process keep the learning going. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. For configuration examples using the commands in this chapter, refer to the section “kerberos configuration examples” located at the end of. We’ll see an example of the client/server exchange a little later in this series. All. Kerberos Client Server Example.
From ithelp.ithome.com.tw
19.Windows Log分析(Kerberos登入) iT 邦幫忙一起幫忙解決難題,拯救 IT 人的一天 Kerberos Client Server Example It’s been used since windows 2000 and is a critical part of windows active. Kerberos process breakdown (16 steps) 1. Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. We’ll see an example of the client/server exchange a little later in this series. All that is required to set up a kerberos. Kerberos Client Server Example.
From www.upguard.com
What is Kerberos Authentication? A Complete Overview UpGuard Kerberos Client Server Example Kerberos process breakdown (16 steps) 1. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. All that is required to set up a kerberos 5 client is to install. Kerberos Client Server Example.
From electronicsguide4u.com
Microservices Architecture & Security With Kerberos Authentication Guide Kerberos Client Server Example Client/server exchange (or lack thereof) Example of the kerberos process keep the learning going. It’s been used since windows 2000 and is a critical part of windows active. All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. Before kerberos, ntlm authentication could. Kerberos Client Server Example.
From www.mvps.net
The Kerberos protocol Blog tutorials Kerberos Client Server Example Kerberos process breakdown (16 steps) 1. Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. Client/server exchange (or lack thereof) We’ll see an example of. Kerberos Client Server Example.
From docs.netscaler.com
How NetScaler implements Kerberos for client authentication Kerberos Client Server Example All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Before kerberos, ntlm authentication could be used, which. Kerberos Client Server Example.
From help.liferay.com
Authenticating with Kerberos Liferay Help Center Kerberos Client Server Example Example of the kerberos process keep the learning going. Kerberos process breakdown (16 steps) 1. It’s been used since windows 2000 and is a critical part of windows active. Client/server exchange (or lack thereof) For configuration examples using the commands in this chapter, refer to the section “kerberos configuration examples” located at the end of. We’ll see an example of. Kerberos Client Server Example.
From searchwindowsserver.techtarget.com
Kerberos platform interoperability connects Windows to the rest of the Kerberos Client Server Example Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. We’ll see an example of the client/server exchange a little later in this series. Example of the kerberos. Kerberos Client Server Example.
From www.upguard.com
What is Kerberos Authentication? A Complete Overview UpGuard Kerberos Client Server Example Example of the kerberos process keep the learning going. Kerberos process breakdown (16 steps) 1. We’ll see an example of the client/server exchange a little later in this series. Client/server exchange (or lack thereof) All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration. Kerberos Client Server Example.
From laptrinhx.com
Preparing onpremises and AWS environments for external Kerberos Kerberos Client Server Example We’ll see an example of the client/server exchange a little later in this series. Client/server exchange (or lack thereof) Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. For configuration examples using the commands in this chapter,. Kerberos Client Server Example.
From www.funtoo.org
Kerberos With Funtoo Funtoo Kerberos Client Server Example We’ll see an example of the client/server exchange a little later in this series. It’s been used since windows 2000 and is a critical part of windows active. Client/server exchange (or lack thereof) Kerberos is the default protocol for authenticating service requests between trusted devices on a network. All that is required to set up a kerberos 5 client is. Kerberos Client Server Example.
From www.oreilly.com
4. Kerberos Hadoop Security [Book] Kerberos Client Server Example For configuration examples using the commands in this chapter, refer to the section “kerberos configuration examples” located at the end of. Kerberos process breakdown (16 steps) 1. We’ll see an example of the client/server exchange a little later in this series. Client/server exchange (or lack thereof) Following these tips when selecting the realm name significantly simplifies the configuration of kerberos. Kerberos Client Server Example.
From blog.csdn.net
HDFS安全kerberos介绍_kerberos hdfs 文件加密CSDN博客 Kerberos Client Server Example All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. Kerberos process breakdown (16 steps) 1. Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. It’s been used since windows 2000 and is a critical. Kerberos Client Server Example.
From access.redhat.com
Chapter 50. Managing Kerberos ticket policies Red Hat Enterprise Linux Kerberos Client Server Example It’s been used since windows 2000 and is a critical part of windows active. Kerberos process breakdown (16 steps) 1. Example of the kerberos process keep the learning going. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Before kerberos, ntlm authentication could be. Kerberos Client Server Example.
From cookinglove.com
Kerberos tutorial Kerberos Client Server Example Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. Client/server exchange (or lack thereof) Kerberos is the default protocol for authenticating service requests between trusted devices on a network. Example of the kerberos process keep the learning going. We’ll see an example of the client/server exchange a little later in this series.. Kerberos Client Server Example.
From www.geeksforgeeks.org
Types of Authentication Protocols Kerberos Client Server Example Kerberos is the default protocol for authenticating service requests between trusted devices on a network. Kerberos process breakdown (16 steps) 1. It’s been used since windows 2000 and is a critical part of windows active. For configuration examples using the commands in this chapter, refer to the section “kerberos configuration examples” located at the end of. Example of the kerberos. Kerberos Client Server Example.
From www.mandiant.com
Kerberos Tickets on Linux Red Teams Mandiant Kerberos Client Server Example Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. All that is. Kerberos Client Server Example.
From www.opensourceforu.com
Kerberos The Trusted Watchdog of Distributed Computing Kerberos Client Server Example Example of the kerberos process keep the learning going. Kerberos process breakdown (16 steps) 1. Client/server exchange (or lack thereof) We’ll see an example of the client/server exchange a little later in this series. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. It’s. Kerberos Client Server Example.
From www.slideshare.net
Kerberos Protocol Kerberos Client Server Example It’s been used since windows 2000 and is a critical part of windows active. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Client/server exchange (or lack thereof) All that is required to set up a kerberos 5 client is to install the client. Kerberos Client Server Example.
From docs.oracle.com
How the Kerberos Service Works Managing Kerberos and Other Kerberos Client Server Example Kerberos is the default protocol for authenticating service requests between trusted devices on a network. Kerberos process breakdown (16 steps) 1. Client/server exchange (or lack thereof) All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. Example of the kerberos process keep the. Kerberos Client Server Example.
From documentation.softwareag.com
Kerberos Delegated Authentication Kerberos Client Server Example Kerberos process breakdown (16 steps) 1. For configuration examples using the commands in this chapter, refer to the section “kerberos configuration examples” located at the end of. We’ll see an example of the client/server exchange a little later in this series. It’s been used since windows 2000 and is a critical part of windows active. Kerberos is the default protocol. Kerberos Client Server Example.
From trabajosdesisifo.blogspot.com
Los trabajos de Sísifo Windows Server Spring Security Kerberos Kerberos Client Server Example We’ll see an example of the client/server exchange a little later in this series. Client/server exchange (or lack thereof) Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. All that is required to set up a kerberos. Kerberos Client Server Example.
From slideplayer.com
CLASP Project AAI Nov 2000 Denise Heagerty, CERN ppt download Kerberos Client Server Example Kerberos is the default protocol for authenticating service requests between trusted devices on a network. Example of the kerberos process keep the learning going. We’ll see an example of the client/server exchange a little later in this series. All that is required to set up a kerberos 5 client is to install the client packages and provide each client with. Kerberos Client Server Example.
From blog.51cto.com
Kerberos认证原理简介_51CTO博客_kerberos认证 Kerberos Client Server Example Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Kerberos process breakdown (16 steps) 1. All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. We’ll see. Kerberos Client Server Example.
From medium.com
Brief Summary of Kerberos. Kerberos authentication process. by Kerberos Client Server Example Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. Kerberos is the default protocol for authenticating service requests between trusted devices on a network. All that is. Kerberos Client Server Example.
From www.getkisi.com
Authentication Protocol Overview OAuth2, SAML, LDAP, RADIUS, Kerberos Kerberos Client Server Example Kerberos is the default protocol for authenticating service requests between trusted devices on a network. All that is required to set up a kerberos 5 client is to install the client packages and provide each client with a valid krb5.conf configuration file. Before kerberos, ntlm authentication could be used, which requires an application server to connect to a domain. It’s. Kerberos Client Server Example.
From www.paloaltonetworks.com
Detecting the Kerberos noPac Vulnerabilities with Cortex XDR™ Palo Kerberos Client Server Example Kerberos is the default protocol for authenticating service requests between trusted devices on a network. For configuration examples using the commands in this chapter, refer to the section “kerberos configuration examples” located at the end of. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust. Kerberos Client Server Example.
From www.beyondtrust.com
Example 3 Kerberos KDC and LDAP Server on Separate Networks Kerberos Client Server Example Example of the kerberos process keep the learning going. Client/server exchange (or lack thereof) We’ll see an example of the client/server exchange a little later in this series. Following these tips when selecting the realm name significantly simplifies the configuration of kerberos clients, above all when it is desired to establish trust relationships. All that is required to set up. Kerberos Client Server Example.